Professional Documents
Culture Documents
Ds Deep Discovery
Uploaded by
Nicolás BoettcherOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Ds Deep Discovery
Uploaded by
Nicolás BoettcherCopyright:
Available Formats
Trend Micro
DEEP DISCOVERY
Targeted attack detection, in-depth analysis, and rapid response
Advanced Persistent Threats (APTs) and targeted attacks have clearly proven their ability to evade conventional security defenses, to remain undetected for extended periods, and to exfiltrate corporate data and intellectual property. Analysts and experts recognize these issues, and recommend that enterprises redefine security due diligence to embrace specialized threat detection technology and a proactive process of real-time threat management. Trend Micro Deep Discovery 3.2 provides you with the network-wide visibility, insight, and control you need to combat APTs and targeted attacks. Deep Discovery uniquely detects and identifies evasive threats in real-time, then provides the in-depth analysis and relevant actionable intelligence that will equip you to assess, remediate, and defend against targeted attacks in your organization. Deep Discovery is at the core of the Trend Micro Custom Defensea complete solution that enables you to detect, analyze, adapt, and respond to targeted attacks against your organization. Deep Discovery specialized inspection engines and custom sandbox simulation identify zero-day malware, malicious communications, and attacker activities that are invisible to standard security defenses. Deep analysis, containment, and remediation are powered by relevant threat intelligence and visibility into network-wide security events, while security update exports enable protection against further attack.
DETECTS AND PROTECTS AGAINST APTs and targeted attacks Zero-day malware and document exploits Attacker network activity Web threats (exploits, drive-by-downloads) Email threats (phishing, spear phishing) Data exfiltration Bots, trojans, worms, keyloggers Disruptive applications
KEY BENEFITS APT & Targeted Attack Detection Reduces the risk of damage and data loss from APTs Network-Wide Visibility Reveals and tracks your true security posture In-Depth Contextual Analysis & Insight Fully characterizes threat and risk factors Rapid Containment & Response Speeds up recovery with actionable intelligence, and security update exports Cornerstone of a Custom Defense Combats the threats that matter to you using custom sandbox simulation, intelligence, and updates
The Deep Discovery solution is comprised of two components. The Deep Discovery Inspector provides network threat detection, custom sandboxing and real-time analysis and reporting. The optional Deep Discovery Advisor provides open, scalable sandbox analysis, visibility to network-wide security events, and security update exportsall in a unified intelligence platform.
PAGE 1 OF 4 DATASHEET DEEP DISCOVERY 3.2
Deep Discovery Inspector
Deep Discovery Inspector provides network traffic inspection, advanced threat detection and real-time analysis and reportingall purpose-built for detecting APT and targeted attacks. It uses a 3-level detection scheme to perform initial detection, then sandbox simulation and correlation, and finally, a cross-correlation to discover low and slow and other evasive attacker activities discernable only over an extended period. Specialized detection and correlation engines provide the most accurate and up-to-date protection aided by global threat intelligence from Trend Micro Smart Protection Network, and dedicated threat researchers. The results are high detection rates, low false positives, and in-depth incident reporting information designed to speed up the containment of an attack.
KEY FEATURES
Advanced Threat Detection Deep Discovery Inspector focuses on identifying malicious content, communications, and behavior indicative of advanced malware or attacker activity across every stage of the attack sequence using a non-intrusive, listen-only inspection of all types of network traffic. Dedicated threat engines and multi-level correlation rules deliver the best detection and minimize false positives Virtual analyzer uses custom sandbox simulation to provide additional detection and full forensic analysis of suspect content Smart Protection Network intelligence and dedicated threat researchers provide continually updated detection intelligence and correlation rules to identify attacks Real-Time Threat Console Places threat visibility and deep analysis at your fingertips Quick access widgets provide critical information at a glance In-depth analysis of attack characteristics, behavior, and communication GeoTrack identifies the origins of malicious communication Watch List Delivers risk-focused monitoring of high severity threats and high value assets Focused tracking of suspicious activity and events on designated hosts Hosts to be tracked determined via threat detection or customer selection Detailed event timeline tracks all attack activities involving target hosts Threat Connect Provides the threat intelligence you need to understand and remediate an attack Direct access to Trend Micro intelligence portal for a specific attack or malware Detailed threat characteristics; containment and remediation recommendations Direction to available antivirus/other signature updates for this threat SIEM Management Integration with leading SIEM platforms delivers improved enterprise-wide threat management from a single SIEM console Network detections, confirmed incidents, and contextual data are reported to SIEM Deep network visibility enhances correlation and multi-dimensional attack profiling of SIEM Enterprise-wide threat management provided by SIEM as the central console
Flexible, High-Capacity Deployment Deep Discovery Inspector features a high-performance architecture designed to meet the demanding and diverse capacity requirements of customers of all sizes. The product is available on a full range of hardware, software, and virtual appliances supporting multi-gigabit corporate backbones down to remote office locations.
Threat Tracking, Analysis, and Action The Deep Discovery Inspector console provides real-time threat visibility and deep analysis in an intuitive format that allows security professionals to focus on the real risks, perform forensic analysis, and rapidly remediate issues.
PAGE 2 OF 4 DATASHEET DEEP DISCOVERY 3.2
Deep Discovery Advisor
Deep Discovery Advisor provides open, scalable custom sandbox analysis, visibility to network-wide security events, and security update exportsall in a unified intelligence platform. The Advisor augments the analysis power of Deep Discovery Inspector and enables the adaptive protection and rapid response capabilities of the Custom Defense.
KEY FEATURES
Threat Analyzer The Threat Analyzer is an optional component designed to offer in-depth simulation and analysis of potentially malicious sample files, including executables and common office documents. It can augment and centralize the simulation of Deep Discovery Inspector, as well as provide advanced detection and analysis security for professionals or any security product or service via an open web services interface. In-depth threat simulation, and analysis uses sandbox simulation and other advanced detection engines to classify and deeply analyze submitted files Custom sandbox execution environments allow the customer to create and analyze multiple fully custom target images that precisely match their host environments Scalable architecture supports incremental capacity that ranges up to 50,000 samples/day Open, automated, and manual submission supports input from security analysts, as well as automated submission and results loopback by Trend Micro products and third-party or custom products Integration with Deep Discovery Inspector and other Trend Micro products provides expanded detection and analysis options to customers Threat Intelligence Center The Threat Intelligence Center is a complete analysis environment for event data from the threat analyzer, as well as security events and logs collected from Deep Discovery Inspector, other Trend Micro products, and third-party solutions. Using these sources and integrated Threat Connect intelligence, Threat Intelligence Center provides in-depth insights to drive risk-based incident assessment, containment and remediation. In-depth analysis of incidents, and events using automated analysis, visualization, and advanced search and investigation tools Risk-focused monitoring and investigation Network-wide security event collection of events/logs from most Trend Micro and third-party products ensures a full risk assessment and effective containment and remediation measures Threat Connect intelligence is automatically integrated into analysis results, providing detailed threat characteristics and context-relevant intelligence for containment and remediation Deep Discovery Inspector centralized reporting consolidates detection results from multiple Deep Discovery Inspector units into a single dashboard and customizable reports SIEM connect with leading platforms delivers improved enterprise-wide threat management from a single SIEM console Security Update Server The Security Update Server provides the means to export useful security blocking information learned from Threat Analyzer simulation. This information includes newly identified malicious IP/ URL addresses and file hash codes that can be useful to a variety of security products. Deep Discovery Inspector and certain other Trend Micro products automatically receive this information. The information can also be manually exported via CSF files.
PAGE 3 OF 4 DATASHEET DEEP DISCOVERY 3.2
How Deep Discovery Works
Deep Discovery is purpose-built for detecting APT and targeted attacksidentifying malicious content, communications, and behavior that may indicate advanced malware or attacker activity across every stage of the attack sequence. Deep Discovery uses a 3-level detection scheme to perform initial detection, custom simulation and correlation, then a final cross-correlation to reduce false positives and discover evasive activities. The detection engines and correlation rules are powered by global threat intelligence from Trend Micro Smart Protection Network and dedicated Threat Researchers. The result is a high detection rate, low false positives, and in-depth incident intelligence to speed the containment of an attack.
ATTACK DETECTION Malicious Content Emails containing embedded document exploits Drive-by-downloads Zero-day and known malware Command-and-control communication for all malware: bots, downloaders, data stealing, worms, and blended threats Backdoor activity by attacker Malware activity: propagation, downloading , spamming, etc. Attacker activity: scan, brute force, service exploitation Data exfiltration DETECTION METHODS Decode and decompress embedded files Sandbox simulation of suspicious files Browser exploit kit detection Malware scan (Signature and Heuristic)
RISK MANAGEMENT SERVICES Trend Micro service specialists augment your security responsiveness and expertise with installation, monitoring and consulting services to further reduce your risk exposure and security management costs. SPECIFICATIONS Deep Discovery Inspector Model 1000: 1 Gbps Hardware Appliance Model 500: 500 Mbps Hardware Appliance Model VM: VMware Software Appliance Deep Discovery Advisor Hardware Appliance Can be clustered up to 5 units
Suspect Communication
Destination analysis (URL, IP, domain, email, IRC channel, etc.) via dynamic blacklisting, white listing Smart Protection Network URL reputation Communication fingerprinting rules Rule-based heuristic analysis Identification and analysis of usage of 100s of protocols and applications including HTTP-based apps
Attack Behavior
The Custom Defense Against Your Attackers
Deep Discovery specialized custom threat detection is at the core of an effective defense against the attacks targeted at your organization. But, Trend Micro has also integrated the advanced malware detection of Deep Discovery Advisor with selected Trend Micro products to improve your protection against the all-important initial stage of an attack. In addition, to provide the truly adaptive protection of a custom defense, the in-depth results of Deep Discovery Advisor analysis are used to update Trend Micro products to immediately strengthen your defense against further attack. Network-level attack detection and custom analysis Protection solutions with custom malware detection Custom security updates for adaptive protection Actionable intelligence based on full contextual analysis speeds response
2012 by Trend Micro Incorporated. All rights reserved. Trend Micro, the Trend Micro t-ball logo, and Trend Micro Smart Protection Network are trademarks or registered trademarks of Trend Micro Incorporated. All other company and/or product names may be trademarks or registered trademarks of their owners. Information contained in this document is subject to change without notice. [DS01_DD3.2_121002]
PAGE 4 OF 4 DATASHEET DEEP DISCOVERY 3.2
You might also like
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- HII Denial of Service Attacks-Trends Techniques and TechnologiesDocument15 pagesHII Denial of Service Attacks-Trends Techniques and TechnologiesNicolás BoettcherNo ratings yet
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- NASA Cybersecurity ReportDocument24 pagesNASA Cybersecurity ReportThe Huntsville TimesNo ratings yet
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- IBM. Taming The Data Demons: Leveraginginformation in The Age of RiskDocument12 pagesIBM. Taming The Data Demons: Leveraginginformation in The Age of RiskNicolás BoettcherNo ratings yet
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- VoIP Q4 2010 Short ReportDocument8 pagesVoIP Q4 2010 Short ReportNicolás BoettcherNo ratings yet
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- Randstad. Uso de Redes Sociales en ChileDocument50 pagesRandstad. Uso de Redes Sociales en ChileNicolás BoettcherNo ratings yet
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- McAfee & SAIC. Intellectual Capital and Sensitive Corporate Data Now The Latest Cybercrime CurrencyDocument11 pagesMcAfee & SAIC. Intellectual Capital and Sensitive Corporate Data Now The Latest Cybercrime CurrencyNicolás BoettcherNo ratings yet
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Mcaffe Risk Compliance Outlook 2011Document22 pagesMcaffe Risk Compliance Outlook 2011Nicolás BoettcherNo ratings yet
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Voluntary Industry Code of Practice On Traffic Management Transparency On Broadband Services March 2011Document9 pagesVoluntary Industry Code of Practice On Traffic Management Transparency On Broadband Services March 2011Chris MarsdenNo ratings yet
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- PIP Social Media and Young Adults Report Final With ToplinesDocument51 pagesPIP Social Media and Young Adults Report Final With ToplinesNicolás BoettcherNo ratings yet
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
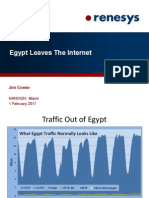
- Renesys. Egypt Leaves The InternetDocument18 pagesRenesys. Egypt Leaves The InternetNicolás BoettcherNo ratings yet
- IFPI Digital Music Report 2011Document32 pagesIFPI Digital Music Report 2011Nicolás BoettcherNo ratings yet
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Forrester Consulting. Ecommerce Web Site Performance TodayDocument21 pagesForrester Consulting. Ecommerce Web Site Performance TodayNicolás BoettcherNo ratings yet
- IDC, Accelerate Hybrid Cloud Success: Adjusting The IT MindsetDocument16 pagesIDC, Accelerate Hybrid Cloud Success: Adjusting The IT MindsetNicolás BoettcherNo ratings yet
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- Dcs PPT VijayDocument14 pagesDcs PPT VijayvijaykumarselvamNo ratings yet
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- Liu 2021Document13 pagesLiu 2021dinhcauduong12No ratings yet
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Lightdm - Ubuntu Gets Stuck in A Login Loop - Ask UbuntuDocument7 pagesLightdm - Ubuntu Gets Stuck in A Login Loop - Ask UbuntuRick RockyNo ratings yet
- Feynman Integral Evaluation by A Sector Decomposition Approach (Fiesta)Document25 pagesFeynman Integral Evaluation by A Sector Decomposition Approach (Fiesta)Victor Alexander Gonzales AquinoNo ratings yet
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Mixed Signal Embedded ProgrammingDocument268 pagesMixed Signal Embedded ProgrammingPavan Kumar100% (14)
- Oop Exercises Java Programming TutorialDocument9 pagesOop Exercises Java Programming TutorialJoe TitanNo ratings yet
- Digital Publishing Zmags PlaybookDocument45 pagesDigital Publishing Zmags Playbookted.hebert7509100% (1)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- 4 Shrink Wrap - 13Document2 pages4 Shrink Wrap - 13Varun ChaitanyaNo ratings yet
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- H. K. Høidalen L. Prikler J. L. Hall: Atpdraw-Graphical Preprocessor To Atp. Windows VersionDocument6 pagesH. K. Høidalen L. Prikler J. L. Hall: Atpdraw-Graphical Preprocessor To Atp. Windows VersionJuan Sebastián Londoño MartínezNo ratings yet
- Chapter 04. AutomataDocument46 pagesChapter 04. Automatakims3515354178No ratings yet
- WT4 Server Side TechnologyDocument18 pagesWT4 Server Side TechnologySagun Raj Basnet75% (4)
- 捷力 TC車床型錄 (跨頁) 190821 (v10) -已壓縮Document11 pages捷力 TC車床型錄 (跨頁) 190821 (v10) -已壓縮mahmoud nafieNo ratings yet
- Empowerment Technologies: 3 Quarter Week 2Document11 pagesEmpowerment Technologies: 3 Quarter Week 2Kay Tracey Aspillaga UrbiztondoNo ratings yet
- Lesson For SpreadsheetsDocument69 pagesLesson For SpreadsheetsCrisna Rivera PundanoNo ratings yet
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (121)
- SP12-18-48 Standard Protocol V3.2Document31 pagesSP12-18-48 Standard Protocol V3.2Ivan Alain Serrudo SeasNo ratings yet
- 4th AIDocument12 pages4th AIPriyaNo ratings yet
- Practical 4Document38 pagesPractical 4YOUR FATHERNo ratings yet
- Chini Chinni Aasa Chinadani AasaDocument3 pagesChini Chinni Aasa Chinadani AasaMastan RaoNo ratings yet
- Interface Clavier PicDocument27 pagesInterface Clavier Picblaiso2020No ratings yet
- Growbyten - Offer LetterDocument2 pagesGrowbyten - Offer LetterHariharan MadeswaranNo ratings yet
- DC Riverside Bldg-LOD 100 PDFDocument9 pagesDC Riverside Bldg-LOD 100 PDFSirHumptyDumptyNo ratings yet
- Unit 1: Computers and Types of ComputerDocument36 pagesUnit 1: Computers and Types of ComputerNgọc CaroNo ratings yet
- Dss Assignment 2 RealDocument7 pagesDss Assignment 2 RealPeace Runyararo MutenderiNo ratings yet
- Intro To Ns2Document239 pagesIntro To Ns2Umair Ali Soomro100% (1)
- Lecture01 4upDocument7 pagesLecture01 4upAnthonyLimNo ratings yet
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- PDF Download Decameron Tarot English and Spanish Edition Textbook 210211144001Document34 pagesPDF Download Decameron Tarot English and Spanish Edition Textbook 210211144001Glenys CabanaNo ratings yet
- PTSC M&C: Resources DepartmentDocument2 pagesPTSC M&C: Resources DepartmentChad Dylan PhamNo ratings yet
- Netbackup Emergencey Binary CodeDocument73 pagesNetbackup Emergencey Binary CodesrccseNo ratings yet
- Hardware OS Assessment-1Document7 pagesHardware OS Assessment-1Kishlay PranjalNo ratings yet
- Normalization Vs DeNormalizationDocument26 pagesNormalization Vs DeNormalizationamolgavaliNo ratings yet
- Healing Your Aloneness: Finding Love and Wholeness Through Your Inner ChildFrom EverandHealing Your Aloneness: Finding Love and Wholeness Through Your Inner ChildRating: 3.5 out of 5 stars3.5/5 (9)