Professional Documents
Culture Documents
Biometrics in Secure E-Transaction: International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Biometrics in Secure E-Transaction: International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Copyright:
Available Formats
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.com Volume 2, Issue 2, March April 2013 ISSN 2278-6856
Biometrics in Secure e-Transaction
Ms. Swati S Bobde1, Prof. D. N. Satange2
1
Post Graduate Student, Dept of Computer Science, Arts, Commerce & Science College, Amravati Asstt. Professor, Dept of Computer Science, Arts Commerce & Science College, Amravati
2
Abstract- In the present day word, online shopping using
WAP enabled mobile phone has widely come into use. Credit cards serve as the currency during e-business and eShopping. As technology has advanced in the negative side also hackers steal, misuse credit card numbers, even though the network has been made secure. So, in this seminar report, we have proposed a multi-biometric model (integrating voice, fingerprint and facial scanning) that can be embedded in a mobile phone, this making e-transactions more secure. The model is very cost effective as we have tried to use the hardware already present in the phone. This paper uses for image processing or facial reorganization and finger print. We have also simulated a few graphs for voice recognition and facial verification using MATLAB. The paper topic Biometrics in Secure E-Transactions CSE Seminars very clearly explains the indispensable role of biometrics for secure-transactions. The topic says that as technology has advanced there has been a negative side also hackers as spoofers steal/ misuse credit card numbers, even though the network has been made secure. The paperr abstract gives some insight into Multibiometrics. It says that A multibiometrics system is obtained by the integration of multiple individual biometrics models. A numbers of models integrating hand geometry, keystroke dynamics, face and iris recognition system have flooded the markets in recent years.
Telemedicine and teleconferencing Thus, these phones with wide roaming facility prove to be a really versatile device. Biometrics in Secure ETransactions clearly explains the indispensable role of biometrics for secure-transactions. This paper discusses that as technology has advanced there has been a negative side also hackers as spoofers steal / misuse credit card numbers, even though the network has been made secure. This paper, proposes a multi-biometric model (integrating voice, fingerprint and facial scanning) that can be embedded in a mobile phone this making etransactions more secure.
2. BIOMETRICS
The term biometrics is derived from the Greek words bio (life) and metrics (to measure). Automated biometric systems have only become available over the last few decades, due to significant advances in the field of computer processing. Many of these new automated techniques, however, are based on ideas that were originally conceived hundreds, even thousands of years ago. Biometrics(or biometric authentication ) refers to the identification of humans by their characteristics or traits. Biometrics is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. A biometric system is a recognition system, which makes a personal identification by determining the authenticity of a specific physiological or behavioral characteristic possessed by the user. This method of identification is preferred over traditional methods involving passwords and PIN numbers for various reasons: The person to be identified is required to be physically present at the point of identification. Identification based on biometric techniques eliminates the need to remember a password or carry an identity. Depending on the context on which a biometric system works, it can be Either classified as an identification system or a verification (authentication) system identification involves in establishing a persons identify whereas in verification involves confirming or denying a persons claiming identity. More traditional means of access control include token-based identification systems , such as a driver's license or passport, and knowledge-based identification systems, such as a password or personal identification Page 243
Keywords-Biometrics, Multibiometrics, Face Recognition, Voice Recognition, Iris Recognition, Finger Print Identification
1.INTRODUCTION
In an era of Information Technology, mobile phones are more and more widely used Worldwide, not only for basic communications, but also as a tool to deal with personal Affairs and process information acquired anywhere at any time. It is reported that there are more than 4 billion cell phone users over the world and this number still continues to grow as predicted that by 2015 more than 86% of the world population will own at least one cell phone. Mobile phones have ceased to be exclusive status of the high class and, today has become an indispensable electronic gadget in the life of many. The main reason for their higher market penetrations in recent days is their incredible array of functions at an affordable cost. Apart from setting remainders and sending e-mails, they are also used in e-business SMS messaging Chatting Volume 2, Issue 2 March April 2013
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.com Volume 2, Issue 2, March April 2013 ISSN 2278-6856
number. Since biometric identifiers are unique to individuals, they are more reliable in verifying identity than token and knowledge-based methods; however, the collection of biometric identifiers raises privacy concerns about the ultimate use of this information. Traditional security practices often involve the use of two authentication methods: possession based and knowledge based. Knowledge based authentication requires that the users remember a user name and password or PIN numbers or answers to security questions. Possession based can use radio frequency IDs, Smart Cards, Interactive Tokens etc. Possession based authentication has the same usability issue as the knowledge based authentication, if the object used for authentication is forgotten at home, in the hotel room, in the car etc the authentication face and iris recognition system have flooded the markets in recent years. Here we present a multimodal system that can be embedded in a mobile phone, which integrates fingerprint, voice and facial scanning. It shuts down the problem of high False Rejection Rate of facial scanners, eliminates the fooling of fingerprint scanners and overshadows the disadvantage of voice recognition models. Multi-biometric systems use multiple sensors or biometrics to overcome the limitations of unimodal biometric systems. For instance iris recognition systems can be compromised by aging iris and finger scanning systems by worn-out or cut fingerprints. While unimodal biometric systems are limited by the integrity of their identifier, sequential, parallel, hierarchical and serial integration modes, respectively. Broadly, the information fusion is divided into three parts, pre-mapping fusion, midst-mapping fusion, and post-mapping fusion/late fusion. In pre-mapping fusion information can be combined at sensor level or feature level. Sensor-level fusion can be mainly organized in three classes: (1) Single sensor-multiple instances, (2) intra-class multiple sensors, and (3) Inter-class multiple sensors. Feature-level fusion can be mainly organized in two categories: (1) intra-class and (2) Inter-class. Intra-class is again classified into four subcategories: (a) Same sensor-same features, (b) Same sensor-different features, (c) Different sensors-same features, and (d) Different sensors-different features[1]
Figure 1. Biometric Systems Classes[1] It is unlikely that several unimodal systems will suffer from identical limitations. Multibiometric systems can integrate these unimodal systems sequentially, simultaneously, a combination thereof, or in series, which refer to sequential, parallel, hierarchical and serial integration modes, respectively Multi-biometric obtain sets of information from the same marker (i.e., multiple images of an iris, or scans of the same finger) or information from different biometrics (requiring fingerprint scans and, using voice recognition, a spoken pass-code) cannot be performed. Biometric security systems are using: Physical human identifiers like fingerprint, face, iris, retina, DNA, hand geometry and vein geometry Behavioral identifiers like speech, signature, and keystroke timing Chemical identifiers like odor and body heat. Biometric systems are used for two purposes. One is to verify that the user is genuine by comparing the acquired biometric trait with the one stored for that user. The other purpose the biometrics are used is to identify a user in which case the acquired biometric trait is compared with a collection of the same traits from multiple users.[3]
4. NEED FOR BIOMETRICS IN MOBILE PHONES
Now a days, shopping through the internet has become very popular and surely, a WAP enabled mobile phone provides the facilities to consumers to shop online. Credit cards continue to be an efficient tool for online money transactions. But, on the other hand, credit card number can be stolen on its way to its destination and can be misused by hackers. Thus, e-Business through a mobile phone becomes insecure. Also, a report in www.download.com stated that much anti-fraud Software, like those provided by ArticSoft and ISC, created a back door entry and were largely involved in data spoofing. In addition to this, many user and companies were prone to the attack of many viruses and Trojan horses. With so much of problems faced, the service provide turned their attention towards biometrics to prevent data spoofing and to provide secure eTransactions. Biometric systems can be integrated with cell phones in two ways: As a biometric collecting device or as a stand-alone system to protect unauthorized use of the cell phone. In the first case cell phones are collecting Page 244
3. MULTIBIOMETRICS
A multi-biometrics system is obtained by the integration of multiple individual biometrics models. A numbers of models integrating hand geometry, keystroke dynamics, Volume 2, Issue 2 March April 2013
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.com Volume 2, Issue 2, March April 2013 ISSN 2278-6856
the biometric and then they are passing it via internet or via voice communication to a remote location where it is processed and matched. This proves useful for remote transactions when the identity of the caller has to be proven. As an example, the user calls his bank to make a transaction, he is going to introduce himself as Swati Bobade and in order to verify his identity he is asked to recite a passphrase. The voice recording is then processed and compared with the sample that was collected when the user enrolled in the system. Face, fingerprint, signature or key stroke are other biometric traits that todays cell phones have the capabilities to collect and transfer them to a remote location. The other implementation of biometric systems on cell phones is that the entire biometric system resides on the cell phone and it serves the purpose of preventing unauthorized access to cell phones functions and data. Biometric systems can replace the annoying PIN security and with a swipe of a finger the phone can be unlocked and used. Todays implementations of biometric systems on cell phones include fingerprint recognition, voice recognition, face recognition, signature recognition and keystroke recognition.
5. FUTURE MOBILE PHONE
Figure 4.future mobile phone [1] example of recent advances which successfully implemented biometrics on mobile phones
6. FINGER PRINT INDENTIFICATION ON MOBILE PHONE
Fingerprint biometric has been adopted widely for access control in places requiring high level of security such as laboratories and military bases. By attaching a fingerprint scanner to the mobile phone, this biometric could also be utilized for phone related security in a similar manner.fig.5.
7. FACE RECOGNITION
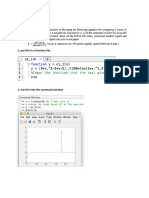
Facial recognition is considered to be one of the most tedious among all scans. Further, difficulty in acquisition of face and cost of equipments make it more complex. However, some WAP enabled phones like CX 400K and LG-SD1000 manufactured by LG electronics, have built in camera that can acquire images and can be transmitted over internet. This it is sent to the credit card company to verify the face received matches with the face in their database. If it matches, the goods are sent, else the order is rejected. We in our IMAGE PROCCESSING LAB took two faces with small differences (you see a small dot in the forehead of second face) and programmed MATLAB to find the difference between the two. The output is place below:[1]
Figure 2. Feasible scenarios of biometrics on mobile phone[1] Incorporated with advanced sensing platforms which could detect physiological and behavioral signals of various kinds, many types of biometric methods could be implemented on cell phones. This offers a wide range of possible applications such as personal privacy protection, mobile bank transaction service security, and telemedicine monitoring. The use of sensor data collected by mobile phones for biometric identification and authentication is an emerging frontier and has been increasingly explored in the recent decade. A typical architecture of this technology can be seen in Fig. 4.
Figure 3 Mobile biometric authentication system (Xie & Liu, 2010) [5] Volume 2, Issue 2 March April 2013 Page 245
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.com Volume 2, Issue 2, March April 2013 ISSN 2278-6856
physiological aspect of the human speech production system is the vocal tract shape. The vocal tract modifies the spectral content of an acoustic wave as it passes through it, thereby producing speech. Therefore, it is common in speaker verification systems to make use of features derived only from the vocal tract. The microphone in the mobile phone captures the speech. Then, using spectral analysis, an utterance may be represented as a sequence of feature vectors. Utterances, spoken by the same person but at difference times, result in similar yet a different sequence of features vectors. So, the irrespective of the mood of the consumer, his transaction is accepted or rejected.. A voice signal conveys a persons physiological characteristics such as the vocal chords, glottis, and vocal tract dimensions. Automatic speaker recognition (ASR) is a biometric method that encompasses verification and identification through voice signal processing. The speech features encompass high-level and low level parts. While the high-level features are related to dialect, speaker style and emotion state that are not always adopted due to difficulty of extraction, the low-level features are related to spectrum, which are easy to be extracted and are always applied to ASR.
Figure.5. Snapshots of fingerprint security - Pro (retrieved from company release news )[6] We in our IMAGE PROCCESSING LAB took two faces with small differences (you see a small dot in the forehead of second face) and programmed MATLAB to find the difference between the two. The output is place below:[1]
Figure 6
F Fffffff
Figure 7
Figure 9. Voice biometric authentication for e-commerce transactions via mobile phone. [7]
9. IRIS RECOGNITION
Figure 8. Difference between two image can be found by MATLAB [1] The above simulations shows that even two persons having almost similar face with minute difference can also be differentiated. Now, there arises a problem. A man, without bread, make as a transaction successfully .A week later he makes another transaction with some hair grown on his chin and go for acquiring images of any part of the face like forehead, nose, ear etc. Hence, this type of facial scanning system can be used as a part of the multi-biometric system we have presented above. With the integration of digital cameras that could acquire images at increasingly high resolution and the increase of cell phone computing power, mobile phones have evolved into networked personal image capture devices, which can perform image processing tasks on the phone itself and use the result as an additional means of user input and a source of context data (Rohs, 2005). This image acquisition and processing capability of mobile phones could be ideally utilized for mobile iris biometric. Recently, iris recognition technology has been utilized for the security of mobile phones. As a biometric of high reliability and accuracy, iris recognition provides high level of security for cellular phone based services for example bank transaction service via mobile phone. One major challenge of the implementation of iris biometric on mobile phone is the iris image quality, since bad image quality will affect the entire iris recognition process. Previously, the high quality of iris images was Page 246
8. VOICE RECOGNITION
The speaker-specific characteristics of speech are due to difference in physiological and behavioral aspects of the speech production system in humans. The main Volume 2, Issue 2 March April 2013
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.com Volume 2, Issue 2, March April 2013 ISSN 2278-6856
achieved through special hardware design. For example, the Iris Recognition Technology for Mobile Terminals software once used existing cameras and target handheld devices with dedicated infrared cameras (Kang, 2010). To provide more convenient mobile iris recognition, an iris recognition system in cellular phone only by using builtin mega-pixel camera and software without additional hardware component was developed (Cho et al., 2005). Considering the relatively small CPU processing power of cellular phone, in this system, a new pupil and iris localization algorithm apt for cellular phone platform was proposed based on detecting dark pupil and corneal specular reflection by changing brightness & contrast value. Results show that this algorithm can be used for real-time iris localization for iris recognition in cellular phone. In2006, OKI Electric Industry Co., Ltd. announced its new Iris Recognition Technology for Mobile Terminals using a standard camera that is embedded in a mobile phone based on the original algorithm OKI developed, a snapshot of which can be seen in Fig. 10.
Figure 10. Iris recognition technology for mobile terminals. [8]
10. CHALLENGES TO MOBILE PHONE
In order to ensure the accuracy and efficiency of biometrics recognition on mobile phones, computing power and storage capacity of mobile phones are still needed to be significantly enhanced. Currently, the implementation of biometrics on mobile phones usually requires the simplification of algorithm used in conventional biometrics in order to be adapted for the relatively small CPU processing power of a cellular phone. This adaption will inevitably reduce the accuracy and security level, which highly limits the performance of mobile phone enabled biometric techniques. In addition, the essential hardware i.e. biometric sensors embedded on mobile phones are also required to provide better performance, e.g. higher resolution of image acquired with digital cameras on mobile phones, at lower cost while maintaining their miniaturization feature.[2]
Figure11. An outline of future development in biometrics on mobile phone[1] Numerous types of biometrics hold the potentials of being implemented onmobile phones. According to the different types of signals needed to be collected for feature extraction, applicable biometric methods can be classified into the imaging type, mechanical type and electrical type. The imaging type includes, but is not limited to the recognition of face, teeth and palm print in addition to fingerprint and iris, utilizing images captured by the camera embedded in the mobile phone. The mechanical type involves voice, heart sound using microphones and blood pressure by specific and miniaturized sensors attached to the mobile phone. Not only ECG can be used in mobile biometrics, the electroencephalography (EEG) identification also has applicability in this new area. The mobile phone based biometrics is also developing towards a multimodal functionality, which combines several biometric recognition methods to provide more reliable and flexible identification and authentication. Promising applications include personal privacy security, ecommerce, mobile bank transactions, e-health technology, etc. A grand outlook of future development in mobile phone based biometrics is outlined in the diagram below:
12. CONCLUSION
In this Paper, we study how the mobile phone can be used in biometrics. This versatile technique has so far proven to be a unique and promising participant in the areas of biometrics. Not only can mobile phone deliver successful solutions in the traditional biometric arenas of human identification and authentication, it has also been instrumental in securing the resource-constrained body sensor networks for health care applications in an efficient and practical manner. At the same time, there remain many challenges to be addressed and a lot more new technologies to be explored and developed. Before successful consumer-ready products are available, a great deal of research and development is still needed to improve all aspects of the mobile phone based biometric system. With a modicum of expectation, it is hoped that this chapter will play a part in further stimulating the research momentum on the mobile phone based biometrics. The paper concludes that the mobile multibiometrics can be embedded in mobile phone. Phone is cost effective since no special hardware is required and is Page 247
11. OUTLOOK OF FUTURE DEVELOPMENT IN MOBILE PHONES
Volume 2, Issue 2 March April 2013
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS)
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.com Volume 2, Issue 2, March April 2013 ISSN 2278-6856
highly secure. Thus, this mobile phone if it becomes a reality will provide more secure e-Business and ETransactions.[2] REFERENCES [1] Shuo Wang and Jing Liu , Department of Biomedical Engineering, School of Medicine, Tsinghua University, P. R.China Biometrics on Mobile Phone www.intechopen.com [2] Informatica Economic vol. 13, no. 1/2009 Biometric Security for Cell Phones [3] Nimalan Solayappan and Shahram Latifi, Department of Electrical engineering, University of Nevada at Las Vegas, USA, A Survey of Unimodal Biometric Methods [4] International Conference on Telecommunication Technology and Applications, Kounoudes et al., 2006, Voice Biometric Authentication for Enhancing Internet Service Security, pp. 10201025, with permission from IEEE. [5] Bao, X.; Wang, J. & Hu, J. (2009). Method of Individual Identification based on Electroencephalogram Analysis. Proceedings of 2009 International Conference on New Trends in Information and Service Science, pp. 390- 393, ISBN 978-0-7695-3687-3, Beijing, P.R.China, June 9-July 2, 2009. [6] Snapshots of fingerprint security - Pro (retrieved from company release news [http://itunes.apple.com/us/app/fingerprint-securitypro/id312912865?mt=8) [7] Reprinted from Proceedings of 2006 2nd International Conference on Telecommunication Technology and Applications, Kounoudes et al., 2006, Voice Biometric Authentication for Enhancing Internet Service Security, pp. 1020-1025, with permission from IEEE [8] (OKI introduces Japans first iris recognition for camera-equipped mobile phones and PDAs, In: OKI Press Releases, 27.11.2006, Available from http://www.oki.com/en/press/2006/z06114e.html)
Volume 2, Issue 2 March April 2013
Page 248
You might also like
- Biomatric in Square E-Transaction: Bachelor of Computer ApplicationDocument27 pagesBiomatric in Square E-Transaction: Bachelor of Computer ApplicationRinesh GhoriNo ratings yet
- Chapter-1: Finger Print Based Security System Using IOTDocument19 pagesChapter-1: Finger Print Based Security System Using IOTAjith ReddyNo ratings yet
- Security by Biometric AuthenticationDocument8 pagesSecurity by Biometric AuthenticationGurudatt KulkarniNo ratings yet
- Bio Metrics AbstractDocument3 pagesBio Metrics AbstractSupraja RamanNo ratings yet
- Image Processing in Biometric and Recognition: M.IndumathiDocument9 pagesImage Processing in Biometric and Recognition: M.IndumathiindumathiNo ratings yet
- Criminal FinalDocument79 pagesCriminal FinalAnuj GuptaNo ratings yet
- Presented By: Biometric Technology To DistinctlyDocument13 pagesPresented By: Biometric Technology To Distinctlymanikumar147No ratings yet
- Bio-Touchpass Efficient Password Mechanism To Overcome Spyware AttacksDocument9 pagesBio-Touchpass Efficient Password Mechanism To Overcome Spyware AttacksIJRASETPublicationsNo ratings yet
- Bio Metrics TechnologyDocument4 pagesBio Metrics TechnologyVenu GopalNo ratings yet
- Bio Metrics in Secure E-TransactionDocument12 pagesBio Metrics in Secure E-Transactionnityanarla100% (4)
- Fingerprint Recognition Using MATLAB PDFDocument74 pagesFingerprint Recognition Using MATLAB PDFtiwaririshi681No ratings yet
- Sandeep Kumar S (1CB11SCS14) 1 Year M.Tech (CSE)Document29 pagesSandeep Kumar S (1CB11SCS14) 1 Year M.Tech (CSE)Angelica SanchezNo ratings yet
- Black BookDocument21 pagesBlack Bookदेवेश सिंह राजपूतNo ratings yet
- Final Lekha ReportDocument25 pagesFinal Lekha ReportUma BusireddyNo ratings yet
- Preventing Spoofing Attacks in Mobile Banking Based On User Input Pattern - Based AuthenticationDocument5 pagesPreventing Spoofing Attacks in Mobile Banking Based On User Input Pattern - Based AuthenticationInternational Organization of Scientific Research (IOSR)No ratings yet
- Biometrics - An AuthenticationDocument24 pagesBiometrics - An AuthenticationrenjythNo ratings yet
- Source 4. Advantages and Disadvantages of BiometricsDocument3 pagesSource 4. Advantages and Disadvantages of Biometricsthecouncil365No ratings yet
- Fingerprint Based Ignition System 01Document30 pagesFingerprint Based Ignition System 01பாலாஜி சிவா86% (7)
- Biometric Seminar ReportDocument15 pagesBiometric Seminar ReportAbhishekNo ratings yet
- Biometric and Information SecurityDocument3 pagesBiometric and Information SecurityAli Ghalehban - علی قلعه بانNo ratings yet
- Ijet V4i3p48 PDFDocument8 pagesIjet V4i3p48 PDFInternational Journal of Engineering and TechniquesNo ratings yet
- Introduction To Biometrics - TextoDocument4 pagesIntroduction To Biometrics - TextoEstefanía R. BoschNo ratings yet
- Multi-Modal Biometric Authentication and Secure TRDocument5 pagesMulti-Modal Biometric Authentication and Secure TRmshashank8867No ratings yet
- Computer Research: The Rizal Memorial Colleges IncDocument7 pagesComputer Research: The Rizal Memorial Colleges IncJainaa JoyceNo ratings yet
- Bio MetricsDocument12 pagesBio Metricsapi-19799369No ratings yet
- Atm Using Two Factor AuthenticationDocument42 pagesAtm Using Two Factor AuthenticationAjewole Eben TopeNo ratings yet
- Abstract On BiometricsDocument9 pagesAbstract On BiometricsBleu Oiseau100% (1)
- What Is Digital Image Processing?Document14 pagesWhat Is Digital Image Processing?12161227No ratings yet
- Seminartopics - Info Seminar ReportDocument24 pagesSeminartopics - Info Seminar ReportSaranya JSNo ratings yet
- BiometricsDocument23 pagesBiometricsanshul_allNo ratings yet
- WP Bio Metrics enDocument4 pagesWP Bio Metrics enCarlo ColombiniNo ratings yet
- BiometricsDocument7 pagesBiometricsLakshmi Priyanka MaruvadaNo ratings yet
- Biometric Recognition: Personal Identification TechniqueDocument5 pagesBiometric Recognition: Personal Identification TechniqueZatin GuptaNo ratings yet
- Bio MetricsDocument9 pagesBio MetricsarulbenjaminchandruNo ratings yet
- BiometricDocument25 pagesBiometricRama KrishnaNo ratings yet
- Smart ATM Pin Recovery and Secured ATM Transactions Based On Fingerprint IdentificationDocument44 pagesSmart ATM Pin Recovery and Secured ATM Transactions Based On Fingerprint IdentificationKanika Seth100% (1)
- Design and Implementation of E-Passport Scheme Using Cryptographic Algorithm Along With Multimodal Biometrics TechnologyDocument10 pagesDesign and Implementation of E-Passport Scheme Using Cryptographic Algorithm Along With Multimodal Biometrics TechnologyijaitjournalNo ratings yet
- Project On Biometrics Security in BankingDocument21 pagesProject On Biometrics Security in BankingJOSEPH100% (1)
- Biometrics in Secure E-Transactions: Fingerprint and Facial Scanning) That Can BeDocument6 pagesBiometrics in Secure E-Transactions: Fingerprint and Facial Scanning) That Can BeShruthi NishaNo ratings yet
- Jurnal 5 Biometric - SecurityDocument6 pagesJurnal 5 Biometric - SecurityMarhayu H. RasanNo ratings yet
- Biometric Report1Document29 pagesBiometric Report1Sachin BhartiNo ratings yet
- Fin ReportDocument19 pagesFin ReportSoulanki KunduNo ratings yet
- Design and Develop Authentication in Electronic Payment Systems Based On IoT and BiometricDocument10 pagesDesign and Develop Authentication in Electronic Payment Systems Based On IoT and BiometricTELKOMNIKANo ratings yet
- Chapter 1 Pr1Document12 pagesChapter 1 Pr1Gem Cyrus Bituin LaraNo ratings yet
- Biometrics Based Security System Using Arduino: Research PaperDocument22 pagesBiometrics Based Security System Using Arduino: Research Paperendryas zewduNo ratings yet
- Biometrics and Standards: ITU-T Technology Watch Report December 2009Document24 pagesBiometrics and Standards: ITU-T Technology Watch Report December 2009Vani_AjayNo ratings yet
- IT Security: The Basics: The Importance of Effective Security To Your BusinessDocument7 pagesIT Security: The Basics: The Importance of Effective Security To Your Businessagkoli30No ratings yet
- Biometrics in Secure E-TransactionDocument4 pagesBiometrics in Secure E-TransactionREx Ethics100% (1)
- Olade2018 PDFDocument8 pagesOlade2018 PDFAmmar MohammedNo ratings yet
- FR-PAY-A Secure Approach For PaymentDocument7 pagesFR-PAY-A Secure Approach For PaymentVIVA-TECH IJRINo ratings yet
- Biometrics ReportDocument16 pagesBiometrics ReportKaran KadakiaNo ratings yet
- Biometric SecurityDocument6 pagesBiometric SecurityNaeem KhanNo ratings yet
- A Comparative Analysis of Biometrics Types: Literature ReviewDocument11 pagesA Comparative Analysis of Biometrics Types: Literature ReviewMohammad AshharNo ratings yet
- With The Increasing Use of Electronics and ElectronicDocument35 pagesWith The Increasing Use of Electronics and ElectronicArushi MishraNo ratings yet
- Fingerprint Recognition With Embedded Cameras On Mobile PhonesDocument12 pagesFingerprint Recognition With Embedded Cameras On Mobile PhonesLionel BoopathiNo ratings yet
- Intrinsic Traits Computer Science Identity Access Management Access Control SurveillanceDocument4 pagesIntrinsic Traits Computer Science Identity Access Management Access Control SurveillanceSiva BhaskarNo ratings yet
- Detection of Malicious Web Contents Using Machine and Deep Learning ApproachesDocument6 pagesDetection of Malicious Web Contents Using Machine and Deep Learning ApproachesInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Study of Customer Experience and Uses of Uber Cab Services in MumbaiDocument12 pagesStudy of Customer Experience and Uses of Uber Cab Services in MumbaiInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- THE TOPOLOGICAL INDICES AND PHYSICAL PROPERTIES OF n-HEPTANE ISOMERSDocument7 pagesTHE TOPOLOGICAL INDICES AND PHYSICAL PROPERTIES OF n-HEPTANE ISOMERSInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- An Importance and Advancement of QSAR Parameters in Modern Drug Design: A ReviewDocument9 pagesAn Importance and Advancement of QSAR Parameters in Modern Drug Design: A ReviewInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- The Mexican Innovation System: A System's Dynamics PerspectiveDocument12 pagesThe Mexican Innovation System: A System's Dynamics PerspectiveInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Analysis of Product Reliability Using Failure Mode Effect Critical Analysis (FMECA) - Case StudyDocument6 pagesAnalysis of Product Reliability Using Failure Mode Effect Critical Analysis (FMECA) - Case StudyInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Soil Stabilization of Road by Using Spent WashDocument7 pagesSoil Stabilization of Road by Using Spent WashInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Performance of Short Transmission Line Using Mathematical MethodDocument8 pagesPerformance of Short Transmission Line Using Mathematical MethodInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Design and Detection of Fruits and Vegetable Spoiled Detetction SystemDocument8 pagesDesign and Detection of Fruits and Vegetable Spoiled Detetction SystemInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Staycation As A Marketing Tool For Survival Post Covid-19 in Five Star Hotels in Pune CityDocument10 pagesStaycation As A Marketing Tool For Survival Post Covid-19 in Five Star Hotels in Pune CityInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- A Deep Learning Based Assistant For The Visually ImpairedDocument11 pagesA Deep Learning Based Assistant For The Visually ImpairedInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- A Comparative Analysis of Two Biggest Upi Paymentapps: Bhim and Google Pay (Tez)Document10 pagesA Comparative Analysis of Two Biggest Upi Paymentapps: Bhim and Google Pay (Tez)International Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Synthetic Datasets For Myocardial Infarction Based On Actual DatasetsDocument9 pagesSynthetic Datasets For Myocardial Infarction Based On Actual DatasetsInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Impact of Covid-19 On Employment Opportunities For Fresh Graduates in Hospitality &tourism IndustryDocument8 pagesImpact of Covid-19 On Employment Opportunities For Fresh Graduates in Hospitality &tourism IndustryInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Ijaiem 2021 01 28 6Document9 pagesIjaiem 2021 01 28 6International Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Design and Manufacturing of 6V 120ah Battery Container Mould For Train Lighting ApplicationDocument13 pagesDesign and Manufacturing of 6V 120ah Battery Container Mould For Train Lighting ApplicationInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Swot Analysis of Backwater Tourism With Special Reference To Alappuzha DistrictDocument5 pagesSwot Analysis of Backwater Tourism With Special Reference To Alappuzha DistrictInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Anchoring of Inflation Expectations and Monetary Policy Transparency in IndiaDocument9 pagesAnchoring of Inflation Expectations and Monetary Policy Transparency in IndiaInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- The Effect of Work Involvement and Work Stress On Employee Performance: A Case Study of Forged Wheel Plant, IndiaDocument5 pagesThe Effect of Work Involvement and Work Stress On Employee Performance: A Case Study of Forged Wheel Plant, IndiaInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- 15062-209 GEMS Percentage MineSchedDocument5 pages15062-209 GEMS Percentage MineSchedmapykNo ratings yet
- HP Vertica 6.1.x Vertica AWSDocument35 pagesHP Vertica 6.1.x Vertica AWSRakesh SinghNo ratings yet
- AN2548Document24 pagesAN2548KrocodileNo ratings yet
- IT Application Controls IcqDocument10 pagesIT Application Controls IcqMohammed OsmanNo ratings yet
- Gatp TcodesDocument2 pagesGatp TcodesDheerajKumarNo ratings yet
- Netapp E5700 Series: Datasheet DatasheetDocument4 pagesNetapp E5700 Series: Datasheet DatasheetNeha SharmaNo ratings yet
- JNCIA Junos P1 - 2012 12 19 PDFDocument100 pagesJNCIA Junos P1 - 2012 12 19 PDFKhaled Gamal100% (1)
- PL-SQL+Exercices+on+Chapter+9+ Procedures+and+FunctionsDocument12 pagesPL-SQL+Exercices+on+Chapter+9+ Procedures+and+FunctionsNtaoleng Leah MofukunyaneNo ratings yet
- Introduction To Neural NetworksDocument51 pagesIntroduction To Neural NetworkssavisuNo ratings yet
- MSC - Acumen 2006 Function DescriptionsDocument676 pagesMSC - Acumen 2006 Function DescriptionsKevinNo ratings yet
- Numerical Methods Test 1Document17 pagesNumerical Methods Test 1Ashley StraubNo ratings yet
- 63dc7ed1010d3c3b8269faf0ba7491d4.txtDocument418 pages63dc7ed1010d3c3b8269faf0ba7491d4.txtali khanNo ratings yet
- Report Zppbapi Upload Indep ReqsDocument9 pagesReport Zppbapi Upload Indep ReqsLo Mejor MedellinNo ratings yet
- Cybersecurity For Medical Devices: Three Threads IntertwinedDocument23 pagesCybersecurity For Medical Devices: Three Threads IntertwinedGuevarita GuevaritaNo ratings yet
- Manual EclipseDocument40 pagesManual EclipseElcio Dias Junior100% (2)
- Navigating in R12 Oracle ApplicationsDocument37 pagesNavigating in R12 Oracle ApplicationsJenner Patrick Lopes BrasilNo ratings yet
- 1z0 1080Document5 pages1z0 1080suman dNo ratings yet
- Advanced Generic Handler ASHX - CodeProject®Document4 pagesAdvanced Generic Handler ASHX - CodeProject®Tanzeel_clNo ratings yet
- Blackhat 2015Document65 pagesBlackhat 2015hungbkpro90No ratings yet
- Huffman CodeDocument51 pagesHuffman CodeHoney LaraNo ratings yet
- 5.4 Does Opencobol Support Any SQL Databases?: Chapter 5. Features and ExtensionsDocument5 pages5.4 Does Opencobol Support Any SQL Databases?: Chapter 5. Features and ExtensionshunterpyNo ratings yet
- Final Os LabDocument103 pagesFinal Os LabgunaNo ratings yet
- Workflow Basic Config and ConceptsDocument87 pagesWorkflow Basic Config and ConceptsJaiNo ratings yet
- Design and Analysis of AlgorithmsDocument37 pagesDesign and Analysis of AlgorithmsSwapnil agrawalNo ratings yet
- CS 313 Introduction To Computer Networking & Telecommunication Data Link Layer Part II - Sliding Window ProtocolsDocument39 pagesCS 313 Introduction To Computer Networking & Telecommunication Data Link Layer Part II - Sliding Window ProtocolsJainam TalsaniaNo ratings yet
- Boot Images and Distribution Point Configuration For OSD in SCCM 2012 R2Document7 pagesBoot Images and Distribution Point Configuration For OSD in SCCM 2012 R2MdSameerNo ratings yet
- Lecture 1 Introduction To Information TechnologyDocument40 pagesLecture 1 Introduction To Information TechnologyZain Raza100% (7)
- Fmri Data Analysis MatlabDocument18 pagesFmri Data Analysis MatlaboumeiganNo ratings yet
- Macro Processors Chap4Document11 pagesMacro Processors Chap4Anonymous jpeHV73mLzNo ratings yet
- OPC Complex Data Working Group OPC Complex Data Specification Version 1.00Document47 pagesOPC Complex Data Working Group OPC Complex Data Specification Version 1.00fatihaNo ratings yet