Professional Documents
Culture Documents
Foxboro Mesh Topology PDF
Uploaded by
iyyaniOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Foxboro Mesh Topology PDF
Uploaded by
iyyaniCopyright:
Available Formats
I/A Series HARDWARE
Product Specifications
PSS 21H-7C2 B3
The MESH Control Network Architecture
The MESH control network is a switched Ethernet network based on IEEE 802.3u (Fast Ethernet) and IEEE 802.3z (gigabit Ethernet) standards.
FEATURES
The MESH control network offers:
System scalability by interconnecting Ethernet
Modular uplinks to high-speed backbones using
switches with 8-ports or more for connecting stations in a linear, ring, star, inverted tree or modified tree network topology
Ethernet switches connected in a MESH
1 Gb 1000Base-T, 1000Base-SX, 1000Base-LX/LH 1000Base-LX, 1000Base-BX and 1000Base-ZX standards
Software in every station to manage redundant
Ethernet ports in response to network faults
Rapid Spanning Tree Protocol (RSTP) which
configuration; up to 1920 I/A Series stations
Support for Fast Ethernet (100 Mbps) and Gigabit
manages redundant paths, prevents loops, and provides high speed convergence time for a network
High speed response to network and station
(uplink only) Ethernet (1000 Mbps)
faults to provide a highly reliable redundant network
PSS 21H-7C2 B3 Page 2
Network management and configuration via local
port or Web access for various switches
Network configuration for Virtual Local Area
Networks (VLANs), separating the MESH Network into multiple segments. A total of six VLANs can be configured. VLANs configured for non-I/A Series communication can only be configured for TCP and UDP protocol use.
With the I-series switch, migration of The MESH
The MESH control network architecture integrates powerful control stations and workstations in a 100 Mb/1 Gb Ethernet network. These control stations, workstations and networks comprise scalable systems for process monitoring, process control and integration with industrial information management. High speed, coupled with redundancy and peer-topeer characteristics, provides high performance and availability. Redundant station interfaces to Ethernet switches further ensure secure communications between the stations.
control network into industrial environments with temperatures ranging from -40C to 60C (-40F to 140F) and into hazardous locations rated for ISA12.12.01 Class I, Div. 2 A-D55022B Class A
Full duplex operation based on the IEEE 802.3
SWITCHED ETHERNET CHARACTERISTICS
Standard Fast Ethernet switches and fiber optic/copper cabling provide versatile, low-cost solutions for building Ethernet networks using industry standard protocols. The 8-port or larger managed Ethernet switches used in The MESH control network allow connection of multiple control stations, workstations and other Ethernet switches.
standards
System Management software for monitoring the
health of The MESH control network and managing equipment in the system.
OVERVIEW
The MESH control network consists of a number of Ethernet switches connected in one of two MESH configurations - Standard and Security Enhanced. Both configurations of The MESH control network allow very high availability by providing redundant data paths and eliminating single points of failure. The MESH control network is designed to provide multiple communication paths between any two devices or stations connected to the network. This network architecture reduces network complexity, cost, and maintenance requirements. The flexibility of the architecture allows you to design a network configuration that fits the needs of the control system. Configurations can be as simple as a workstation and controller connected with a single switch, or as complex as a multi-switch, fully meshed Ethernet network, communicating at speeds up to 1 gigabit per second.
SECURITY ENHANCED CONFIGURATION FEATURES
The Security Enhanced Configuration provides additional features beyond those of the Standard Configuration. The Security Enhanced Configuration of The MESH control network offers improvements in network security, Loop Detection and many additional features not offered in the Standard Configuration. Refer to Additional Features of the Security Enhanced Configuration on page 14 for more details. The Security Enhanced Configuration deploys specific network topologies and switch configurations that allow for advanced network loop detection in the event of an RSTP and/or data loop (storm) failure. This advanced network loop detection minimizes the potential for a single point of failure that will degrade communications between devices in the network.
PSS 21H-7C2 B3 Page 3
Deploying the advanced network loop detection is accomplished by carefully designing the network and correctly deploying the Loop Detection Policy (LDP) algorithms required for the network design, and by following the network configuration requirements provided in The MESH Control Network Architecture Guide (B0700AZ) and The MESH Control Network Operation and Switch Installation and Configuration Guide (B0700CA).
Security Enhanced Configuration
Linear Star Inverted tree Modified inverted tree Each topology listed has unique features and the one chosen for a particular control network depends on the specific requirements of the site or installation. The following diagrams provide examples of the different topologies as well as recommendations on where they might be used. NOTE All graphics of switches and media converters in this Product Specification Sheet are intended as generic illustrations of networking concepts and do not necessarily reflect the currently offered products. For the current product line of switches, refer to The MESH Control Network Ethernet Equipment (PSS 21H-7C3 B4).
NETWORK TOPOLOGIES
The Standard, and Security Enhanced Configurations of The MESH control network are available. These switches are listed in The MESH Control Network Operation and Switch Installation and Configuration Guide (B0700CA). The Security Enhanced version takes advantage of features available in higher-end Ethernet equipment to provide additional security features. There are several basic MESH control network topologies supported by the I/A Series system in each of the Standard and Security Enhanced Configurations. These are:
Standard Configuration
Linear Ring Star Inverted tree Modified inverted tree
PSS 21H-7C2 B3 Page 4
Linear Configuration
The linear configuration is appropriate for a small, two switch network, as shown in Figure 1. In this example a failure of any one component in the network does not affect the operation of the remaining components due to switch redundancy.
Large chassis switches with hundreds of ports can be used in a linear configuration to create a large control system.
Figure 1. Linear Topology
PSS 21H-7C2 B3 Page 5
Ring Topology
This topology is suited for networks containing three to seven switches. As shown in Figure 2, each switch has connections to the two adjacent switches. The primary and the backup root switch must be connected. In the event of a failed switch, the ring is broken and the network assumes the characteristics of the linear topology shown in Figure 1. There is a limit of seven (7) switches between any two devices on the network, a limit imposed by the I/A Series system
Figure 2 illustrates a network composed of six managed switches configured in a ring. A network in this configuration is able to maintain its integrity during the failure of:
a cable to a CP270 or workstation interconnecting cables within the network a switch within the network
The ring topology cannot be configured with the Security Enhanced Configuration. When designing Security Enhanced Configurations, use one of its four supported topologies.
Figure 2. Ring Topology
PSS 21H-7C2 B3 Page 6
Star Topology
The star topology is the preferred topology for all medium and large sized networks. In a star topology, the switches at the outside edge of the network have connections to each of the two root switches. The root switches are connected to each other and to the edge switches. Redundant data paths allow the network to continue to operate if any one component fails. Figure 3 illustrates a star network containing ten edge switches and two root switches. In a Standard
Configuration star topology, the switch can support up to 190 edge switches using 1 Gb uplinks, depending on the switch blade type configuration. In a Security Enhanced Configuration star topology, up to 190 edge switches can be connected to the Chassis switches using 1 Gb uplinks. (Refer to The MESH Control Network Architecture Guide (B0700AZ) for the number of switch types allowed in a network.) An inverted tree topology can be considered if there are a larger number of edge switches required (up to 500 total switches).
Figure 3. Star Topology
PSS 21H-7C2 B3 Page 7
Inverted Tree Topology
The inverted tree topology is suited for very large networks with specific physical constraints. In this topology the switches are arranged in tiers, with the root switches in the top tier and up to three tiers below them. The root switches have redundant connections between them, and the other switches each have a connection to two of the switches in the tier above them. An inverted tree network topology is illustrated in Figure 4 on page 8.
When deployed in a Security Enhanced Configuration, all switches within the network must be switch types that support Loop Detection (LDP). The switches available to each Configuration are listed in The MESH Control Network Operation and Switch Installation and Configuration Guide (B0700CA). There can be no more than four-tiers of switches (including the root) in order to comply with the I/A Series system requirement limiting the number of switches between devices to seven.
PSS 21H-7C2 B3 Page 8
Primary Root TIER 1 Managed Switches
Backup Root
Note: Primary and Backup Root Switches have two connections.
Managed Switches
TIER 2 Gigabit Ethernet over Fiber Uplink Ports Gigabit Ethernet over Fiber Uplink Ports
TIER 3
TIER 4
Control Processor
Workstation
Figure 4. Inverted Tree Topology
PSS 21H-7C2 B3 Page 9
Modified Inverted Tree Topology
The modified inverted tree topology is suited for very large enhanced networks with specific physical constraints and requirements. The modified inverted tree topology allows for standard qualified (lower cost) switches to be utilized at the outer edge, which allows for larger networks to be deployed at a lower cost. In this topology, the switches are arranged in tiers, with the root switches in the top tier with up to three tiers below them. The root switches (tier 1) are the only switches in the network that have connections between switches on the same tier; all other switches have two connections to switches in the tiers above them. All outer edge switches are interfaced to the network on different tiers (e.g., tier 3 and tier 4). By doing this, all end devices with redundant connections interface to the network on different tiers. A modified inverted tree network topology is illustrated in Figure 5. There can be no more than four-tiers of switches (including the root) in order to comply with the I/A Series system requirement limiting the number of switches between devices to seven.
PSS 21H-7C2 B3 Page 10
Primary Root
Backup Root
TIER 1 Core Switches Core Switches
TIER 2 Gigabit Ethernet over Fiber Uplink Ports Gigabit Ethernet over Fiber Uplink Ports
TIER 3
TIER 4
Control Processor
Figure 5. Modified Inverted Tree Topology
PSS 21H-7C2 B3 Page 11
THE MESH CONTROL NETWORK CONFIGURATION EXAMPLE
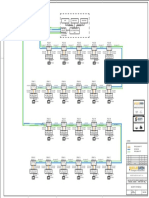
The MESH control network utilizes Fast Ethernet switches which are configured to form a highly robust redundant network. Figure 6 shows an example with several I/A Series stations connected redundantly to The MESH control network. Workstations are also redundantly connected to the Fast Ethernet switches. The Field Control Processor 270 (FCP270) is a single or fault-tolerant control processor that mounts on a baseplate and provides a communication interface between the FBMs and The MESH control network.The FCP270 connects to The MESH control network via standard fiber optic 100 Mbps Fast Ethernet.
The Z-Module Control Processor 270 (ZCP270) is a single or fault-tolerant control processor that mounts in a 1x8 or 2x8 mounting structure.The ZCP270 connects to The MESH control network via fiber optic cables. The Fieldbus Communications Module (FCM100Et or FCM100E) provides interface between the ZCP270 and the FBMs. The FCM100Et and FCM100E are available as a single or redundant modules. Fieldbus Modules (FBMs) serve as an interface between the field devices and the I/A Series control station. They perform necessary data conversion, providing full support for analog measurement, discrete sensing, analog or discrete control and digital communication.
PSS 21H-7C2 B3 Page 12
ZCP270 Information Network WorkstationS
Splitter/ COMBINERS
Ethernet SwitcheS
The MESH Control Network
SPLITTER/COMBINER (Not USed with FCM100E) DIN RAIL BASEPLATE FCP270 FBM FCM100Et or FCM100E FBM
DIN RAIL BASEPLATE to/From Process TO/FROM PROCESS
Figure 6. The MESH Control Network Example
PSS 21H-7C2 B3 Page 13
FOR MORE INFORMATION
For additional information describing The MESH control network, refer to The MESH Control Network Ethernet Equipment (PSS 21H-7C3 B4). For more information on designing The MESH control network, refer to The MESH Control Network Architecture Guide (B0700AZ). F U N C T I O N A L S P E C I F I C AT I O N S
Number of I/A Series Stations
I/A Series stations including Ethernet switches, 1920 maximum (FCM100Et and FCM100E not included in count). Up to 500 switches.
I/A Series Station Switchover Time
Typical, less than 1 second Maximum, 3 seconds
Protocols Used
IEEE 802.1w Rapid Spanning Tree Protocol (RSTP), IEEE 802.1d Spanning Tree, IEEE 802.3 Ethernet, IEEE 802.3u Fast Ethernet, IEEE 802.3z Gigabit Ethernet,
Number of IP Addresses
10,000 maximum includes switches, controllers, workstations, ATSs, FCM100Ets and FCM100Es
Standards Supported
Full duplex operation, 100Mbps copper and fiber cables, modular uplinks using 100Mb 100Base-FX and, modular uplinks using 1 Gb 1000Base-T, 1000Base-SX, 1000Base-LX/LH, 1000Base-LX and 1000Base-ZX, 1000Base-BX standards
Loop Protect Algorithm
The Loop Protect Algorithm (LPA) feature is supported on both the Standard and Security Enhanced Configurations for all topologies on The MESH network. LPA prevents loop formations within a network when redundant paths are utilized. LPA requires ports to receive type 2 BPDUs (RSTP/MSTP) on point-to-point inter-switch links (ISLs) before their states are allowed to switch to the forwarding state. This function prevents a loop within the network similar to LDP on the Security Enhanced Configuration but with LPA, both upstream and downstream facing ports are protected. This feature is deployable across all switch types in the network with the exception of V-series switch (P0972WP and P0972YC). Refer to The MESH Control Network Operation, and Switch Installation and Configuration Guide (B0700CA) for deployment rules. LPA operates as a per port, per MST instance feature. It should only be set on inter-switch links that support this feature. LPA functionality does not protect root level ISL bridging ports. LPA does not protect the network against spanning tree events at the root level. It is recommended that LDP still be deployed across network when requiring sub-second failover.
Virtual Local Area Networks (VLANs)
Six configurable VLANs, VLAN 2 is dedicated for I/A Series communications only, VLANs 3-7 are supported with the I/A Series system when configured for use only with the TCP and UDP protocols. When VLANs are configured, VLAN 1 is not used.
Number of Ethernet Switches Between Any Two Stations
Seven maximum
Speeds Supported
Fast Ethernet (100 Mbps) and uplink Gigabit Ethernet (1000 Mbps)
Network Failover Time
Typically a failover time of less than 1 second is achievable using fast ethernet switches qualified and supplied by Invensys and configured in accordance with I/A Series documentation.
PSS 21H-7C2 B3 Page 14
F U N C T I O N A L S PE CI F I C AT I O N S ( C O N T I N U E D )
Additional Features of the Security Enhanced Configuration
RATE LIMITING This function is to limit the rate of inbound or outbound traffic on the S-Series devices on a per port/priority basis. The allowable range for the rate limiting is 64 kilobytes per second minimum up to the maximum transmission rate allowable on the interface type. Rate limit is configured for a given port and list of priorities. The list of priorities can include one, some, or all of the eight 802.1p priority levels. Once configured, the rate of all traffic entering or leaving the port with the priorities configured to that port is not allowed to exceed the programmed limit. If the rate exceeds the programmed limit, frames are dropped until the rate falls below the limit. ADVANCED PORT QOS RATE LIMITING A port priority Port Quality of Service (QoS) Rate Limiting can be set on each port ranging from 07, with 0 being the lowest priority. As the port (VLAN) receives packet frames, the port will assign a priority according to the default priority setting on the port. Advanced port QoS Rate Limiting utilizes the Class of Service (CoS) features, which allows you to assign mission-critical data to higher priority through the device by delaying less critical traffic during periods of congestion. The higher priority traffic through the device is serviced first before lower priority traffic. The CoS capability of the device is implemented by a priority queueing mechanism, QoS. The CoS allows you to define eight priorities (0 through 7) and QoS allows you to define up to four transmit queues (0-3) of traffic for each network device port.
ADVANCED PORT TXQ RATE LIMITING The Advanced Port TxQ rate limiting takes the port QoS Rate Limiting one step further by setting a bandwidth limit on to the transmit queue. Each of the four transmit queues (0-3) can be assigned a bandwidth percentage of the port ranging from 0 to 100%. The four transmit queue must total 100%. For example, if all ports in VLAN 2 are assigned a priority of 7, and priority 7 transmit queue is set to 3, and transmit queue 3 is set to 51%, then frames received through a port on that VLAN are classified as a priority 7 with a priority queue of 3 and allocated 51% of the bandwidth. All packets with a lower priority will transmit after this packet and as the network becomes congested this packet/port/VLAN will be allotted at least 51% of the bandwidth.
PSS 21H-7C2 B3 Page 15
P H Y S I C A L S P E C I F I C AT I O N S
Cable Lengths
INTERCONNECTING STATIONS OR ETHERNET SWITCHES CAT5 100Base-TX or 1000Base-T; 100 m (328 ft) maximum Fiber Optic, 100Base-FX 100Base-FX
MMF, 2 km (6,560 ft) maximum
TOTAL CONNECTION LENGTH ALLOWED BETWEEN SWITCHES Simplex-Single mode fiber (S-SMF) 120 km (74.6 mi) maximum Single mode fiber (SMF) 80 km (49.6 mi) maximum Multimode fiber (MMF) 2 km (6,560 ft) maximum
Fiber Optic, 1000Base-X 1000Base-SX
MMF, 275 m (902 ft) maximum
1000Base-LX/LH
MMF, 2 km (6,560 ft) maximum
1000Base-LX
MMF, 275 m (902 ft) maximum SMF, 10 km (6.2 miles) maximum
1000Base-ZX
SMF, 80 km (49.6 miles) maximum
1000Base-BX
Simplex-SMF, up to 10 km (6.2 miles), 40 km ( 24.8 miles) and 120 km (74.6 miles) maximum depending on the module
PSS 21H-7C2 B3 Page 16
Invensys Operations Management 5601 Granite Parkway Suite 1000 Plano, TX 75024 United States of America http://iom.invensys.com
Invensys, Foxboro, I/A Series, and the Invensys logo are trademarks of Invensys plc, its subsidiaries, and affiliates. All other brands and product names may be the trademarks of their respective owners. Copyright 2004-2012 Invensys Systems, Inc. All rights reserved. Unauthorized duplication or distribution is strictly prohibited.
Global Customer Support Inside U.S.: 1-866-746-6477 Outside U.S.: 1-508-549-2424 or contact your local Invensys representative. Website: http://support.ips.invensys.com
MB 21A
0812
You might also like
- FoxView SoftwareDocument12 pagesFoxView SoftwareRobert Villavicencio100% (1)
- 2PAA111693-610 A en System 800xa 6.1 Post InstallationDocument156 pages2PAA111693-610 A en System 800xa 6.1 Post Installationershivkumar2002No ratings yet
- 6th Central Pay Commission Salary CalculatorDocument15 pages6th Central Pay Commission Salary Calculatorrakhonde100% (436)
- 6th Central Pay Commission Salary CalculatorDocument15 pages6th Central Pay Commission Salary Calculatorrakhonde100% (436)
- Honeywell FSCDocument30 pagesHoneywell FSCManoj Kage100% (1)
- Pactware Manual 1Document240 pagesPactware Manual 1bangiful100% (1)
- Foxboro PIDA (Low)Document75 pagesFoxboro PIDA (Low)Cecep AtmegaNo ratings yet
- InFusion Engineering EnvironmentCourse5612 Participant GuideDocument440 pagesInFusion Engineering EnvironmentCourse5612 Participant GuideJayesh BhadjaNo ratings yet
- Basic Overview of Foxboro IA SeriesDocument8 pagesBasic Overview of Foxboro IA SeriesvelusunilNo ratings yet
- B0700ay BDocument44 pagesB0700ay BRodrigoCastilloAcostaNo ratings yet
- b0193wq - P - System DefnitionDocument80 pagesb0193wq - P - System DefnitionsaratchandranbNo ratings yet
- PGM Based Profibus - UpdatedDocument58 pagesPGM Based Profibus - UpdatedpianuelsNo ratings yet
- Foxboro Ia ManualDocument99 pagesFoxboro Ia ManualLuis Orlando Rios MorenoNo ratings yet
- I/A Series System Foxview™ and Foxdraw™ Software V10.2.1 Release NotesDocument68 pagesI/A Series System Foxview™ and Foxdraw™ Software V10.2.1 Release NotespianuelsNo ratings yet
- Security Implementation User's Guide For I/A Series and Foxboro Evo WorkstationsDocument134 pagesSecurity Implementation User's Guide For I/A Series and Foxboro Evo Workstationsabdel taibNo ratings yet
- B0700be F PDFDocument522 pagesB0700be F PDFsaratchandranb100% (1)
- Skills-Based Assessment (Version A) : TopologyDocument5 pagesSkills-Based Assessment (Version A) : TopologyYagui100% (1)
- 4.2.2.7 Lab - Building An Ethernet Crossover CableDocument6 pages4.2.2.7 Lab - Building An Ethernet Crossover Cablerezhablo100% (2)
- OPC Service Manual-V1.7Document106 pagesOPC Service Manual-V1.7Robert VillavicencioNo ratings yet
- 03A How To Operate CCC S3 Antisurge Control PDFDocument27 pages03A How To Operate CCC S3 Antisurge Control PDFingezoneNo ratings yet
- TRICON Product Spec PDFDocument78 pagesTRICON Product Spec PDFUdaya Kumar Krishnan100% (1)
- Foxboro Control Software User Documentation 3.0Document1 pageFoxboro Control Software User Documentation 3.0Luis AngelNo ratings yet
- FoxBoro IA Series PLBDocument33 pagesFoxBoro IA Series PLBUsamaTariq0% (1)
- Tristation 4.16 Developers GuideDocument1,108 pagesTristation 4.16 Developers GuidePurnama Putra PontohNo ratings yet
- Trisen TS160 TrainingDocument105 pagesTrisen TS160 TrainingGian ErzhaNo ratings yet
- B0700BG BDocument64 pagesB0700BG BRodrigoCastilloAcostaNo ratings yet
- Invensys Foxboro PDFDocument20 pagesInvensys Foxboro PDFPustinjak SaharicNo ratings yet
- Appearance Object Editor User's Guide: Foxboro Evo Process Automation SystemDocument50 pagesAppearance Object Editor User's Guide: Foxboro Evo Process Automation Systemjesus lopezNo ratings yet
- Manual For IA Controlers V6Document60 pagesManual For IA Controlers V6Bharadwaj SubramanianNo ratings yet
- Hardware ConfigDocument74 pagesHardware ConfigLuis AngelNo ratings yet
- B0193ax3 N (Function Block)Document712 pagesB0193ax3 N (Function Block)Jack YenNo ratings yet
- b0193mq MDocument148 pagesb0193mq MReinaldo Andres Castillo JopiaNo ratings yet
- FoxRTU SoftwareManualDocument239 pagesFoxRTU SoftwareManualhbahriioNo ratings yet
- DeltaV ModbusTCP AppNoteDocument18 pagesDeltaV ModbusTCP AppNotegcjhaNo ratings yet
- Software Utilities: I/A Series SystemDocument64 pagesSoftware Utilities: I/A Series SystemFrancis RodríguezNo ratings yet
- Bently 3500 To CDocument1 pageBently 3500 To CDenis Jimenez0% (2)
- Mesh ControlDocument130 pagesMesh ControlSaravana Prabhu100% (1)
- TN66Document6 pagesTN66Raja BalasubramaniamNo ratings yet
- 03B How To Operate CCC S3++ Antisurge Control (Compatibility Mode)Document24 pages03B How To Operate CCC S3++ Antisurge Control (Compatibility Mode)elsyakieb100% (1)
- b0700CA LDocument268 pagesb0700CA Lchergui.adelNo ratings yet
- Foxboro DCSDocument11 pagesFoxboro DCSLeni A100% (1)
- DeltaV OPCDocument2 pagesDeltaV OPCZain AliNo ratings yet
- DeltaV Opc MatlabIntegrationDocument12 pagesDeltaV Opc MatlabIntegrationedcocuNo ratings yet
- Foxboro SCADA Master Stations PDFDocument39 pagesFoxboro SCADA Master Stations PDFFlavio AlxNo ratings yet
- B0700ba KDocument392 pagesB0700ba Kabdel taib100% (1)
- Control Load Station B0700ax - JDocument62 pagesControl Load Station B0700ax - JtecnoradsNo ratings yet
- B0750ap - D System ManagerDocument328 pagesB0750ap - D System ManagerSreedhar Avula100% (1)
- b0193wq HDocument68 pagesb0193wq HJúlia KistNo ratings yet
- Bloques 1Document820 pagesBloques 1Robert VillavicencioNo ratings yet
- Control Software v7.1.1 Release Notes: Foxboro Evo Process Automation SystemDocument47 pagesControl Software v7.1.1 Release Notes: Foxboro Evo Process Automation Systemabdel taibNo ratings yet
- DeltaV SIS With Electronic Marshalling Hardware Reference Guide PDFDocument115 pagesDeltaV SIS With Electronic Marshalling Hardware Reference Guide PDFQuayo Deejay100% (1)
- B0700ax WDocument102 pagesB0700ax WBen SahraouiNo ratings yet
- S3 Common FunctionsDocument54 pagesS3 Common Functionsplim5ollNo ratings yet
- Foxboro IA Series DCS PDFDocument6 pagesFoxboro IA Series DCS PDFJean Callata Chura0% (1)
- Archestra IDEDocument468 pagesArchestra IDEalsase100% (3)
- HIMA ElopDocument221 pagesHIMA Elopsendutdut100% (1)
- Cascade ControlDocument28 pagesCascade Controlach_1964No ratings yet
- Foxboro FM242Document16 pagesFoxboro FM242jose luisNo ratings yet
- Rockwell Automation Library of Process P - PIDEDocument70 pagesRockwell Automation Library of Process P - PIDEjuanjovm77No ratings yet
- Flow Measurement: By Square-Edged Orifice Plate Using Corner TappingsFrom EverandFlow Measurement: By Square-Edged Orifice Plate Using Corner TappingsRating: 5 out of 5 stars5/5 (1)
- Wireless Control Foundation: Continuous and Discrete Control for the Process IndustryFrom EverandWireless Control Foundation: Continuous and Discrete Control for the Process IndustryNo ratings yet
- Certified Automation Professional A Complete Guide - 2020 EditionFrom EverandCertified Automation Professional A Complete Guide - 2020 EditionNo ratings yet
- Fieldbus Systems and Their Applications 2005: A Proceedings volume from the 6th IFAC International Conference, Puebla, Mexico 14-25 November 2005From EverandFieldbus Systems and Their Applications 2005: A Proceedings volume from the 6th IFAC International Conference, Puebla, Mexico 14-25 November 2005Miguel Leon ChavezNo ratings yet
- Lead Sheathed CablesDocument22 pagesLead Sheathed CablesYousef Eisa Abdel SalamNo ratings yet
- DralimDocument2 pagesDralimiyyaniNo ratings yet
- DC Polarization CellDocument13 pagesDC Polarization CelliyyaniNo ratings yet
- SamaDocument8 pagesSamalosmoscasbr100% (1)
- Emerson-Valve Sizing Calculations (Traditional Method)Document21 pagesEmerson-Valve Sizing Calculations (Traditional Method)iqtorresNo ratings yet
- Trim Number Chart API ValveDocument2 pagesTrim Number Chart API ValveJuliusMaximus12No ratings yet
- DFFJ Dfgu SSJDocument3 pagesDFFJ Dfgu SSJmehdi227No ratings yet
- MVcables DesignDocument40 pagesMVcables DesigniyyaniNo ratings yet
- Fundamentals of Orifice Measurement Techwpaper PDFDocument9 pagesFundamentals of Orifice Measurement Techwpaper PDFartletNo ratings yet
- Oil in WaterDocument2 pagesOil in WateriyyaniNo ratings yet
- Sarasota RTR900Document2 pagesSarasota RTR900iyyaniNo ratings yet
- DC Ploarisation Cell InstallationDocument10 pagesDC Ploarisation Cell InstallationiyyaniNo ratings yet
- Flare Stack WhitepaperDocument4 pagesFlare Stack WhitepaperiyyaniNo ratings yet
- Partial Stroke Testing ComparisonDocument8 pagesPartial Stroke Testing ComparisonasimozmaNo ratings yet
- Corrosion Guide Instructions: WarningDocument13 pagesCorrosion Guide Instructions: WarningiyyaniNo ratings yet
- Hazardous Area Classification MoxrexDocument48 pagesHazardous Area Classification MoxrexMuhammad Mubashir Hassan100% (4)
- LVCables Design InfoDocument80 pagesLVCables Design InfoiyyaniNo ratings yet
- Hart ConnectionsDocument9 pagesHart ConnectionsiyyaniNo ratings yet
- Marking of Explosion-Protected Equipment: New Ruling in IEC 60079-0, 2007 and EN 60079-0, 2009Document4 pagesMarking of Explosion-Protected Equipment: New Ruling in IEC 60079-0, 2007 and EN 60079-0, 2009iyyaniNo ratings yet
- Industrial Networking IDocument214 pagesIndustrial Networking Ieucae00100% (2)
- 3.5.5 Packet Tracer - Configure DTPDocument8 pages3.5.5 Packet Tracer - Configure DTPUmayra YusoffNo ratings yet
- Troubleshooting Switch Issues: Ethernet LansDocument13 pagesTroubleshooting Switch Issues: Ethernet Lansamapreet.scorpioNo ratings yet
- Bsl1-Ele-032 Security System SLD .Rev 0Document1 pageBsl1-Ele-032 Security System SLD .Rev 0jdzarzalejoNo ratings yet
- Adva FSP 150CC-GE201 Data SheetDocument2 pagesAdva FSP 150CC-GE201 Data SheetMark LamondNo ratings yet
- CRS109 8G 1S 2HnD IN 171016104814 PDFDocument1 pageCRS109 8G 1S 2HnD IN 171016104814 PDFIvan LopezNo ratings yet
- LEONTON - PT2-0800 - DatasheetDocument3 pagesLEONTON - PT2-0800 - DatasheetherlanNo ratings yet
- Link Street 88E6092/88E6095/ 88E6095F Datasheet: 8 Fe + 3 Ge Stackable Ethernet Switch With Qos and 802.1QDocument302 pagesLink Street 88E6092/88E6095/ 88E6095F Datasheet: 8 Fe + 3 Ge Stackable Ethernet Switch With Qos and 802.1QMohsen haghighatNo ratings yet
- Manual LightBolt - 1.7 - InglêsDocument159 pagesManual LightBolt - 1.7 - InglêsGerman RodriguezNo ratings yet
- OTN - ETS Use Case 0: InitialisationDocument9 pagesOTN - ETS Use Case 0: InitialisationBoonsub ThongwichitNo ratings yet
- Transceiver Data SheetDocument26 pagesTransceiver Data SheetROGELIO GARCIANo ratings yet
- 3 Underlying TechnologiesDocument49 pages3 Underlying TechnologiesTutun JuhanaNo ratings yet
- ANSI - TIA-568-C.0-2009 February 2009 Annex DDocument3 pagesANSI - TIA-568-C.0-2009 February 2009 Annex DAndresNo ratings yet
- Ether TypeDocument4 pagesEther Typeujwala_512No ratings yet
- Ruckus Hands On Training v2Document77 pagesRuckus Hands On Training v2Welly AndriNo ratings yet
- Lab6 - Configuring VLANs and TrunkingDocument12 pagesLab6 - Configuring VLANs and TrunkingkashifNo ratings yet
- 5.2.1 Packet Tracer - Configure VTP and DTP - ILMDocument6 pages5.2.1 Packet Tracer - Configure VTP and DTP - ILMJean Paul Vladimir De la Rosa EstrellaNo ratings yet
- Ds-3E0518P-E/M 16-Port Gigabit Unmanaged Poe Switch: Feature and FunctionDocument5 pagesDs-3E0518P-E/M 16-Port Gigabit Unmanaged Poe Switch: Feature and FunctionSandeep KamatNo ratings yet
- Tenant Same VRF Diff BD prv2Document33 pagesTenant Same VRF Diff BD prv2ravi kantNo ratings yet
- Integrasi To Uplink Metro XGPON-KaliasemDocument11 pagesIntegrasi To Uplink Metro XGPON-KaliasemMasfuk YazidNo ratings yet
- SFP ModulesDocument2 pagesSFP ModulesUriel Yesid Garzon CastroNo ratings yet
- RFQ - Cisco MerakiDocument3 pagesRFQ - Cisco MerakiUbaid UddinNo ratings yet
- Modelos Tipping Point IPSDocument4 pagesModelos Tipping Point IPSatlnacional02100% (1)
- Lesc 43 PBBDocument62 pagesLesc 43 PBBkhoantdNo ratings yet
- DAP-2360 B1 QIG v2.00 (DI)Document48 pagesDAP-2360 B1 QIG v2.00 (DI)Luis Antonio Salazar AlejoNo ratings yet
- 4.2.1.3 Packet Tracer - Configuring EtherChannelDocument11 pages4.2.1.3 Packet Tracer - Configuring EtherChannelTdd SanaNo ratings yet
- IP6820Document10 pagesIP6820edithsonNo ratings yet
- Prokolpo Protibedon Prantio Jonogosthi Gan VittikDocument76 pagesProkolpo Protibedon Prantio Jonogosthi Gan VittikKhan Mohammad Mahmud HasanNo ratings yet