Professional Documents
Culture Documents
Configuring Security For Mobile Devices: This Lab Contains The Following Exercises and Activities
Uploaded by
MD4733566Original Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Configuring Security For Mobile Devices: This Lab Contains The Following Exercises and Activities
Uploaded by
MD4733566Copyright:
Available Formats
MOAC 70-687 - Configuring Windows 8 Lab Manual
LAB 20
CONFIGURING SECURITY FOR MOBILE DEVICES
THIS LAB CONTAINS THE FOLLOWING EXERCISES AND ACTIVITIES:
Exercise 20.1 Exercise 20.2 Exercise 20.3 Lab Challenge Configuring BitLocker Creating a Data Recovery Agent (DRA) Disabling the Windows Location Provider Performing a Remote Wipe using the Exchange Admin Center (EAC)
BEFORE YOU BEGIN
The lab environment consists of student workstations connected to a local area network, along with a server that functions as the domain controller for a domain called adatum.com. The computers required for this lab are listed in Table 20-1.
Table 20-1 Computers Required for Lab 20
Computer Server (VM 1) Client (VM 3) Operating System Windows Server 2012 Windows 7 Enterprise Computer Name SVR-DC-A WKSTN-MBR-C
In addition to the computers, you will also need the software listed in Table 20-2 to complete Lab 20.
MOAC 70-687 - Configuring Windows 8 Lab Manual
Table 20-2 Software Required for Lab 20
Software Lab 20 student worksheet Location Lab20_worksheet.docx (provided by instructor)
Working with Lab Worksheets
Each lab in this manual requires that you answer questions, shoot screen shots, and perform other activities that you will document in a worksheet named for the lab, such as Lab20_worksheet.docx. You will find these worksheets on the book companion site. It is recommended that you use a USB flash drive to store your worksheets so you can submit them to your instructor for review. As you perform the exercises in each lab, open the appropriate worksheet file, type the required information, and then save the file to your flash drive.
SCENARIO
After completing this lab, you will be able to:
Enable and configure BitLocker Install the Certificate Authority Request a certificate from a Certificate Authority Disable the Windows Location Provider Create a Data Recovery Agent (DRA) for EFS Perform a Remote Wipe using the Exchange Admin Center (EAC)
Estimated lab time: 70 minutes
Exercise 20.1
Overview
Configuring BitLocker
In this exercise, you will enable BitLocker for the volume containing the operating system. 20 minutes
Completion time
1.
On WKSTN-MBR-C, log on using the adatum\administrator account and the Pa$$w0rd password. On the Start screen, type gpedit.msc, and then press Enter.
2.
MOAC 70-687 - Configuring Windows 8 Lab Manual
3.
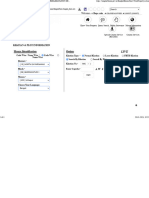
When the Local Group Policy Editor opens, navigate to \Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives and then double-click Require additional authentication at startup. When the Require additional authentication at startup dialog box opens, click Enabled. Take a screen shot of the local policy setting by pressing Alt+Prt Scr and then paste it into your Lab 20 worksheet file in the page provided by pressing Ctrl+V. Click OK to close the Require additional authentication at startup dialog box. Close Local Group Policy Editor. Mouse over the lower-left corner of the desktop and right-click the Start screen thumbnail that appears there. Then, from the context menu that appears, click Control Panel. When the Control Panel opens, click System and Security > BitLocker Drive Encryption. The BitLocker Drive Encryption control panel application appears (see Figure 20-1).
4.
5.
6. 7. 8.
9.
Figure 20-1 The BitLocker Drive Encryption page
10. For the C drive, click Turn on BitLocker.
MOAC 70-687 - Configuring Windows 8 Lab Manual
11. When prompted to choose how you will unlock your drive at startup, click Enter a password.
Question 1
Why is it necessary to use a password to unlock the drive?
12. In the Enter your password text box and in the Reenter your password text box, type Pa$$w0rd and then click Next. 13. When prompted to back up your recovery key, click Save to a file 14. Type \\SVR-DC-A\Downloads\ in front of the filename, and then press the Enter. Click Save. 15. Back on the How do you want to back up your recovery key? page, click Next. 16. On the Choose how much of your drive to encrypt page, click Next. On the Are you ready to encrypt this drive? page, with Run BitLocker system check selected, click Continue. 17. Move mouse to lower right corner and select Settings. Click Power and then click Restart. 18. After reboot, you are prompted to enter a password to unlock this drive. Type Pa$$w0rd and then press Enter. 19. After restart, log on to WKSTN-MBR-C as adatum\administrator and using the Pa$$w0rd password. 20. Type Control Panel and press Enter. 21. Click System and Security > BitLocker Drive Encryption. You should now see the encryption is in process (BitLocker Encrypting). 22. Take a screen shot of the BitLocker Drive Encryption page by pressing Alt+Prt Scr and then paste it into your Lab 20 worksheet file in the page provided by pressing Ctrl+V. End of exercise. Leave WKSTN-MBR-C running and logged in for the next exercise.
MOAC 70-687 - Configuring Windows 8 Lab Manual
Exercise 20.2
Overview
Creating a Data Recovery Agent (DRA)
In this exercise, you will create an EFS data recovery agent that can be used to recover documents that are protected with EFS. When a user forgets his or her password to unlock a drive that is protected by BitLocker or when a user has left the company and the account has been deleted, a Data Recovery Agent (DRA) can be used to recover the encrypted disk. 30 minutes
Mindset
Completion time
First, you must install a Certificate Authority by performing the following steps: 1. On SVR-DC-A, log on using the adatum\administrator account and the Pa$$w0rd password. When Server Manager opens, click Manage > Add Roles and Features. Click Next to start the Add Roles and Features Wizard. Click Next to accept the Role-based or feature-based installation default setting. From the Server pool, click your domain controller and then click Next. On the Select server roles page, click to select Active Directory Certificate Services and then click Add Features to include the management tools. Click Next to continue. Click Next to continue on the Select features screen. After reading the information provided on the Active Directory Certificate Services screen, click Next.
2. 3. 4. 5. 6.
7. 8. 9.
10. Confirm that Certification Authority is checked and then click Next. 11. On the Confirm installation selections screen, select Restart the destination server automatically if required and then click Yes to allow automatic restarts. 12. Click Install to begin the installation of the AD CS role. 13. When the installation has completed, click Close. 14. Click the yellow triangle with black exclamation point that appears at the top of the Server Manager Dashboard (see Figure 20-2), and then click Configure Active Directory Certificate Services on the destination server to complete the post-deployment configuration.
MOAC 70-687 - Configuring Windows 8 Lab Manual
Figure 20-2 The Post-deployment Configuration dialog box.
15. On the Specify credentials to configure role services screen, click Next to accept the default credentials (ADATUM\Administrator). 16. On the Select Role Services to configure screen, select Certification Authority and then click Next. 17. On the Specify the setup type of the CA screen, click Next to accept the Enterprise CA default setting. 18. On the Specify the type of the CA screen, click Next to accept the Root CA default setting. 19. On the Specify the type of the private key screen, click Next to accept the Create a new private key default setting. 20. On the Specify the cryptographic options screen, click Next to accept the default settings. 21. On the Specify the name of the CA screen, click Next to accept the default settings. 22. On the Specify the validity period screen, change the validity period to 10 years. Click Next to accept the default settings.
MOAC 70-687 - Configuring Windows 8 Lab Manual
23. On the Specify the database locations screen, click Next to accept the default settings. 24. Click Configure. When the configuration succeeds, click Close.
Next, you must request a Digital Certificate by performing the following steps: 1. On WKSTN-MBR-C, mouse over the lower-left corner of the desktop and rightclick the Start screen thumbnail that appears there. Click Run. In the Run dialog box, type certmgr.msc. Click the Personal Folder, then right-click the Personal Folder, and click All Tasks > Request New Certificate. When the Certificate Enrollment Wizard appears, click Next. Make sure Active Directory Enrollment Policy is highlighted and then click Next to continue. On the Request Certificates screen, select Basic EFS and then click Enroll. After you are informed the certificate has been enrolled and installed on the computer, click Finish. Expand the Personal folder, click Certificates, and then double-click the Administrator certificate. When the Certificate dialog box opens, click the Details tab.
2. 3.
4. 5.
6. 7.
8.
9.
10. Click the Copy to File button. When the Certificate Export Wizard dialog box appears, click Next. 11. Leave the No, do not export the private key option selected and then click Next. 12. Verify that the DER encoded binary X.509 (.CER) format is selected and then click Next. 13. On the File to Export page, click Browse to display the Save as dialog box. 14. In the File name text box, type BitLocker. In the Save as type option, verify that DER Encoded Binary X.509 (.cer) is selected and then click Save. Question 2
What is the path of the certificate export?
15. Back on the File to Export page, click Next.
MOAC 70-687 - Configuring Windows 8 Lab Manual
16. Click Finish to complete the Certificate Export Wizard. 17. Take a screen shot of the The export was successful dialog box by pressing Alt+Prt Scr and then paste it into your Lab 20 worksheet file in the page provided by pressing Ctrl+V. 18. When the The export was successful dialog box displays, click OK. 19. Close any open dialog boxes. 20. Close the certmgr console. 21. Log off of SVR-DC-A. End of exercise. Leave WKSTN-MBR-C running and logged in for the next exercise.
Exercise 20.3
Overview
Disabling the Windows Location Provider (WLP)
In this exercise, you will disable the Windows Location Provider (WLP) for a computer running Windows 8, and then modify a policy to perform the same action. The Windows Location Provider (WLP) is used by applications to gain access to location data. If you do not want to establish location information, you can disable the WLP. 10 minutes
Mindset
Completion time
1.
On WKSTN-DOM-C, mouse over the lower-left corner of the desktop and rightclick the Start screen thumbnail that appears there. Click Control Panel. When the Control Panel is open, click the Hardware and Sound category. Click Location Settings. Question 3
What does Windows Location Provider use to determine geographic location?
2. 3.
4. 5.
Deselect Turn on the Windows Location platform and then click Apply. Take a screen shot of the Location Settings page by pressing Alt+Prt Scr and then paste it into your Lab 20 worksheet file in the page provided by pressing Ctrl+V. Close the Control Panel.
6.
MOAC 70-687 - Configuring Windows 8 Lab Manual
7.
Mouse over the lower-left corner of the desktop and right-click the Start screen thumbnail that appears there. Click Run. In the Run dialog box, type gpedit.msc. Click Computer Configuration > Administrative Templates > Windows Components > Location and Sensors > Windows Location Provider (see Figure 20-3).
8. 9.
Figure 20-3 The Windows Location Provider page
10. Double-click Turn off Windows Location Provider and then click Enabled. 11. Take a screen shot of the Turn off Location Provider dialog box by pressing Alt+Prt Scr and then paste it into your Lab 20 worksheet file in the page provided by pressing Ctrl+V. 12. Click OK to close the Turn off Windows Location Provider dialog box. 13. Close Local Group Policy Editor. 14. Log off of WKSTN-MBR-C.
MOAC 70-687 - Configuring Windows 8 Lab Manual
End of exercise. Close all windows before you start the next exercise.
Lab Challenge
Overview
Performing a Remote Wipe using the Exchange Admin Center (EAC)
In this challenge, you will demonstrate how to perform a remote wipe using the Exchange Admin Center (EAC) Mobile devices (such as a smartphone) use Active Sync to retrieve emails, contacts, and other confidential information. If the phone has become lost or stolen, you can use the Exchange Admin Center (EAC) to remotely wipe the phone. 10 minutes
Mindset
Completion time
You can use EAC to remotely wipe a mobile device that uses ActiveSync to connect to the Exchange environment. In this exercise, you will specify the steps to wipe a mobile device. Since this exercise would require an Exchange environment connected to the network or Internet as well as a mobile device, this is only a written exercise. End of lab. You can log off or start a different lab. If you want to restart this lab, youll need to click the End Lab button in order for the lab to be reset.
You might also like
- Linda Foulkes - Learn Microsoft Office 2021 - Your One-Stop Guide To Upskilling With New Features of Word, PowerPoint, Excel, Outlook, and Teams, (2022, Packt Publishing) - Libgen - LiDocument655 pagesLinda Foulkes - Learn Microsoft Office 2021 - Your One-Stop Guide To Upskilling With New Features of Word, PowerPoint, Excel, Outlook, and Teams, (2022, Packt Publishing) - Libgen - LimatiasNo ratings yet
- OSWE NOTES BASIC BY JOASDocument233 pagesOSWE NOTES BASIC BY JOASjjjabriyel jabriNo ratings yet
- Smart Plant InstallationDocument52 pagesSmart Plant InstallationGem GemNo ratings yet
- 1z0 1042 21Document16 pages1z0 1042 21Siddiqa Ayesha100% (1)
- v01 NBU83ADM - Lab 01 Introducing NetBackup LinuxDocument16 pagesv01 NBU83ADM - Lab 01 Introducing NetBackup Linuxrambabu koppokuNo ratings yet
- Configuring System Recovery Options: This Lab Contains The Following Exercises and ActivitiesDocument10 pagesConfiguring System Recovery Options: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring System Recovery Options: This Lab Contains The Following Exercises and ActivitiesDocument10 pagesConfiguring System Recovery Options: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- v01 NBU83ADM - Lab 01 Introducing NetBackup WindowsDocument18 pagesv01 NBU83ADM - Lab 01 Introducing NetBackup Windowsrambabu koppoku100% (1)
- Win Server ChecklistDocument10 pagesWin Server ChecklistEduardo MorenoNo ratings yet
- Module 1 Lab ManualDocument38 pagesModule 1 Lab ManualCosmin NicolăițăNo ratings yet
- Configuring and Maintaining Network Security: This Lab Contains The Following Exercises and ActivitiesDocument9 pagesConfiguring and Maintaining Network Security: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring and Maintaining Network Security: This Lab Contains The Following Exercises and ActivitiesDocument9 pagesConfiguring and Maintaining Network Security: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring Remote Management: This Lab Contains The Following Exercises and ActivitiesDocument7 pagesConfiguring Remote Management: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Monitoring System Performance: This Lab Contains The Following Exercises and ActivitiesDocument12 pagesMonitoring System Performance: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring Backups: This Lab Contains The Following Exercises and ActivitiesDocument7 pagesConfiguring Backups: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Splunk Quick Reference GuideDocument6 pagesSplunk Quick Reference GuidechinkshadyNo ratings yet
- Configuring Local Security Settings: This Lab Contains The Following Exercises and ActivitiesDocument11 pagesConfiguring Local Security Settings: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring Authentication and Authorization: This Lab Contains The Following Exercises and ActivitiesDocument6 pagesConfiguring Authentication and Authorization: This Lab Contains The Following Exercises and ActivitiesMD4733566100% (1)
- Configuring Authentication and Authorization: This Lab Contains The Following Exercises and ActivitiesDocument6 pagesConfiguring Authentication and Authorization: This Lab Contains The Following Exercises and ActivitiesMD4733566100% (1)
- CP R81 Quantum SecurityManagement AdminGuideDocument652 pagesCP R81 Quantum SecurityManagement AdminGuideAyan NasNo ratings yet
- Migrating and Configuring User Data: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesMigrating and Configuring User Data: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- A Case Study On Identifying Software Development Lifecycle and Process FrameworkDocument5 pagesA Case Study On Identifying Software Development Lifecycle and Process FrameworkIJAERS JOURNALNo ratings yet
- Installing Operations ManagerDocument11 pagesInstalling Operations ManagerAbi ChandranNo ratings yet
- C8 Installation InstructionsDocument17 pagesC8 Installation InstructionschapparapuNo ratings yet
- IMPLEMENTING AZURE INFRASTRUCTURE SOLUTIONSDocument8 pagesIMPLEMENTING AZURE INFRASTRUCTURE SOLUTIONSsunil kambleNo ratings yet
- Vpro Labs GuideDocument27 pagesVpro Labs GuiderodderixNo ratings yet
- Installing Governance Minder InstructionsDocument48 pagesInstalling Governance Minder Instructionsyasas.biz100% (1)
- 70-411 Module 10 - Configuring Encryption and Advanced AuditingDocument21 pages70-411 Module 10 - Configuring Encryption and Advanced AuditingJason HawthorneNo ratings yet
- End PointDocument3 pagesEnd PointShibu VargheseNo ratings yet
- 20410csetupguide PDFDocument6 pages20410csetupguide PDFmgl111No ratings yet
- Meghdoot - Administration - GuideDocument105 pagesMeghdoot - Administration - Guidem_kumarnsNo ratings yet
- 70-697 Exam Guide with 165 Practice QuestionsDocument134 pages70-697 Exam Guide with 165 Practice QuestionsNamiNo ratings yet
- Lab Setup Guide 98 367Document9 pagesLab Setup Guide 98 367Morfeo MunitaNo ratings yet
- Nakivo Backup and Replication Virtual Appliance Deployment GuideDocument15 pagesNakivo Backup and Replication Virtual Appliance Deployment GuideJordan KnightNo ratings yet
- Respondus For Webassessor: Lockdown Browser Installation & Launch Guide For Client Proctored EventsDocument16 pagesRespondus For Webassessor: Lockdown Browser Installation & Launch Guide For Client Proctored EventsJohn EdwardsNo ratings yet
- MCC7500 Initial Setting Procedure (April 2022)Document3 pagesMCC7500 Initial Setting Procedure (April 2022)Max KomarovNo ratings yet
- CA Identity Suite 14.x: Implementation - Install The Components 200Document44 pagesCA Identity Suite 14.x: Implementation - Install The Components 200Steven AvilaNo ratings yet
- Module 4 Implementing VPN PDFDocument7 pagesModule 4 Implementing VPN PDFAfendey ArthurNo ratings yet
- Software Installation - How ToDocument4 pagesSoftware Installation - How ToGenio FalconNo ratings yet
- Implement Failover Clustering for Hyper-V VMsDocument9 pagesImplement Failover Clustering for Hyper-V VMslucasNo ratings yet
- System Requirements & Settings ManualDocument14 pagesSystem Requirements & Settings ManualfaisalNo ratings yet
- Guide to Set Up bizhub User Authentication with Active Directory, NDS, and SMBDocument25 pagesGuide to Set Up bizhub User Authentication with Active Directory, NDS, and SMBGustavo SiqueiraNo ratings yet
- 01 - How To Install MicroStationDocument5 pages01 - How To Install MicroStationWesleyPettyMinasNo ratings yet
- System Center 2012 ConfigurationDocument30 pagesSystem Center 2012 ConfigurationJose Miguel Martinez Grullon100% (1)
- CP E80.50 SecuRemoteClient UserGuideDocument16 pagesCP E80.50 SecuRemoteClient UserGuideGabino PampiniNo ratings yet
- Installing Windows 8: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesInstalling Windows 8: This Lab Contains The Following Exercises and ActivitiesMD4733566100% (1)
- Module 08 - Deploying and Managing AD CSDocument12 pagesModule 08 - Deploying and Managing AD CSCong TuanNo ratings yet
- 6293a Enu CompanionDocument107 pages6293a Enu CompanionStephanie DominguezNo ratings yet
- Table of Contents for GstarCAD 2020 License Activation GuideDocument37 pagesTable of Contents for GstarCAD 2020 License Activation Guidegstarcad IndonesiaNo ratings yet
- How To Install Smartplant 3D (Step-By-Step Guide)Document2 pagesHow To Install Smartplant 3D (Step-By-Step Guide)m 418No ratings yet
- ITB6004 70-680 Lab Setup Guide For VMwareDocument10 pagesITB6004 70-680 Lab Setup Guide For VMwarez1No ratings yet
- CTS 272 Chapter 1 LabDocument14 pagesCTS 272 Chapter 1 Labe0055996No ratings yet
- Developer's Guide: 950 Boardwalk, Suite 205, San Marcos, CA 92078 - (760) 510-1200Document15 pagesDeveloper's Guide: 950 Boardwalk, Suite 205, San Marcos, CA 92078 - (760) 510-1200Anonymous qBZmHMUNo ratings yet
- Mantra - Regisration Desk DocumentDocument19 pagesMantra - Regisration Desk DocumentanshulNo ratings yet
- Nicdsigner Linux HelpDocument10 pagesNicdsigner Linux HelpGghss MadappallyNo ratings yet
- Cyberoam Authentication For Thin Client (CATC) Installation Guide V 2.0.0.9Document16 pagesCyberoam Authentication For Thin Client (CATC) Installation Guide V 2.0.0.9Saad AhmedNo ratings yet
- Deploying A Captured ImageDocument12 pagesDeploying A Captured Imagecrackhead19950% (1)
- Windows Server 2008 Active DirectoryDocument151 pagesWindows Server 2008 Active DirectoryPichai Ng-arnpairojhNo ratings yet
- Informatica Support Console Installation GuideDocument17 pagesInformatica Support Console Installation GuideAlok TiwaryNo ratings yet
- Module 11 - Implementing Software Defined NetworkingDocument9 pagesModule 11 - Implementing Software Defined NetworkingCong TuanNo ratings yet
- Mission1-General ECE Troubleshooting - LG-JRDocument32 pagesMission1-General ECE Troubleshooting - LG-JRKleber RodriguesNo ratings yet
- LLDocument7 pagesLLJesse AdelmanNo ratings yet
- Test Lab Guide: Deploying An AD CS Two-Tier PKI HierarchyDocument22 pagesTest Lab Guide: Deploying An AD CS Two-Tier PKI HierarchyAkram AlqadasiNo ratings yet
- Step by Step Windows Server 2012 Failover Cluster Study LabDocument14 pagesStep by Step Windows Server 2012 Failover Cluster Study LabRavi Chandra RNo ratings yet
- Setting Up The VMWare ImageDocument26 pagesSetting Up The VMWare ImageNikolaNo ratings yet
- Configuring File and Folder Access: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesConfiguring File and Folder Access: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Installation of Attendance ManagementDocument2 pagesInstallation of Attendance ManagementjosephNo ratings yet
- Installation Instructions WindowsDocument17 pagesInstallation Instructions WindowsEoffice kollamNo ratings yet
- AutoCAD Civil 3D 2014 Standalone InstallationDocument8 pagesAutoCAD Civil 3D 2014 Standalone InstallationRenukadevi RptNo ratings yet
- CyberOps v1.1 Instructor Game InstructionsDocument6 pagesCyberOps v1.1 Instructor Game InstructionsozsaNo ratings yet
- SSILMDocument13 pagesSSILMStajic MilanNo ratings yet
- Evaluation of Some Android Emulators and Installation of Android OS on Virtualbox and VMwareFrom EverandEvaluation of Some Android Emulators and Installation of Android OS on Virtualbox and VMwareNo ratings yet
- MCTS 70-680 Exam Questions: Microsoft Windows 7, ConfiguringFrom EverandMCTS 70-680 Exam Questions: Microsoft Windows 7, ConfiguringRating: 3.5 out of 5 stars3.5/5 (2)
- Configuring File Recovery Options: This Lab Contains The Following Exercises and ActivitiesDocument4 pagesConfiguring File Recovery Options: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring Mobility Options: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesConfiguring Mobility Options: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring and Managing Updates: This Lab Contains The Following Exercises and ActivitiesDocument9 pagesConfiguring and Managing Updates: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Managing Local Storage: This Lab Contains The Following Exercises and ActivitiesDocument7 pagesManaging Local Storage: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring File and Folder Access: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesConfiguring File and Folder Access: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring Remote Connections: This Lab Contains The Following Exercises Cand ActivitiesDocument7 pagesConfiguring Remote Connections: This Lab Contains The Following Exercises Cand ActivitiesMD47335660% (1)
- Configuring Ip Settings: This Lab Contains The Following Exercises and ActivitiesDocument9 pagesConfiguring Ip Settings: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring Shared Resources: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesConfiguring Shared Resources: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Installing and Configuring Desktop Applications: This Lab Contains The Following Exercises and ActivitiesDocument6 pagesInstalling and Configuring Desktop Applications: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configuring Hyper-V: This Lab Contains The Following Exercises and ActivitiesDocument9 pagesConfiguring Hyper-V: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Configure Internet Explorer: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesConfigure Internet Explorer: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- 70-687 01Document6 pages70-687 01MD4733566No ratings yet
- Controlling Access To Local Hardware and Applications: This Lab Contains The Following Exercises and ActivitiesDocument9 pagesControlling Access To Local Hardware and Applications: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Installing and Configuring Windows Store Applications: This Lab Contains The Following Exercises and ActivitiesDocument6 pagesInstalling and Configuring Windows Store Applications: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Windows Server 2008 Administrator 70-646Document532 pagesWindows Server 2008 Administrator 70-646scottysockoNo ratings yet
- Installing Windows 8: This Lab Contains The Following Exercises and ActivitiesDocument8 pagesInstalling Windows 8: This Lab Contains The Following Exercises and ActivitiesMD4733566100% (1)
- Configuring Devices and Device Drivers: This Lab Contains The Following Exercises and ActivitiesDocument11 pagesConfiguring Devices and Device Drivers: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- Mungkin Maksud Anda AdalahDocument4 pagesMungkin Maksud Anda AdalahgeeNo ratings yet
- Axios Circular Error and JSON ParsingDocument5 pagesAxios Circular Error and JSON Parsingakash guptaNo ratings yet
- Online Course Reservation System JavaDocument46 pagesOnline Course Reservation System JavaAazmi Sayed100% (1)
- OUD011102 Oracle Network Configuration ISSUE 1.00Document33 pagesOUD011102 Oracle Network Configuration ISSUE 1.00Brice TOSSAVINo ratings yet
- An Operating Systems Course: With Projects in JavaDocument3 pagesAn Operating Systems Course: With Projects in JavaJonathan JoestarNo ratings yet
- BIM Adoption in Malaysia GuideDocument31 pagesBIM Adoption in Malaysia GuideJasonChong212No ratings yet
- Prerequisites NDD ReleaseDocument7 pagesPrerequisites NDD ReleaseLeandro MegarockNo ratings yet
- Passenger Flow Detection Management Platform (English Version)Document14 pagesPassenger Flow Detection Management Platform (English Version)Mafosk8No ratings yet
- 536550918195Document3 pages536550918195Luiz EduardoNo ratings yet
- Mysqldayroma Mysqlshellandvisualstudiocodeextensionv3 220928142035 488af3f0Document126 pagesMysqldayroma Mysqlshellandvisualstudiocodeextensionv3 220928142035 488af3f0Junior NogueiraNo ratings yet
- Assignment No 1-A SRSDocument6 pagesAssignment No 1-A SRSswatisahireNo ratings yet
- PackageManager and Display Device LogsDocument38 pagesPackageManager and Display Device LogsEkis PutraNo ratings yet
- Techrefvol2 PDFDocument482 pagesTechrefvol2 PDFRachidAbdallahNo ratings yet
- CV - Vikash - Kumar Singh - Java - Developer - 10+yrsDocument8 pagesCV - Vikash - Kumar Singh - Java - Developer - 10+yrsVikash SinghNo ratings yet
- Rahul KaladgiDocument1 pageRahul KaladgiPramanik ArijitNo ratings yet
- Module 2 - Apply Your KnowledgeDocument3 pagesModule 2 - Apply Your KnowledgeerieshaNo ratings yet
- Benu BhusanDocument4 pagesBenu BhusanADINo ratings yet
- Fundamentals of Graph and Browser DatabasesDocument18 pagesFundamentals of Graph and Browser Databasesthecoolguy96No ratings yet
- Technical Skills Tools and Application Used Methods Domain Business DevelopmentDocument2 pagesTechnical Skills Tools and Application Used Methods Domain Business DevelopmentKumar GuruNo ratings yet
- Unit 1 - Chapter - 1Document23 pagesUnit 1 - Chapter - 1Shamanth EdgeNo ratings yet
- Licensing Guide: Microsoft Dynamics NAV 2017Document18 pagesLicensing Guide: Microsoft Dynamics NAV 2017Bappi BiswasNo ratings yet
- Data Structure Module-3 Doubly Linked ListDocument19 pagesData Structure Module-3 Doubly Linked Listbhumika.verma00No ratings yet
- SAP Enhancement Package 8 For SAP ERP 6.0 ABAP: Document Version: 1.0 - 2016-01-20Document25 pagesSAP Enhancement Package 8 For SAP ERP 6.0 ABAP: Document Version: 1.0 - 2016-01-20Charith Nilanga WeerasekaraNo ratings yet
- Resume PavanRajDocument2 pagesResume PavanRajpavan rajNo ratings yet