Professional Documents
Culture Documents
LAB Topology Configuration
Uploaded by
Rc JohnnyOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
LAB Topology Configuration
Uploaded by
Rc JohnnyCopyright:
Available Formats
LAB Topology Configuration
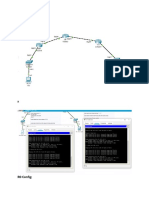
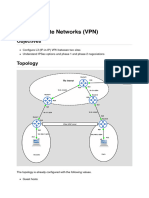
London Router (Cisco 2611 XM) The serial and the fast ethernet interfaces are configured with the appropriate IP addressing as shown below. The DTE end of the cable is connected to the router. Interface configuration interface FastEthernet0/0 ip address 10.1.0.1 255.255.0.0 interface Serial0/0 ip address 172.16.1.1 255.255.0.0 interface FastEthernet0/1 ip address 192.168.1.1 255.255.255.0 DHCP configuration DHCP is configured on the appropriate interfaces to provide ip addresses to computers connected to the networks in the specific range. DHCP on FE0/1 ip dhcp pool lan2 (Creates a dhcp pool with name lan 2) network 192.168.1.0 /24(DHCP addresses would be provided in this range) dns-server 192.168.1.1 (DNS server IP ) default-router 192.168.1.1 (Default gateway IP )
DHCP on FE 0/0 ip dhcp pool lan1 network 10.1.0.0 /16 dns-server 10.1.0.1 default-router 10.1.0.1 Excluding DHCP addresses for static ip address on the network (To be done in global config mode) ip dhcp excluded-address 10.1.0.0 10.1.0.3 ip dhcp excluded-address 192.168.1.0 192.168.1.3 The IP addresses till 10.1.0.3 and 192.168.1.3 are used for servers, routers, access points which are used on the network, which is excluded from the addresses leased out by the dhcp server. IPSEC Tunnel Configuration IKE Phase 1 configuration Crypto isakmp enable crypto isakmp policy 10 hash md5 authentication pre-share encryption DES group 1 lifetime 3600
Shared key configuration with the peer.
The value of the shared key asterix is configured with the peer crypto isakmp key asterix address 172.16.1.2. IKE Phase 2 configuration crypto ipsec transform-set ipsec1 esp-des esp-md5-hmac mode tunnel ESP is selected as the IPSEC protocol along with DES and MD5-HMAC. The mode is selected as tunnel. Crypto ACL The following ACL are used by IPSEC to identify the traffic which needs to be encrypted. access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255 access-list 101 permit ip 10.1.0.0 0.0.255.255 192.168.2.0 0.0.0.255 This would let the router know that the traffic from 192.168.1.0 to 192.168.2.0 and traffic from 10.1.0.0 to 192.168.2.0 is to be sent via the tunnel Crypto MAP After the ACL is created, crypto maps are configured on the router. The name is l2r crypto map l2r 10 ipsec-isakmp set peer 172.16.1.2 set transform-set ipsec1 match address 101
The crypto map is then applied to the corresponding interface. interface Serial0/0 crypto map l2r Routing After the IPSEC tunnel is configured, a default route is set to route all packets to the peer router. ip route 0.0.0.0 0.0.0.0 172.16.1.2 Access restriction to servers on the staff network. Access restriction is provided to the AD and management server systems from the guest network. Note: Only the configuration is identified, but is not demonstrated or configured in the routers in the tests, due to the number of systems required. access-list 102 deny ip host 192.168.1.2 10.1.0.0 0.0.255.255 access-list 102 deny ip host 192.168.1.2 10.2.0.0 0.0.255.255 access-list 102 deny ip host 192.168.1.3 10.1.0.0 0.0.255.255 access-list 102 deny ip host 192.168.1.3 10.2.0.0 0.0.255.255 access-list 102 permit ip any any The first four lines would deny traffic to the hosts 192.168.1.2 and 192.168.1.3 (AD and management server) from the guest networks. The ACL is applied as inbound on the interface on which the staff network is connected , which is FE0/1 interface FastEthernet0/0 ip address 10.1.0.1 255.255.0.0 ip access-group 101 in
Paris Router (Cisco 1751) The serial and the fast ethernet interface are configured with the appropriate IP addressing as shown below. The DCE end of the cable is connected to the router. The clock rate is configured as it is the DCE end of the cable. Interface configuration interface FastEthernet0/0 ip address 192.168.2.1 255.255.255.0 interface Serial0/0 ip address 172.16.1.2 255.255.0.0 clockrate 56000 DHCP configuration DHCP is configured on the appropriate interface to provide ip addresses to computers connected to the networks in the specific range. DHCP on FE0/0 ip dhcp pool lan1 (Creates a dhcp pool with name lan 1) network 192.168.2.0 255.255.255.0 ((DHCP addresses would be provided in this range) dns-server 192.168.2.1 (DNS-server IP ) default-router 192.168.2.1(Default gateway IP) Excluding DHCP addresses for static ip address on the network (To be done in global config mode) ip dhcp excluded-address 192.168.2.0 192.168.2.4
The IP addresses till 192.168.2.4 are used for servers, routers, access points which are used on the network, which is excluded from the addresses leased out by the dhcp server. IPSEC Tunnel Configuration IKE Phase 1 configuration Crypto isakmp enable crypto isakmp policy 10 hash md5 authentication pre-share encryption DES group 1 lifetime 3600 Shared key configuration with the peer. The value of the shared key asterix is configured with the peer crypto isakmp key asterix address 172.16.1.1 IKE Phase 2 configuration crypto ipsec transform-set ipsec1 esp-des esp-md5-hmac mode tunnel ESP is selected as the IPSEC protocol along with DES and MD5-HMAC. The mode is selected as tunnel. Crypto ACL The following ACL are used by IPSEC to identify the traffic which needs to be encrypted.
access-list 101 permit ip 192.168.2.0 0.0.0.255 10.1.0.0 0.0.0.255 access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255 This would let the router know that the traffic from 192.168.2.0 to 10.1.0.0 and traffic from 192.168.2.0 to 192.168.1.0 is to be sent via the tunnel Crypto MAP After the ACL is created, crypto maps are configured on the router. The name is r2l. crypto map r2l 10 ipsec-isakmp set peer 172.16.1.2 set transform-set ipsec1 match address 101 The crypto map is then applied to the corresponding interface. interface Serial0/0 crypto map r2l Routing After the IPSEC tunnel is configured, a default route is set to route all packets to the peer router. ip route 0.0.0.0 0.0.0.0 172.16.1.1
Running Config (Cisco 2611 XM) Building configuration...
Current configuration : 2047 bytes ! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname LONDON ! boot-start-marker boot-end-marker ! ! no aaa new-model memory-size iomem 15 no network-clock-participate slot 1 no network-clock-participate wic 0 ip cef !
! no ip dhcp use vrf connected ip dhcp excluded-address 10.1.0.0 10.1.0.3 ip dhcp excluded-address 192.168.1.0 192.168.1.3 ! ip dhcp pool lan1 network 10.1.0.0 255.255.0.0 dns-server 10.1.0.1 default-router 10.1.0.1 ! ip dhcp pool lan2 network 192.168.1.0 255.255.255.0 dns-server 192.168.1.1 default-router 192.168.1.1 ! ! ip auth-proxy max-nodata-conns 3 ip admission max-nodata-conns 3 ! ! ! !
!crypto isakmp policy 10 hash md5 authentication pre-share lifetime 3600 crypto isakmp key asterix address 172.16.1.2 ! ! crypto ipsec transform-set ipsec1 esp-des esp-md5-hmac ! crypto map l2r 10 ipsec-isakmp set peer 172.16.1.2 set transform-set ipsec1 match address 101 ! interface FastEthernet0/0 ip address 10.1.0.1 255.255.0.0 duplex auto speed auto ! interface Serial0/0 ip address 172.16.1.1 255.255.0.0 no fair-queue
crypto map l2r ! interface FastEthernet0/1 ip address 192.168.1.1 255.255.255.0 duplex auto speed auto ! interface Serial1/0 no ip address shutdown ! interface Serial1/1 no ip address shutdown ! interface Serial1/2 no ip address shutdown ! interface Serial1/3 no ip address shutdown
! ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 172.16.1.2 ! ! ip http server no ip http secure-server ! access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255 access-list 101 permit ip 10.1.0.0 0.0.255.255 192.168.2.0 0.0.0.255 ! ! control-plane ! !line con 0 line aux 0 line vty 0 4 login ! ! end
Paris Router ( Cisco 1751 ) PARIS#show run Building configuration...
Current configuration : 1272 bytes ! version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname PARIS ! ! memory-size iomem 20 ip subnet-zero ! ! ip dhcp excluded-address 192.168.2.0 192.168.2.4 ! ip dhcp pool lan1
network 192.168.2.0 255.255.255.0 dns-server 192.168.2.1 default-router 192.168.2.1 ! ip audit notify log ip audit po max-events 100 ip ssh time-out 120 ip ssh authentication-retries 3 ! crypto isakmp policy 10 hash md5 authentication pre-share lifetime 3600 crypto isakmp key asterix address 172.16.1.1 ! ! crypto ipsec transform-set ipsec1 esp-des esp-md5-hmac crypto mib ipsec flowmib history tunnel size 200 crypto mib ipsec flowmib history failure size 200 ! crypto map r2l 10 ipsec-isakmp set peer 172.16.1.1
set transform-set ipsec1 match address 101 ! ! ! ! interface FastEthernet0/0 ip address 192.168.2.1 255.255.255.0 speed auto ! interface Serial0/0 ip address 172.16.1.2 255.255.0.0 clockrate 256000 crypto map r2l ! ip classless ip route 0.0.0.0 0.0.0.0 172.16.1.1 no ip http server ip pim bidir-enable ! access-list 101 permit ip 192.168.2.0 0.0.0.255 10.1.0.0 0.0.0.255 access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
! ! line con 0 line aux 0 line vty 0 4 login ! end
You might also like
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Ipsec/Gre With Nat On Ios Router Configuration Example: Document Id: 14137Document7 pagesIpsec/Gre With Nat On Ios Router Configuration Example: Document Id: 14137Gustavo SánchezNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- 09 - How To Connect Securely Between 2 Regional Offices Using CISCO VPNDocument4 pages09 - How To Connect Securely Between 2 Regional Offices Using CISCO VPNJohnpatrick DejesusNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- Ejemplo VPN 2Document5 pagesEjemplo VPN 2jhonjunisNo ratings yet
- Design A Secure Network Case Study 2: Box Hill Institute of TAFEDocument5 pagesDesign A Secure Network Case Study 2: Box Hill Institute of TAFErussian00No ratings yet
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- CCNA Exploration: Accessing The WAN Student Skills Based Assessment Lab (CCNA 4 Skill 2011)Document13 pagesCCNA Exploration: Accessing The WAN Student Skills Based Assessment Lab (CCNA 4 Skill 2011)Cường NgôNo ratings yet
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingFrom EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingNo ratings yet
- Lab Report IpsecDocument11 pagesLab Report Ipsecv4meetNo ratings yet
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksFrom EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNo ratings yet
- Configuration Example of Dynamic IPsec BDocument15 pagesConfiguration Example of Dynamic IPsec BTransmission EngineerNo ratings yet
- RWPS ApexM2 PublicDocument9 pagesRWPS ApexM2 Publickuratsa49No ratings yet
- Embedded Software Design and Programming of Multiprocessor System-on-Chip: Simulink and System C Case StudiesFrom EverandEmbedded Software Design and Programming of Multiprocessor System-on-Chip: Simulink and System C Case StudiesNo ratings yet
- Ospf Primer EjemploDocument10 pagesOspf Primer EjemplomikineroNo ratings yet
- Internet Security: Cryptographic Principles, Algorithms and ProtocolsFrom EverandInternet Security: Cryptographic Principles, Algorithms and ProtocolsNo ratings yet
- VPN IPsecDocument4 pagesVPN IPsecDenisa PriftiNo ratings yet
- Yasser Auda CCIEv5 WorkbookDocument26 pagesYasser Auda CCIEv5 WorkbookphamvanhaNo ratings yet
- PLC: Programmable Logic Controller – Arktika.: EXPERIMENTAL PRODUCT BASED ON CPLD.From EverandPLC: Programmable Logic Controller – Arktika.: EXPERIMENTAL PRODUCT BASED ON CPLD.No ratings yet
- Configuring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingDocument9 pagesConfiguring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingAndika PajriNo ratings yet
- Cisco ConfigDocument4 pagesCisco ConfigfadrolNo ratings yet
- Cisco Network Academy Ccna 1 Introduction To Networks: Ipv4 AddressingDocument12 pagesCisco Network Academy Ccna 1 Introduction To Networks: Ipv4 AddressingangelNo ratings yet
- Internet 2Document4 pagesInternet 2mihai102001No ratings yet
- 5.2.3.4 Lab - Troubleshooting Advanced Single-Area OSPFv2Document7 pages5.2.3.4 Lab - Troubleshooting Advanced Single-Area OSPFv2joleszaz JenciNo ratings yet
- Ethernet Networks: Design, Implementation, Operation, ManagementFrom EverandEthernet Networks: Design, Implementation, Operation, ManagementRating: 4 out of 5 stars4/5 (1)
- HQ-ASA Practice Lab.pkt - копияDocument13 pagesHQ-ASA Practice Lab.pkt - копияDavid VardanyanNo ratings yet
- CCST Cisco Certified Support Technician Study Guide: Networking ExamFrom EverandCCST Cisco Certified Support Technician Study Guide: Networking ExamNo ratings yet
- Laboratorio 5.2.3.4Document10 pagesLaboratorio 5.2.3.4Zaskya Yissellmitth Cordoba DelisserNo ratings yet
- ARM Microcontrollers Programming for Embedded SystemsFrom EverandARM Microcontrollers Programming for Embedded SystemsRating: 5 out of 5 stars5/5 (1)
- Ejemplo VPN 1 PDFDocument4 pagesEjemplo VPN 1 PDFjhonjunisNo ratings yet
- Cisco EZVPN With 2911 and ASADocument4 pagesCisco EZVPN With 2911 and ASAmsteppNo ratings yet
- Next-Generation switching OS configuration and management: Troubleshooting NX-OS in Enterprise EnvironmentsFrom EverandNext-Generation switching OS configuration and management: Troubleshooting NX-OS in Enterprise EnvironmentsNo ratings yet
- Configuring Cisco Site To Site Ipsec VPN With Dynamic Ip Endpoint Cisco RoutersDocument8 pagesConfiguring Cisco Site To Site Ipsec VPN With Dynamic Ip Endpoint Cisco RoutersjeannzonzidiNo ratings yet
- 4.3.9 Packet Tracer Configure Site To Site VPN Answer KeyDocument4 pages4.3.9 Packet Tracer Configure Site To Site VPN Answer Keymalaklmawt0000No ratings yet
- Lab VPNDocument9 pagesLab VPNhung kungNo ratings yet
- IP Telephony: Deploying VoIP Protocols and IMS InfrastructureFrom EverandIP Telephony: Deploying VoIP Protocols and IMS InfrastructureNo ratings yet
- Ipsec FeatDocument19 pagesIpsec Featpankajagr83No ratings yet
- IPSec VPNDocument5 pagesIPSec VPNcciersmanNo ratings yet
- EzVPN, Configure, TroubleshootDocument13 pagesEzVPN, Configure, TroubleshootAlviso1No ratings yet
- Smart Home Technology: Hands-0N Technical DemonstrationDocument64 pagesSmart Home Technology: Hands-0N Technical DemonstrationSaiPrasad AvulamNo ratings yet
- Lan2lan VPNDocument6 pagesLan2lan VPNFelix BlasioNo ratings yet
- ASA Firewall LabDocument5 pagesASA Firewall LabLindsey Benter100% (3)
- Ccna 2 Practice Lab SolutionsDocument7 pagesCcna 2 Practice Lab SolutionsSandrino PostelnicuNo ratings yet
- IPsec Quick and DirtyDocument4 pagesIPsec Quick and Dirtysgopal7No ratings yet
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument4 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersSuhas KanikarNo ratings yet
- Configuring Ipsec With Eigrp and Ipx Using Gre Tunneling: Document Id: 14136Document12 pagesConfiguring Ipsec With Eigrp and Ipx Using Gre Tunneling: Document Id: 14136cybersh3657No ratings yet
- Router Behind CM 19268Document5 pagesRouter Behind CM 19268Pablo Guerrero GuzmánNo ratings yet
- CISCO EWAN NAT-ACL PT Practice SBA With SolutionDocument9 pagesCISCO EWAN NAT-ACL PT Practice SBA With Solutionandreajr100% (1)
- Rbi Script 2ND QuarterDocument4 pagesRbi Script 2ND QuarterJosephine RiveraNo ratings yet
- The Information AGE: Reporters Ryan Joshua D. Burnea Vicente L. Vecina Marnelle BalagonDocument28 pagesThe Information AGE: Reporters Ryan Joshua D. Burnea Vicente L. Vecina Marnelle BalagonJAMICA CUSHI ESTAMPANo ratings yet
- The Bases of Folding - Joseph FlemingDocument157 pagesThe Bases of Folding - Joseph FlemingPraschant Iyer100% (4)
- MEIL QuizDocument5 pagesMEIL QuizRyan MostarNo ratings yet
- Module 2 - Lesson 2Document5 pagesModule 2 - Lesson 2renz daveNo ratings yet
- The NFT BibleDocument113 pagesThe NFT BibleIsrael GamalielNo ratings yet
- BGP Additional PathsDocument15 pagesBGP Additional PathsEdon BlakajNo ratings yet
- Struktur Harga Unit Printronix Barcode ModelDocument1 pageStruktur Harga Unit Printronix Barcode ModelAtika FirdausNo ratings yet
- Model Bank: (Resource Upload Guide)Document10 pagesModel Bank: (Resource Upload Guide)sayeedNo ratings yet
- Workshop - LTE SolutionDocument29 pagesWorkshop - LTE SolutionabhineetkumarNo ratings yet
- English 7 - WEEK 4Document21 pagesEnglish 7 - WEEK 4Ginelyn MaralitNo ratings yet
- Meme StocksDocument18 pagesMeme StocksSybil AzurNo ratings yet
- Pengertian Satpam, Tugas Dan Fungsi Serta Peran Star GuardDocument6 pagesPengertian Satpam, Tugas Dan Fungsi Serta Peran Star GuardFaiz PondokNo ratings yet
- EMULISTDocument2 pagesEMULISTNext uhdNo ratings yet
- Asn 8th Sem Etec 406Document3 pagesAsn 8th Sem Etec 406Ishant SadhawaniNo ratings yet
- Sigtran 01 IntroductionDocument9 pagesSigtran 01 IntroductionPhilippe PopulaireNo ratings yet
- CCE Learn (Learning Management System) - Blackboard LMSDocument9 pagesCCE Learn (Learning Management System) - Blackboard LMSNitin SinghNo ratings yet
- Services - SMMSMDocument53 pagesServices - SMMSMSaurabh ChhillarNo ratings yet
- MSTeams Diagnostics Log 2 - 4 - 2020 - 6 - 12 - 17 - P. - M.Document218 pagesMSTeams Diagnostics Log 2 - 4 - 2020 - 6 - 12 - 17 - P. - M.manueljgNo ratings yet
- Igcse Computer ScieneDocument70 pagesIgcse Computer ScieneGatika SuneelNo ratings yet
- G2a Method January2024Document10 pagesG2a Method January2024ofiucoloopNo ratings yet
- Media and Information Literacy 12 Lesson 7: Legal, Ethical and Societal Issues in Media and InformationDocument2 pagesMedia and Information Literacy 12 Lesson 7: Legal, Ethical and Societal Issues in Media and InformationShen EugenioNo ratings yet
- Routing and Switching Lab - 2019: Anycast TopologyDocument7 pagesRouting and Switching Lab - 2019: Anycast TopologyChinen momoNo ratings yet
- Speakout Elementary End of Course Test - PDFDocument1 pageSpeakout Elementary End of Course Test - PDFAhmet Bülent BozdoğanNo ratings yet
- # - Import The Local Microsoft Online Powershell Module Cmdlets and Connect To O365 Online - #Document2 pages# - Import The Local Microsoft Online Powershell Module Cmdlets and Connect To O365 Online - #Michele McdowellNo ratings yet
- Riccar R1850 Sewing Machine Instruction ManualDocument45 pagesRiccar R1850 Sewing Machine Instruction ManualiliiexpugnansNo ratings yet
- Sri Rudram Laghunyasam TeluguDocument3 pagesSri Rudram Laghunyasam Teluguincognito kalyanNo ratings yet
- VXLAN Tutorial: THERDTOON TheerasasanaDocument36 pagesVXLAN Tutorial: THERDTOON TheerasasanaRaj KaranNo ratings yet
- Notes CheckDocument5 pagesNotes ChecksaivenkateswarNo ratings yet
- Chapter 2Document25 pagesChapter 2Hoàng AnhNo ratings yet
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamFrom EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamRating: 5 out of 5 stars5/5 (1)
- Kali Linux - An Ethical Hacker's Cookbook - Second Edition: Practical recipes that combine strategies, attacks, and tools for advanced penetration testing, 2nd EditionFrom EverandKali Linux - An Ethical Hacker's Cookbook - Second Edition: Practical recipes that combine strategies, attacks, and tools for advanced penetration testing, 2nd EditionRating: 5 out of 5 stars5/5 (1)
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsFrom EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsNo ratings yet
- Hacking Network Protocols: Complete Guide about Hacking, Scripting and Security of Computer Systems and Networks.From EverandHacking Network Protocols: Complete Guide about Hacking, Scripting and Security of Computer Systems and Networks.Rating: 5 out of 5 stars5/5 (2)
- Concise Guide to OTN optical transport networksFrom EverandConcise Guide to OTN optical transport networksRating: 4 out of 5 stars4/5 (2)
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsFrom EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsRating: 5 out of 5 stars5/5 (1)
- Alcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsFrom EverandAlcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsNo ratings yet
- Azure DevOps Engineer: Exam AZ-400: Azure DevOps Engineer: Exam AZ-400 Designing and Implementing Microsoft DevOps SolutionsFrom EverandAzure DevOps Engineer: Exam AZ-400: Azure DevOps Engineer: Exam AZ-400 Designing and Implementing Microsoft DevOps SolutionsNo ratings yet
- The Linux Command Line Beginner's GuideFrom EverandThe Linux Command Line Beginner's GuideRating: 4.5 out of 5 stars4.5/5 (23)
- PHP BLUEPRINT: An Essential Beginners Guide to Learn the Realms of PHP From A-ZFrom EverandPHP BLUEPRINT: An Essential Beginners Guide to Learn the Realms of PHP From A-ZNo ratings yet
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNFrom EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNRating: 5 out of 5 stars5/5 (1)
- RHCSA Red Hat Enterprise Linux 9: Training and Exam Preparation Guide (EX200), Third EditionFrom EverandRHCSA Red Hat Enterprise Linux 9: Training and Exam Preparation Guide (EX200), Third EditionNo ratings yet
- Linux For Beginners: The Comprehensive Guide To Learning Linux Operating System And Mastering Linux Command Line Like A ProFrom EverandLinux For Beginners: The Comprehensive Guide To Learning Linux Operating System And Mastering Linux Command Line Like A ProNo ratings yet
- Computer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityFrom EverandComputer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityRating: 4.5 out of 5 stars4.5/5 (13)