Professional Documents
Culture Documents
Authentication Using Hand Geometry and Finger Geometry Biometric Techniques
Uploaded by
seventhsensegroup0 ratings0% found this document useful (0 votes)
23 views6 pagesBiometric authentication systems are gaining importance in the today’s world where information security is essential. Hand geometry verification systems use geometric measurements of hand for authentication of individuals. It is believed that the combination of different features of the hand is unique for a particular person. Different hand geometry authentication systems use reference pegs for capturing the image of the hand. We propose peg free hand geometry and finger geometry system
Original Title
Authentication Using Hand geometry And Finger geometry biometric Techniques
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentBiometric authentication systems are gaining importance in the today’s world where information security is essential. Hand geometry verification systems use geometric measurements of hand for authentication of individuals. It is believed that the combination of different features of the hand is unique for a particular person. Different hand geometry authentication systems use reference pegs for capturing the image of the hand. We propose peg free hand geometry and finger geometry system
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
23 views6 pagesAuthentication Using Hand Geometry and Finger Geometry Biometric Techniques
Uploaded by
seventhsensegroupBiometric authentication systems are gaining importance in the today’s world where information security is essential. Hand geometry verification systems use geometric measurements of hand for authentication of individuals. It is believed that the combination of different features of the hand is unique for a particular person. Different hand geometry authentication systems use reference pegs for capturing the image of the hand. We propose peg free hand geometry and finger geometry system
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 6
International Journal of Computer Trends and Technology (IJCTT) volume4Issue8August 2013
ISSN: 2231-2803http://www.ijcttjournal.org Page 2776
Authentication Using Hand geometry And Finger
geometry biometric Techniques
1
AmandeepKaur Bhatia,
2
SupreetKaurGujral
1
M.E (CSE)Student, Punjabi University Regional Centre for IT &Management, Punjab, India,
2
Assistant Professor (CS), Punjabi University Regional Centre for IT &Management, Punjab, India,
AbstractBiometric authentication systems are gaining
importance in the todays world where information security is
essential. Hand geometry verification systems use geometric
measurements of hand for authentication of individuals. It is
believed that the combination of different features of the hand is
unique for a particular person. Different hand geometry
authentication systems use reference pegs for capturing the
image of the hand. We propose peg free hand geometry and
finger geometry system
Keywords- Biometrics, Recognition, Verification, Identification,
Hand Geometry
I. INTRODUCTION
As increase of security requirements, a person has to
remember lots of pin numbers, passwords and other security
codes. The passwords can be easily guessed and stolen
electronically. Once an intruder acquires the user ID and
password, the intruder has total access to the users resources.
It is suggested that people should not use same password for
different applications. In the modern world that would mean
memorizing a large number of Security codes. Biometric is
most suitable solution to all these requirements. In the
future,the biometric system will be more convenient and
reliable[1].
In the era of Information Technology, openness of the
information is a major concern. As the confidentiality and
integrity of the information is critically important, it has to be
secured fromunauthorized access. Security refers toprohibit
some unauthorized persons fromsome important data or from
some precious assets. So we need accurateautomatic personal
identification in various applications such as ATM, driving
license, passports, citizens card,cellular telephones, voters
ID card. Hand geometry is most widely used for person
identification in the recentyears. Hand geometry based
biometric system are gaining acceptance in low to medium
security applications [2]. Hand geometry recognitions terms
are based on a number of measurements taken from the
humanhand, including its shape, size of palm, and length and
widths of the fingers.The technique is very simple, relatively
easy to use, and inexpensive. Environmental factors such as
dry weather or individual anomalies such as dry skin do not
appear to have any negative effects on the verification
accuracy of hand geometry-basedsystems. The hands images
can be obtained by using a simple setup including a web cam,
digital camera.However other biometric traits require a
specialized, high cost scanner to acquire the data. The
useracceptability for hand geometry based biometrics is very
high as it does not extract detail features of theindividual. An
individual's hand does not significantly change after a certain
age. The strengths of hand geometry Biometrics are as follows
[3].
Ease of use: Hand is placed on the units surface but the
systemalso works fairly well with dirty hand.
Resistant to fraud: model of an enrolled persons hand
and fingers, it would be difficult to submit a fake sample.
Template size: template size of hand geometry is
extremely small if it is compared with other biometrics
systems.
Traditional hand geometry systems are always used thepegs to
fix the placement of the hand [4].Two main weaknesses of
using pegs are that pegs will definitely deformthe shape of
the hand silhouette and users might place their hands
incorrectly as shown in Figure 1. These problems can
certainly reduce the Performance of the biometric system.
International Journal of Computer Trends and Technology (IJCTT) volume4Issue8August 2013
ISSN: 2231-2803http://www.ijcttjournal.org Page 2777
Figure 1: Three peg-fixed hand photos: deformed hand shape
II. MODULES OF BIOMETRIC SYSTEM
As shown in the Figure 2, a biometric systemcomprises of
fivemajor steps involved in Hand Geometry Based
identification. These steps are Image acquisition, Imagepre
processing, Feature extraction,Matching and Decision as
follows:
Figure 2: Components of a Biometric System
A. Image Acquisition
Image acquisition is the first step in a hand geometric system.
This process involves the capturing and storage of digital
image from vision sensors like colour digital cameras,
monochrome and colour CCD camera, video cameras,
scanners etc. The proposed image acquisition systemconsists
of digital camera and black flat surface used as a background.
User can placed one hand pointing up, on flat surface with the
back of hand touching the flat surface or the user can place
hand freely as there are no pegs to fix position of hand, then
image is acquired using digital camera. Users are only
requested to make sure that their fingers do not touch one
another. In this experiment right hand images of users are
acquired. There are various format stored for the images such
as .jpeg, .tiff, .png,.gif and .bmp. The captured images are
stored in one of these formats on the computer for possible
image processing.
Figure3:Image Acquisition
B. Pre-processing
The next stage is image pre-processing module. Image pre-
processing relates to the preparation of an image for later
analysis and use. The role of the pre-processing module is to
prepare the image for feature extraction. The images are
captured using a digital camera. The input image is a coloured
image of the right hand without any deformation. The input
image, shown in Figure 3 is stored in jpeg format. In cases of
standard deformity such as a missing finger the system
expresses its inability to process the image. It is also critical
that the fingers are separated from each other. However it is
not required to stretch the fingers to far apart as possible. The
hand should be placed in a relaxed state with fingers separated
from each other. Since features such as length and width
which are dependent on the image size and resolution are
being used, it is critical that to have uniformsize of images.
Image pre-processing module is consisting of operations such
as Gray scale image, Noise Removal, Binarized Image and
Edge detection [5].
1) Gray scale image
In this proposed system hand image is captured through
digital camera so the original image is colour image. For
digital image processing it is necessary to convert the
coloured hand image into the gray scale image as shown in
Figure 4.
Decision
Matching
Feature Extraction
Preprocessing
Image Capture
International Journal of Computer Trends and Technology (IJCTT) volume4Issue8August 2013
ISSN: 2231-2803http://www.ijcttjournal.org Page 2778
Figure 4: Gray scaleimage
Figure 5: Binarized image
Figure 6: Filtered Image
Figure 7: Image contains only edges
2) Binarized Image
In this step gray level image is converted into an image with
two levels 0 or 1.Where 1indicates the white colour and 0
indicates the blackcolor.Red, green and blue (RGB) values of
each pixel are extracted. Since a monochromaticimage is
required for the proposed systema threshold is determined.
All pixels withRGB values above the threshold are considered
white pixels and all pixels below the thresholdare considered
as black pixels [8].
3) Filtered image
It is necessary to remove the noise fromthe image because it
may produce difference between the actual image and
captured image. Basically noise produced in the image is due
to device using for capturing image, atmosphere condition or
surrounding condition. There are many methods to remove the
noise in MATLAB simulation tool. So, before extracting
features fromthe image, it is very important to remove the
noise fromthe image (Figure 6).
4) Edge detection
In order to extract geometric features of the hand it is required
that image contains only edges(Figure 7). The image obtained
after elimination of noise contains regions of black andwhite
pixels. In order to extract geometric features of the hand it is
require that the image contains only edges. Consequently it is
required to convert regions of black space to an image
containing only the boundary of the white pixels. Thisis
achieved by using an edge detection algorithm. The algorithm
converts all pixelsexcluding those at the boundary of black
and white regions to white pixels. Thealgorithmalso has to
ensure that the thickness of this boundary is as low as
possible. This is because a thick boundary will adversely
affect the accuracy of the feature detection algorithm[8].
C. Feature Extraction
Since there is no peg to x the placement of hand, users can
place their hands in various positions as shown in Figure 8.
Before extracting the hand features, the landmark points
have to be located [6]. These landmark points include the
ngertips and valley points that can be seen in (Figure 9).
International Journal of Computer Trends and Technology (IJCTT) volume4Issue8August 2013
ISSN: 2231-2803http://www.ijcttjournal.org Page 2779
Figure 8: Various poses of hand placement
Figure 9:fingertip and valley points of a hand Figure 10: Features Extraction of hand
After pre-processing, 19 features have been extracted(9
fingertip and valley point, 4 widths, 5 heights) where width is
the distance from thumb valley point to all fingers valley point
and Height is the height of the all the finger is measured as
shown in Figure 10.
D. Matching
The feature matching determines the degree of similarity
between stored feature vector and claimed feature vector.
TheAs shown in figure 10 feature vector obtained fromthe
input image which is matched against the features vector of
images in the database. It is not necessary that under the best
of condition the obtained features match exactly with the
features of the same individual. The extracted features are in
the form of positive integer. These are referred to as
magnitude of the features. Absolute distance function is
defined as [7].
D
a
= (Yi Fi)
n
=1
(1)
Where, Fi=h(F1,F2,F3Fd) is the feature vector with d
dimension of a registered user in the database,
Y
i
=h(Y
1
,Y
2
,Y
3
.Yd) is the features vector of an
unknown or a claimer and
F
i
is the mean of the 50 feature vector of 50registered person.
Therefore distance between claimer features vector Y
i
and
database feature vector F
i
is shown in following equation:
Match Value=
AbsoIutcdstuncc
No.o]]cutucs
(2)
After calculating the match, the system has compared the
result with the predefined threshold and classifies the claimer.
The systemaccepts the claimer if and only if the calculated
match value is lower than the threshold and it rejects the
claimer if and only if the calculated distance is higher than the
threshold [7].
III. SIMULATION RESULTS
The systemhas been tested on 500 images. Database of this
systemconsist of 10 different acquisitions of 50 people. These
images have contained some images of the same individuals
taken at different time intervals. Since no pegs are used to
align the position of the palmit is obvious that the alignment
may vary for the images of the same individual. Although a
slight rotation is acceptable the system is not completely
rotation invariant [6]. One image of each users hand was
selected to compute the feature vector which is stored in the
database along with the users name. The authentication refers
International Journal of Computer Trends and Technology (IJCTT) volume4Issue8August 2013
ISSN: 2231-2803http://www.ijcttjournal.org Page 2780
to the problemof confirming or denying a claim of individuals and considered as one to one matching.
Figure 11:Results of Hand Geometry Measurement
Figure 12:Fingertipand valley point of hand
Figure 13:Distance fromthumb to all fingers valley point
Figure 14: Distance fromtip point to valley point
There are various performance measurement parameters of
this proposed work, these are explained below:
1) False Acceptance rate (FAR):In access control
systems, a false acceptance occurs when a sample is
incorrectly matched to a different users template in a
database (in the case of an access control system, an
impostor is allowed in the building)[2].
FAR =
1otuI PuIsc Acccptuncc
1otuI PuIsc Rc]ccton
(3)
2) False Rejection rate (FRR): A false rejection
occurs when a sample is incorrectly not matched to
an otherwise correct matching template in the
database (in the case of an access control system, a
legitimate enrolee is falsely rejected)[2].
FRR =
1otuI PuIsc Rc]ccton
1otuI tuc uttcmts
(4)
3) Equal Error Rate (EER): Error rate is a point
where FRR and FAR are same. The ERR is an
indicator on how accurate the device is lower the
ERR is the better the system. The results of this
experiment shows that EER=3%. The graph between
error and threshold is shown in Figure 12[2].
International Journal of Computer Trends and Technology (IJCTT) volume4Issue8August 2013
ISSN: 2231-2803http://www.ijcttjournal.org Page 2781
Figure 12: FAR-FRR CURVE(graph between error and threshold)
shows that EER=3%.
IV. CONCLUSION AND FUTURE WORK
A peg free hand geometry authentication systemhas been
developed in this work which is independent of orientation
and placement of the hand. The systemis experimented with a
database consisting of 500 images collected over time from 50
users. Ten sample images from each user were used for
authentication purpose. The authentication system extracts
feature vector from the image and stores the template for later
authentication. FRR is obtained by comparing the features
vector of two different hands. The systemshows effectiveness
of results with accuracy around 97%. The ERR is found to be
3%.
The proposed work utilizes primarily the geometry of the
hand. The palm creases and even the fingerprints can be
extracted fromthe input image. Combining all these features
in biometrics would result in a multimodal systemwith very
high accuracy. The image extracted is in grayscale format. If a
colour image is utilized for the system additional features such
as the colour of the palmcan also be used. For huge databases
the search takes a long time and colour is so distinct. A feature
that it can be used as an initial classifier so as to narrow the
search space in the database considerably. The use of neural
network based classifier trained on a larger database may
result in further improvement of the system accuracy.
REFERENCES
[1] Rashmi Singhal and Payal J ain, "Biometrics:Enhancing Security,"
Asian J ournal of computer science and information technology,
pp. 89-92, 2011.
[2] Biometric Technology Application Manual Volume
One:Biometric Basics Compiled and Published By National
Biometrics Security Project Updated Summer 2008.
[3] R. Sanchez-Reillo, C. Sanchez-Avila, A. Gonzalez-Marcos,
Biometric Identification Through Hand Geometry
Measurements, IEEETrans. on PAMI, vol. 22, no. 10, pp. 1168-
1171, October 2000.
[4] K. J ain, N. Duta, Deformable Matching of Hand Shapes for
Verification, Proc. of IEEE International Conference on
ImageProcessing, Kobe, October1999.
[5] K. J ain, A. Ross, S. Pankanti, A Prototype Hand Geometry-based
Verification System, 2nd Int. Conference on Audio- and
VideobasedPersonal Authentication (AVBPA), Washington, pp.
166-171March 1999.
[6] Y. Bulatov, S. J ambawalikar, P. Kumar, and S. Sethia, Hand
recognition usinggeometric classifiers. 1999.
[7] N Covavisaruch,P Prateepamornkul, P Ruchikachorn and P
Taksaphan,Personal Verication and Identication Using Hand
Geometry , ECTI TRANSACTIONS ON COMPUTER AND
INFORMATION TECHNOLOGY, vol.1, no.2, November 2005.
[8] Sampda A Dhole and V.H. Patil, "Person identification using
pegfree hand geometry measurement," International journal of
engineering science and technology, vol. 4, no. 6, 2012.
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (894)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Horizon Trial: Torstein Godeseth 1st Witness StatementDocument20 pagesHorizon Trial: Torstein Godeseth 1st Witness StatementNick WallisNo ratings yet
- MyDFIR RoadmapDocument22 pagesMyDFIR Roadmapmanishkharwar.hhNo ratings yet
- Make Money With SurveysDocument13 pagesMake Money With SurveysApril Twinkletoes100% (2)
- Optimal Search Results Over Cloud With A Novel Ranking ApproachDocument5 pagesOptimal Search Results Over Cloud With A Novel Ranking ApproachseventhsensegroupNo ratings yet
- FPGA Based Design and Implementation of Image Edge Detection Using Xilinx System GeneratorDocument4 pagesFPGA Based Design and Implementation of Image Edge Detection Using Xilinx System GeneratorseventhsensegroupNo ratings yet
- Comparison of The Effects of Monochloramine and Glutaraldehyde (Biocides) Against Biofilm Microorganisms in Produced WaterDocument8 pagesComparison of The Effects of Monochloramine and Glutaraldehyde (Biocides) Against Biofilm Microorganisms in Produced WaterseventhsensegroupNo ratings yet
- Experimental Investigation On Performance, Combustion Characteristics of Diesel Engine by Using Cotton Seed OilDocument7 pagesExperimental Investigation On Performance, Combustion Characteristics of Diesel Engine by Using Cotton Seed OilseventhsensegroupNo ratings yet
- High Speed Architecture Design of Viterbi Decoder Using Verilog HDLDocument7 pagesHigh Speed Architecture Design of Viterbi Decoder Using Verilog HDLseventhsensegroupNo ratings yet
- Application of Sparse Matrix Converter For Microturbine-Permanent Magnet Synchronous Generator Output Voltage Quality EnhancementDocument8 pagesApplication of Sparse Matrix Converter For Microturbine-Permanent Magnet Synchronous Generator Output Voltage Quality EnhancementseventhsensegroupNo ratings yet
- An Efficient Model of Detection and Filtering Technique Over Malicious and Spam E-MailsDocument4 pagesAn Efficient Model of Detection and Filtering Technique Over Malicious and Spam E-MailsseventhsensegroupNo ratings yet
- Fabrication of High Speed Indication and Automatic Pneumatic Braking SystemDocument7 pagesFabrication of High Speed Indication and Automatic Pneumatic Braking Systemseventhsensegroup0% (1)
- Extended Kalman Filter Based State Estimation of Wind TurbineDocument5 pagesExtended Kalman Filter Based State Estimation of Wind TurbineseventhsensegroupNo ratings yet
- A Multi-Level Storage Tank Gauging and Monitoring System Using A Nanosecond PulseDocument8 pagesA Multi-Level Storage Tank Gauging and Monitoring System Using A Nanosecond PulseseventhsensegroupNo ratings yet
- Color Constancy For Light SourcesDocument6 pagesColor Constancy For Light SourcesseventhsensegroupNo ratings yet
- An Efficient and Empirical Model of Distributed ClusteringDocument5 pagesAn Efficient and Empirical Model of Distributed ClusteringseventhsensegroupNo ratings yet
- Comparison of The Regression Equations in Different Places Using Total StationDocument4 pagesComparison of The Regression Equations in Different Places Using Total StationseventhsensegroupNo ratings yet
- Design, Development and Performance Evaluation of Solar Dryer With Mirror Booster For Red Chilli (Capsicum Annum)Document7 pagesDesign, Development and Performance Evaluation of Solar Dryer With Mirror Booster For Red Chilli (Capsicum Annum)seventhsensegroupNo ratings yet
- Implementation of Single Stage Three Level Power Factor Correction AC-DC Converter With Phase Shift ModulationDocument6 pagesImplementation of Single Stage Three Level Power Factor Correction AC-DC Converter With Phase Shift ModulationseventhsensegroupNo ratings yet
- Ijett V5N1P103Document4 pagesIjett V5N1P103Yosy NanaNo ratings yet
- Design and Implementation of Height Adjustable Sine (Has) Window-Based Fir Filter For Removing Powerline Noise in ECG SignalDocument5 pagesDesign and Implementation of Height Adjustable Sine (Has) Window-Based Fir Filter For Removing Powerline Noise in ECG SignalseventhsensegroupNo ratings yet
- The Utilization of Underbalanced Drilling Technology May Minimize Tight Gas Reservoir Formation Damage: A Review StudyDocument3 pagesThe Utilization of Underbalanced Drilling Technology May Minimize Tight Gas Reservoir Formation Damage: A Review StudyseventhsensegroupNo ratings yet
- Study On Fly Ash Based Geo-Polymer Concrete Using AdmixturesDocument4 pagesStudy On Fly Ash Based Geo-Polymer Concrete Using AdmixturesseventhsensegroupNo ratings yet
- Separation Of, , & Activities in EEG To Measure The Depth of Sleep and Mental StatusDocument6 pagesSeparation Of, , & Activities in EEG To Measure The Depth of Sleep and Mental StatusseventhsensegroupNo ratings yet
- An Efficient Expert System For Diabetes by Naïve Bayesian ClassifierDocument6 pagesAn Efficient Expert System For Diabetes by Naïve Bayesian ClassifierseventhsensegroupNo ratings yet
- An Efficient Encrypted Data Searching Over Out Sourced DataDocument5 pagesAn Efficient Encrypted Data Searching Over Out Sourced DataseventhsensegroupNo ratings yet
- Non-Linear Static Analysis of Multi-Storied BuildingDocument5 pagesNon-Linear Static Analysis of Multi-Storied Buildingseventhsensegroup100% (1)
- Review On Different Types of Router Architecture and Flow ControlDocument4 pagesReview On Different Types of Router Architecture and Flow ControlseventhsensegroupNo ratings yet
- Ijett V4i10p158Document6 pagesIjett V4i10p158pradeepjoshi007No ratings yet
- Key Drivers For Building Quality in Design PhaseDocument6 pagesKey Drivers For Building Quality in Design PhaseseventhsensegroupNo ratings yet
- Free Vibration Characteristics of Edge Cracked Functionally Graded Beams by Using Finite Element MethodDocument8 pagesFree Vibration Characteristics of Edge Cracked Functionally Graded Beams by Using Finite Element MethodseventhsensegroupNo ratings yet
- A Review On Energy Efficient Secure Routing For Data Aggregation in Wireless Sensor NetworksDocument5 pagesA Review On Energy Efficient Secure Routing For Data Aggregation in Wireless Sensor NetworksseventhsensegroupNo ratings yet
- A Comparative Study of Impulse Noise Reduction in Digital Images For Classical and Fuzzy FiltersDocument6 pagesA Comparative Study of Impulse Noise Reduction in Digital Images For Classical and Fuzzy FiltersseventhsensegroupNo ratings yet
- Performance and Emissions Characteristics of Diesel Engine Fuelled With Rice Bran OilDocument5 pagesPerformance and Emissions Characteristics of Diesel Engine Fuelled With Rice Bran OilseventhsensegroupNo ratings yet
- Chap4 RSA TutorialDocument3 pagesChap4 RSA TutorialGrace Xiao HanNo ratings yet
- Nbi Vs HwangDocument11 pagesNbi Vs HwangRhei BarbaNo ratings yet
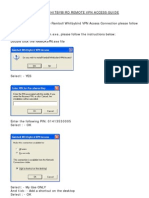
- Ramboll Whit by Bird Remote VPN Access GuideDocument6 pagesRamboll Whit by Bird Remote VPN Access Guidecarol_lewisNo ratings yet
- MATH2114 Numerical LN2Document24 pagesMATH2114 Numerical LN2was122333gmail.comNo ratings yet
- Calculus I - Ursinus College Math 111Document7 pagesCalculus I - Ursinus College Math 111Manoel RendeiroNo ratings yet
- Pangas in AnDocument67 pagesPangas in AnIris ManansalaNo ratings yet
- SMS Software User Guide: Symmetry™ Security ManagementDocument34 pagesSMS Software User Guide: Symmetry™ Security ManagementRatan KumarNo ratings yet
- Locking and Unlocking of Automobile Engine Using RFID1Document19 pagesLocking and Unlocking of Automobile Engine Using RFID1Ravi AkkiNo ratings yet
- Defending Elections: Federal Funding Needs For State Election SecurityDocument10 pagesDefending Elections: Federal Funding Needs For State Election SecurityThe Brennan Center for JusticeNo ratings yet
- Robert Smith: Information Security Engineer - Part TimeDocument2 pagesRobert Smith: Information Security Engineer - Part TimeKumaranNo ratings yet
- Intranet and Internet Security Policy - Sample 2Document7 pagesIntranet and Internet Security Policy - Sample 2Dennis Bacay100% (1)
- IT 29 May 2008Document8 pagesIT 29 May 2008Jagdeesh GosineNo ratings yet
- Student Registration System SRSDocument23 pagesStudent Registration System SRSAmani Idd MrishoNo ratings yet
- CSCU Module 12 Information Security and Legal Compliance PDFDocument12 pagesCSCU Module 12 Information Security and Legal Compliance PDFSandeep Roy100% (1)
- A Fuzzy & K-L Based Reduced Reference ImageQualityDocument4 pagesA Fuzzy & K-L Based Reduced Reference ImageQualityIOSRjournalNo ratings yet
- YL-007M5B Alarm SystemDocument16 pagesYL-007M5B Alarm SystemDa PoNo ratings yet
- Numeric To Numeric Encryption of Databases Using 3kDES AlgorithmDocument5 pagesNumeric To Numeric Encryption of Databases Using 3kDES AlgorithmSwathi VasudevanNo ratings yet
- Security Incident Reporting 1Document9 pagesSecurity Incident Reporting 1Anonymous Fhs3ufkCNo ratings yet
- DentalDocument2 pagesDentalJohn Gabriel LibutNo ratings yet
- Viva Cheat SheetDocument6 pagesViva Cheat SheetRahul SharmaNo ratings yet
- Cyber Security Course 5Document19 pagesCyber Security Course 5Cristina PaliuNo ratings yet
- Whodunit Case StudyDocument1 pageWhodunit Case StudyAnna LiuNo ratings yet
- Mach3 V3.x Programmer Reference Draft v0.11Document141 pagesMach3 V3.x Programmer Reference Draft v0.11Alexandre OliveiraNo ratings yet
- Seclore Data-Centric Security PlatformDocument2 pagesSeclore Data-Centric Security PlatformJulie SmithNo ratings yet
- DFD PDFDocument14 pagesDFD PDFRio ArdianNo ratings yet
- TGTDCL Gzaw3vDocument2 pagesTGTDCL Gzaw3vbasum matNo ratings yet
- 10 Steps To Cyber Security PDFDocument20 pages10 Steps To Cyber Security PDFmillian0987100% (1)