Professional Documents
Culture Documents
Stevenson College - Graded Unit-1
Uploaded by
karagenskiOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Stevenson College - Graded Unit-1
Uploaded by
karagenskiCopyright:
Available Formats
[Type the document title]
Page 1 of 53
CONTENTS PAGE
[Type the document title]
Page 2 of 53
PLANNING
STAGE
[Type the document title]
Page 3 of 53
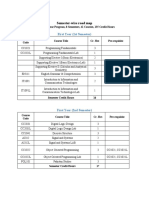
1.1 Project Plan
1.1.1 Identify Main Tasks
Once I had read Project Schedule I pin-pointed and listed the entire Main tasks and subtasks
and listed them in a Gantt chart so the information is easy to read and understand what is
happening and when it is happening.
The Gantt chart can be seen in Appendix A (Gantt chart).
1.1.2 Identify Milestones
Project Stage Submission Date
Planning Stage 28
th
February 2013
Development Stage 1 19
th
March 2013
Development Stage 2 18
th
April 2013
Evaluation 15
th
May 2013
[Type the document title]
Page 4 of 53
1.2 Identify Requirements
1.2.1 Networks Current Usage
After reading and analysing the information I was provided, I have came up with a list
of the organizations current network usage:
The network contains a collision domain of 254 nodes
Unmanaged hubs are used to gain access to the backbone of the network
1 single Baystack router handles all traffic entering and leaving the network
10 Mbps cabling used for the Colleges backbone, connectivity to end devices, and
WAN services including Internet access via the local University.
All web access is via a proxy server that continually hangs as it is unable to cope with
the current amount of traffic
Windows NT server is used to verify standard login
There is no distinction between students, teaching and administrative staff
Each lab uses a workgroup with a printer
The network utilises NetBeui, TCP/IP, and AppleTalk protocols
There are no restrictions in place to prevent misuse of the Internet facilities
All software is loaded locally onto the Hard Drive of each machine
All e-mail goes through a single Sun Netra server
The Administrative system runs on a Sun Sparc server
The remote sites of Dun Learning and No More are not connected into the network
A firewall server checks all incoming packets and filters all traffic entering and
leaving the network
A Windows NT based server provides access to the P: network drive
A Linux Server is available for the tuition of Unix classes
A link to the local University currently provides access to Super Janet III
The DNS server is contained within the Sun Netra e-mail server running under Solaris
Only staff have e-mail accounts
MCP courses are currently running within the college and thus, 8 machines need to be
multiboot to accommodate a Windows 2000 server
A proxy server using Windows Proxy Server 2.0 running under Windows NT 4.0
caches all web pages locally to reduce WAN traffic
Very basic IP addressing scheme
[Type the document title]
Page 5 of 53
1.2.2 Future Requirements
My plan is to build a network that is Scalable, reliable, flexible, available, and fault tolerant
for the next 10 years due to a projected 100% growth in business within this time. I will
achieve this by implementing the following:
High speed WAN/LAN connections
Connect directly to the SuperJanet 5 network and remove the local Universities
influence over the system
All wiring should conform to EIA/TIA standards
1 Single Routing protocol used throughout the Network
All classrooms (used & empty) require a connection to access the Network with the
correct number of ports and devices
E-mail for all Students and Staff
A scalable IP addressing scheme
Introduce Variable Length Subnet Masking to build a private and more secure internal
network using the IP addresses provided (215.29.151.0, 215.29.152.0, 215.29.153.0,
and 185.158.0.0)
Implementation of NAT/PAT to conserve public address space
Firewall to be placed at the main college facility and a Firewall at each outlying site
Each site location will have an Administration server
Physical security of equipment
DNS and E-mail will be located on the master server in the MDF
Each site will have a DNS host and E-mail services
All DNS servers will be able to communicate with each other
Distinction between Students, Staff, and Management
Implement Anti-Virus to protect Network
Minimum number of useable PCs, Printers, Servers, Scanners
Each outlying site will connect to the main site so teaching and administrative staff
can connect to each other
1.2.4 User Questionnaire
See Appendix B for User Questionnaire.
[Type the document title]
Page 6 of 53
1.3 Physical Layer Topology
1.3.1 Layer 1 Topologies
[Type the document title]
Page 7 of 53
A full explanation for all of these topologies is in Appendix C (Physical Layer Topology)
All information for this topic was found at
http://www.completepcpedia.com/ &
http://www.ianswer4u.com
Mesh Topology
Advantages of Mesh Topology:
1. Data can be transmitted from different devices simultaneously, thus making it
withstand high traffic.
2. If 1 device fails then there is an alternative route, so data transfer doesnt get affected.
3. Expansion and modification in topology can be done easily without disrupting other
devices.
4. Since messages are sent along a dedicated link, the topology is more secure.
Disadvantages of Mesh Topology
1. Set-up and maintenance of this topology is very difficult.
2. Very expensive compared to other topologies because of a higher length of cable is
required
This is a very good topology to use to ensure your network is redundant, but is also very
expensive to implement and maintain. I will be implementing the partial mesh on switches in
the Core, Distribution, and Access layer for my Advanced Network.
Bus Topology
Advantages of Bus Topology
It is easy to set-up and to expand bus network.
[Type the document title]
Page 8 of 53
There is little cable length required when compared to other network topologies.
If one node breaks down the network doesnt go down.
Nodes can easily be removed.
It is suitable for smaller networks.
Disadvantages of Bus Topology
If there is a problem with the backbone then the whole network is rendered useless.
The efficiency of the Bus network reduces, as the number of devices connected
increases.
Maintenance costs can get higher with time.
It is not suitable for networks with a heavy amount of traffic.
Not very secure as all computers connected receive the message sent from the source.
There is a limit on cable length and the number of devices that can be added.
It is difficult to detect and troubleshoot fault at an individual station.
The data transfer rate will slow down as more nodes are connected.
I will not be implementing this topology.
Star Topology
Advantages of Star Topology
Easy to set-up and implement
[Type the document title]
Page 9 of 53
Better performance as messages dont pass through various nodes unlike the bus
topology.
Faulty nodes can easily be removed without affecting the network and vice versa.
As there is centralized management, it helps monitoring the network.
Disadvantages of Star Topology
If the central node fails then the whole network is down.
The number of nodes is limited to the amount of physical connections the central
device has.
The more nodes that are connected to the central device then the more the central
devices performance deteriorates.
The more nodes that are added the more cable you need, which increases the cost.
I will be implementing this topology to give end devices connectivity to the network. This
will be at the access layer.
Ring Topology
Advantages of Ring Topology
This topology is very organized, because each node can only send data when it
receives an empty token it reduces the chance of a collision.
All traffic flows in only 1 direction at a very high speed.
Even when the load on the network increases, its performance is better than the bus
topology.
[Type the document title]
Page 10 of 53
There is no need for a network server to control the connectivity between computers.
Additional computers will not affect the performance of the network.
Each computer has equal access to resources.
Disadvantages of Ring Topology
Each packet of data must pass through all the computers between the source and
destination, making it slower than the Star Topology.
If 1 workstation or port goes down the entire network is affected.
The network is highly dependent on the wire which connects all the workstations.
It is difficult to add/remove workstations.
As you can see this topology would be slower than the Star
topology, and as speed is highly important in my network I
will not be choosing this topology.
Tree Topology
[Type the document title]
Page 11 of 53
Advantages of Tree Topology
It is an extension of Star and Bus topologies, so in networks where these topologies
cant be implemented individually for reasons related to scalability, tree topology is
the best alternative.
Expansion of the network is possible and easy.
As we can divide the whole network into segments (Star Networks), we can easily
manage and maintain the network.
Error detection and correction is easy.
If 1 segment is damaged, other segments are not affected.
Each segment is provided with dedicated point-to-point wiring to the central node.
Disadvantages of Tree Topology
As it has a basic structure the whole network is dependent on Bus cable, so if that
goes down, the whole network goes down.
As more and more nodes and segments are added, the maintenance becomes more
difficult.
Scalability of the network depends on the type of cable used.
I will not be implementing this topology.
1.4 Logical Layer Topology
[Type the document title]
Page 12 of 53
There is a full explanation of the Data Link Layer in Appendix D (Logical Layer Topology)
1.4.1 Identification of Collision Domains
A Collision Domain, occurs when more than 1 device (connected to an internetworking
device) transmits data at the same time. Collisions are resolved by using a Carrier Sense
Multiple Access with Collision Detection (CSMA/CD) in which the competing packets are
discarded and re-sent 1 at a time. As only one device may be transmitting at any one time,
total network bandwidth is shared among all devices IF using a hub. If using a switch then
every port is considered a separate collision domain in the case of half duplex link. The
possibility of collisions is eliminated entirely in the case of full duplex links. Collisions also
decrease network efficiency on a collision domain; if two devices transmit simultaneously, a
collision occurs, and both devices must retransmit at a later time. Collision domains are also
found in wireless networks such as Wi-Fi.
1.4.2 Identification of Broadcast Domains
A Broadcast Domain is when all devices receive any broadcast packet originating from any
device within the Broadcast Domain. A Broadcast Domain can only go as far as a Router, as
the router doesnt forward broadcast packets. A switch will act as a buffer and check all the
data packets, or frames, being sent between computers. Only when a broadcast frame is sent
do all computers on the broadcast domain receive the frame, otherwise the switch sends the
frames to the receiving computer only.
This picture shows collisions domains as well as broadcast domains.
1.5 IP Addressing Scheme
[Type the document title]
Page 13 of 53
1.5.1 How Many End Devices
Admin Network - I will consider every device that will need an IP address for the simple
network design. I will show another table later on that will also allow for the 100% expected
growth in the network. Some servers will have more than 1 NIC so there is less chance of
bottlenecks.
Room WAN
Link
PCs Printers
+
Scanners
Server Router LAN Interfaces Total Number
of Hosts
POP/MDF 4 4 1 3 2 14
Stores 0 6 1 0 0 7
Accommodation
and Welfare
0 6 1 0 0 7
Business Studies
Support
0 12 1 0 0 13
Training
Initiatives Flexi
0 4 1 0 0 5
Training
Initiatives
0 4 1 0 0 5
148 0 7 1 0 0 8
Faculty Office 0 10 1 0 0 11
International
Business
Development
0 8 1 0 0 9
Facilities
Management
0 4 1 0 0 15
Desk Top
Publishing
0 8 7 0 0 15
Assistant
Principal
0 2 1 0 0 3
Director Finance 0 1 1 0 0 2
Personnel 0 6 1 0 0 8
Payroll 0 1 1 1 0 3
College Office 0 30 2 0 0 32
Principal 0 4 1 0 0 5
Principals
Secretary
0 8 1 0 0 9
Library 0 6 1 1 0 8
CSU 0 18 1 0 0 19
Audio Visual 0 4 1 0 0 5
Support unit 0 4 1 0 0 5
College Secretary 0 4 1 0 0 5
IDF/Each floor 0 0 0 9 0 9
Fica Test Centre 0 16 1 0 0 17
Total Hosts = 239
[Type the document title]
Page 14 of 53
Teaching Network -I will consider every device that will need an IP address for the simple
network design. I will show another table later on that will also allow for the 100% expected
growth in the network.
Room WAN Link PCs Printers Servers Router LAN Interfaces Total No of Hosts
Hardware
Lab
0 16 2 0 0 18
Special
needs 1
0 20 2 0 0 22
Special
needs 2
0 20 2 0 0 22
113 0 16 2 0 0 18
114 0 16 2 0 0 18
119 0 16 2 0 0 18
Multi Media
audio visual
0 18 2 0 0 20
CAD lab 0 14 2 1 0 17
Library 0 14 2 0 0 16
Flexi centre 0 16 2 0 0 18
New Flexi
Centre
0 20 2 0 0 22
208 0 16 2 0 0 18
210 0 16 2 0 0 18
211 0 18 2 0 0 20
212 0 26 2 0 0 28
215 0 26 2 0 0 28
303 0 20 2 0 0 22
312 0 26 2 0 0 28
313 0 18 2 0 0 20
317 0 32 3 0 0 35
324 0 20 2 0 0 22
325 0 20 2 1 0 23
326 0 20 2 1 0 23
411 0 32 3 0 0 35
427 0 16 2 0 0 18
Health and
Safety Flexi
0 16 2 0 0 18
Flexi Centre
Health
0 16 2 0 0 18
Flexi Maths 0 6 1 0 0 7
Staff
Rooms*39
0 78 39 0 0 117
Total Hosts = 707
[Type the document title]
Page 15 of 53
DMZ There wont be a DMZ until the 2
nd
Proposed Design.
Server No of NICs
AD DS + DNS + Licensing + WSUS (active) 2
AD DS + DNS + Licensing + WSUS Backup
(passive)
2
Email Server (active) 2
Email Server Backup (passive) 2
Web Server (active) 2
Web Server Backup (passive) 2
Anti-Virus Server (active) 2
Anti-Virus Server Backup (passive) 2
Proxy Server (active) 2
Proxy Server Backup (passive) 2
Linux Server for HNC Students 1
Teaching Server P:Network Drive 1
Library Server connecting to British Libraries 1
Total Hosts = 23
Admin Network = 239
Teaching Network = 707
DMZ = 23
[Type the document title]
Page 16 of 53
1.5.2 Class B & Class C Addressing Scheme
I have been give these 4 IP Ranges
215.29.151.0
215.29.152.0
215.29.153.0
185.158.0.0
Now to allocate IP addresses to the network I will use a simplified VLSM approach. This
means that all subnets use the same prefix length and same number of host bits.
I will use the IP range 185.158.0.0 as it is a class B IP address and has 65536 IP addresses,
although I only need 707. I will have to borrow 10 host bits, and I will use this formula, 2 ^n
-2 (where n is the amount of bits borrowed) to calculate the amount of useable addresses.
2 ^10 = 1024
1024-2 = 1022 useable hosts
1022 useable hosts now meets the requirement for 707 addresses with an allowance for
growth. This leaves 22 network bits as there is 32 total bits the 10 host bits I borrowed.
This gives me a Subnet Mask of 255.255.252.0 and a prefix of /22 (32-10=22)
So the 2 networks will have 4 blocks of 1024 addresses.
My address block is 185.158.0.0 /22
Network Subnet Host Range Broadcast Address
Admin 185.158.0.0 /22 185.158.0.1 185.158.3.254 185.158.3.255
Teaching 185.158.4.0 /22 185.158.4.1 185.158.7.254 185.158.7.255
The problem we have with this is that there is a massive amount of wasted addresses; I will
explain how I will use a more efficient method of subnetting in the Development Stage. You
can see the amount of wasted addresses in this table for each network.
Network Total No of Useable Addresses Actual Requirements Wasted Addresses
Admin 1022 239 1022 239 = 783
Teaching 1022 707 1022 707 = 315
[Type the document title]
Page 17 of 53
1.6 Choosing Physical Media
There is a full explanation of Cabling Types, EIA/TIA Standards, and a cut sheet in
Appendix F.
End Devices
Device Ethernet
Type
Bandwidth Cable Type Max Distance
PC/Servers 1000Base-TX 1Gbps Cat6 UTP 100m
Printer 1000Base-TX 1Gbps Cat6 UTP 100m
Admin Servers 10GBase-T 10Gbps Cat6a UTP 100m
Application Servers 10GBase-T 10Gbps Cat6a UTP 100m
Backbone
Device Ethernet Type Bandwidth Cable Type Maximum Distance
Core to Distribution 10GBase-S 10Gbps Multimode
Fiber
300m
Distribution to Access 10GBase-S 10Gbps Multimode
Fiber
300m
Ethernet Type Bandwidth Cable Type Maximum Distance
10Base-T 10Mbps Cat3/Cat5 UTP 100m
100Base-TX 100Mbps Cat5 UTP 100m
100Base-TX 200Mbps Cat5 UTP 100m
100Base-FX 100Mbps Multi-Mode Fiber 400m
100Base-FX 200Mbps Multi-Mode Fiber 2Km
1000Base-T 1Gbps Cat5e UTP 100m
1000Base-TX 1Gbps CAT6 UTP 100m
1000Base-SX 1Gbps Multi-Mode Fiber 550m
100Base-LX 1Gbps Single Mode Fiber 2Km
10GBase-T 10Gbps Cat6a/Cat7 UTP 100m
10GBase-LX4 10Gbps Multi-Mode Fiber 100m
10GBase-S 10Gbps Multi-Mode Fiber 300m
10GBase-LX4 10Gbps Single Mode Fiber 10Km
[Type the document title]
Page 18 of 53
1.7 Three Tier Hierarchical Explanation
A 3 Tier Hierarchical design was designed by Cisco and developed their system according to
this model. Cisco recommends their end-users to follow suit. There are 3 Layers to this
model, Core Layer (Top), Distribution Layer (Middle), and Access Layer (Bottom). When
compared to other network designs the Hierarchical design is easier to manage and expand,
as well as easier to identify and correct problems within the network.
When designing a hierarchical network topology, one of the 1
st
things to consider is Network
Diameter. This is a measure of distance or devices that a packet has to cross before reaching
its destination. The lower the network diameter the lower the latency is between devices.
Bandwidth aggregation is important when designing a network. This is where links between
specific switches can be aggregated (also known as link aggregation) and allows higher
throughput between switches for certain parts of the network that need it.
Redundancy is very important in the hierarchical design. This can be done by either doubling
up the network connections between devices or doubling up the devices (expensive!)
themselves. Redundancy is there so that if a link fails on a switch, the switch can use another
connection to transmit the data.
The benefits of a Hierarchical Network include:
Scalability Can be expanded easily
Redundancy Redundancy at the core and distribution layers ensure path availability
Performance Link aggregation between the layers allows near wire-speed
throughout the network
Security Port security at the access layer and policies at the distribution layer make
the network more secure
Manageability Consistency between switches at each level makes management
more simple
Maintainability The design of the model allows the network to scale without
becoming overly complicated
1. Access Layer This layer interfaces with devices that are accessing the network, such as
PCs, printers, IP Phones, and in some cases servers. This layer can include routers,
switches, bridges, hubs, and wireless access points. Other features of the access layer
include:
MAC Address Filtering Program the switch to only allow certain end devices to
access the connected LANs.
Create separate collision domains The switch can create separate collision
domains for each connected node to improve performance.
[Type the document title]
Page 19 of 53
2. Distribution Layer This layer receives all the data from the access layer and aggregates
(collects and forms together) it before sending it off to the core layer. The flow of
network traffic is controlled by the switch(s) in the distribution layer using policies.
Broadcast domains are identified and kept within the boundary from which network they
came from, this is done by performing routing functions between VLANs that are defined
at the access layer. VLANs allow you to segment the traffic on a switch into separate
subnetworks. Switches in the distribution layer are high-performance devices that have
high availability and redundancy to ensure reliability. Functions that are preformed at the
distribution layer include:
ACLs Access Control Lists that filter traffic based on their configuration.
Security Implementing policies containing address translation and firewalls.
Routing between VLANs.
Defining broadcast and multicast domains.
3. Core Layer The Core Layer of this design is the high-speed backbone of the
internetwork and is super critical for connectivity between distribution layer devices. As
the core layer is critical to the functioning of the network design the devices in this layer
have to be highly available and redundant. The core layer can also connect to Internet
resources if needs be. Just like the distribution layer, the core layer aggregates the data
received from the layer below (distribution layer) so it must be capable of forwarding
large amounts of data quickly.
I got all this information from CCNA Exploration 4.0 LAN Switching and Wireless
[Type the document title]
Page 20 of 53
1.8 Choosing Equipment
1.8.1 Hubs, Switches, and Routers
Hub
A hub receives a signal, regenerates it, and sends the signal over all ports. They broadcast all
traffic they receive to all devices attached, so collisions are more likely to occur.
Although multiple hubs can be interconnected they remain a single collision domain.
There are 3 different types of hubs:
Passive This means that the hub doesnt view or interact with the traffic travelling
through it. It does not need electrical power.
Intelligent Also known as Smart Hubs, these are more expensive than other hubs
but are more useful than active hubs in troubleshooting.
Active This is the most common type of hub, it will receive a signal and amplify it
before sending it out all other ports. It must be plugged into an electrical outlet.
Hubs are very rarely used nowadays but if you were to find one, they would be within a
very small LAN that requires low throughput and finances are limited.
Switches
A switch is used in a wired network to allow communication between devices. Switches
receive frames and regenerate them before sending to the appropriate destination. The
switch filters and forwards packets between LANs. They operate at the Data Link Layer
(layer 2) of the OSI model, meaning that they use MAC addresses to determine hosts. They
can sometimes operate at the Network Layer (layer 3) and therefore support any packet
protocol. Each port on the switch creates a separate collision domain, reducing the collisions
on the LAN as a whole.
Switches have a number of advantages:
Allow dozens of devices to communicate
Allows control of who has access to various parts of the network
Allows you to monitor usage
Reduce the number of broadcast domains
Supports VLANs (which then breaks up broadcast domains)
Intelligent device Make use of CAM table for Port to MAC mapping
Cheaper to implement than routers when based on the number of ports you need
Provides dedicated bandwidth on each port Increased LAN performance
Stackable Connect another switch to existing switch to increase number of available
ports to use
[Type the document title]
Page 21 of 53
Layer 3 Switches operate at the Network Layer of the OSI model and are high-performance
devices for network routing. This type of switch differs very little from a router. They support
the same routing protocols, they inspect incoming packets and make dynamic routing
decisions based and on the source and destination address inside the packet. Layer 3 switches
do not have WAN ports. Layer 3 switches are stackable.
Routers
Routers are physical devices that join multiple networks together. The router acts as a
gateway to the Internet and other networks to everyone on the network. The router operates at
the Network Layer of the OSI model as it deals with IP addresses. The router will receive a
packet from one network, and depending on the header of the packet, and will look up the
destination address in its routing table and send the packet on its way. Routers also have the
ability to break up broadcast domains and collision domains. They use routing protocols to
advertise networks and store network addresses in their routing table, routing protocols are
explained in the development stage 1.
Routers can be used to multitask including:
Firewall
VPN
IP Services
I got all the information from http://compnetworking.about.com/
Switch
Hub
Router
[Type the document title]
Page 22 of 53
1.9 Finalizing the Network
1.9.1 Proposed Designs
2
nd
Proposed Design
[Type the document title]
Page 23 of 53
1.9.2 Justification for the Designs
The 1
st
design is just very basic network design. It consists of a router, 4 switches, firewall,
and end devices.
It shows internal servers for teaching and student use, as well as the servers for the
administration network.
There is no DMZ.
The only security this design offers is the firewall that is situated at the Edge router.
This proposal doesnt provide any redundancy, reliability, or scalability (as all LAN ports are
occupied). As the network is set up the way it is there will be 2 very large broadcast
domains, which isnt very efficient for the network.
The 2
nd
design offers redundancy, scalability, manageability, security, and better
performance, as I am using the 3 Tier Hierarchical Design model.
1. Redundancy There is always available links for switches to find their way to any
part/out of the network.
2. Scalability As I am using the 3 Tier Hierarchical Design (Access, Distribution, and
Core Layers) adding switches to accommodate new users wouldnt be a problem and
would be easy to manage.
3. Manageability The consistency between the switches at each level makes the
network more manageable.
4. Security I have implemented a Router/Firewall at the entrance to the network to
filter wanted/unwanted traffic. There will be ACLs implemented throughout the
network to block and allow specific traffic to specific users. VLANs will also provide
a level of security to each subnetwork, as it wont pass broadcast traffic to nodes that
are not part of the network as well as allowing the college to separate sensitive
information from the rest of the network, decreasing the likelihood that users can gain
access to this information.
For specific users that are unlikely to change (servers mainly) I will apply MAC
locking to the switch ports that these servers connect to, this will stop rogue users
accessing the network through these ports. I have also implemented a DMZ for public
servers as well as my proxy server.
5. Performance This design will provide high-availability and fast throughput
throughout the network. VLANs can reduce the number of router hops, thus
increasing the bandwidth for network users. As I am using 10Gigabit cabling to
connect all the internetworking devices my network will be very fast and will cope
with all the bandwidth requirements for all users. The 3 Tier design also supports
Quality of Service (QoS) and VoIP for future growth.
[Type the document title]
Page 24 of 53
I will implement VLANs to further segment the network into smaller broadcast domains.
This will relieve network congestion and increase bandwidth. I will be assigning different
ports to different subnetworks on the switches. The Layer 3 switches will be used for Inter-
VLAN communication to take the pressure of the router. This method is more cost effective
than having to buy more routers to provide for more networks, which will also make it very
hard to maintain and troubleshoot. The use of switches reduces the size of collision domains.
I will also be implementing NAT/PAT for using Private Addresses (RFC1918) within my
network.
Spanning-Tree Protocol (STP) will also be implemented within my network so that there are
no loops.
Rooms that have no PCs in them just now will be fitted with a faceplate that connects to a
Distribution switch so in the event that PCs are added to the room(s) the technicians will only
have to connect an Access switch to the port and the PCs to the Access Switch.
There will a Proxy server, Email Server, External Library Server, Teaching Server P:Network
Drive, Linux Server for HNC Students, Web Server, and a Active Directory + DNS + WSUS
server.
There will be 2 versions of these servers, 1 Active and 1 Passive, this means that in the event
that the Active server goes down the Passive server will take over and provide the service.
There will be an Application Server on each floor that will serve Microsoft Office
Professional 2013 to users on that floor.
[Type the document title]
Page 25 of 53
DEVELOPMENT
STAGE 1
[Type the document title]
Page 26 of 53
2.1 WAN Connections
2.1.1 Choosing WAN Link
Wide Area Networks (WANs) were introduced to meet the ever expanding business
requirements; allowing LANs to interconnect with other LANs in different geographic
scopes. There are many different types of WAN links to choose from that will allow me to
connect the two outlaying sites (Dun Learning & No More) to the main college facility. As
you can see from the diagram below I can choose either a Private Infrastructure or a Public
Infrastructure. For connecting to the two outlaying sites I shall use Broadband VPNs for
these reasons:
Eliminates the need for expensive long-distance leased lines.
Data is encrypted and therefore more secure.
Network Scalability Broadband VPN offers superior reach and QoS.
The main college building (Stevenson College) will connect to SuperJanet 5. This provides a
10Gbit/s backbone over a dedicated fibre network.
Private WAN connections include both dedicated and switched transmissions of data,
whereas a Public WAN connection uses the Internet.
[Type the document title]
Page 27 of 53
Private Dedicated Leased Lines
Leased lines are dedicated lines that are reserved by communications carriers for the private
use of customers. They are used in WAN connections when there is a requirement for high
bandwidth &permanent connections between sites. Although they provide permanent
connections, leased lines also have some disadvantages You have to pay for bandwidth that
you have even if you are not using it & increased equipment costs as each end point
connection requires its own interface, therefore meaning more equipment.
Private Switched Circuit Switched
Circuit switching dynamically establishes a dedicated virtual connection for voice and data
between a sender and receiver. Before communication can start, it is necessary to establish
the connection through the network of the service provider. PSTN (Public Switched
Telephone Network) and ISDN (Integrated Services Digital Network) are both examples of
circuit-switched communication links; these are also both analogue dial-ups so are outdated.
Private Switched Packet Switched
This method is where nodes share bandwidth with each other by sending packets
simultaneously. The most common packet-switching technology used today in WAN
networks are:
Frame Relay
This high-performance WAN protocol operates at the Physical and Data Link Layers of the
OSI model. Its a leased line and it handles data transmission over a frequently changing
path. Frame Relay has become one of the most extensively used WAN protocols, primarily
because it is inexpensive compared to dedicated lines. Frame Relay handles multiple Virtual
Circuits (VCs) using encapsulation. It provides no error correction or flow control but does
provide permanent, shared, bandwidth connectivity.
Public Internet Broadband VPN
Broadband VPN is where VPN technology is combined with broadband services such as
DSL, broadband wireless, and cable modem to provide privacy across Internet WAN
connection links. This type of connection is inexpensive and a secure way to connect remote
sites and teleworkers to the network they need to be connected to. Broadband VPNs were
designed specifically to replace Leased Lines. VPNs use strong encryption and monitor
traffic to ensure no packets have been altered.
[Type the document title]
Page 28 of 53
2.1.2 Justification of Choosing WAN Link
The main College will have its Internet supplied from SuperJanet 5, and a back up Internet
connection from an ISP.
The 2 outlaying sites (Dun Learning & No More) will be connected to the Main College
facility through Broadband VPNs as it is the least expensive and also with the use of VPN
technology the connection will be secure as it uses IPSec, a very secure protocol.
Any access to the Internet from the remote sites will be through the proxy server located in
the main college building. The firewall at the main site supports VPN technology therefore
separate software and devices for VPN connections will not be required.
Each of the remote sites will also have a firewall which will be used to connect the VPN and
also to protect the internal network traffic between the sites from exposure to possible threats.
As the remote sites are connected to the main college building through Broadband VPN
connections it will mean that they will access to all the servers including the library server
which was previously inaccessible from external sites
[Type the document title]
Page 29 of 53
2.2 Choosing Vendor Equipment
2.2.1 Routers, Switches, Firewalls, and End Devices
I have selected Cisco as my equipment vendor as Cisco is the leader in the Data Networking
Hardware Market. As the cabling has been selected I have to pick equipment that can match
the speed or even exceed these speeds.
Cisco offers a wide range of devices that range from inexpensive low-end units to expensive
high-end units. As my network is to be future-proof by 10 years I have chosen to pick high-
end devices to interconnect my network as in 10 years the high-end devices now will most
probably be considered low-end devices due to technology advancement. The high-end
devices are obviously going to be expensive but are more likely to not need replacing within
the next 10 years. You can see what appliances I have chosen in Appendix G.
[Type the document title]
Page 30 of 53
2.3 Choosing a Routing Protocol
I have a choice of several different routing protocols to implement in my network design,
these include: Distance Vector Routing, Link-State Routing, Hybrid, Dynamic Routing, and
Static Routing
Routing protocols can either be classful or classless, classful is where routers will route data
based on the class of the IP address; they DO NOT send subnet mask information with their
routing updates. A disadvantage of classful routing is that its a waste of IP addresses as you
cannot use VLSM (which can make use of all IP addresses in the network). Classless routing
protocols send the subnet mask with their updates, therefore allowing the use of VLSM.
All these routing protocols use metrics to determine the best path for a packet to take in a
network. The metrics used include Bandwidth, Hop Count, Delay Load, Reliability, and Cost.
Distance Vector Routing
Distance vector routes are routes to destinations that depend on the vectors of distance and
direction that the packet has to go to. The Distance is defined by metrics such as Hop Count,
where as Direction is defined as the Next Hop or Interface to go to. There are 4 Distance
Vector protocols and these are: RIP, RIPv2, IGRP and EIGRP.
Distance Vector
Protocol
Description
RIP (Routing
Information Protocol)
RIP is classful and uses Hop Count as its metric. The maximum
Hop Count is 15 hops, if the packet hasnt found its destination by
then the destination is deemed unreachable. By default RIP sends
out routing updates as a broadcast or multicast every 30 seconds.
Advantages Easy Configuration and Minimum processing
Disadvantages Broadcasting, Slow Coverage, Routing Loop, Max 15 Hop Count,
limited scalability, and Classful
Verdict I will not be using this.
Distance Vector
Protocol
Description
RIPv2 (Routing
Information Protocol
version 2)
RIPv2 is classless and uses Hop Count as its metric. The maximum
Hop Count is 15 hops, if the packet hasnt found its destination by
then the destination is deemed unreachable. RIPv2 is a
standardised protocol that works in a mixed vendor environments,
i.e. Cisco and non-Cisco devices. By default RIPv2 sends out routing
updates as a broadcast or multicast every 30 seconds.
Advantages Supports VLSM, Multicasting, Authentication
Disadvantages Slow Coverage, Routing Loop, Limited Scalability, and Max 15 Hop
Count
Verdict I will not be using this.
[Type the document title]
Page 31 of 53
Distance Vector
Protocol
Description
EIGRP (Enhanced
Interior Gateway
Routing Protocol)
EIGRP is classful and is an open routing protocol. To determine the
best path EIGRP uses metrics such as Hop Count, Bandwidth,
Delay, Load, and Reliability. The maximum amount of hops it can
take is 255 and by default routing updates are broadcast every 90
seconds
Advantages Fast Coverage, Scalability, and supports VLSM
Disadvantages High resource requirements, complex implantation and
maintenance
Verdict I will not be using this.
Distance Vector
Advantages Disadvantages
Simple Implementation & Maintenance Limited Scalability
Low bandwidth as packet sizes are small Slow Convergence time
Does not require a large amount of CPUs Routing Loops
Does not require a large amount of Memory
Link-State Routing
Link-State routing is where a Layer 3 device can get a complete overview of the network by
gathering information from all other Layer 3 devices in the network. Link-State protocols use
and algorithm called Shortest Path First (SPF). This Algorithm accumulates the cost of each
path from start to finish; this determines the best path selection. There are 2 Link-State
protocols and these are, OSPF and IS-IS.
Distance Vector
Protocol
Description
IGRP (Interior Gateway
Routing Protocol)
IGRP is classful and is a Cisco proprietary routing protocol. To
determine the best path IGRP uses metrics such as Hop Count,
Bandwidth, Delay, Load, and Reliability. The maximum amount of
hops it can take is 255 and by default routing updates are
broadcast every 90 seconds.
Advantages Max 255 Hop Count minimum processing.
Disadvantages Classful, Limited Scalability, Slow Coverage
Verdict I will not be using this.
[Type the document title]
Page 32 of 53
Link-State Protocol Description
OSPF (Open Shortest
Path First)
OSPF is classless and is an active routing protocol used today. It
uses a Link-State algorithm and operates within a single
autonomous system (AS). It gathers link-state information from
routers and constructs a topology map of the network and is an
open standard.
Advantages Fast Convergence, Builds a topological map, Event-driven updates,
and Hierarchical design
Disadvantages More CPU and Memory usage, High bandwidth usage at Network
start-up
Verdict I will be implementing this Routing Protocol within my network.
Link-State Protocol Description
IS-IS (Intermediate
System to Intermediate
System)
IS-IS is classless and reliably floods link-state information
throughout a network of routers. Each router that is running IS-IS
independently builds a database of the networks topology and
uses the same algorithm as OSPF to route the information to
neighbouring routers.
Advantages Fast Convergence, Builds a topological map, Event-driven updates,
and Hierarchical design
Disadvantages More CPU and Memory usage,
Verdict I will not be using this.
Link-State
Advantages Disadvantages
Triggered Updates Faster Convergence More CPU and Memory is required
Topological table of network Floods the network with LSAs as Network
Start-Up
No Routing Loops More administrator knowledge is required
Supports CIDR and VLSM
Hybrid
Hybrid routing is a combination of distance-vector routing and link-state routing. Hybrid
routing protocols use distance-vectors for more accurate metrics to determine the best
paths to destination networks, and reports routing information only when there is a change
in the topology of the network. Hybrid routing allows for rapid convergence but requires
less processing power and memory as compared to link-state routing. EIGRP is a hybrid
routing protocol.
[Type the document title]
Page 33 of 53
Dynamic Routing
Dynamic routing is where routes are learned and automatically added to the routing table of
a device without an Administrator. Routers are able to select paths according to real-time
logical network layout changes.
Typically, dynamic routing protocol operations can be explained as follows:
1. The router delivers and receives the routing messages on the router interfaces.
2. The routing messages and information are shared with other routers, which use
exactly the same routing protocol.
3. Routers swap the routing information to discover data about remote networks.
4. Whenever a router finds a change in topology, the routing protocol advertises this
topology change to other routers.
Dynamic routing is easy to configure on large networks, but as routers share updates, they
consume bandwidth. More CPUs and RAM are needed for the additional loads that comes
with the result of routing protocols. Dynamic Routing is less secure than static routing.
Dynamic Routing
Advantages Disadvantages
Protocols react to topology changes
automatically
More Bandwidth consumed
Less Errors with faulty configurations Minimal control over route path
Scalability High CPU usage.
Re-Routes around link failures
Static Routing
Static Routing is the exact opposite of Dynamic Routing, where instead of routes being
dynamically learned they are manually configured by a network administrator. If you have a
large network then Static Routing would become very difficult to implement and maintain,
as adding networks and routers to the network would make it very time consuming as you
would have to configure the current routers with the new network changes and also
configure the new routers with the current network routes. Static Routing is more secure
than Dynamic Routing.
Static Routing
Advantages Disadvantages
Minimal CPU usage Does not Scale well
Easy to configure Every Router has to be manually configured
More Secure Does not respond to faults without administrator
BGP
[Type the document title]
Page 34 of 53
BGP (Border Gateway Protocol) is a path vector protocol and is used for exchanging routing
information between all of the major Internet Service Providers, as well as large client sites
and their ISPs. Routing messages contain complete routes and if a router receives a message
where the route is missing then an error message is generated. It has a quick convergence
time and can have 1000s of routers involved within the network.
2.3.1 Justification for Choosing a Routing Protocol
My chosen routing protocol is Open Shortest Path First as it has fast convergence time,
scales well, and supports CIDR and VLSM. OSPF develops adjacencies with its neighbours.
The protocol sends periodic hello packets to keep the connection alive and as well as
sending changes to neighbouring routers when a links status changes. OSPF sends update
packets to neighbouring routers every 30 minutes (by default) of all recent link state
changes. Routing updates are small as the entire routing table is not sent and also
recognizes the bandwidth of a link, therefore being able to make the correct decision when
choosing a link.
All information was from:
http://www.inetdaemon.com/tutorials/internet/ip/routing/dv_vs_ls.shtml
http://www.ciscopress.com/articles/article.asp?p=24090&seqNum=3
[Type the document title]
Page 35 of 53
2.4 Testing the Network
2.4.1 Network Tools
There is a variety of network tools and testing tools that I will be using to test my network
and ensure full functionality. The most common tests to run when ensuring full functionality
of a network are:
Throughput Testing This is where devices such as servers are tested to see how
much requests they can handle per second.
Availability Testing This is where devices are pushed to within their limit to see if
there are any faults.
Application response time testing This is where the time that is taken for an
application to respond is recorded and used to make any changes to the application.
The Network Tools that I can use to test the network are QoS and Service Level
Management Tools, Protocol Sniffers, and Network Management and Monitoring Tools.
Network Tool Description
Quality of Service
Management Tool
This tool is used to measure the availability and performance of
applications and the system, such as throughput level, jitter,
delay, response time, scalability requirements, manageability,
security, and sometimes even cost.
Service Level
Management Tool
The Service-level management is the monitoring and
management of the Quality of Service. This enables you to see the
amount of stability, reliability, and performance of the Network
Infrastructure.
Protocol Sniffers This tool is a computer program or even a piece of computer
hardware that can intercept and log traffic passing over the
network or a part of the network. Wireshark is an example of a
Protocol Sniffer.
Network Management
and Monitoring Tool
This tool is used to alert Network Administrators to significant
network problems.
[Type the document title]
Page 36 of 53
Two network tools I can run directly from any device using the TCP/IP protocol are:
Ping
This tool determines whether or not an IP address is accessible by sending a packet to the
specified address and waiting for a reply. This is a very good tool as the network
administrator can ping a device on a different subnet and can determine if the Layer 3
internetworking device is working. This tool operates by sending an ICMP (Internet Control
Message Protocol) echo request packets to the specified IP address and waiting for an ICMP
response. This tool then measures the time taken for the ping to make a round trip and
records any packet loss. You can set different variations on the packet being sent, I.e. Packet
Size, Number of Packets, and TTL (Time To Live).
Trace Route
This tool traces a packet from a device to another device, recording how many Routers
(hops) the packet needs to go through and how long each hop takes. This tool is known as
tracert, and an administrator can use this tool to determine where the network is faulty and
where a devices packet is getting dropped when trying to reach another device.
The last type of testing that can be done to test the network is Stress Testing. This is the
process where a computer, network, program, or network device is tested to see what level
they can perform at when in unfavourable conditions. This test is just like a performance
test. The main point in this test is to determine how fast a device can recover from a failure.
[Type the document title]
Page 37 of 53
2.5 Securing the Network
To secure my network I must protect all the network devices and the data that they handle.
I will talk about Physical Security, Monitoring, Firewalls, Anti-Virus, DMZ, Proxy Server,
Backups, NAT, ACLs, Port Security, Authentication, Encryption, Cisco Best Practice and
Group Policy.
Physical Security
Physical Security is ensuring that only authorized personnel have access to the whole/parts
of your system. The simplest method of physical security is locking the door(s) where the
network devices are situated. You can then build on this by adding Key cards, biometrics,
and even having security guards to keep unauthorised personnel out.
If, for some reason unauthorised users get into network rooms you can protect the
machines by putting padlocks on end devices, server racks, and cabinets that hold network
devices. This stops users from taking components out and adding in components.
Monitoring
There is no foolproof way to ensure that a server is always physically protected. Breakdowns
in security always happen. Monitoring is necessary to ensure that unauthorized actions do
not occur with the server. You can use Security cameras, sensors, and security guards to
monitor your system.
Firewalls
Firewalls are software or hardware based network security systems that control incoming
and outgoing network traffic by analyzing the data packets and determining whether or not
they are allowed into/out the internal network. They prevent unauthorized Internet users
from accessing private networks.
What does a Firewall offer?
Packet Filtering: The Firewall analyzes each packet entering or leaving the network
ad accepts or rejects it based on user-defined rules.
Remote Access: Allows users to remotely login to the network by the use of secure
login procedures and authentication certificates.
Logging and Reporting: The Firewall will log and then compile a report on any
unusual activity within the network.
Application Gateway: Applies security mechanisms to specific applications, such as
FTP and Telnet servers. This is very affective, but can degrade performance.
[Type the document title]
Page 38 of 53
Anti-Virus
This is a program that searches a HDD for viruses and removes them if any is found. The
majority of these programs include an auto-update feature that enables the program to
download profiles of new viruses so that it can check for new viruses as soon as they are
discovered. Information from -
http://www.webopedia.com/DidYouKnow/Internet/2008/antivirus_antispyware.asp
DMZ
A Demilitarized Zone is a neutral zone that resides between the public network and an
organisations private network, as each side of the DMZ should be protected by a firewall, it
creates an isolated LAN inside the DMZ. Any service that is being provided to users on an
external network can be placed within the DMZ, I.e. Web servers, mail servers, and FTP
servers. The firewalls will prevent any unauthorized users from connecting to these servers
without correct authentication.
Proxy Server
A Proxy server is a server that that acts as an intermediary for requests from clients seeking
resources from other servers; I.e. a client requests a web page from a server on the
Internet. It hides the network addresses.
A proxy server has many features:
Keeps machines within the private network anonymous
Caches web pages, which speeds up access to resources
Prevents downloading the same content multiple times, which then saves bandwidth
Filter web pages
Bypass security/parental controls (dependant on how it is configured)
Log network traffic to see who is accessing what
Backups
When you have important information that can keep your company/organization going
backups are very important. A backup is a routine part of a network so that in any event
where there is a fire, natural disaster, or a robbery all the data can be backed up and the
organization can resume. You can backup up locally (file servers, USBs, CDs) or externally
(Internet, File servers located in a different geographical location).
[Type the document title]
Page 39 of 53
Types of Backup Description
Full Backup
Full backup is a method of backup where all the files and folders selected for the
backup will be backed up. Restores are fast and easy, but each backup run is time
consuming as the entire list of files is copied again and also takes up a lot more
storage space.
Incremental Backup
Incremental backup is a backup of all changes made since the last backup. Much
faster backup and less storage space used but restores are slower than a full
backup.
Differential Backup
Differential backup is a backup of all changes made since the last full backup. Much
faster backup and less storage space used but restores are slower than a full backup
but faster than an Incremental backup.
Mirror Backup
Mirror backups are as the name suggests a mirror of the source being backed up.
With mirror backups, when a file in the source is deleted, that file is eventually also
deleted in the mirror backup. Because of this, mirror backups should be used with
caution as a file that is deleted by accident or through a virus may also cause the
mirror backups to be deleted as well.
Full PC Backup
In this backup, it is not the individual files that are backed up but entire images of
the hard drives of the computer that is backed up. With the full PC backup, you can
restore the computer hard drives to its exact state when the backup was done. With
the Full PC backup, not only can the work documents, picture, videos and audio files
be restored but the operating system, hard ware drivers, system files, registry,
programs, emails etc can also be restored.
Local Backup
Local backups are any kind of backup where the storage medium is kept close at
hand or in the same building as the source. It could be a backup done on a second
internal hard drive, an attached external hard drive, CD/ DVD ROM or Network
Attached Storage (NAS).
Offsite Backup
When the backup storage media is kept at a different geographic location from the
source, this is known as an offsite backup. The backup may be done locally at first
but once the storage medium is brought to another location, it becomes an offsite
backup.
Online Backup
These are backups that are ongoing or done continuously or frequently to a storage
medium that is always connected to the source being backed up. Typically the
storage medium is located offsite and connected to the backup source by a network
or Internet connection. It does not involve human intervention to plug in drives and
storage media for backups to run.
Remote Backup
Remote backups are a form of offsite backup with a difference being that you can
access, restore or administer the backups while located at your source location or
other location. You do not need to be physically present at the backup storage
facility to access the backups.
FTP Backup
This term is often used interchangeably with Online Backup and Remote Backup. It
is where data is backed up to a service or storage facility connected over the
Internet. With the proper login credentials, that backup can then be accessed or
restored from any other computer with Internet Access.
Cloud Backup
This is a kind of backup where the backup is done via FTP (File Transfer Protocol)
over the Internet to an FTP Server. Typically the FTP Server is located in a
commercial data centre away from the source data being backed up. When the FTP
server is located at a different location, this is another form of offsite backup.
All this information can be found at http://typesofbackup.com/
[Type the document title]
Page 40 of 53
NAT
Network Address Translation allows a LAN to use one set of IP addresses for internal traffic
and a second set of addresses for external traffic. It limits the number of public IP addresses
an organization or company can use. This allows them to use private addresses such as
10.0.0.0 to 10.255.255.255
172.16.0.0 to 172.31.255.255
192.168.0 0 to 192.168.255.255
ACLs
Also known as Access Control List, it provides a set of rules that determines whether or not
a specific object(s) can access certain resources or use certain protocols or even access
networks. I.e. this command will permit IP traffic from the 10.1.1.0 network to the
172.16.1.0 network.
Access-list 101 permit ip 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255
Any IP addresses not in these networks will be rejected.
Port Security
This is a feature on Cisco switches and it operates at Layer 2 (MAC Address). All switch ports
or interfaces should be secured before the switch is deployed. Port security limits the
number of valid MAC addresses allowed on a port. When you assign secure MAC addresses
to a secure port, the port does not forward packets with source addresses outside the group
of defined addresses. You should also shutdown any ports that are not in use.
Authentication
Authentication is the process of determining whether or not someone or something is, in
fact who they say they are. The most common authentication method used is username and
password. Passwords should be of a strong quality and by using these rules you can create
one.
1. Password must have a minimum of 8 characters
2. No dictionary words
3. A combination of Numbers, Letters, and special characters
4. Change your password every 60 days
However, passwords can be cracked or acquired using phishing techniques, so businesss
can use Digital Certificates that are used and verified by a Certificate Authority (CA) as part
of a public key infrastructure.
[Type the document title]
Page 41 of 53
Encryption
Encryption is recommended for users who access the network remotely, i.e. via the
Internet. A VPN uses a tunnel that encrypts all the data sent along it to provide remote
access to a network. The encryption used can be IPSec protocol.
Cisco Best Practice
Cisco has a recommended best practice for securing Cisco IOS Devices. All the
Internetworking devices in my network are Cisco I am going to use Cisco Best Practice, this
includes Enable Secret Password, Disable un-used services, VTY access to use SSH, Restrict
access on VTY to know list of addresses, and Disable logging on console and monitor ports.
Group Policy
Group Policy is a hierarchical infrastructure that allows a network administrator in charge of
Microsoft's Active Directory to implement specific configurations for users and computers.
Group Policy can also be used to define user, security and networking policies at the
machine level. Group Policy allows administrators to define options for what users can do
on a network including what files, folders and applications they can access.
[Type the document title]
Page 42 of 53
3.1 Scaling IP Addressing Scheme
3.1.1 Problems of Basic IP Addressing Scheme
The main problem with using a basic IP addressing scheme is the wastage of IP addresses. As
you can see on page (page No planning) I used basic VLSM and I am wasting 783 IP
addresses in the Admin network and 315 IP addresses in the Teaching network. Also, I was
using 2 switches coming off a single router I had two very large broadcast domains.
To reduce the broadcast domains I can implement VLANs (Virtual Local Area Networks) and
also use a more advanced VLSM (Variable Length Subnet Mask) approach where I will
subnet the current subnets. Although VLSM is used to create multiple subnets, CIDR
(Classless Inter-Domain Routing) allows for route summarisation so that routing tables are
not being filled with lots of individual IP addresses. I.e. the IP address 192.168.1.1 through
192.168.1.100 would be summarised and shown as 192.168.1.0 in the routing table, this is
also known as Route Aggregation. I will be using a DHCP server to allocate IP addresses to
end devices, using a DHCP Scope.
3.1.2 VLSM Design
As I am using VLSM I also have to choose a Routing protocol that is classless such as BGP,
EIGRP, IS-IS, OSPF, or RIPv2. I have chosen OSPF.
The main benefits of VLSM are:
Ability to perform route summarization
Reduced wastage of IP Addresses
Different subnet masks result in separate broadcasts to each subnet, therefore
saving bandwidth
Information from http://www.orbit-computer-solutions.com/VLSM.php
As I am using NAT I can use Private IP addresses within these ranges:
10.0.0.0 Through 10.255.255.255
172.16.0.0 through 172.31.255.255
192.168.0.0 through 192.168.255.255
I will be using the 172.16.0.0 through 172.31.255.255 Private IP range. This has a subnet mask
of /16, 255.255.0.0.
Teaching/Student = 707 Hosts 100%
Growth
Student 587 1174
Admin 239 478
Teachers 120 240
Technicians 15 30
DMZ 23 N/A
[Type the document title]
Page 43 of 53
I have made this table for an easier on the eye look at the above information.
Network Hosts Network
Address
Host Range Broadcast Subnet Mask
Students 1174 172.16.0.0 172.16.0.1 172.16.7.254 172.16.7.255 255.255.248.0 /21
Admin 478 172.16.8.0 172.16.8.1 172.16.9.254 172.16.9.255 255.255.252.0 /22
Teachers 240 172.16.10.0 172.16.10.1 172.16.10.254 172.16.10.255 255.255.254.0 /23
Technicians 30 172.16.11.0 172.16.11.1 172.16.11.30 172.16.11.31 255.255.255.224 /27
DMZ 23 172.16.11.32 172.16.11.32 172.16.11.62 172.16.11.63 255.255.255.224 /27
As I am using 5 VLANs I will need to use Inter-VLAN Routing to allow them to communicate
between themselves and this will be done using a layer 3 switch.
[Type the document title]
Page 44 of 53
3.2 Advanced Routing Concepts
3.2.1 OSPF
Open Shortest Path First is a Link-State classless routing protocol used within a large
autonomous system (AS) network. This protocol was designed by the Internet Engineering
Task Force (IETF). The host that is running OSPF sends multicasts updates of the routing
table to connected hosts every time there is a change in the network, however only the part
of the routing table that has changed gets sent, thus saving bandwidth.
The OSPF host sends LSAs (Link-State Advertisements) to other hosts on the network and
when all the LSAs have been received, the host builds a link-state database using Dijkstras
Shortest Path First (SPF) algorithm to create a SPF tree, then the SPF Tree is used to
populate the IP routing table with the best paths to each network. The metric used for OSPF
is cost.
As I only have two Layer 3 devices the network wont be getting flooded with LSAs. When
OSPF is used in multi-access networks an election process takes place to find a Designated
Router (DR) and a Backup Designated Router (BDR). The DR collects and distributes all the
LSAs that are sent and received in the network. The BDR is elected in the event that the DR
fails. If there are any other routers in the network they are called the DROthers just to
indicate that they arent DR or BDR. The DR is elected by which router has the highest OSPF
interface priority. The BDR is elected by which router has the 2
nd
highest OSPF interface
priority. If in the case that each router has the same OSPF interface priorities, the router
with the highest Router ID is elected DR.
3.2.2 EIGRP
Enhanced Interior Gateway Routing Protocol is a Cisco proprietary routing protocol. It uses
DUAL (Diffusing Update Algorithm) to select the best and shortest path for packets. EIGRP
can perform load balancing of unequal costs. EIGRP keeps a copy of its neighbours routing
tables, and if the router cannot find the required route in this table it will query its
neighbour for the route and then that router will query its own neighbours for that route
and so on until the route is found and sent back to the original router that sent the query.
Just like OSPF when there is a change in the routing table it wont send the whole routing
table just the change that has occurred.
To keep all routers aware of the state of neighbours, each router sends out a periodic hello
packet. A router that hasnt sent a hello packet within a certain period of time is considered
inoperative.
I got this information from www.searchnetworking.techtarget.com
[Type the document title]
Page 45 of 53
3.3 Switch Design
3.3.1 Applying Switched Network Design
As you can see from my 2
nd
Proposed Design I have implemented a switched network design
in a hierarchical fashion. There are 2 Layer 3 devices (Router and Layer 3 Switch) that will
perform the routing functions for the network and the Layer 3 Device will perform the Inter-
VLAN Routing. There are redundant links in the switched design to ensure that the entire
network does not grind to a halt if one of the switches fails.
STP (Spanning Tree Protocol) will be configured on all switches to ensure a loop-free
topology and provide redundant links to provide an automatic backup path if an active link
fails. I have provided a network design of what links are Trunks and what links are not.
This design meets the customers goal for availability and performance.
These switches have multiple features that include:
Feature Description
Quality of Service (QoS) This prioritises the traffic on the network.
Port Security This allows the switch to decide what devices are allowed to
connect to which port.
Link Aggregation This allows the switches to use multiple links simultaneously, thus
aggregating the bandwidth of the ISL trunks between the switches,
which therefore provides a faster and higher quality link.
[Type the document title]
Page 46 of 53
3.4 Choose Vendor Switch Equipment
I have chosen Cisco Catalyst 3750G-12S as my Layer 3 switch in the core. It is stackable so I
can join the same switch to it and they 2 switches can act as 1 whole switch. Features of this
Switch:
Advanced Layer 3 Switching
Multicasting
Supports multiple routing protocols including OSPF
Copper and Fiber connectivity
Supports VLANs
DHCP
ACLs
QoS
Link Aggregation
STP & RSTP
TFTP Support
I have chosen Cisco Catalyst 3560X-24T-L Switches as the distribution layer switches. It has
12 SPF ports for fiber connections. Features of this switch:
Spanning Tree Protocol
QoS
Rapid Spanning Tree Protocol & Spanning Tree Protocol
TFTP Support
VLANs
Link Aggregation
I have chosen Cisco Catalyst 2960S-48TD-L -Switch as the Access layer switches. It has 46
Gigabit ports and 2 SPF ports for fiber connections. Features of this switch:
Spanning Tree Protocol
QoS
Rapid Spanning Tree Protocol & Spanning Tree Protocol
TFTP Support
VLANs
Link Aggregation
[Type the document title]
Page 47 of 53
3.5 VLAN Implementation
3.5.1 Virtual Local Area Networks
The customer requested that the Administrators, Teachers, and Student networks to be
separated for security purpose but also still be able to share resources, so I have made 4
VLANs.
Administrator VLAN
Teacher VLAN
Student VLAN
Technician VLAN
I have implemented VLANs throughout the network for ease of management and
troubleshooting. Here is a Diagram of how the VLANs will work.
[Type the document title]
Page 48 of 53
4.0 Evaluation
4.1 NAT/PAT
NAT (Network Address Translation) is a type of network translation that helps with scaling
IP addresses. NAT allows LANs to use one set of IP addresses for internal traffic and a
second set of address(s) to use for external traffic. Basically, a packet coming into public side
of the layer 3 device will have a Public IP Address assigned to it and then the router
performing NAT will translate that public IP address into the private IP address of the
packets destination (end device).
NAT saves IP Addresses by allowing the internal networks to use Private IP addresses, then
translating them to either 1 single public IP Address or multiple Public IP Addresses.
PAT (Port Address Translation) also known as NAT overloading maps multiple IP addresses
to a single public IP address or multiple public IP addresses, but also uses a port number at
the end of the private IP Address. The majority of home routers perform PAT as the ISP
assigns you a single public IP address and you and other family members can all surf the
Internet simultaneously.
[Type the document title]
Page 49 of 53
The port numbers assigned to the source IP address doesnt change at all but the IP address
gets translated to a public IP Address. Once the packet is out on the Internet and comes back
the public IP address is translated back to the private IP address and this address is
determined by what port number is assigned to the source address.
So overall each computer on a LAN is translated to the same Public IP Address but they all
have a different port number assigned.
4.2 WAN Design
As you can see the two outlaying sites, Dun Learning & No More, will get there Internet
access by going through Stevenson College using a Broadband VPN. I have decided to do it
this way so that there is increased security for network traffic exiting and entering the sites.
I have decided to use VPN technology as there is a secure tunnelling protocol being used
(IPSec) and the information being sent is encrypted. VPNs use virtual connections called
VPN tunnels, which are routed through the Internet. Each site will have a VPN gateway, such
as a Router, Firewall, etc...
There will be a backup Internet connection to the No More and Dun Learning networks
provided by an ISP in the event that the broadband VPN goes down.
The main college site, Stevenson College will get its Internet provided through SuperJanet5.
As well as providing the Internet, SuperJanet 5 blocks and filters traffic not suited for
educational buildings.
In the case that the link between SuperJanet5 and Stevenson College goes down, I have
provided a backup Internet link supplied from an ISP to supply the Internet to the Main site
and the two outlaying sites.
[Type the document title]
Page 50 of 53
4.3 Evaluation
4.3.1 Scalability of Design
To ensure scalability in my design I have designed my network to conform to the 3 Tier
Hierarchical Model. The Core Layer provides the fast backbone, reliability, and availability.
The Distribution Layer consists of fast and reliable switches that provide redundant links
between the Access Layer switches and the Layer 3 switch in the Core Layer. The Access
Layer has switches that provide fast connections and provide multiple links to the
Distribution Layer. The 3 Tier Hierarchical Design is highly recommended to use within a
network as you can easily add networking devices to expand the network and it also provides
redundancy and Quality of Service.
4.3.2 Effect on Bandwidth
The implementation of Layer 2 switches within the network provides small bandwidth
domains, therefore only a limited number of devices can compete for bandwidth at any one
time.
4.3.3 Effect on Broadcast Domains
With the use of VLANs on my network the broadcast domains are only the size of the
VLAN, as VLANs dont forward broadcast packets to other VLANs, thus decreasing the size
of my broadcast domains.
4.3.4 Effect on Collision Domains
As I have implemented switches throughout my network collision domains are kept to the
single port from which device they are connected to, thus eliminating the previous problem of
having 254 nodes within a collision domain.
4.3.5 Effective use of Address Space
One of the most ever increasing problems with the Internet is the usage of IPv4 Addresses.
By using NAT/PAT and VLSM I can use 1 Public IP address and provide for hundreds of
thousands of users within a private network. Variable Length Subnet Masking (VLSM)
allows you to:
1. Manage IP Addresses
2. Decrease the amount of wasted IP addresses
3. Use Route aggregation and Summarization
4. Use multiple subnet masks, which also provides additional security
[Type the document title]
Page 51 of 53
4.3.6 Effect of Security Measures
I have placed a Router Integrated with a Firewall at each site that filters out unwanted traffic
coming into the network. I have also implemented a Hardware Firewall behind the Router at
Stevenson College for additional security to the Internal Network. The Firewalls will contain
appropriate ACLs to control traffic coming in and going out. I am using a DMZ to put my
public servers in to decrease the chance of a virus getting into my Internal Network.
As for LAN isolation which was requested by the customer I have implemented VLANs to
provide distinction between Administration, Teaching, and Students.
The proxy server in the DMZ will also cache websites so that users dont always have to go
out onto the Internet to get the web pages that can cause a threat to the network.
For physical security all Networking Devices (Routers, Switches, and Servers) will be locked
within a cabinet that is locked within secure room(s). If however someone was to gain
physical access to the machines they would need to have correct passwords that meet the
complexity requirements to login to the machines.
4.3.7 Effect of Redundancy Measures
By using the 3 Tier Hierarchical Design each Access Layer Switch has at least 1 Connection
to 2 Distribution Switches, Each Distribution switch has a at least 1 connection to 2 Layer 3
Switches within the Core Layer. The 2 Core Layer 3 Switches will have a Link between them
in the event that the link to the Firewall goes down.
In the Event that the SuperJanet 5 Links goes down I have set up a backup Internet
connection from an ISP to the main college facility. I have also provided a backup Internet
connection for the 2 outlaying sites in the event that the broadband VPNs go down.
4.3.8 WAN Connectivity
The broadband VPNs I selected provides great security for connecting to the Main College
facility. VPN offers multiple advantages in the terms of security. The use of routing protocols
will be used to encrypt all travelling data from the network and to the network.
4.3.9 Ease of Administration and Management
With the use of servers, network administration and management can be easily done.
Implementation of Active Directory, Group Policy, Logs, User Monitoring, and other tools
should provide the customer with enough satisfaction to run and manage the network.
The use of Active Directory allows you to see who has logged in when and where, as well as
anyone who is not authorised to login to the system at a specific time or place, or allowed to
login at all!
Performance in the network is increased by eliminating bottlenecks from high usage areas
(servers, DMZ, etc...).
The use of Protocol Analyzer can stop also stop unwanted traffic from getting to its
destination.
[Type the document title]
Page 52 of 53
4.3.10 Appropriateness of Equipment
When setting up a network, the choice of correct equipment is one of, if not the most,
important aspect, as if the equipment doesnt perform then the whole network goes down or
ends up being completely useless. I feel that I have chosen the correct equipment for my
network as they provide high-speeds across the network, redundancy, availability and
scalability. The servers have enough of each component to be able to provide for the whole
network as well as users from the 2 outlaying sites, No More & Dun learning.
4.3.11 Design Project conducted within allocated Timescale
I feel that I have completed this project within the allocated timescale that I was given, as
well as sticking to my Planning Stage.
One approach I thought of taking during the Planning and Development Stage was to
introduce Wireless Access Points throughout the network but this could be a potential threat
to the network. I was planning on NOT using a DMZ zone but once I looked at the
advantages and disadvantages I really couldnt see me NOT using it.
4.4 Recommendation
As security is one the most important features of a network I would recommend
implementing a RADIUS server to authenticate users logging.
Another recommendation would be to implement Wireless technology so that users can login
when they are within the building but not at their PCs, although the highest security measures
would have to be put into place:
Disable SSID so that unwanted users cannot see the network
Strong passwords, Minimum 8 Characters, 2 Special Characters, 2 Numbers, Etc...
Reduce the size of the DHCP scope to the amount of all users within the network
MAC Filtering
Either A Use specialized paint to keep the RF signals within the building or B Turn
the power down on the Wireless Access Points
Use the Highest-Strongest Encryption Type (Currently WPA2)
[Type the document title]
Page 53 of 53
4.5 Conclusion
I feel as if I have developed my project very well by using all my current knowledge and
skills that I have acquired throughout college. I know that I can and will learn more about
planning/implementing networks as my education goes on.
I have stuck to my Planning Stage which has shown itself in the Development Stages, thus
creating a Reliable, Available, Secure, Redundant network.
I thought the use of the 3 Tier Hierarchical Design was very important to achieving my goal
of making this network all that it can be.
By implementing the VLANs and the switched network I feel as if I have created a very fast
and reliable network as well as providing the distinction between Administrators, Teachers,
and Students.
The client requested that a single routing protocol be used throughout the network, and I have
feel that by choosing OSPF I have meet the clients needs.
The use of Fiber throughout my network provides fast access to all parts of the network.
By using the 3 Tier Hierarchical Design I feel as if I have met the clients need for a
manageable, scalable maintainable network.
Overall I believe I have met every one of the clients needs.
I think I have done a good job in designing this network, but I also know that I have a lot still
to learn.
You might also like
- HNC Graded Unit Paul Osborne Culzean Country Park Upgrading Construction SequenceDocument1 pageHNC Graded Unit Paul Osborne Culzean Country Park Upgrading Construction Sequenceosbo1611100% (2)
- Concrete Test Slump and StrengthDocument2 pagesConcrete Test Slump and Strengthosbo1611No ratings yet
- Duffer Inc a Construction Business Start Up AdventureFrom EverandDuffer Inc a Construction Business Start Up AdventureRating: 5 out of 5 stars5/5 (1)
- HNC Graded Unit Paul Osborne Culzean Country Park UpgradingDocument4 pagesHNC Graded Unit Paul Osborne Culzean Country Park Upgradingosbo1611No ratings yet
- Horticulture Lesson PlanDocument2 pagesHorticulture Lesson Planapi-412438755No ratings yet
- Graded Unit 1Document38 pagesGraded Unit 1Yen Fa Chen100% (1)
- Most Projects Are Awarded On Competitive Bidding BasisDocument3 pagesMost Projects Are Awarded On Competitive Bidding BasisArefiq ShafikNo ratings yet
- Project Management Week 8 Risk ManagementDocument34 pagesProject Management Week 8 Risk ManagementcahidNo ratings yet
- Project Management: Cpm/Pert by Dr. Neeraj AnandDocument23 pagesProject Management: Cpm/Pert by Dr. Neeraj AnandAsasAsasNo ratings yet
- Project Manager Green BuildingDocument4 pagesProject Manager Green BuildingSaak มอนเตรNo ratings yet
- Individual Assignment1 231019Document3 pagesIndividual Assignment1 231019nevermoreNo ratings yet
- Cube Method EstimatingDocument3 pagesCube Method EstimatingAzam DeenNo ratings yet
- Building Construction ReportDocument10 pagesBuilding Construction ReportRahul NawaniNo ratings yet
- Sign-In Sheet For Members: Name Business Phone Email SIGN (Subs, Please Print Name)Document3 pagesSign-In Sheet For Members: Name Business Phone Email SIGN (Subs, Please Print Name)Silvestre Acuna AcedilloNo ratings yet
- HNC Graded Unit Culzean Country Park UpgradeDocument3 pagesHNC Graded Unit Culzean Country Park Upgradeosbo161150% (2)
- Construction of 2w & 4w Cbu Warehouse Building - Project CharterDocument7 pagesConstruction of 2w & 4w Cbu Warehouse Building - Project CharterNaseem Abbas100% (2)
- Case Study 3 Analysis (K Shanika Dilini)Document4 pagesCase Study 3 Analysis (K Shanika Dilini)Shanika Dilini Pathigoda100% (1)
- Feasibility ProposalDocument3 pagesFeasibility Proposalapi-273313942No ratings yet
- HN Civil Engineering UnitsDocument223 pagesHN Civil Engineering UnitsSamitha HarshaniNo ratings yet
- ConstructionDocument7 pagesConstructionYilkal AddisuNo ratings yet
- Assiegnment On Khidmah Credit CardDocument14 pagesAssiegnment On Khidmah Credit Cardgaffar652No ratings yet
- PM Project Draft 3Document18 pagesPM Project Draft 3sexysunny009No ratings yet
- National Highways Authority of India: Kanyakumari Etturvattam Tollway LimitedDocument52 pagesNational Highways Authority of India: Kanyakumari Etturvattam Tollway LimitedKarthi KeyanNo ratings yet
- ECM 566 Construction Project Management Course OverviewDocument9 pagesECM 566 Construction Project Management Course OverviewiskandarNo ratings yet
- Dayang Sabriah Safri MFKA2009Document114 pagesDayang Sabriah Safri MFKA2009Muhammad AmirNo ratings yet
- Project Charter For Cornerstone HQ Office Building March 2016Document33 pagesProject Charter For Cornerstone HQ Office Building March 2016Michael Ehimen100% (1)
- Group Project AsignmentDocument22 pagesGroup Project AsignmentAzizi MustafaNo ratings yet
- PRM - Analyzing The Singer CaseDocument10 pagesPRM - Analyzing The Singer CasegiourtiNo ratings yet
- A Cost Control System Development - A Collaborative Approach For Small and Medium-Sized ContractorsDocument8 pagesA Cost Control System Development - A Collaborative Approach For Small and Medium-Sized Contractorsntl9630No ratings yet
- Practical System ReliabilityDocument17 pagesPractical System ReliabilityNicoline ReyneckeNo ratings yet
- Attachment Report GuidelinesDocument15 pagesAttachment Report GuidelinesSam KOkeloNo ratings yet
- PM ProjectDocument21 pagesPM ProjectHamayun RasheedNo ratings yet
- BIM Questions & AnswersDocument5 pagesBIM Questions & AnswersMAB AliNo ratings yet
- DQS360 Tutorial 5 Constraints & Basic Features of Project SoftwareDocument3 pagesDQS360 Tutorial 5 Constraints & Basic Features of Project Softwarelily0% (1)
- Improving Awarness of Green Building Concept in Sri Lanka.Document23 pagesImproving Awarness of Green Building Concept in Sri Lanka.Isurika Ranasinghe100% (1)
- Background Information: Presentation: Very Good 90% Proposal Content: Great 100% Technical Data: Average 100% Total: 100%Document12 pagesBackground Information: Presentation: Very Good 90% Proposal Content: Great 100% Technical Data: Average 100% Total: 100%LoisNo ratings yet
- Fuel Cells: Aeronautical Engineering Propulsion IDocument7 pagesFuel Cells: Aeronautical Engineering Propulsion IMaria Clara MoralesNo ratings yet
- 16 Cost EstimatingDocument5 pages16 Cost EstimatinganasameranaNo ratings yet
- Project Management Plan TemplateDocument7 pagesProject Management Plan TemplateDilli BabuNo ratings yet
- WBS Assignement-Example2 PDFDocument1 pageWBS Assignement-Example2 PDFMohammed ShebinNo ratings yet
- Technology Innovation in Construction Industry (Engineering Management)Document2 pagesTechnology Innovation in Construction Industry (Engineering Management)AngelaDeviNo ratings yet
- The Accuracy of Pre-Tender Building Cost Estimates in Australia.Document14 pagesThe Accuracy of Pre-Tender Building Cost Estimates in Australia.Barbara Kruzic0% (1)
- BSR 257 Assignment 1Document16 pagesBSR 257 Assignment 1AMIRAH BATRISYIA IMRANNo ratings yet
- Reflective Report 134Document2 pagesReflective Report 134Radu IonutNo ratings yet
- MERIT Report LoughboroughDocument19 pagesMERIT Report LoughboroughSamuel DoyleNo ratings yet
- Feasibility Report On Internet CafeDocument17 pagesFeasibility Report On Internet Cafepiu_chatterjee100% (1)
- Developing a Common WBS for School ProjectsDocument131 pagesDeveloping a Common WBS for School ProjectsWaqas979No ratings yet
- Project Delivery Methods & Contract Types GuideDocument37 pagesProject Delivery Methods & Contract Types GuideArifNo ratings yet
- Demand ManagementDocument22 pagesDemand Managementpatil_962113756No ratings yet
- Title: Construction Technology Ii Course Work Report: Siti Nadiah Binti Mokhtar Noor Safika Faezan Binti AzahariDocument107 pagesTitle: Construction Technology Ii Course Work Report: Siti Nadiah Binti Mokhtar Noor Safika Faezan Binti AzahariSeid HodzicNo ratings yet
- Case Studies in Project Management Semester September 2020Document8 pagesCase Studies in Project Management Semester September 2020faroukalias100% (1)
- Foreman Delay Survey Finds Material Wait Top CauseDocument18 pagesForeman Delay Survey Finds Material Wait Top Causevalkiria112No ratings yet
- Pre ConstructionDocument6 pagesPre ConstructionGRACE THIRSTNo ratings yet
- Risk and Response MangementDocument19 pagesRisk and Response MangementMuhammad HussainNo ratings yet
- Group 4 - Comm Rehab Comm Project Charter (EDIT Maryon)Document3 pagesGroup 4 - Comm Rehab Comm Project Charter (EDIT Maryon)Kool Bhardwaj33% (3)
- Housing Project Process GuideDocument52 pagesHousing Project Process Guidekarri1963100% (1)
- Adminstrate Network and Hardware PeripherialsDocument18 pagesAdminstrate Network and Hardware PeripherialsDark KnightNo ratings yet
- Data Communication Lecture 2Document12 pagesData Communication Lecture 2Shakibur RahmanNo ratings yet
- Cubase LE AI Elements 750 Activated 72 PDFDocument3 pagesCubase LE AI Elements 750 Activated 72 PDFLoriNo ratings yet
- CSC 5301 - Paper - DB & DW SecurityDocument17 pagesCSC 5301 - Paper - DB & DW SecurityMohamedNo ratings yet
- HC series controller instruction manualDocument12 pagesHC series controller instruction manualRCG100% (1)
- DualCell HSDPADocument29 pagesDualCell HSDPASABER1980No ratings yet
- EEE 3209 - Digital Electronics IIDocument63 pagesEEE 3209 - Digital Electronics IIHenry KabasaNo ratings yet
- 2015may FE PM QuestionDocument39 pages2015may FE PM Questionjive_gumelaNo ratings yet
- Application - CEMTES Cambodia) Pte LTDDocument2 pagesApplication - CEMTES Cambodia) Pte LTDsuylyvarNo ratings yet
- Analog Modeling Using Event-Driven HDLsDocument4 pagesAnalog Modeling Using Event-Driven HDLsGuru VelmathiNo ratings yet
- Basic Mpls VPN LabDocument2 pagesBasic Mpls VPN LabcarolatuNo ratings yet
- Semester-Wise Road Map: First Year (1st Semester)Document4 pagesSemester-Wise Road Map: First Year (1st Semester)Hashim AliNo ratings yet
- Firewall Training, Checkpoint FirewallDocument7 pagesFirewall Training, Checkpoint Firewallgaurav775588No ratings yet
- Hard Disk PerformanceDocument5 pagesHard Disk Performanceweilong100% (1)
- Installation Procedure For Linux: $sudo LsusbDocument2 pagesInstallation Procedure For Linux: $sudo LsusbRai Kashif JahangirNo ratings yet
- DH61AG TechProdSpec04Document106 pagesDH61AG TechProdSpec04George IoakimedesNo ratings yet
- 11-Speech Encryption and DecryptionDocument13 pages11-Speech Encryption and Decryptionapi-19799369No ratings yet
- Lecture 10 - Data CompressionDocument18 pagesLecture 10 - Data CompressionTanveer Ahmed HakroNo ratings yet
- Andover Continuum IO Module ExpansionDocument4 pagesAndover Continuum IO Module Expansionvugiang_itd1248No ratings yet
- Installation and Administration Guide DPADocument204 pagesInstallation and Administration Guide DPARafaelHerreraNo ratings yet
- FreebsdDocument47 pagesFreebsdMohammad Bilal MirzaNo ratings yet
- IBS Components with 4.3-10 Interface Combiners Smart POIDocument6 pagesIBS Components with 4.3-10 Interface Combiners Smart POIdenny gloriousNo ratings yet
- Distributed Objects and RMIDocument15 pagesDistributed Objects and RMIHưng Hoàng TrọngNo ratings yet
- Experienced full stack developer with 4+ years of experience in web application developmentDocument4 pagesExperienced full stack developer with 4+ years of experience in web application developmenttest 1 misoNo ratings yet
- MSP430 FR49 XX FamilyDocument643 pagesMSP430 FR49 XX FamilygimenNo ratings yet
- PrintersDocument5 pagesPrintersnithinnikilNo ratings yet
- Alonex Special Amp Industrial Electronic Equipment PDFDocument342 pagesAlonex Special Amp Industrial Electronic Equipment PDFthanh vanNo ratings yet
- DLP ProjectorsDocument62 pagesDLP ProjectorsVenkatesh Subramanya100% (1)
- Spi-3. Narrowband Passive GSM Interceptor of New GenerationDocument11 pagesSpi-3. Narrowband Passive GSM Interceptor of New GenerationStriker Plus100% (1)
- Atasheet: Airmax® Ac Basestation With Airprism® TechnologyDocument7 pagesAtasheet: Airmax® Ac Basestation With Airprism® TechnologyEshuac RedNo ratings yet
- Xda-Developers - SECRET CODES - Omnia 2 GT-i8000 PDFDocument3 pagesXda-Developers - SECRET CODES - Omnia 2 GT-i8000 PDFM Arshad Iqbal HarralNo ratings yet
- DVR Eyemax XVST Magic 08p 16p 16mDocument2 pagesDVR Eyemax XVST Magic 08p 16p 16mSaeful AnwarNo ratings yet