Professional Documents
Culture Documents
VPN Site To Site Packet Tracer 5
Uploaded by
R.s. Félix0 ratings0% found this document useful (0 votes)
110 views2 pagesLab shows you how to type the right commands on both router sides using packet tracer 5. We will have the following topology Notice you will set static route between the two routers while on real live both will connected through ISP's.
Original Description:
Original Title
VPN Site to Site Packet Tracer 5
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentLab shows you how to type the right commands on both router sides using packet tracer 5. We will have the following topology Notice you will set static route between the two routers while on real live both will connected through ISP's.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
110 views2 pagesVPN Site To Site Packet Tracer 5
Uploaded by
R.s. FélixLab shows you how to type the right commands on both router sides using packet tracer 5. We will have the following topology Notice you will set static route between the two routers while on real live both will connected through ISP's.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 2
10/9/2014 VPN site to site packet tracer 5.
3 lab - The Cisco Learning Network
https://learningnetwork.cisco.com/docs/DOC-10756 1/3
Login Register Premium Library Contact Us/Help About Us Mobile View
Connect with us on: Search the Learning Network
Cisco Learning Home IT Careers Connections Certifications Learning Center Our Store
Cisco Learning Home > Certifications > Security (CCNA Security) > IINS Exam > Documents
Jusqu' IINS Exam documents dans
Cr le: 19 dc. 2010 12:22 par Yasser Ramzy Auda - CCSI , CCNP R&S ,
CCNP Security - Dernire modification: 19 dc. 2010 12:42 par Yasser
Ramzy Auda - CCSI , CCNP R&S , CCNP Security
VPN site to site packet tracer 5.3 lab
VERSION 1
79 Jaime
first of all you need to study Well the concepts of IPSec , VPN types , CRYPTOLOGY before you
read this document
Its just show you how to type the right commands on both router sides using packet tracer 5.3
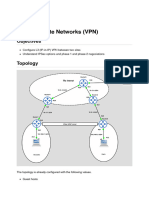
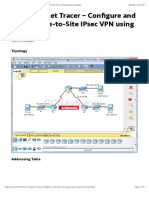
We will have the following topology
Notice you will set static route between the two routers while on real live both will connected
through ISPs
for router 1 we will type the following commands :
Router(config)#crypto isakmp enable <=== enable IPsec
Router(config)#crypto isakmp policy 1 <=== set new policy with number 1
Router(config-isakmp)#authentication pre-share <=== using shred key authentication
method (if use certification use rsa-sig instead of pre-share)
Router(config-isakmp)#encryption aes <=== use symmetric encryption AES
Router(config-isakmp)#hash sha <=== use hash alghorthim sha for data integrity
Router(config-isakmp)#group 2 <=== use diffe helman group 2
Router(config-isakmp)#exit
Router(config)#crypto isakmp key 0 address 11.0.0.1 0.0.0.0 <=== 0 is the key will used
with next site , next site ip address 11.0.0.1 and note on packet tracer you use 0.0.0.0
instead of subnetmask
Router(config)#crypto ipsec transform-set yasser esp-aes esp-sha-hmac <=== set
transform set called yasser and esp is the protocol will be used , u can use AH on internal
VPN
Router(config)#crypto ipsec security-association lifetime seconds 86400 <=== key
expire after 86400 seconds
Router(config)#ip access-list extended ramzy <=== ACL
called ramzy to tell which traffic will use the vpn tunnel
Router(config-ext-nacl)#permit ip 12.0.0.0 0.255.255.255 10.0.0.0 0.255.255.255
Router(config-ext-nacl)#exit
Router(config)#crypto map auda 100 ipsec-isakmp <=== create crypto map
called auda with seq number 100
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Router(config-crypto-map)#match address ramzy <=== link above
ACL to this crypto map
Router(config-crypto-map)#set peer 11.0.0.1 <=== link next site ip
address to this crypto map
Router(config-crypto-map)#set pfs group2 <=== link DH group 2 to
this crypto map
Router(config-crypto-map)#set transform-set yasser <=== link
above transform set to this crypto map
Router(config-crypto-map)#ex
Router(config)#int fa 0/1 <=== apply crypto map auda to interface
face the next site link.
Router(config-if)#crypto map auda
*Jan 3 07:16:26.785: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Router(config-if)#do wr
Building configuration...
[OK]
Router(config-if)#^Z
Router#
for router 0 we will type the following commands :
Router(config)#crypto isakmp enable
Router(config)#crypto isakmp policy 1
Router(config-isakmp)#authentication pre-share
Router(config-isakmp)#encryption aes
Router(config-isakmp)#group 2
Router(config-isakmp)#hash sha
Router(config-isakmp)#exit
Router(config)#crypto isakmp key 0 address 11.0.0.2 0.0.0.0
Router(config)#crypto ipsec transform-set yasser esp-aes esp-sha-hmac
Router(config)#crypto ipsec security-association lifetime seconds 86400
Router(config)#ip access-list extended ramzy
Router(config-ext-nacl)#permit ip 10.0.0.0 0.255.255.255 12.0.0.0 0.255.255.255
Router(config-ext-nacl)#exit
Router(config)#crypto map auda 100 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Router(config-crypto-map)#match address ramzy
Router(config-crypto-map)#set peer 11.0.0.2
Router(config-crypto-map)#set pfs group2
Router(config-crypto-map)#set transform-set yasser
Router(config-crypto-map)#exit
Router(config)#interface fastEthernet 0/1
Certifications
Show All
ENTRY
ASSOCIATE
Data Center (CCNA Data Center)
Design (CCDA)
Routing & Switching (CCNA)
Security (CCNA Security)
Syllabus
Data Sheets and Literature
IINS Exam
Exam Logic Tool
SP Operations (CCNA SP Ops)
Service Provider (CCNA SP)
Video (CCNA Video)
Voice (CCNA Voice)
Wireless (CCNA Wireless)
PROFESSIONAL
EXPERT
ARCHITECT
SPECIALIST
POLICIES| REFERENCE|
TOOLS
Actions
Register / Login to participate in
the community & access resources
like:
Register for free now.
IT Training Videos and
Seminars
Cisco Certification Study Groups
Cisco Certification Exam Topics
Learn more about The Cisco
Learning Network and our
Premium Subscription options.
Afficher :
Tous
Dfini comme signet par
(13)
D'autres liens comparables
router to router vpn... cli step
by step
dmvpn w/ipsec
gre w/crypto...
Gateway-to-gateway VPN with
preshared secrets
DF Bit Override With IPsec
VPNs
Plus parYasser Ramzy
Auda - CCSI , CCNP R&S ,
CCNP Security
Afficher le profil de Yasser
Ramzy Auda - CCSI , CCNP R&S ,
CCNP Security
AAA Lab using Packet tracer
5.3
Languages:
10/9/2014 VPN site to site packet tracer 5.3 lab - The Cisco Learning Network
https://learningnetwork.cisco.com/docs/DOC-10756 2/3
Router(config-if)#crypto map auda
*Jan 3 07:16:26.785: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Router(config-if)#exit
Router(config)#do wr
Building configuration...
[OK]
Router(config)#
now lets go to router 0 and do some show commands :
Router#show crypto Isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: AES - Advanced Encryption Standard (128 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #2 (1024 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
Router#
Router#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
11.0.0.1 11.0.0.2 QM_IDLE 1062 0 ACTIVE
IPv6 Crypto ISAKMP SA
Router#
Router#show crypto map
Crypto Map auda 100 ipsec-isakmp
Peer = 11.0.0.1
Extended IP access list ramzy
access-list ramzy permit ip 12.0.0.0 0.255.255.255 10.0.0.0 0.255.255.255
Current peer: 11.0.0.1
Security association lifetime: 4608000 kilobytes/86400 seconds
PFS (Y/N): Y
Transform sets={
yasser,
}
Interfaces using crypto map auda:
FastEthernet0/1
Router#
Router#sh crypto ipsec transform-set
Transform set yasser: { { esp-aes esp-sha-hmac }
will negotiate = { Tunnel, },
Router#
now lets make pc0 ping pc1
Router#show crypto ipsec sa
interface: FastEthernet0/1
Crypto map tag: auda, local addr 11.0.0.2
protected vrf: (none)
local ident (addr/mask/prot/port): (12.0.0.0/255.0.0.0/0/0)
remote ident (addr/mask/prot/port): (10.0.0.0/255.0.0.0/0/0)
current_peer 11.0.0.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 6, #pkts encrypt: 6, #pkts digest: 0
#pkts decaps: 5, #pkts decrypt: 5, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 11.0.0.2, remote crypto endpt.:11.0.0.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/1
current outbound spi: 0x12D96D50(316239184)
inbound esp sas:
spi: 0x590D14F4(1494029556)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: FPGA:1, crypto map: auda
sa timing: remaining key lifetime (k/sec): (4525504/86170)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x12D96D50(316239184)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: FPGA:1, crypto map: auda
sa timing: remaining key lifetime (k/sec): (4525504/86170)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
packet tracer file :
yasser ramzy auda
CCNA,CCNA security,CCNA voice ,CCDA,CCNP,CCIP,CCNP security (CCSP).
You might also like
- TP4'-Ipsec VPN Site To SiteDocument2 pagesTP4'-Ipsec VPN Site To SiteGeraud TchadaNo ratings yet
- TP4'-Ipsec VPN Site To SiteDocument2 pagesTP4'-Ipsec VPN Site To SiteGERAUDNo ratings yet
- Creacion VPN IPSECDocument2 pagesCreacion VPN IPSECCarlos Amaranti GonzálezNo ratings yet
- Router Vpnclient Pi StickDocument10 pagesRouter Vpnclient Pi Stickjames SpywangNo ratings yet
- Configure A Site To Site VPN Tunnel WithDocument11 pagesConfigure A Site To Site VPN Tunnel WithArouna ChamNo ratings yet
- TP-1 VPN Configuration Lab Using Routers in Cisco Packet TracerDocument5 pagesTP-1 VPN Configuration Lab Using Routers in Cisco Packet TracerKhaoula RAZZAKINo ratings yet
- S2S Ikev2 Configure-AsaDocument9 pagesS2S Ikev2 Configure-Asahesenzade38No ratings yet
- Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument6 pagesConfigure and Verify A Site-To-Site IPsec VPN Using CLIMilošKovačevićNo ratings yet
- Configure ASA device and site-to-site IPsec VPNDocument13 pagesConfigure ASA device and site-to-site IPsec VPNDavid VardanyanNo ratings yet
- Technical ReportDocument19 pagesTechnical ReportUsmanNo ratings yet
- Config VPNDocument28 pagesConfig VPNAureo Miraval BravoNo ratings yet
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument4 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersSuhas KanikarNo ratings yet
- Lan2lan VPNDocument6 pagesLan2lan VPNFelix BlasioNo ratings yet
- IPSec VPNDocument5 pagesIPSec VPNcciersmanNo ratings yet
- Configuring Site To Site Ipsec VPN Tunnel Between Cisco RoutersDocument6 pagesConfiguring Site To Site Ipsec VPN Tunnel Between Cisco RoutersSyed AliNo ratings yet
- IPSec VPN LABDocument7 pagesIPSec VPN LABAparna Garg100% (2)
- 8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument5 pages8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLITalha Ur RehmanNo ratings yet
- Configuring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingDocument9 pagesConfiguring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingAndika PajriNo ratings yet
- Day3 Ch2 Manag IOSDocument27 pagesDay3 Ch2 Manag IOSManoj BorahNo ratings yet
- Lab VPNDocument9 pagesLab VPNhung kungNo ratings yet
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument6 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco Routerskymk21No ratings yet
- InteropDocument6 pagesInteropSaurav LodhNo ratings yet
- Juniper Netscreen - VPN TroubleshootingDocument8 pagesJuniper Netscreen - VPN TroubleshootingrubinbrittoNo ratings yet
- 1694000474061Document18 pages1694000474061Chinmay GhateNo ratings yet
- 8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorDocument5 pages8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorSalem TrabelsiNo ratings yet
- Site to Site VPN CLI Setup on GNS3Document6 pagesSite to Site VPN CLI Setup on GNS3dayno_majNo ratings yet
- Configure and Verify A Site To Site IPsec VPN Using CLIDocument4 pagesConfigure and Verify A Site To Site IPsec VPN Using CLICristhian HadesNo ratings yet
- ISP Lab Tutorial - GNS3Document19 pagesISP Lab Tutorial - GNS3Ceh0% (1)
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- SDWAN Ipsec IKEV2Document2 pagesSDWAN Ipsec IKEV2piyush aggarwalNo ratings yet
- Configuration Example of Dynamic IPsec BDocument15 pagesConfiguration Example of Dynamic IPsec BTransmission EngineerNo ratings yet
- Lab3 IPSecDocument13 pagesLab3 IPSecDanarNo ratings yet
- Configure and Verify Site-to-Site IPsec VPNDocument8 pagesConfigure and Verify Site-to-Site IPsec VPNAkram AliNo ratings yet
- IPsec Troubleshooting Understanding and Using Debug CommandsDocument17 pagesIPsec Troubleshooting Understanding and Using Debug CommandsVineeth KanthareddyNo ratings yet
- Cisco ASA Site-To-Site VPN ConfigsDocument2 pagesCisco ASA Site-To-Site VPN ConfigsAdelNo ratings yet
- IPsec quick and dirtyDocument4 pagesIPsec quick and dirtysgopal7No ratings yet
- Configuring Easy VPN With The IOS CLI: Learning ObjectivesDocument26 pagesConfiguring Easy VPN With The IOS CLI: Learning ObjectivesAli TariqNo ratings yet
- Cisco Ipsec Static DynamicDocument9 pagesCisco Ipsec Static DynamichsitadmNo ratings yet
- 19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersDocument5 pages19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersAna Maria Citlali Diaz HernandezNo ratings yet
- CCNA Basic Cofiguration CommandsDocument3 pagesCCNA Basic Cofiguration CommandsValeri ProninNo ratings yet
- Lab Cisco VPN-GenericDocument2 pagesLab Cisco VPN-Genericbliss21100% (5)
- OSCP NotesDocument78 pagesOSCP NotesRocKet100% (1)
- Dynamic PixDocument15 pagesDynamic PixAndika PajriNo ratings yet
- Configuration On Router1 Set Isakmp Policy Enable (Site To Site VPN)Document7 pagesConfiguration On Router1 Set Isakmp Policy Enable (Site To Site VPN)Varun MalhotraNo ratings yet
- FirewalllDocument15 pagesFirewalllfundacionunnuevos2023No ratings yet
- Installar NotesDocument42 pagesInstallar Notesvivik mirayNo ratings yet
- Configuring Cisco Site To Site Ipsec VPN With Dynamic Ip Endpoint Cisco RoutersDocument8 pagesConfiguring Cisco Site To Site Ipsec VPN With Dynamic Ip Endpoint Cisco RoutersjeannzonzidiNo ratings yet
- Tutor MikrotikDocument7 pagesTutor MikrotikgokekNo ratings yet
- Ipsec Troubleshooting: Understanding and Using Debug CommandsDocument17 pagesIpsec Troubleshooting: Understanding and Using Debug CommandsSuryamani KumarNo ratings yet
- ISAKMP RSA key IPsec tunnelsDocument4 pagesISAKMP RSA key IPsec tunnelssgopal7No ratings yet
- Ticket 9 - DMVPNDocument9 pagesTicket 9 - DMVPNPeter HixNo ratings yet
- A VPN Gateway SetupDocument6 pagesA VPN Gateway Setupachmadzulkarnaen100% (1)
- Discovery 17: Configure Static VTI Point-to-Point TunnelsDocument5 pagesDiscovery 17: Configure Static VTI Point-to-Point TunnelsIonut StanciuNo ratings yet
- 16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersDocument6 pages16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersimen loussaiefNo ratings yet
- 7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsDocument6 pages7.1.2.4 Packet Tracer - Configuring VPNs (Optional) InstructionsParitosh KumarNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- Evaluation of Some Intrusion Detection and Vulnerability Assessment ToolsFrom EverandEvaluation of Some Intrusion Detection and Vulnerability Assessment ToolsNo ratings yet
- Evaluation of Some Windows and Linux Intrusion Detection ToolsFrom EverandEvaluation of Some Windows and Linux Intrusion Detection ToolsNo ratings yet
- CA Unified Infrastructure Management Probes - ENU - Probe Development Tools - 20170109Document285 pagesCA Unified Infrastructure Management Probes - ENU - Probe Development Tools - 20170109R.s. FélixNo ratings yet
- Fix Mobile Convergence ' S StandardizationDocument11 pagesFix Mobile Convergence ' S StandardizationR.s. FélixNo ratings yet
- LTE Security I-Concept and Authentication (En)Document13 pagesLTE Security I-Concept and Authentication (En)anuj tripathi 12No ratings yet
- GSM AddressingDocument2 pagesGSM AddressingR.s. FélixNo ratings yet
- IMS Core Elements GuideDocument10 pagesIMS Core Elements GuideR.s. FélixNo ratings yet
- PS Call FlowDocument137 pagesPS Call FlowmanuelNo ratings yet
- Guide To The Zabbix Plugin Version 1.0.0 For FuelDocument12 pagesGuide To The Zabbix Plugin Version 1.0.0 For FuelR.s. FélixNo ratings yet
- SIP Request Methods ExplainedDocument1 pageSIP Request Methods ExplainedR.s. FélixNo ratings yet
- Fuel 8.0 InstallGuideDocument67 pagesFuel 8.0 InstallGuideR.s. Félix100% (1)
- 3GPP Long Term Evolution (LTE) - Voice Solutions in LTEDocument7 pages3GPP Long Term Evolution (LTE) - Voice Solutions in LTER.s. FélixNo ratings yet
- Nokia Mobile Packet Backbone Network White PaperDocument8 pagesNokia Mobile Packet Backbone Network White PaperR.s. FélixNo ratings yet
- FreephoneWalkthru in IMSDocument11 pagesFreephoneWalkthru in IMSR.s. FélixNo ratings yet
- Ixia Showcases Wireless Security, VoLTE, Offload, Planning InnovationsDocument2 pagesIxia Showcases Wireless Security, VoLTE, Offload, Planning InnovationsR.s. FélixNo ratings yet
- A Quick Guide To PMP MicrowaveDocument12 pagesA Quick Guide To PMP Microwaveธนวรรณ โภคาอนนต์No ratings yet
- Volte With SRVCC:: White Paper October 2012Document10 pagesVolte With SRVCC:: White Paper October 2012julian_binevNo ratings yet
- Cellular QosDocument24 pagesCellular Qosdayoladejo777No ratings yet
- BTS Training Troubleshooting Lte With WiresDocument5 pagesBTS Training Troubleshooting Lte With WiresTimmy ChengNo ratings yet
- Voiceip by Rahul RK (9986510206)Document27 pagesVoiceip by Rahul RK (9986510206)rahulkmarNo ratings yet
- Eozdemir21.12.2009 11.48.34sciDocument9 pagesEozdemir21.12.2009 11.48.34sciR.s. FélixNo ratings yet
- DBS3900 PDFDocument24 pagesDBS3900 PDFKaue LinkNo ratings yet
- Umts White PaperDocument18 pagesUmts White Paperimmy4uNo ratings yet
- Power System & Environment Monitoring (PSEM) Solution OverviewDocument49 pagesPower System & Environment Monitoring (PSEM) Solution OverviewleechulmiuNo ratings yet
- Base Transceiver Station - Wikipedia, The Free EncyclopediaDocument4 pagesBase Transceiver Station - Wikipedia, The Free EncyclopediaR.s. FélixNo ratings yet
- HUAWEI Outdoor Power System TP48120A-HD09A1 DatasheetDocument2 pagesHUAWEI Outdoor Power System TP48120A-HD09A1 DatasheetR.s. FélixNo ratings yet
- 6th Central Pay Commission Salary CalculatorDocument15 pages6th Central Pay Commission Salary Calculatorrakhonde100% (436)
- Large Capacity HUAWEI 64 Ports DSLAM VDSL2 MA5600, View Huawei Dslam, HUAWEI Product Details From Shanghai Chu Cheng Information Technology Co., Ltd. On AlibabaDocument6 pagesLarge Capacity HUAWEI 64 Ports DSLAM VDSL2 MA5600, View Huawei Dslam, HUAWEI Product Details From Shanghai Chu Cheng Information Technology Co., Ltd. On AlibabaR.s. FélixNo ratings yet
- AY SecurityDocument2 pagesAY SecurityR.s. FélixNo ratings yet
- Base Station Subsystem - Wikipedia, The Free EncyclopediaDocument5 pagesBase Station Subsystem - Wikipedia, The Free EncyclopediaR.s. FélixNo ratings yet
- HUAWEI IP DSLAM - MSAN MA5600 Large Capacity, View Ip Dslam, Huawei Product Details From Shanghai Chu Cheng Information Technology Co., Ltd. On AlibabaDocument5 pagesHUAWEI IP DSLAM - MSAN MA5600 Large Capacity, View Ip Dslam, Huawei Product Details From Shanghai Chu Cheng Information Technology Co., Ltd. On AlibabaR.s. FélixNo ratings yet
- Cedaspe Buchholz RelayDocument22 pagesCedaspe Buchholz RelayRichard Sy100% (2)
- QMS-17-SF Inspection and Test Plan TemplateDocument3 pagesQMS-17-SF Inspection and Test Plan TemplatearavinNo ratings yet
- IEI AM Application FormDocument9 pagesIEI AM Application Formjpr220022No ratings yet
- Csla 2 ElDocument5 pagesCsla 2 ElPedro CarvalhoNo ratings yet
- mITSM - ISO27k Foundation Script v.7.0.ENDocument131 pagesmITSM - ISO27k Foundation Script v.7.0.ENMonica CairesNo ratings yet
- DS51 Digital Substrobe Setup and Operation GuideDocument10 pagesDS51 Digital Substrobe Setup and Operation GuideJose Miguel Simon PeinadoNo ratings yet
- SQA-V and QwikCheck Gold Test Report 61010-1Document108 pagesSQA-V and QwikCheck Gold Test Report 61010-1rajeeshNo ratings yet
- 2010 Buick LaCrosse Complete Ordering GuideDocument33 pages2010 Buick LaCrosse Complete Ordering GuideDavid Traver Adolphus100% (1)
- Specification For Seamless Cold-Drawn Intermediate Alloy-Steel Heat-Exchanger and Condenser TubesDocument5 pagesSpecification For Seamless Cold-Drawn Intermediate Alloy-Steel Heat-Exchanger and Condenser Tubesmr.aghelNo ratings yet
- Republic Act No. 10611: GOVPH (/)Document26 pagesRepublic Act No. 10611: GOVPH (/)Christian FarofaldaneNo ratings yet
- Config Guide For Sap SourcingDocument36 pagesConfig Guide For Sap SourcingJawad Ahmed Hasan50% (2)
- HPA Enumeration of CPerfringensDocument13 pagesHPA Enumeration of CPerfringensHMVMCNo ratings yet
- Product Data Sheet 6Es7414-3Xj00-0Ab0: Cir - Configuration in RunDocument10 pagesProduct Data Sheet 6Es7414-3Xj00-0Ab0: Cir - Configuration in RunsadeghNo ratings yet
- Toyota GD Series Diesel Engines: Eugenio, 77Document16 pagesToyota GD Series Diesel Engines: Eugenio, 77Sutikno100% (4)
- Et-Wml100 Spec enDocument1 pageEt-Wml100 Spec en1015646541610312No ratings yet
- Elective III E CommerceDocument6 pagesElective III E CommercepocketoxyNo ratings yet
- Interleaving in GSMDocument3 pagesInterleaving in GSMNabil Magdi Hasan100% (3)
- 2012 Bike Master CatalogDocument221 pages2012 Bike Master CatalogAntonioPallone50% (2)
- 300-W STEREO / 600-W MONO Purepath™ HD Analog-Input Power StageDocument37 pages300-W STEREO / 600-W MONO Purepath™ HD Analog-Input Power StageJose ArmandoNo ratings yet
- Teltonika Fm1100 IoDocument1 pageTeltonika Fm1100 IoBbgGabrielNo ratings yet
- How To Simplify Compliance With The New ISO 13485 2016 Final PDFDocument63 pagesHow To Simplify Compliance With The New ISO 13485 2016 Final PDFAymen Bekir100% (3)
- Electronic Data InterchangeDocument17 pagesElectronic Data Interchangesudha_adventNo ratings yet
- VEGABAR 83 (Manual En)Document88 pagesVEGABAR 83 (Manual En)Fayez AlnamarnehNo ratings yet
- Iec 60947-7-1-2009 PDFDocument36 pagesIec 60947-7-1-2009 PDFphong vi100% (2)
- CS4400 Owners ManualDocument28 pagesCS4400 Owners Manualflanker_13No ratings yet
- Admin GuideDocument496 pagesAdmin GuideKrnv KumarNo ratings yet
- RestorationDesignCatalogue PDFDocument21 pagesRestorationDesignCatalogue PDFMarcinNo ratings yet
- 970772d0431022c3f94af580a01d95a2Document374 pages970772d0431022c3f94af580a01d95a2Stancu BranNo ratings yet
- Pelco VCD 5202 ManualDocument26 pagesPelco VCD 5202 ManualScott FiresheetsNo ratings yet
- Cdma2000 1xEV-DO Rev.A Scheduling Algorithm BSC 6600 Cluster PekanbaruDocument20 pagesCdma2000 1xEV-DO Rev.A Scheduling Algorithm BSC 6600 Cluster PekanbaruOpeyemi DadaNo ratings yet