Professional Documents
Culture Documents
Build & Deploy Secure Shorewall Firewall Protected Network v1.2
Uploaded by
Kefa RabahCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Build & Deploy Secure Shorewall Firewall Protected Network v1.2
Uploaded by
Kefa RabahCopyright:
Available Formats
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.
Global Open Versity
IT Security & Network Defense Hands-on Labs Training Manual
Build & Deploy Secure Shorewall Firewall Protected Network
Kefa Rabah
Global Open Versity, Vancouver Canada
krabah@globalopenversity.org www.globalopenversity.org
Table of Contents Page No.
BUILD & DEPLOY SECURE SHOREWALL FIREWALL PROTECTED NETWORK 1
Introduction 1
Part 1: Network Configuration 3
Part 2: Dynamic Host Configuration Protocol (DHCP) 3
Step 1: Install and Configure DHCP Server 3
Part 3: Download and Install Shorewall 5
Step 1: Download & Install Shorewall 5
Step 2: Configure Shorewall 5
Part 4: Using Web Webmin to Configure Shorewall 6
Step 1: Basic Configuration 6
Step 2: Configure Network Zones 8
Step 3: Configure Network Interfaces 11
Step 4: Configure the Default Policies (Policy) 13
Step 5: Configure Masquerading (masq) Rule 15
Step 6: Check Firewall Configuration 17
Step 7: Finally Start the Shorewall Firewall 18
Part 5: Advanced Configuration for Shorewall Firewall 18
Step1: Configuring Shorewall Firewall Rules 18
Step 1: Webserver installed on the Firewall box 19
Step 2: Port forwarding – Webserver on a box on the LAN 20
1. Port forwarding for Clients on the LAN 20
2. Port forwarding for Clients on the DMZ 21
3. Port Redirection 22
Step 3: Test DMZ Connectivity 23
Step 4: Type of Service (ToS) 24
Part 6: Troubleshooting 25
Part 7: Installing and configuring anti-virus software ClamAV 26
Part 8: Need More Training on Linux: 28
Secure Firewall Administration Training 28
Linux Administration Training 28
Part 9: Hands-on Lab Assignments 29
1
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.2
Global Open Versity
IT Security & Network Defense Hands-on Labs Training Manual
Build & Deploy Secure Shorewall Firewall Protected Network
By Kefa Rabah, krabah@globalopenversity.org July 26, 2010 GTS Institute
Introduction
The Shorewall, is a high-level tool for configuring Netfilter. You describe your firewall/gateway
requirements using entries in a set of configuration files. Shorewall reads those configuration files and with
the help of the iptables utility, Shorewall configures Netfilter to match your requirements. Shorewall can be
used on a dedicated firewall system, a multi-function gateway/router/server or on a standalone GNU/Linux
system. Shorewall does not use Netfilter's ipchains compatibility mode and can thus take advantage of
Netfilter's connection state tracking capabilities.
CentOS is a community-supported, free and open source operating system based on Red Hat Enterprise
Linux. It exists to provide a free enterprise class computing platform and strives to maintain 100% binary
compatibility with its upstream distribution .CentOS stands for "Community ENTerprise Operating
System". CentOS is the perfect server for people who need an enterprise class operating system stability
without the cost of certification and support and pocket burning baggage that comes with proprietary
software. And the beauty is CentOS is free.
Webmin is a web-based GUI interface for system administration for Linux/UNIX. Using any modern web
browser, you can setup user accounts, Apache, DNS, file sharing and much more. Webmin removes the
need to manually edit UNIX configuration files like /etc/passwd, and lets you manage a system from
the console or remotely with ease. Here we’ll use Webmin mainly to configure Shorewall firewall.
Lockdown server: we also need to lockdown our firewall server to secure our application servers against
cyber-criminals and malwares. For this we’ll use Clamd. Clamd which comes integrated with ClamAV and
Clamav-db fits the bill for our task. It’s a multi-threaded daemon that uses libclamav to scan files for
viruses. The daemon listens for incoming connections on Unix and/or TCP socket and scans files or
directories on demand for viruses. The daemon is fully configurable via the clamd.conf file. It reads the
configuration from /etc/clamd.conf. Clam AntiVirus (ClamAV) is an open source (GPL) anti-virus
toolkit for UNIX, designed especially for e-mail scanning on mail gateways. It provides a number of utilities
including a flexible and scalable multi-threaded daemon, a command line scanner and advanced tool for
automatic database updates. The core of the package is an anti-virus engine available in a form of shared
library.
Assumptions:
It’s assumed that you have a good understanding of Linux operating system and its working environment.
It’s also assumed that you know how to install and configure Linux CentOS5, if not go ahead and pop over
to scribd.com and check out a good howto entitled “Install Guide Linux CentOS5 Server v1.1” to get you
started.
1
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.2
Solution:
In this Lab session, you’ll learn how to setup virtual network on VMware (you may also use any other
virtual machines like MS VirtualPC, Linux Xen, or VirtualBox from Oracle). Next it’s assumed that you
know how to install and configure Linux CentOS5 (VM1) with three NIC adapters. On the Linux VM1, I’ll
show you how to install & configure a DHCP server and Shorewall firewall on it. I’ll show you how to use
Webmin to ease the pain of configuring Shorewall firewall. You’ll also learn how to configure to more
virtual machines (VM) either a Linux distros or any OS of choice to use for testing your firewalled network
connectivity form LAN and DMZ to public network (Internet). Finally, you’ll have an opportunity to do some
Hands-on Labs assignment to test what you have learned in this lab session. Once you’re done with this
labs session you should have gained an experience and capability to enable you to plan design implement
and deploy a secure private network or Home/SMB office network infrastructure.
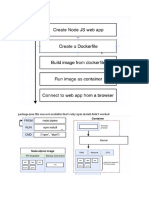
Fig. 1: Private LAN, with test PC (Internal PC) added
Note: once you’re done with hands-on training and build a pilot test lab for prototype testing, and
all is working great then you can migrate your setup to your production environment.
2
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.2
Part 1: Network Configuration
Figure 1 show the setup for our hands-on lab session of our private Home/SMB LAN, which is configured
using VMware with two NIC adapters attached to VMnet2. The eth0 is attached to the public side of the
network or Internet and is receiving its IP address from DHCP. The eth1 is our internal LAN network, and
is configured with static IP address and is also the NIC that is attached to DHCP server, which feeds the
dynamic IP address to the devices located within the private LAN via the VMnet2 virtual switch. Machine 1
is running Linux CentOS5 server which we’ll use to install the DHCP server and the firewall on eth1, and
also the Shorewall firewall. The eth2 via the VMnet3 virtual switch is our DMZ network and, all the
servers located here, e.g., VM3 Webserver, are configured with static IP address.
Part 2: Dynamic Host Configuration Protocol (DHCP)
DHCP (Dynamic Host Configuration Protocol) is an Internet protocol for automating the configuration of
computers that use TCP/IP. DHCP can be used to automatically assign IP addresses, to deliver TCP/IP
stack configuration parameters such as the subnet mask and default router, and to provide other
configuration information such as the addresses for printer, time and news servers.
Step 1: Install and Configure DHCP Server
By default all Linux distros come with DHCP server. However, rather than use the default DHCP server
included with your Red Hat / Fedora Linux system, for security reasons, it’s recommend that you use the
latest version of software.
Why is it important to have the latest version? In IT security best practices, as is with any other software
that you're going to run on your server, it's critically important that you have the very latest version of this
'daemon' (the Linux lingo for programs that run on the server without intervention) on your system. It's
also very important to shut off any services that you’re not using
Installation
1. Head over to the Internet Software Consortium and Download the latest version of the
DHCP Server. As I write this, it's at version "dhcp-4.1.0p1.tar.gz".
2. Once you've downloaded it, move the file to your favorite location (/usr/local/src for this guide)
and unpack it by running the following command:
# tar -zxvf dhcp-*.tar.gz
3. This will create a directory called "DHCP 4.1.0p1" (in our case). Change into newly created
directory and run the following command as root:
# ./configure
4. If there are no errors you may run the following commands (as root):
# make && make install
3
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.2
to build and install the software. You may be prompted for the root password, then, if you typed it in
correctly, the new DHCP server will be installed onto your system.
Note: If you come across any errors when running the above commands you are likely missing some
library files or files on your system.
5. Good. Now you have the latest DHCP server it's time to configure it properly for your environment.
6. That’s, before launching the DHCP server, copy the file "server/dhcpd.conf" from the build
directory into your "/etc" directory,
# cp server/dhcpd.conf /etc/
7. Finally, it’s time to edit the configuration file to match your system configuration. Here's what the
"/etc/dhcpd.conf" file looks like:
ddns-update-style none; # keep it simple for now
ignore client-updates; # here too
DHCPARGS=eth1; # tells it what interface to listen on
subnet 192.168.0.0 netmask 255.255.255.0 {
# --- default gateway
option routers 192.168.0.1; # gateway on your eth1 internal interface
option subnet-mask 255.255.255.0; # subnet mask
# option domain-name "example.com"; # domain name given to client
# the IP of your ISP's nameservers and any other local name server(s) you're using. You can
# normally found under "/etc/resolv.conf" file. These will be distributed all DHCP clients
option domain-name-servers 192.168.1.1;
option time-offset off; # Pacific Standard Time - set to what you have
option ip-forwarding 21600;
range 192.168.0.128 192.168.0.254; # the range of IP's your clients will get
default-lease-time 21600; # how long the client's will keep the same IP
max-lease-time 43200;
# we want the nameserver to appear at a fixed address (optional)
host ns {
next-server ns1.ispserver.net; # change to your ISP's nameservers
hardware ethernet 0A:A9:5B:8E:05:67; # hardware MAC
fixed-address 192.68.0.7 # your ISP's nameserver IP
}
}
4
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.2
Note 1: For the DNS Server, you can use the OpenDNS for all your public DNS needs; it's free and
allows for content filtering. For production server remember to use public IP address.
Note 2: It’s very important that you make sure that you set the domain name properly, identify your
set of DNS servers by name, and define the subnet range for which you want to provide services via
DHCP.
8. Now we restart the DHCP server
# service dhcpd configtest
Syntax: OK
# service dhcpd restart
Note: When checking the configuration for errors, if there are errors, you'll find them listed in
/var/log/messages so the changes will take effect.
Part 3: Download and Install Shorewall
Step 1: Download & Install Shorewall
1. Hope over to shorewall official web site for newer versions. http://www.shorewall.net/download.htm. At
the time of writing this article we downloaded: shorewall-4.4.10.3.noarch.rpm
2. To install shorewall, just open a terminal and run:
rpm -ivh shorewall-4.4.10-3.noarch.rpm
3. Now use the whereis command to locate shorewall installed directory:
4. As you can observe above, we have configuration files located in /etc/shorewall.
5. We’re done with this section.
Step 2: Configure Shorewall
Here we need to modify shorewall configuration file /etc/shorewall/shorewall.conf to enable it
start.
6. To do this, use your favorite Text editor and it the file as follows::
5
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.2
vi /etc/shorewall/shorewall.conf
7. Change the first line from
STARTUP_ENABLED=No
to
STARTUP_ENABLED=Yes
8. Also ensure that forwarding is enabled forwarding and reads "IP_Forwarding=on"
9. Save and exit (in vi, hit [ESC] and then ':wq').
Note: Shorewall Web interface or GUI tool
You can download Webmin for GUI configuration of Shorewall. You’ll also need the Webmin interface
for Shorewall to configure through GUI. You can download from here.
Part 4: Using Web Webmin to Configure Shorewall
Step 1: Basic Configuration
As the Linux server implementation increases every year, it becomes more and more important to have
easy to use tools for server administration, instead of logging on with ssh. GUI based tools have the effect
of an increased accessibility and it creates a clearer understanding of the configuration and features of the
functions of a server and of course less prone to error which is common with manual script configuration.
In this section I show through a step-by-step procedure for configuring the Shorewall firewall using
Webmin as the interface instead of using the console for editing files. It assumed that you already have a
server in basic configuration with Webmin. After the installation of Webmin and configuring it you can login
using the URL http://localhost:10000 or http://yourdomain:10000
1. Now you see the first screen of the Webmin admin interface.
2. Here you can select the topics to different tasks, such as Webmin administration, different server
administration tasks etc.
3. Scroll down and click Networking Æ click Shorewall Firewall, link to access Shorewall
configuration screen, as shown in Fig. 1:
6
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
Global Open Versity, ICT Labs Build & Deploy Secure Shorewall Firewall Network.v1.2
Fig. 2: Shorewall Firewall configuration screen
In the next section we’ll expand on the different options for configuring Shorewall Firewall.
1. Follow the link below to access the full document.
The full document has moved to Docstoc.com. You can access and download it from
here:
• Build & Deploy Secure Shorewall Firewall Protected Network v1.2
OR
http://www.docstoc.com/docs/50346510/Build-and-Deploy-Secure-Shorewall-Firewall-Protected-Network
Fellow us on Twitter: Global Open Versity and Kefa Rabah
-----------------------------------------------
Kefa Rabah is the Founder of Global Technology Solutions Institute. Kefa is knowledgeable in several
fields of Science & Technology, Information Security Compliance and Project Management, and
Renewable Energy Systems. He is also the founder of Global Open Versity, a place to enhance your
educating and career goals using the latest innovations and technologies.
7
© April 2007, Kefa Rabah, Global Open Versity, Vancouver Canada
www.globalopenversity.org EBT107 – Secure Firewall System Administration Training
You might also like
- Setting Up of An Open Source Based Private CloudDocument6 pagesSetting Up of An Open Source Based Private Cloudsmart teleNo ratings yet
- n1000v Install OvaDocument24 pagesn1000v Install OvaaykargilNo ratings yet
- Ultimatep2V: by Chris Huss and Mike LaverickDocument29 pagesUltimatep2V: by Chris Huss and Mike LaverickmultihumanNo ratings yet
- BeEF XSS FrameworkDocument3 pagesBeEF XSS Frameworkmario_soares_94No ratings yet
- Step-By-Step Guide Installing Ethereum & Building A Blockchain On Ubuntu 16.04 Linux ServerDocument10 pagesStep-By-Step Guide Installing Ethereum & Building A Blockchain On Ubuntu 16.04 Linux ServerKefa Rabah0% (1)
- Computer System Engineering Department ENCS413 Network Lab Access ListDocument13 pagesComputer System Engineering Department ENCS413 Network Lab Access Listak akNo ratings yet
- Extra Checks in ProwlerDocument2 pagesExtra Checks in Prowlermaham sabirNo ratings yet
- CCNA 3 and 4 Companion Guide, 3rd Edition (CNAP)Document9 pagesCCNA 3 and 4 Companion Guide, 3rd Edition (CNAP)api-3826866100% (1)
- 1.1 Laravel PDFDocument10 pages1.1 Laravel PDFjande0115194No ratings yet
- BlockchainDocument26 pagesBlockchainPranav BansalNo ratings yet
- Huawei Blockchain WhitepaperDocument63 pagesHuawei Blockchain WhitepaperkimshaynearriolaNo ratings yet
- Fortinet Fortigate Workspot Configuration Guide 1.0Document13 pagesFortinet Fortigate Workspot Configuration Guide 1.0Abdelilah CharboubNo ratings yet
- Hyperconverged Vs Traditional Paper v4Document5 pagesHyperconverged Vs Traditional Paper v4vipsin1974No ratings yet
- RbAC 3rd ReviewDocument22 pagesRbAC 3rd ReviewRebeckah VimalaNo ratings yet
- 10 Outstanding Linux Backup Utilities: FwbackupsDocument3 pages10 Outstanding Linux Backup Utilities: FwbackupsadminakNo ratings yet
- Ce500 FactoryDocument9 pagesCe500 FactoryAgus HariyantoNo ratings yet
- Virtual Private Networking With Openvpn: Wim Kerkhoff Fraser Valley Linux Users Group April 15, 2004Document11 pagesVirtual Private Networking With Openvpn: Wim Kerkhoff Fraser Valley Linux Users Group April 15, 2004Ihsan Nuriza HNo ratings yet
- Certificate AuthoritiesDocument11 pagesCertificate AuthoritiesLiloMejiaNo ratings yet
- Blockchain Crash CourseDocument38 pagesBlockchain Crash CourseAlexandre CarvalhoNo ratings yet
- Introduction To Cloud ComputingDocument68 pagesIntroduction To Cloud ComputingyosiaNo ratings yet
- Docker Cheat SheetDocument50 pagesDocker Cheat SheetabhinavsrivastavNo ratings yet
- High Availability Cluster - Proxmox VEDocument4 pagesHigh Availability Cluster - Proxmox VEDhani MultisolutionNo ratings yet
- Vyatta Open-VpnDocument10 pagesVyatta Open-Vpnduranduran11100% (1)
- Install Mod - SecurityDocument18 pagesInstall Mod - Securitychinku85No ratings yet
- IMPV Path To Your Data InfographicDocument1 pageIMPV Path To Your Data InfographicghileonNo ratings yet
- Cisco Ace To Nginx: Migration GuideDocument51 pagesCisco Ace To Nginx: Migration GuideSèdjro Enock TITONo ratings yet
- Preferred Architecture For Cisco WebEx Hybrid ServicesDocument126 pagesPreferred Architecture For Cisco WebEx Hybrid ServicesDijar VrellaNo ratings yet
- Blockchain Technology PDFDocument11 pagesBlockchain Technology PDFAnshul DiwakarNo ratings yet
- Cisco Catalyst Switch GuideDocument59 pagesCisco Catalyst Switch Guideapi-3695954100% (3)
- An Introduction To ARP Spoofing & Other Attacks: Presenting: Philip Yakubovsky & Ohad BenitaDocument28 pagesAn Introduction To ARP Spoofing & Other Attacks: Presenting: Philip Yakubovsky & Ohad Benitakhanh buiNo ratings yet
- Cisco UCMDocument1,266 pagesCisco UCMdondegNo ratings yet
- With Intel Xeon Processors: Cisco Unif Ied Computing SystemDocument2 pagesWith Intel Xeon Processors: Cisco Unif Ied Computing SystemPavan NavNo ratings yet
- Technical Sales LENU319EMDocument239 pagesTechnical Sales LENU319EMHibaNo ratings yet
- What Is BigBlueButtonDocument32 pagesWhat Is BigBlueButtonlbonilla3089No ratings yet
- Howto Build A Wifi Hotspot Using Chillispot and Debian EtchDocument12 pagesHowto Build A Wifi Hotspot Using Chillispot and Debian EtchMas AinunNo ratings yet
- Configuration Guide For Red Hat Linux Host AttachmentDocument56 pagesConfiguration Guide For Red Hat Linux Host AttachmentvqbhanuNo ratings yet
- YateBTS LabKit Quick Start GuideDocument6 pagesYateBTS LabKit Quick Start GuideBubaiko JhonNo ratings yet
- Paessler PRTG v12 ManualDocument1,345 pagesPaessler PRTG v12 ManualIsrael MurilloNo ratings yet
- Integrative Network Design ProjectDocument11 pagesIntegrative Network Design ProjectJayNo ratings yet
- Step by Step Build and Deploy Citrix XenServer 5 6 and XenCenterDocument9 pagesStep by Step Build and Deploy Citrix XenServer 5 6 and XenCenterJ. Jonas JansonNo ratings yet
- Firewall RulesDocument1 pageFirewall RulesmarkdavidboydNo ratings yet
- Partner Fat Pipe Deployment GuideDocument18 pagesPartner Fat Pipe Deployment GuidePrasad KshirsagarNo ratings yet
- Ansible@nettrainDocument939 pagesAnsible@nettrainelahi elahiNo ratings yet
- Preview Ethical Hacking Starter KitDocument45 pagesPreview Ethical Hacking Starter KitJavierNo ratings yet
- Portnox v3.3 - Getting Started GuideDocument42 pagesPortnox v3.3 - Getting Started Guideoscar tebarNo ratings yet
- SSL Mitm AttacksDocument12 pagesSSL Mitm AttacksMymy MimiNo ratings yet
- Cclab ManualDocument69 pagesCclab ManualNandhaNo ratings yet
- DeHBQ5nPEem6SAq8ilBGGg Your IBM Subject Matter Experts Intro To Cybersecurity ToolsDocument7 pagesDeHBQ5nPEem6SAq8ilBGGg Your IBM Subject Matter Experts Intro To Cybersecurity ToolsMitali MadhusmitaNo ratings yet
- Nutanix TechNote-VMware VSphere Networking With NutanixDocument18 pagesNutanix TechNote-VMware VSphere Networking With NutanixKRISNo ratings yet
- Cisco UCSDocument23 pagesCisco UCSHarish Krishnamoorthy100% (1)
- A Hands-On Tutorial: Working With Smart Contracts in EthereumDocument50 pagesA Hands-On Tutorial: Working With Smart Contracts in EthereumJohn RootNo ratings yet
- Nginx Security Hardening GuideDocument12 pagesNginx Security Hardening Guidescrib_nokNo ratings yet
- Configuration GuideDocument25 pagesConfiguration GuideAlexanderEstepaPazNo ratings yet
- Opennebula 5.6 Deployment Guide: Release 5.6.2Document224 pagesOpennebula 5.6 Deployment Guide: Release 5.6.2darkd76nsNo ratings yet
- Install Ntopng Network Traffic Monitoring Tool On CentOS 7Document6 pagesInstall Ntopng Network Traffic Monitoring Tool On CentOS 7anirudhas100% (1)
- UntitledDocument5 pagesUntitledHemal KarmakarNo ratings yet
- Netlab Install GuideDocument27 pagesNetlab Install Guideviorel_grigoreNo ratings yet
- Fintech and Blockchain PPT-1-1Document47 pagesFintech and Blockchain PPT-1-1Namyenya MaryNo ratings yet
- Mimikatz PhdaysDocument51 pagesMimikatz PhdaysCarlos VizcarraNo ratings yet
- AlienVault Component CommunicationxDocument12 pagesAlienVault Component CommunicationxReallykul Kuul100% (1)
- SSL Fundamentals Linux AcademyDocument1 pageSSL Fundamentals Linux AcademyDivyam PateriyaNo ratings yet
- Tripwire CheatsheetDocument6 pagesTripwire CheatsheetdigitaltvguyNo ratings yet
- Step-By-Step Guide On Deploying Blockchain Voting Smart ContractsDocument21 pagesStep-By-Step Guide On Deploying Blockchain Voting Smart ContractsKefa RabahNo ratings yet
- Developing Smart Contract On Ethereum Blockchain Using Truffle FrameworkDocument11 pagesDeveloping Smart Contract On Ethereum Blockchain Using Truffle FrameworkKefa RabahNo ratings yet
- Step-By-Step Guide Build & Deploy Ethereum Blockchain Smart ContractDocument44 pagesStep-By-Step Guide Build & Deploy Ethereum Blockchain Smart ContractKefa Rabah100% (1)
- Step-By-Step Guide Building & Deploying A Private Blockchain Network On WindowsDocument22 pagesStep-By-Step Guide Building & Deploying A Private Blockchain Network On WindowsKefa RabahNo ratings yet
- Step-By-Step Guide On Deploying Revenue Sharing Blockchain Smart Contracts Using Remix-IDE On WindowsDocument27 pagesStep-By-Step Guide On Deploying Revenue Sharing Blockchain Smart Contracts Using Remix-IDE On WindowsKefa RabahNo ratings yet
- Step-By-Step Guide Writing & Testing Real-World Crowdsale Contracts On EthereumDocument24 pagesStep-By-Step Guide Writing & Testing Real-World Crowdsale Contracts On EthereumKefa Rabah100% (1)
- Mara Research JournalsDocument7 pagesMara Research JournalsKefa RabahNo ratings yet
- Build and Deploy Your Own Learning Management Systems Using Moodle 2.x On CentOS-6 Server v1.0Document11 pagesBuild and Deploy Your Own Learning Management Systems Using Moodle 2.x On CentOS-6 Server v1.0Kefa RabahNo ratings yet
- Install Guide Ubuntu 10.04 Lucid Lynx On Proxmox VE ServerDocument12 pagesInstall Guide Ubuntu 10.04 Lucid Lynx On Proxmox VE ServerKefa RabahNo ratings yet
- Jaramogi Oginga Odinga University of Science and Technology, Kenya - BSC Computer Security & Forensics MSC IT Security & Audit, PHD IT Security & AuditDocument2 pagesJaramogi Oginga Odinga University of Science and Technology, Kenya - BSC Computer Security & Forensics MSC IT Security & Audit, PHD IT Security & AuditKefa Rabah100% (1)
- Step-By-Step Install Guide Enterprise Application Servers With Proxmox VE ClusterDocument19 pagesStep-By-Step Install Guide Enterprise Application Servers With Proxmox VE ClusterKefa Rabah100% (1)
- Build and Deploy Your Own ERP Powered by Apache OfBiz ERP On Fedora 17 Server v1.0Document17 pagesBuild and Deploy Your Own ERP Powered by Apache OfBiz ERP On Fedora 17 Server v1.0Kefa Rabah100% (1)
- Build Your Own Multimedia Production Studio With Ubuntu StudioDocument32 pagesBuild Your Own Multimedia Production Studio With Ubuntu StudioKefa RabahNo ratings yet
- Step-By-Step Install Guide Ubuntu 9.10 Karmic ServerDocument36 pagesStep-By-Step Install Guide Ubuntu 9.10 Karmic ServerKefa RabahNo ratings yet
- Step-By-Step Install Guide CentOS-5 On Proxmox VEDocument12 pagesStep-By-Step Install Guide CentOS-5 On Proxmox VEKefa Rabah100% (1)
- Step-By-Step Install Guide OpenEMR On Ubuntu 10.04 LTSDocument27 pagesStep-By-Step Install Guide OpenEMR On Ubuntu 10.04 LTSKefa RabahNo ratings yet
- Step-By-Step Install Guide OpenEMR On Linux Debian 5 ServerDocument24 pagesStep-By-Step Install Guide OpenEMR On Linux Debian 5 ServerKefa Rabah100% (1)
- Using Samba 3 Client Technology and Kerberos For Win2k8 AD-Based Identity ManagementDocument16 pagesUsing Samba 3 Client Technology and Kerberos For Win2k8 AD-Based Identity ManagementKefa RabahNo ratings yet
- Install Guide Linux Ubuntu 11.04 Natty DesktopDocument8 pagesInstall Guide Linux Ubuntu 11.04 Natty DesktopKefa RabahNo ratings yet
- Step-By-Step Install Guide Mandriva Linux 2010 Spring v1.0Document46 pagesStep-By-Step Install Guide Mandriva Linux 2010 Spring v1.0Kefa Rabah100% (2)
- Step-By-Step Install Guide Ubuntu 9.04 Jaunty ServerDocument29 pagesStep-By-Step Install Guide Ubuntu 9.04 Jaunty ServerKefa RabahNo ratings yet
- Deploy Private Document Management System With KnowledgeTree DMS On Windows 7Document27 pagesDeploy Private Document Management System With KnowledgeTree DMS On Windows 7Kefa RabahNo ratings yet
- Step-By-Step Install Guide Debian 5 Lenny ServerDocument10 pagesStep-By-Step Install Guide Debian 5 Lenny ServerKefa RabahNo ratings yet
- Build and Deploy Your Own Private PIAF-GOLD With Asterisk VoIP Telephony SystemDocument15 pagesBuild and Deploy Your Own Private PIAF-GOLD With Asterisk VoIP Telephony SystemKefa RabahNo ratings yet
- Step-By-Step Install Guide CiviCRM With Drupal CMS On LinuxDocument21 pagesStep-By-Step Install Guide CiviCRM With Drupal CMS On LinuxKefa RabahNo ratings yet
- Build and Deploy Enterprise SipXecs 4.2 IP PBX Integration With Openfire/XMPPDocument15 pagesBuild and Deploy Enterprise SipXecs 4.2 IP PBX Integration With Openfire/XMPPKefa Rabah100% (1)
- Step-By-Step Build and Deploy Xen Hypervisor Virtualization On Linux OpenSUSE 11.3 ServerDocument11 pagesStep-By-Step Build and Deploy Xen Hypervisor Virtualization On Linux OpenSUSE 11.3 ServerKefa RabahNo ratings yet
- Step-By-Step Install Guide VtigerCRM On Linux v1.0Document31 pagesStep-By-Step Install Guide VtigerCRM On Linux v1.0Kefa RabahNo ratings yet
- Step-By-Step Install Guide Mahara Eportfolio & Integration With Moodle LMS v1.0Document9 pagesStep-By-Step Install Guide Mahara Eportfolio & Integration With Moodle LMS v1.0Kefa Rabah0% (1)
- Chapter 5 Interfaces ResumoDocument20 pagesChapter 5 Interfaces ResumoGabrielNo ratings yet
- 3.6.1.2 Packet Tracer - Skills Integration ChallengeDocument4 pages3.6.1.2 Packet Tracer - Skills Integration ChallengejohnathanNo ratings yet
- Barly WicaksonoDocument3 pagesBarly WicaksonoBarly WicaksonoNo ratings yet
- ESX Configuration Guide - ESX 4.0Document246 pagesESX Configuration Guide - ESX 4.0Priyo SanyotoNo ratings yet
- Exam H12-222 - V2.5-ENU: The Safer, Easier Way To Help You Pass Any IT ExamsDocument91 pagesExam H12-222 - V2.5-ENU: The Safer, Easier Way To Help You Pass Any IT ExamsfishNo ratings yet
- Manual Zte ZXHN F660: Read/DownloadDocument2 pagesManual Zte ZXHN F660: Read/DownloadChandra CumpretNo ratings yet
- Ltrcol 2250Document39 pagesLtrcol 2250cheatNo ratings yet
- 2013-05-08 Ericsson RELEASE NOTES 5.0.1Document34 pages2013-05-08 Ericsson RELEASE NOTES 5.0.1Antonio MantovaniNo ratings yet
- UntitledDocument532 pagesUntitledJaredNo ratings yet
- Camera: Installation Guide v1.0Document6 pagesCamera: Installation Guide v1.0LeonardLapatratNo ratings yet
- 300-710 - SCNF EditDocument30 pages300-710 - SCNF EditgochorneaNo ratings yet
- 9060 (A) ManualDocument23 pages9060 (A) ManualpttnpttnNo ratings yet
- 22 04 2022 00 05 25 NetDocument4 pages22 04 2022 00 05 25 NetPahlavon Toshpo‘latovNo ratings yet
- 1.1 4.3 Introduction To Cisco Packet Tracer PDFDocument6 pages1.1 4.3 Introduction To Cisco Packet Tracer PDFPkumarNo ratings yet
- F0sw3d2205iv03 Ziv sw3 Din Data Sheet R3-IDocument2 pagesF0sw3d2205iv03 Ziv sw3 Din Data Sheet R3-IMạc DavidNo ratings yet
- PROGRAMA AUDUINO Auto Con GruaDocument4 pagesPROGRAMA AUDUINO Auto Con GruaMarcelo VargasNo ratings yet
- 20 June Sheet 6Document4 pages20 June Sheet 6aman98No ratings yet
- APS 6.0 Defend Unit 3 View Attack Details - 20180823 PDFDocument82 pagesAPS 6.0 Defend Unit 3 View Attack Details - 20180823 PDFmasterlinh2008No ratings yet
- How To Configure IPSec VPNs 2.1Document15 pagesHow To Configure IPSec VPNs 2.1Monica VanceNo ratings yet
- PTP Best Practices For Media and Entertainment and Broadcast CentersDocument16 pagesPTP Best Practices For Media and Entertainment and Broadcast CentersSukrit ChaudharyNo ratings yet
- Configuring A Wireless Router and ClientDocument4 pagesConfiguring A Wireless Router and ClientJomar RamosNo ratings yet
- CTR 8500-8300 3.6.0 TACACS+ CLI Commands - July2018Document16 pagesCTR 8500-8300 3.6.0 TACACS+ CLI Commands - July2018Bryan Delfín Aguirre OrtegaNo ratings yet
- Mediaaccess Tg784: Wireless Voip GatewayDocument5 pagesMediaaccess Tg784: Wireless Voip GatewaykallesvenNo ratings yet
- Gilat Product Sheet SkyEdge II C Capricorn 4Document2 pagesGilat Product Sheet SkyEdge II C Capricorn 4gilbertixNo ratings yet
- ISCOM2824G Conifuguration20090519Document378 pagesISCOM2824G Conifuguration20090519Svetlin IvanovNo ratings yet
- Competition Between Huawei Switches and Cisco SwitchesDocument6 pagesCompetition Between Huawei Switches and Cisco SwitchesElizabeth RichNo ratings yet
- pt530 2 PDFDocument61 pagespt530 2 PDFJOSE GARCIA TAGLENo ratings yet