Professional Documents
Culture Documents
Hitachi ID Privileged Access Manager Brochure
Uploaded by
HitachiIDCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Hitachi ID Privileged Access Manager Brochure
Uploaded by
HitachiIDCopyright:
Available Formats
Hitachi ID Privileged Access Manager hitachi-id.
com
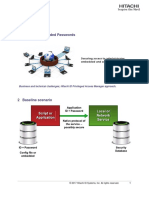
Securing Access to Privileged Accounts
Hitachi ID Privileged Access Manager secures access to elevated privileges. It
eliminates shared and static passwords to privileged accounts and enforces
strong authentication and reliable authorization prior to granting access. User
access is logged, creating strong accountability.
Strong Authentication, Authorization
HiPAM integrates with corporate directories to identify users. It can either leverage existing 2FA
solutions, such as tokens or smart cards, or introduce its own 2FA, via a smart-phone app.
Temporary Access to Accounts and Groups
Challenges Users may request access to shared or personal administrator accounts or membership in security
groups. Access may be pre-authorized or require approval using the included workflow.
Security
Elevated-privilege accounts are a prime target for
attackers and are subject to abuse and misuse
Password Randomization and Vaulting
by authorized users. Static, shared and plaintext HiPAM randomizes passwords on a schedule and after each session. Passwords are stored in an
passwords can be compromised by departed encrypted, replicated vault that protects against data loss and service interruption.
employees or malicious software. When
authorized users sign into shared accounts there
is little to no accountability for their actions, which
is problematic both for problem diagnosis and
Access Disclosure, not Password Disclosure
forensic audits. HiPAM can launch administrator programs on behalf of users and inject credentials from its vault.
Sessions can be established directly from the users PC, or via VDI or HTML5 proxy servers.
Regulatory Compliance
Government legislation and industry guidelines
regarding privacy protection and corporate Session Recording
governance, including PCI-DSS, SOX, EU GDPR,
HIPAA and more all demand robust internal When HiPAM launches login sessions, it can also capture video, keystrokes and more, creating a
controls. This includes control over privileged forensic audit trail.
access, be it privileged accounts or security
groups.
Coordination Discovery and Analysis of SSH Trust
HiPAM discovers SSH trust relationships and can analyze trust graphs. It can inject temporary trusts
Changing passwords on shared accounts is
to grant access to Unix/Linux systems.
difficult, as is changing service account and
embedded passwords. Manual processes are
time consuming, error prone and costly but failure
to change passwords violates policy. Support for Local Accounts on Mobile PCs
A local agent is included to secure access to PCs that may be turned off, disconnected or moved
off-site.
Key Benefits
Hitachi ID Privileged Access Manager secures
access to elevated privileges, be they shared Windows Service Account Password Changes
accounts, personal administrator accounts,
service accounts, embedded accounts or security When HiPAM randomizes Windows service account passwords, it notifies SCM, the Scheduler, IIS
groups. It replaces static, shared passwords and other OS components of the new password, to ensure uninterrupted service after each
with periodically set, random passwords. Users password change.
and applications are strongly authenticated and
authorized before gaining access. Audit logs and
session recordings create strong accountability A Secure API to Replace Static, Embedded Passwords
for access.
A secure API allows one application to acquire a password for connecting to another. This
eliminates plaintext passwords in source code or configuration files.
Hitachi ID Systems, Inc.
2017 Hitachi ID Systems, Inc. All rights reserved.
All other marks, symbols and trademarks are the property of their respective owners.
Hitachi ID Privileged Access Manager 2
Auto-discovery of Systems and Accounts Included Connectors
HiPAM can automatically discover systems, look up appropriate credentials, connect and scan for Directories
accounts, groups and services. Discovered systems and accounts are automatically assigned to
Any LDAP, AD, eDirectory, NIS/NIS+
policies based on import rules.
Servers
Analytics and Dashboards Windows 2000--2012, Samba, SharePoint
Built-in reports and dashboards can monitor the behaviour of individual users, access to systems Databases
and overall activity. A risk model flags unusual patterns prior to access and in post-facto reviews. Oracle, Sybase, SQL Server, DB2/UDB, ODBC, Informix, Progress
Unix
Linux, Solaris, AIX, HPUX, many more
Mainframes
z/OS with RAC/F, ACF/2 or TopSecret
Midrange
iSeries (OS400), OpenVMS
ERP
JDE, Oracle eBiz, PeopleSoft, SAP, Siebel, Business Objects
Collaboration
Lotus Notes, Exchange
Tokens, Smart Cards
RSA SecurID, SafeWord, Duo Security, RADIUS, ActivIdentity,
Schlumberger
WebSSO
CA SiteMinder, IBM TAM, Oracle AM, RSA Access Manager
Ticket systems
ServiceNow, Remedy, BMC SDE, HP SM, CA, Assyst, HEAT, Altiris,
Clarify, Track-It!, RSA Envision, MS SCS Manager
Network devices
Cisco IOS, Juniper JunOS, F5, iLO cards, DRAC cards, RSA cards,
etc
Cloud
Salesforce.com, WebEx, Google Apps, Office 365, Concur, AWS,
vCloud
Miscellaneous
OLAP, Hyperion, iLearn, Cache, Success Factors, vSphere
Extensible
SPML, SCIM, SAML, SSH, Telnet, TN3270, HTTP(S), SQL, LDAP,
ODBC, CSV, Python/web services
Hitachi ID Privileged Access Manager is part of the Hitachi
ID Identity and Access Management Suite, which also includes:
Identity Manager for governance and administration of identities
and entitlements and Password Manager for strong authentication,
federation and credential management.
For more information, please visit: http://hitachi-id.com/
or call: 1.403.233.0740 | 1.877.386.0372
2017 Hitachi ID Systems, Inc. All rights reserved.
All other marks, symbols and trademarks are the property of their respective owners.
You might also like
- An Executive Guide to Identity Access Management - 2nd EditionFrom EverandAn Executive Guide to Identity Access Management - 2nd EditionRating: 4 out of 5 stars4/5 (3)
- Microservices in SAP HANA XSA: A Guide to REST APIs Using Node.jsFrom EverandMicroservices in SAP HANA XSA: A Guide to REST APIs Using Node.jsNo ratings yet
- Hitachi Id Privileged Access ManagerDocument2 pagesHitachi Id Privileged Access ManagerHitachiIDNo ratings yet
- Hitachi ID Identity and Access Management SuiteDocument16 pagesHitachi ID Identity and Access Management SuiteHitachiIDNo ratings yet
- Core PAS-DS-Mar-2019-2Document2 pagesCore PAS-DS-Mar-2019-2Trinh Hoang LongNo ratings yet
- Sailpoint Predictive Identity PlatformDocument30 pagesSailpoint Predictive Identity PlatformPuja DevkanNo ratings yet
- Identity and Access Management Tutorial PDFDocument20 pagesIdentity and Access Management Tutorial PDFKrish krishNo ratings yet
- CyberArk Enterprise Password Vault 4-28-2014 enDocument2 pagesCyberArk Enterprise Password Vault 4-28-2014 enRitu RajNo ratings yet
- Hitachi ID Group ManagerDocument7 pagesHitachi ID Group ManagerHitachiIDNo ratings yet
- Privileged Access Security Data Sheet PDFDocument2 pagesPrivileged Access Security Data Sheet PDFDa ArchNo ratings yet
- Integrating Mtech Idm Suite With MiisDocument13 pagesIntegrating Mtech Idm Suite With MiisHitachiIDNo ratings yet
- PAM1Document19 pagesPAM1zareen.zehraNo ratings yet
- PIM Brochure Low ResDocument4 pagesPIM Brochure Low Resn_neethu11No ratings yet
- 1 Hitachi ID Privileged Access Manager: Temporary, Secure and Accountable Privilege ElevationDocument14 pages1 Hitachi ID Privileged Access Manager: Temporary, Secure and Accountable Privilege Elevationmadhav_maroNo ratings yet
- CyberArk Application Access Manager-DS-Mar-2019Document2 pagesCyberArk Application Access Manager-DS-Mar-2019Trinh Hoang LongNo ratings yet
- Cyber Security That’s Good for Your People and Your BusinessDocument2 pagesCyber Security That’s Good for Your People and Your BusinessSyed MoizNo ratings yet
- Symantec Privileged Access Management: Product BriefDocument3 pagesSymantec Privileged Access Management: Product BriefKo Ko AungNo ratings yet
- Company Profile: PT Mega Cyber SecurityDocument50 pagesCompany Profile: PT Mega Cyber SecurityYohannes AlumagubiNo ratings yet
- Hipam FeaturesDocument4 pagesHipam FeaturesHitachiIDNo ratings yet
- Password Manager Faq Network ArchitectsDocument9 pagesPassword Manager Faq Network ArchitectsHitachiIDNo ratings yet
- PAM DocumentationDocument8 pagesPAM DocumentationsidNo ratings yet
- Implementing SSO with Shared CredentialsDocument8 pagesImplementing SSO with Shared CredentialsPrasad KshirsagarNo ratings yet
- Password Manager: Detailed Presentation.Document27 pagesPassword Manager: Detailed Presentation.HitachiIDNo ratings yet
- Thycotic Denver PresentationDocument41 pagesThycotic Denver PresentationuakarsuNo ratings yet
- Active Directory Security Audit ChecklistDocument7 pagesActive Directory Security Audit ChecklistVikas KorutlaNo ratings yet
- RHEL IDM Solution v1Document23 pagesRHEL IDM Solution v1raouyrNo ratings yet
- Ilantus Sign On Express Vs Softex OmnipassDocument8 pagesIlantus Sign On Express Vs Softex OmnipassrenokurianNo ratings yet
- Privileged Access Management: SecurityDocument13 pagesPrivileged Access Management: SecurityMohamedNo ratings yet
- Privileged Access Manager Faq GenericDocument8 pagesPrivileged Access Manager Faq GenericHitachiIDNo ratings yet
- Identity and Access Lifecycle AutomationDocument14 pagesIdentity and Access Lifecycle AutomationHitachiIDNo ratings yet
- Active Directory Based Single Sign Onfor SAPon UNIXand LinuxDocument2 pagesActive Directory Based Single Sign Onfor SAPon UNIXand LinuxAbdul GafoorNo ratings yet
- Management Access HandbookDocument20 pagesManagement Access HandbookCarla GonçalvesNo ratings yet
- cyberark dna邃 datasheetDocument2 pagescyberark dna邃 datasheetVeeru HosamaniNo ratings yet
- IAM DeveloperDocument5 pagesIAM Developerabhay.rajauriya1No ratings yet
- Hitachi ID Privileged Access Manager: Randomize and Control Disclosure of Privileged PasswordsDocument14 pagesHitachi ID Privileged Access Manager: Randomize and Control Disclosure of Privileged PasswordsHitachiID100% (2)
- APM f5Document17 pagesAPM f5Rizky 'Kimun' Rachmanto PrastyoNo ratings yet
- OAuth 2Document16 pagesOAuth 2Kanth MuthyalaNo ratings yet
- Arka Inventory: Make Better Decisions With Data Driven Business InsightsDocument11 pagesArka Inventory: Make Better Decisions With Data Driven Business InsightsPrashant DixitNo ratings yet
- Arka Inventory: Make Better Decisions With Data Driven Business InsightsDocument11 pagesArka Inventory: Make Better Decisions With Data Driven Business InsightsPrashant DixitNo ratings yet
- Ds Discovery and Audit 11-17-2014 WebDocument2 pagesDs Discovery and Audit 11-17-2014 WebMedyDoankNo ratings yet
- Comparison of Operating System Security - Windows Vs Linux: Techno International New TownDocument10 pagesComparison of Operating System Security - Windows Vs Linux: Techno International New TownMinu ChoudharyNo ratings yet
- Pa 3Document7 pagesPa 3Bruno SolizNo ratings yet
- Ciam?: Extensibility - Scalability and Usability - Security - Privacy and ComplianceDocument2 pagesCiam?: Extensibility - Scalability and Usability - Security - Privacy and CompliancecarklounNo ratings yet
- KuppingerCole February 2022 Executive View_ Hitachi ID Bravura Security Fabric - IAM (Hitachi ID Licensed for Distribution)Document14 pagesKuppingerCole February 2022 Executive View_ Hitachi ID Bravura Security Fabric - IAM (Hitachi ID Licensed for Distribution)Riyas AbdulkhaderNo ratings yet
- IBM Privileged Identity ManagerDocument6 pagesIBM Privileged Identity ManagerMuhittin KetelogluNo ratings yet
- ARCON PAM BrochureDocument10 pagesARCON PAM BrochureEslam SaberNo ratings yet
- WatchDox HV On-Premise DeploymentDocument9 pagesWatchDox HV On-Premise DeploymentchesterljsNo ratings yet
- Sailpoint and Microsoft Collaborative IntegrationDocument6 pagesSailpoint and Microsoft Collaborative IntegrationDavid YoungNo ratings yet
- Secure Application Access HS5020 BrochureDocument5 pagesSecure Application Access HS5020 BrochureAjit Pratap KundanNo ratings yet
- Big Ip Access Policy Manager DsDocument17 pagesBig Ip Access Policy Manager Dskhalid anjumNo ratings yet
- Big Ip Access Policy Manager Ds PDFDocument17 pagesBig Ip Access Policy Manager Ds PDFAgus HerdiyanaNo ratings yet
- The Effortless And: Data Loss Prevention Insider Threat ProtectionDocument13 pagesThe Effortless And: Data Loss Prevention Insider Threat ProtectionMing LeNo ratings yet
- Sonika Reddy Sr. IAM Engineer SummaryDocument6 pagesSonika Reddy Sr. IAM Engineer SummaryvenkayNo ratings yet
- PAM in Most Reasonable Price in India.Document26 pagesPAM in Most Reasonable Price in India.Iraje SoftwareNo ratings yet
- Manage Passwords for Privileged SAP UserIDsDocument1 pageManage Passwords for Privileged SAP UserIDslaxmachada2843No ratings yet
- Fortisiem: Unified Event Correlation and Risk Management For Modern NetworksDocument7 pagesFortisiem: Unified Event Correlation and Risk Management For Modern Networksdhazh007No ratings yet
- Zero Trust - Fortem ITDocument53 pagesZero Trust - Fortem ITJayavignesh ZohoNo ratings yet
- PAM FeaturesDocument9 pagesPAM Featuresquyetpv144No ratings yet
- Defender Datasheet 69032Document2 pagesDefender Datasheet 69032Santhanamariyan TNo ratings yet
- Hitachi ID Password Manager: Lower Cost, Improve Service and Strengthen Security With Password Synchronization and ResetDocument14 pagesHitachi ID Password Manager: Lower Cost, Improve Service and Strengthen Security With Password Synchronization and ResetHitachiIDNo ratings yet
- Hitachi ID Password ManagerDocument27 pagesHitachi ID Password ManagerHitachiIDNo ratings yet
- Hitachi ID Password ManagerDocument17 pagesHitachi ID Password ManagerHitachiIDNo ratings yet
- Hitachi ID Access CertifierDocument2 pagesHitachi ID Access CertifierHitachiIDNo ratings yet
- Hitachi ID Identity ManagerDocument17 pagesHitachi ID Identity ManagerHitachiIDNo ratings yet
- Maximizing User Adoption With Hitachi ID Password ManagerDocument8 pagesMaximizing User Adoption With Hitachi ID Password ManagerHitachiIDNo ratings yet
- Hitachi ID Identity ManagerDocument4 pagesHitachi ID Identity ManagerHitachiIDNo ratings yet
- An Overview of Business Drivers and Technology SolutionsDocument6 pagesAn Overview of Business Drivers and Technology SolutionsHitachiIDNo ratings yet
- Hitachi ID Password ManagerDocument5 pagesHitachi ID Password ManagerHitachiIDNo ratings yet
- Authentication ManagementDocument6 pagesAuthentication ManagementHitachiIDNo ratings yet
- Hitachi ID Access CertifierDocument7 pagesHitachi ID Access CertifierHitachiIDNo ratings yet
- Hitachi ID Group ManagerDocument2 pagesHitachi ID Group ManagerHitachiIDNo ratings yet
- Hitachi ID Group ManagerDocument7 pagesHitachi ID Group ManagerHitachiIDNo ratings yet
- Hitachi ID Identity ManagerDocument20 pagesHitachi ID Identity ManagerHitachiIDNo ratings yet
- Building An Identity Management Business CaseDocument11 pagesBuilding An Identity Management Business CaseHitachiIDNo ratings yet
- Hitachi ID Identity and Access Management SuiteDocument10 pagesHitachi ID Identity and Access Management SuiteHitachiIDNo ratings yet
- Privileged Access ManagementDocument15 pagesPrivileged Access ManagementHitachiIDNo ratings yet
- Identity and Access Lifecycle AutomationDocument14 pagesIdentity and Access Lifecycle AutomationHitachiIDNo ratings yet
- Privileged Access ManagementDocument3 pagesPrivileged Access ManagementHitachiIDNo ratings yet
- Hitachi ID Access CertifierDocument7 pagesHitachi ID Access CertifierHitachiIDNo ratings yet
- Hitachi ID Password Manager BrochureDocument2 pagesHitachi ID Password Manager BrochureHitachiIDNo ratings yet
- Securing Embedded PasswordsDocument7 pagesSecuring Embedded PasswordsHitachiIDNo ratings yet
- Hitachi ID Identity Express™ - Corporate Edition BrochureDocument2 pagesHitachi ID Identity Express™ - Corporate Edition BrochureHitachiIDNo ratings yet
- 2015 Privileged Access Management StudyDocument26 pages2015 Privileged Access Management StudyHitachiIDNo ratings yet
- Hitachi ID Management Suite BrochureDocument2 pagesHitachi ID Management Suite BrochureHitachiIDNo ratings yet
- GLB - Gramm-Leach-Bliley ActDocument2 pagesGLB - Gramm-Leach-Bliley ActHitachiIDNo ratings yet
- Hitachi ID Identity Manager BrochureDocument2 pagesHitachi ID Identity Manager BrochureHitachiIDNo ratings yet
- NCR Corporation - Identity and Access Management - A Case StudyDocument2 pagesNCR Corporation - Identity and Access Management - A Case StudyHitachiIDNo ratings yet
- Simplifying Lotus Notes Id and Password ManagementDocument2 pagesSimplifying Lotus Notes Id and Password ManagementHitachiIDNo ratings yet
- Byte Ordering - Unit 2Document77 pagesByte Ordering - Unit 2Nipurn BhaalNo ratings yet
- ENSA 312-38 QuestionDocument90 pagesENSA 312-38 QuestionPhoneit PoloNo ratings yet
- Real Estate Management System Design DocumentDocument8 pagesReal Estate Management System Design DocumentjhateshkolipakulaNo ratings yet
- Computer Programming and Data StructuresDocument2 pagesComputer Programming and Data StructuresNarsim MudirajNo ratings yet
- Gateway Network PDFDocument10 pagesGateway Network PDFvijikesh ArunagiriNo ratings yet
- Inforbright IEE Architecture OverviewDocument14 pagesInforbright IEE Architecture Overviewpeterpan107No ratings yet
- Kadaster Inspire Geonovum 3mrt11Document20 pagesKadaster Inspire Geonovum 3mrt11AspirantNo ratings yet
- Darktrace Csensor Release NotesDocument10 pagesDarktrace Csensor Release NotesNelson JuniorNo ratings yet
- CSE06CSL47Document36 pagesCSE06CSL47jincyjosephNo ratings yet
- MP Lab Introduction to GEBUG ProgrammingDocument4 pagesMP Lab Introduction to GEBUG ProgrammingMamounNo ratings yet
- C4 CD: Networking With Windows 98 and Window NT: Rakesh RanjanDocument42 pagesC4 CD: Networking With Windows 98 and Window NT: Rakesh RanjansrdsosonpurNo ratings yet
- Computer System Structure PDFDocument24 pagesComputer System Structure PDFvidishsaNo ratings yet
- ADBMS Quiz 1 Key TermsDocument4 pagesADBMS Quiz 1 Key TermsJayson LucenaNo ratings yet
- MGW PingDocument7 pagesMGW PingAsif ShafiNo ratings yet
- PS Setup EMHub, EMAgents, ChangeAssistantDocument14 pagesPS Setup EMHub, EMAgents, ChangeAssistantMichel FrappierNo ratings yet
- (M8S1-POWERPOINT) - Advanced SQLDocument37 pages(M8S1-POWERPOINT) - Advanced SQLYael CabralesNo ratings yet
- What Is The 5G User Plane Function (UPF)Document6 pagesWhat Is The 5G User Plane Function (UPF)mlazar20009720No ratings yet
- Exploring Lakehouse 751615 NDXDocument32 pagesExploring Lakehouse 751615 NDXamir hayatNo ratings yet
- Manual InformixDocument962 pagesManual InformixIsabel ArdónNo ratings yet
- 8086 Unit-2Document85 pages8086 Unit-2Bala KrishnaNo ratings yet
- Manage AWS services from the terminal with the AWS CLIDocument2 pagesManage AWS services from the terminal with the AWS CLIOMRoutNo ratings yet
- Standard SAP ModulesDocument3 pagesStandard SAP ModulesP PapireddyNo ratings yet
- Legacy VS Apps Interface DesignDocument3 pagesLegacy VS Apps Interface DesignashibekNo ratings yet
- How To Estimate The Size of An RMAN Database Backup (Doc ID 1274720.1)Document2 pagesHow To Estimate The Size of An RMAN Database Backup (Doc ID 1274720.1)Jheyner López HurtadoNo ratings yet
- Pediatric Neonatal Dosage Handbook 19th EditionDocument3 pagesPediatric Neonatal Dosage Handbook 19th EditionHarry Febryanto25% (4)
- Insert - Update - Delete in GridviewDocument5 pagesInsert - Update - Delete in GridviewJemi MoradiyaNo ratings yet
- Classwork of Lab 2: 1. Create A New User, Naming sv2Document18 pagesClasswork of Lab 2: 1. Create A New User, Naming sv2Phú VinhNo ratings yet
- Types of Digital Data ClassificationDocument20 pagesTypes of Digital Data ClassificationTejus R SNo ratings yet
- AirN@v Installation and Consultation Guide V1.1Document30 pagesAirN@v Installation and Consultation Guide V1.1renjithaero86% (7)
- Extended Access-List Example On Cisco RouterDocument1 pageExtended Access-List Example On Cisco RouterSamuel HOUNGBEMENo ratings yet