Professional Documents
Culture Documents
Preventing File Inclusion Attacks On Website
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Preventing File Inclusion Attacks On Website
Copyright:
Available Formats
Preventing File Inclusion Attacks on Website
P.S.Sadaphule, Utkarsha Dhande, Priyanka Kamble, Sanika Mehre, Rashmi Savant
sadaphule.compdept@gmail.com, utkarshadhande13@gmail.com, piukamble1249@gmail.com, sanikamehre@gmail.com,
sawant.27.rashmi@gmail.com
Computer Engineering, AISSMS’s IOIT, Pune
Abstract — People use internet to communicate database , shell and other important confidential files of
with one another. Without internet, it would be both the site via front end web application.
more expensive and slower to maintain personal and
PHP is Hypertext Preprocessor; because of its
professional relationships. Many people use internet prevalent and easy to develop web application the
to enjoy themselves and to engage in personal vulnerabilities found in codding of website and also
interests. However, there are many security threats
because of careless use of functions in PHP language
people come across which may be viruses, worms, file web sites becomes unsecured. Better use of proper GUI
inclusion etc. So, to provide security to web
to communicate with clients in better way may cause to
applications and preventing root shell access and
build a better website.
admin passwords is the main challenge. In previous
survey, we have studied on security threats such as Most of the time website are altered by
remote file inclusion and local file inclusion. Also, we vulnerabilities like SQLi, LFI, RFI & XSS. In this survey
have mentioned different prevention techniques such we only focus on two main vulnerabilities which are LFI
as Digital Signature, File size verification, and RFI. Existence of vulnerabilities in web application
Sanitization of input and Dynamic allocation to represented if web application has some codes that will
prevent website attacks. In this paper we have dynamically refer to an external script .Where as LFI
implemented these techniques by using methods such attacks occurred when file is injected into site present
as MD5, SHA256. The expected outcome will be already in web application. The main purpose is to
achieved by using these methods, providing security exploit function to upload malware (backdoor shell) in
to the websites from RFI and LFI attacks. application.
Keywords- Local File Inclusion attacks, Prevent
vulnerability, Remote File Inclusion Attacks, Security
OBJECTIVE
The objective of this paper is to prevent the web
site from various malicious attacks of RFI & LFI by
using PHP language & CSS. Also preventing
information theft and to prevent content modification in
web site and hence building trust with the customers.
INTRODUCTION
Human beings relay on websites and web LITERATURE SURVEY
applications for most of the things and transactions. On
the other hand as the usage of the web application There are many of researches done on various
increases so as maintaining security to such applications web vulnerabilities which comes under Semantic URL,
become more complex but the important and essential Cross-Site scripting, Cross-Site Request forgery, etc.
aspect. Such applications are used frequently which This system comes under Semantic URL means such
produces high risk of getting affected by attackers ,by attacks involve a user modifying the URL discover mode
exploiting the vulnerabilities between them. to perform various actions which are not originally
planned to be handled by server[2]. Survey found
Vulnerabilities or weaknesses found in web site reviews on various vulnerabilities such as RFI, LFI,
causes loss of important data of website of an SQLi, Query string attacks[1][3][4][5][6].
organization which further can cost to an organization in
critical way and hence it may reduce or harm reputation Also, Studied various methods used for
of an organization. This kind of vulnerabilities provoke exploitation, testing areas and security method and tools
attacker to have an unauthorized access to the back end including different algorithms which are being
Volume: 3 Issue: 2 April - 2018 95
used[1][2][3].For preventing from the LFI attack also the paper to understand the importance of sanitization and
various vulnerabilities and methods of LFI attacks[4].For how it i used as a prevention method. AntiLFIer is used
studying more about RFI attack we have studied the RFI for prevention which allows access to only the trusted
botnet[8].To learn more about attackers perspective and file. Prevention method checks whether file is trust full
why attacker choose RFI type of vulnerability we have or not. This paper[5] done the different types of attacks
studied different types of exploits and learnt how the and analysis on such attacks are mentioned
attacker gains root shell access and admin passwords[7] .Vulnerability scan carried out in 2013 by semantic
website vulnerability assessment services found that 77
In paper [1] The reachers focuses on this paper LFI percent of site are vulnerable. Many organization are
based RFI and SQLi attacks ,then to prevent this attacks losing their reputation because of the vulnerabilities
confidential and sensitive data such that root user found in websites. In this paper concentrate on
,password ,SSH login credential are disclosed by the prevention methods performed after executing attack on
system. In this paper to learn different methods such that user's machine. This paper attack scenario o the known
get method and post method used for exploitation. This vulnerable websites WAckoPicko of three types of
paper introduces security features which developers attacks -SQL Injection stored XSS and Remote File
usually design data processing technology through HTTP Inclusion. In this application has 10 vulnerability
POST method. Different files which are stored in accessible without authentication. In forensics expertise
different directories for security purpose. For system there are mail three phases acquisition, analysis,
security also studied different methods which are apply presentation. The purpose of the system in this paper [6]
for exploitation and security. LFI and RFI attacks system is to detect and prevent against malicious attacks over
concentrated on it. LFI is web application attack which the developers Website written in programming
allow user to include different files located in web languages like PHP,ASP.net and ASP also, it creates
application on server machine. RFI is one of the attack in native language API through which transaction and
website by remotely handled and access any type of user interactions are sent to IDS server through inter server
machine. The paper [2] mainly studied for various communication mechanism. IDS server developed from
testing strategies and types of testing. Also focuses on PHPPIDS. Base of PHPIDS is PHP intrusion detection
the knowledge of the technique pen testing on website, system which is mean to be used as server site tool. In
discusses the different phases ,in this attack victims and this paper to detect and prevents attacks such that SQLi
upgrades software tools to make the penetration test. ,LFI,RFI and XSS types of attacks. By using WAPT
Pentesting means a safety test with a specific objective algorithm to analyze the attacks is done with the help of
for evaluating systems. Its the set of safety test with this to record the activities of website and examine the
detector objective, after achieving the goal ID is suspicious behavior. Hacker constantly attacks on
terminated. This paper refer for different types of website so in this paper [7] field study which is
security entities such that authentication, authorization, presented on the attacker perspective is looking over real
integrity and availability. Also in common attacks which exploits used by hackers to attack website .SQL
are used such as semantic URL, cross site scripting, injection and remote file inclusion are two most
HTTP request counterfeited and attacks through the frequently used attacking techniques by hacker because
database. From this system understood that RFI and LFI attacker prefer easier techniques than complicated. Root
attacks comes under semantic URL method. The paper shell and the admin password are the main aim of
[3] protects the front end web applications from attacker to obtain the this entity because its easily attack
unauthorized access. Website front end and database is on website. website exploits may be simple as a specially
back end it can be accessible through web browser. crafted URL or as complex as an automated program
Vulnerability scanner is used for front end. This paper with hundreds of lines of code that can be executed and
focuses on design of web application , detection and completed .This paper field analyses the attacks of six
prevention of attacks which are RFI ,query string attacks widely used and well known web applications like PHP-
,cross site scripting attacks and union attacks. It Nuke, drupal, PHP-fusion, wordpress php MyAdmin and
overcomes by applying different algorithms such as phpBB. The paper [8] covered attacking methods like a
longest sub sequence algorithm and brute force string Remote File Inclusion, Cross Site Scripting and code
matching algorithm. The aim is to develop a web Inclusion. The ethics of attack or attackers are RFI .In
application-bot admin and user credentials ASP.net and botnet RFI attacks involved and the attacker are web
system also refer how to provide website authentication. promised. Domain name, content and dynamic IP
This paper [4] mainly focuses on LFI vulnerability. The address by using this vulnerable web sites are done.
local file access is done by manipulating the user IP. LFI Attacker are hosted the hoster which is the host that have
attack are null byte poisoning, log poisoning, malicious web server or FTP server by using some tools .In this
image upload, self file in linux environment and paper to highlight the RFI attacks which include another
alternate log poisoning .In this paper system understand internet site or directories in the same hard drive ,this is
the LFI Vulnerability is prevented from root cost analyze big advantage for the coder and it neglect result which
source code and defeat attack sanitization. From this
Volume: 3 Issue: 2 April - 2018 96
can be in successful attack point and compromising of included the attacker can get access to the remote
the host. servers.
PROPOSED METHODOLOGY This kind of attack can be avoided/prevented by not
making the use of any arbitrary input data in the file
include request or simply disable the allow_url_include
LFI is an inclusion attack ,where attacker exploit the
from the php ini file on the php running server.
functionalities which dynamically includes the scripts
This attack can be very destructive and can create alots
and the files. The LFI attacks takes place/happens when
of complications.
the attacker gets the path to the file which is to be
included as the input .This local file is allowed to put in
Steps for Vulnerable site:
the ‘include’ statement/request. The result of this LFI
attack incorporates Directory Traversal and Information
Step-1: Site on which attacker tries to attack:
Disclosure.Following is the example which is
In this stage, Security is not provided to the site.User is
vulnerable to LFI: free to access the site.
Step 2:Attacker gets shell access:
$file = $_GET[‘file’]; When the user tries to get access on this site he is able
include(‘directory/’,.$file); to get root shell access over server.
Step-3: Security of website get compromised:
Suppose we have the URL as: As no security is provided security of website gets
http://localhost/file.php?command=xyz.php instead of compromised and attacker has control over all the
xyz.php we can enter any of the file name we want. confidential information.
So here if we want any file content we can change it as:
http://localhost/file.php?command=../../apache/conf/http Steps for Secured site:
d.conf
Similarly we can retrive the content of any file on file Step-1:Attacker tries on site which is secured by
security API :
system.
This is the site on which our security API works.
When attacker tries to attack on the site, the code
One mitigation for LFI is simply change the settings in gets verified.
php.ini file, uncomment it and set as follows:
open_basedir =c:\\xamp\\htdocs, ,and save the Step-2:Attackers URl/code gets verified:
configuration, which means if anyone want to access
the file usin the include() method, it checks the location In this stage, all the prevention techniques are used
to verify the user`s URL/code.
of the file, the php refuses to access the file ,as it is
a) Dynamic Allocation Prevention method
present outside the specified directory-tree. The Every page has entry stored in theHash table. In
application can create a whitelist of files which can be Dynamic allocation method; these entries get
included in order to avoid the the inclusion of file by matched with the page which is dynamically
attacker. entered. If both the entries get matched, user is
allowed to procced .Else access denied for the
RFI is Remote File Inclusion . The Php running user. This is the simplest kind of prevention
method.
websites, are often vulnerable to the RFI type of attack.
b) Sanitization of Input Prevention Method
The attacker can include a file remotely through a script Validation checks if the input meets a set of
on Web Server. The possibility of this attack can be criteria. In Sanitization, it modifies the input to
due to the user input without any proper validation. ensure that it is valid. So, in this method the
contents are getting filtered and only the
The attacker can contrivance the application to execute Sanitized code will be executed. This method is
most promising as it allows only the non-
a malicious code which the attacker can upload on the
vulnerable code to be executed ignoring all the
web servers ,it can be through webshell. The attack can vulnerabilities of it.
be done by the use of the user supplied input without c) Digital Signature Prevention Method
any proper validations .Once the webshell is being A Digital Signature is a mathematical scheme
for validating the authenticity of Digital
message or document. In Digital Signature
Volume: 3 Issue: 2 April - 2018 97
,every page entered into hash table has provided
an unique ID. If ID gets matched the user is
allowed to proceed.
d) File size verification Prevention Method
File size verification is a process of using an
algorithm for verifying the integrity of file. In
File size verification the input of file size is
compared , this can be done by comparing two
files bit by bit. But the only problem with this
method is, once in a while the file size can be
matched though there are least chances of it. If
we put the file size in bytes then there will be
less chances of getting matched with the same
file size.
Step-3: System`s Actions after Verifying code :
Here, the system takes an action after verifying the
code. User get access to website if he is valid user.If the
user is not valid user`s IP address will be blocked for
next 24 hours.
Step-4 : User IP Add blocked forever :
Even after 24 hours user tries to gain access site and if
it is invalid and vulnerable code then it is considered as
the User is an attacker and purposefully he is trying to
attack the site. Here in this case the Attackers IP
address will be blocked forever
SYSTEM ARCHITECTURE
This architecture consists of mainly two Figure 1. Intrusion Detection and Prevention Architecture
scenarios, the first scenario shows how exactly attack is
performed by attacker. The second scenario shows, how
system response when attacker tries to attack , and how it
prevent from attacks by implementing prevention
methods and what actions will be taken on attacker.
In second scenario, it is shown how the system
The below architecture shows detailed working reacts when any user tries to access the particular site.
of proposed system. Firstly, it will check for the prevention methods. It will
compare the code or URL with each of the prevention
Basically there are two scenarios which method, if the data is non vulnerable, user is allowed to
explains the total working of the model. In first scenario, access the site. If the URL is vulnerable then the user is
Attacker tries to inject malicious code into the page not allowed to access the site as well as it might be
remotely. He might try to include the file or say code, considered as an attacker and alert message sent to
where the code is vulnerable. After finding such server site. So, the attacker`s IP address will be blocked
weakness from the page the attacker is free to attack on for 24hrs and the site will be secured. It might be
the site , if attacker tries to include .php file into such possible that the URL which we are considering
place he will be succeed to have control on the server as vulnerable is accidently put by the user. That’s why users
the PHP code compiled directly from the server. Such or we can say attackers IP has been blocked for 24hrs
kind of code is known as shell. In this scenario the only. But, if the user/attacker retries to put such
attacker gains shell access. incorrected URL it is considered that he is trying to put
malicious code on the site to harm the site or to gain
unauthorized control. So in this case, attackers IP is
blocked forever.
Volume: 3 Issue: 2 April - 2018 98
RESULTS
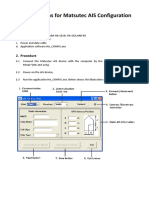
This is the initial configuration page.
Fig: System Initialization page Fig:Access denied page
This page contains the actual machanisam of blocking
and unblocking all the unwanted requests and all the
logs related to previous attacks.
CONCLUSION
In this paper, the purpose is to provide
prevention to website by various malware attacks. The
attacks performed using LFI and RFI techniques has
been prevented by this web application using different
prevention methods like Dynamic Allocation method,
Digital Signature method , verification of input and File
Size Allocation , which provides security to the web
site.
Fig: Dashboard
REFERENCES
[1 ] Afasana Begum and Md. Maruf Hassan,”RFI and
SQLi based Local File Inclusion Vulnerabilities in Web
Applications”,International Workshop on
Computational Intelligence(IWCI),12-13 Dec 2016.
This page will be displayed when particular request has [2] Rina Elizabeth Lopez De Jimenez,”Pentesting on
been blocked or IP address has been banned on the Web Applications using Ethical Hacking”,ITCA
server. FEPADE,La Libertad,30 June 2016.
[3]J.Jemmi Hazel and Dr. P.Valarmathie,”Guarding
Web Application with multi-angled attack
detection”,(ICSNS),25 Feb 2015.
[4] Mir Saman Tajbakhsh and Jamshid Bagherzadeh,”A
sound framework for Dynamic prevention of Local File
Inclusion ”, 7th International Conference on Information
and Knowledge Technology,2015.
[5]Natasa Suteva and Mario Loleski,”Computer
Forensic Analysis Of some Web
Attacks”,(WorldCIS),2014
Volume: 3 Issue: 2 April - 2018 99
[6]Mr.R.Priyadarshini and Mr.Jagadiswaree,”A Cross 21st International Symposium on Software Reliability
Platform Intrusion Detection System using Inter Server Engineering , 2010
Communication Technique”, IEEE-ICRTIT 2011 MIT,
Anna University, Chennai. June 3-5 2011 [8]Hugo F.Gonzalez and Robeldo,”Types of Hosts on
Remote File Inclusion (RFI)”, Electronics, Robotics and
[7]Jose Fonseca, Macro Vicira and Henrique Madeira, Automotive Mechanics Conference, 2008
”The Web Attacker Perspective-A Field Study”, IEEE
Volume: 3 Issue: 2 April - 2018 100
You might also like
- Application Security and Secure ProgrammingDocument81 pagesApplication Security and Secure ProgrammingSemi YuliantoNo ratings yet
- Unit-6 - Web Application SecurityDocument32 pagesUnit-6 - Web Application Securityyototi8935No ratings yet
- Hacker Intelligence Initiative, Monthly Trend Report #1Document3 pagesHacker Intelligence Initiative, Monthly Trend Report #1farah_nishuNo ratings yet
- API Security The Complete Guide To Threats, Methods ToolsDocument25 pagesAPI Security The Complete Guide To Threats, Methods Toolsjpaul42391No ratings yet
- Hacking Web ApplicationsDocument5 pagesHacking Web ApplicationsDeandryn RussellNo ratings yet
- Globally Recognized by Developers As The First Step Towards More Secure CodingDocument3 pagesGlobally Recognized by Developers As The First Step Towards More Secure CodingRicyNo ratings yet
- Web Security For Software TestingDocument6 pagesWeb Security For Software TestingguruannamalaiNo ratings yet
- Assignment On: Top 10 Owasp Vulnerability of WebDocument5 pagesAssignment On: Top 10 Owasp Vulnerability of Webdua khanNo ratings yet
- Paper - Akbar Rosyidi - 20220130008Document3 pagesPaper - Akbar Rosyidi - 20220130008AkbarRosyidiNo ratings yet
- Top Five Dangerous Security Risks Over Web ApplicationDocument3 pagesTop Five Dangerous Security Risks Over Web ApplicationInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- SSRN Id3315587Document5 pagesSSRN Id3315587arslan zulfiqarNo ratings yet
- InjectiomDocument2 pagesInjectiomAdu-Boahene ChristianNo ratings yet
- Application Security CloudDocument31 pagesApplication Security CloudM S Prasad100% (1)
- A Survey of Intelligent Detection Designs of HTML URL Phishing AttacksDocument23 pagesA Survey of Intelligent Detection Designs of HTML URL Phishing AttacksRajesh RNo ratings yet
- Cross-Site Request Forgery: Attack and Defense: Tatiana Alexenko Mark Jenne Suman Deb Roy Wenjun ZengDocument2 pagesCross-Site Request Forgery: Attack and Defense: Tatiana Alexenko Mark Jenne Suman Deb Roy Wenjun ZengMhackSahuNo ratings yet
- IETE-COE - PPT - Overview of Cybersecurity Threats, Vunerabilities and AttacksDocument33 pagesIETE-COE - PPT - Overview of Cybersecurity Threats, Vunerabilities and AttacksreshmiprNo ratings yet
- Web Application Pentest 101Document121 pagesWeb Application Pentest 101Azlan YatimNo ratings yet
- Chapter 1 and 2-1Document46 pagesChapter 1 and 2-1Tora SarkarNo ratings yet
- CSRF and XSS Attacks and Defense MechanismsDocument4 pagesCSRF and XSS Attacks and Defense MechanismsInternational Journal of Innovative Science and Research Technology100% (1)
- Web Application Security 101Document10 pagesWeb Application Security 101Laheb KareemNo ratings yet
- On Security Analysis of PHP Web Applications: David Hauzar and Jan Kofro NDocument6 pagesOn Security Analysis of PHP Web Applications: David Hauzar and Jan Kofro Nabdel_lakNo ratings yet
- Chapter 4 Application and OS SecurityDocument49 pagesChapter 4 Application and OS SecurityhaileNo ratings yet
- Research Report 92091Document8 pagesResearch Report 92091Honey DhaliwalNo ratings yet
- White Paper c11 740455Document3 pagesWhite Paper c11 740455rajatc2011No ratings yet
- Sad Lab All ExptDocument53 pagesSad Lab All ExptadtiiNo ratings yet
- Report On OWASP What Is OWASP?: Deep Nandu BED-C-48Document4 pagesReport On OWASP What Is OWASP?: Deep Nandu BED-C-48deep nanduNo ratings yet
- FALLSEM2022-23 CSE3501 ETH VL2022230103420 Reference Material I 05-09-2022 Lect 10Document24 pagesFALLSEM2022-23 CSE3501 ETH VL2022230103420 Reference Material I 05-09-2022 Lect 10Swastik BanerjeeNo ratings yet
- Application Security: Coding PracticesDocument3 pagesApplication Security: Coding PracticesSridhar PNo ratings yet
- API PentestingDocument27 pagesAPI Pentestingmrgodzilla00000000009No ratings yet
- Priyal Keharia Is Exp 5Document19 pagesPriyal Keharia Is Exp 5Priyal KehariaNo ratings yet
- Cybersecurity Best Practices For Python Web ApplicationsDocument25 pagesCybersecurity Best Practices For Python Web ApplicationsAbu RayhanNo ratings yet
- Website Defacement AttackDocument5 pagesWebsite Defacement AttackandrisurantiNo ratings yet
- Report For Foophones: by Utkarsh MunraDocument37 pagesReport For Foophones: by Utkarsh Munrasuraj fbNo ratings yet
- Web SecurityDocument1 pageWeb SecurityJohn MainaNo ratings yet
- Vulnerabilities in Web ApplicationsDocument6 pagesVulnerabilities in Web ApplicationswamalupiloNo ratings yet
- Exploiting Server Vulnerabilities With XSS and Server Side Scripting AttacksDocument21 pagesExploiting Server Vulnerabilities With XSS and Server Side Scripting AttacksMike Kennedy100% (1)
- CCS374 Web Application SecurityDocument18 pagesCCS374 Web Application Securitydhanush02010No ratings yet
- CSS Question BankDocument19 pagesCSS Question BankArun ChoudharyNo ratings yet
- CSE2 ResearchDocument25 pagesCSE2 ResearchDTCHAMENI WOKFA GREGORY ROMUALDNo ratings yet
- Types of VulnerabilitiesDocument5 pagesTypes of VulnerabilitiesNikhil NaikNo ratings yet
- Application SecurityDocument20 pagesApplication SecurityAwal MamaneNo ratings yet
- Chapter 4Document41 pagesChapter 4haileNo ratings yet
- XSS Vulnerability Assessment and Prevention in Web ApplicationDocument4 pagesXSS Vulnerability Assessment and Prevention in Web ApplicationSanaNo ratings yet
- Cyber Ops SummaryDocument5 pagesCyber Ops SummaryDominique EijansantosNo ratings yet
- Cyber Security !Document3 pagesCyber Security !kavya keerthiNo ratings yet
- The Appilication of Fuzzing in Web Software Security Vulnerabilities TestDocument4 pagesThe Appilication of Fuzzing in Web Software Security Vulnerabilities TestBangsa PEJUANGNo ratings yet
- Improving Web Application Vulnerability Detection Leveraging Ensemble FuzzingDocument9 pagesImproving Web Application Vulnerability Detection Leveraging Ensemble Fuzzingtaslim bangkinangNo ratings yet
- Security in HTML5 Name: Khalid Shaikh Roll No: 43: AbstractDocument9 pagesSecurity in HTML5 Name: Khalid Shaikh Roll No: 43: Abstractkhalid shaikhNo ratings yet
- Web Technologies and Cyber Security Literature ReviewDocument5 pagesWeb Technologies and Cyber Security Literature ReviewengineeringwatchNo ratings yet
- Secure Mobile DevelopmentDocument102 pagesSecure Mobile DevelopmentSukun2000No ratings yet
- My InternDocument22 pagesMy Internshiny DudduNo ratings yet
- Web Security: Vulnerability and Threats: Presented by Deepti PatoleDocument21 pagesWeb Security: Vulnerability and Threats: Presented by Deepti PatoleDeepti PatoleNo ratings yet
- 01 - Security EssentialsDocument34 pages01 - Security EssentialsMan ModiNo ratings yet
- ABSTRACTDocument2 pagesABSTRACTaminkhizer377No ratings yet
- Web Security TestingDocument11 pagesWeb Security TestingHritika RawatNo ratings yet
- 11-Access Control Structures, Firewalls.-06!05!2023Document27 pages11-Access Control Structures, Firewalls.-06!05!2023pritish.kheraNo ratings yet
- Threats and Vulnerability in Service Oriented ArchitectureDocument7 pagesThreats and Vulnerability in Service Oriented ArchitectureAman SaxenaNo ratings yet
- CSE-111-07-Unit5 UpdatedDocument37 pagesCSE-111-07-Unit5 UpdatedYogiNo ratings yet
- Web Application Vulnerabilities - The Hacker's TreasureDocument5 pagesWeb Application Vulnerabilities - The Hacker's TreasureBangsa PEJUANGNo ratings yet
- Password Security System and HoneywordsDocument6 pagesPassword Security System and HoneywordsInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Security Issue and Cryptography in Cloud ComputingDocument4 pagesSecurity Issue and Cryptography in Cloud ComputingInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- E-Learning Using Cloud Computing and ChallengesDocument6 pagesE-Learning Using Cloud Computing and ChallengesInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Survey On Automatic Spinal Cord Segmentation Using MR ImagesDocument6 pagesSurvey On Automatic Spinal Cord Segmentation Using MR ImagesInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Leukaemia Detection Using Image Processing TechniquesDocument5 pagesLeukaemia Detection Using Image Processing TechniquesInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Data Mining in Image Processing and It's ApplicationDocument5 pagesData Mining in Image Processing and It's ApplicationInternational Journal Of Emerging Technology and Computer Science100% (1)
- Effect of Entry Material and Machine Parameters On Drilling Process On PCB.Document10 pagesEffect of Entry Material and Machine Parameters On Drilling Process On PCB.International Journal Of Emerging Technology and Computer ScienceNo ratings yet
- 222 25 849 1 10 20181003 - 2 PDFDocument5 pages222 25 849 1 10 20181003 - 2 PDFInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Survey On Cloud Computing Platform For Ehealth SystemsDocument6 pagesSurvey On Cloud Computing Platform For Ehealth SystemsInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- 3D Solid Model Using Printing Technique Using Powder MetallurgyDocument7 pages3D Solid Model Using Printing Technique Using Powder MetallurgyInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Energy Minimization Using Binary To Ternary Conversion Along With ACODocument6 pagesEnergy Minimization Using Binary To Ternary Conversion Along With ACOInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Winning Prediction Analysis in One-Day-International (ODI) Cricket Using Machine Learning TechniquesDocument8 pagesWinning Prediction Analysis in One-Day-International (ODI) Cricket Using Machine Learning TechniquesInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Privacy Preserving Techniques in Data Stream and ChallengesDocument6 pagesPrivacy Preserving Techniques in Data Stream and ChallengesInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Distributed Image Processing Using Different Techniques in HadoopDocument7 pagesDistributed Image Processing Using Different Techniques in HadoopInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Dermatological Disease Detection Using Artificial Neural NetworksDocument4 pagesDermatological Disease Detection Using Artificial Neural NetworksInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- An Android Application To Shift Multimedia From Phone's Gallery Onto The CloudDocument4 pagesAn Android Application To Shift Multimedia From Phone's Gallery Onto The CloudInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Brain Tumor Detection Using Segmentation of MriDocument4 pagesBrain Tumor Detection Using Segmentation of MriInternational Journal Of Emerging Technology and Computer Science100% (1)
- Animate Object Detection Using Deep LearningDocument6 pagesAnimate Object Detection Using Deep LearningInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Novel Implementation of Hybrid Rootkit: 2. Algorithm 2.1 Reverse ConnectionDocument6 pagesNovel Implementation of Hybrid Rootkit: 2. Algorithm 2.1 Reverse ConnectionInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Stock Market Prediction Using Machine LearningDocument4 pagesStock Market Prediction Using Machine LearningInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Audio Visual Emotion Based Music PlayerDocument4 pagesAudio Visual Emotion Based Music PlayerInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Medical Information Storage and Retrieval System Using QR Code TechnologyDocument4 pagesMedical Information Storage and Retrieval System Using QR Code TechnologyInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Novel Implementation of Hybrid Rootkit: 2. Algorithm 2.1 Reverse ConnectionDocument6 pagesNovel Implementation of Hybrid Rootkit: 2. Algorithm 2.1 Reverse ConnectionInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Study of Social Image Re-Ranking According Inter and Intra User ImpactDocument4 pagesStudy of Social Image Re-Ranking According Inter and Intra User ImpactInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Securing Cloud Server Data Network From Evolving DDoS AttackDocument4 pagesSecuring Cloud Server Data Network From Evolving DDoS AttackInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Victimization of Road and Social Network Based On KNN.Document4 pagesVictimization of Road and Social Network Based On KNN.International Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Prevention of Cross Site Scripting (XSS) and Securing Web Application Atclient SideDocument4 pagesPrevention of Cross Site Scripting (XSS) and Securing Web Application Atclient SideInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Email Correlation and Analysis Using Pattern Matching TechniqueDocument3 pagesEmail Correlation and Analysis Using Pattern Matching TechniqueInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Data Compression Using Wireless Distributed ComputingDocument4 pagesData Compression Using Wireless Distributed ComputingInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- The Automated System For General Administration Using QR CodeDocument4 pagesThe Automated System For General Administration Using QR CodeInternational Journal Of Emerging Technology and Computer ScienceNo ratings yet
- Cybersecurity For AccountantsDocument3 pagesCybersecurity For Accountantskhushboosingh25junNo ratings yet
- 2-0114-16x-00 - Content Server Forms Design v16 - OTDocument144 pages2-0114-16x-00 - Content Server Forms Design v16 - OTOscar PerezNo ratings yet
- Notifier Battery Calculations-ReadmeDocument11 pagesNotifier Battery Calculations-Readmesajithrjn83No ratings yet
- HiPath 4000 V4, Section 1 - AMO Descriptions, Service Documentation, Issue 5Document3,154 pagesHiPath 4000 V4, Section 1 - AMO Descriptions, Service Documentation, Issue 5Orlando OliveiraNo ratings yet
- Ucm To Ucm Peer GuideDocument7 pagesUcm To Ucm Peer GuideEmilio I WildeNo ratings yet
- HA 102 ConfigManualDocument9 pagesHA 102 ConfigManualOlavo PastoreNo ratings yet
- Easy Setting Box UM EngDocument21 pagesEasy Setting Box UM EngStellaNo ratings yet
- AN153 StudDocument570 pagesAN153 StudpamukumarNo ratings yet
- Social Media Map 2019Document1 pageSocial Media Map 2019ahhgoksdgnokgnskgnskNo ratings yet
- Stop Google Chrome From Auto-UpdatesDocument5 pagesStop Google Chrome From Auto-UpdatesMarielRamosNo ratings yet
- Ronald Jackson SutantoDocument1 pageRonald Jackson SutantoRonald SutantoNo ratings yet
- The Big Cartoon Database: Jump To Navigation Jump To SearchDocument4 pagesThe Big Cartoon Database: Jump To Navigation Jump To SearchGanesha MoorthiNo ratings yet
- Scribus TutorialDocument60 pagesScribus Tutorialrichx790% (10)
- 1101.2 BlkDiag ClockLockDocument1 page1101.2 BlkDiag ClockLockAnonymous j5apk2AumNo ratings yet
- Cisco TMS Release Notes 15 9Document10 pagesCisco TMS Release Notes 15 9Valentin GRADINARUNo ratings yet
- بيولوجيا الخليةDocument11 pagesبيولوجيا الخليةHassan kandilNo ratings yet
- DocumentationDocument48 pagesDocumentationstchatzNo ratings yet
- CPK60DWS DriverGuideE V300Document16 pagesCPK60DWS DriverGuideE V300PaquitoNo ratings yet
- Hitachi 078fk Firmware Update Using The CK3: Let Us KnowDocument10 pagesHitachi 078fk Firmware Update Using The CK3: Let Us KnowAnibal MonschauNo ratings yet
- Offline License RequestDocument4 pagesOffline License RequestYusri RazakNo ratings yet
- Openfiler ConfigurationDocument16 pagesOpenfiler ConfigurationSayed MobinNo ratings yet
- Basic 7 - Computing - Emt 1 - Prof DukerDocument5 pagesBasic 7 - Computing - Emt 1 - Prof DukerEdd NoddNo ratings yet
- SS Experiment Love Camp (1976) BRRip 720p x264 (Dual Audio) (Italian + English) - Prisak (HKRG) .MKVDocument3 pagesSS Experiment Love Camp (1976) BRRip 720p x264 (Dual Audio) (Italian + English) - Prisak (HKRG) .MKVArsalanNo ratings yet
- Cascading Style SheetsDocument19 pagesCascading Style SheetsRuth Mac'OdoNo ratings yet
- Operating System Concepts (Linux) : Lab InstructorDocument29 pagesOperating System Concepts (Linux) : Lab InstructorMUHAMMAD ADNAN SALEEMNo ratings yet
- User Requirements Document: Loan Management SystemDocument7 pagesUser Requirements Document: Loan Management SystemtdurgaNo ratings yet
- Cyber Security Public TalkDocument29 pagesCyber Security Public TalkMD Aminul IslamNo ratings yet
- Content Server - Web Services - How To Use Search API With REST AuthenticationDocument7 pagesContent Server - Web Services - How To Use Search API With REST AuthenticationbouncehhNo ratings yet
- ChatGPT Money Machine 2024 - The Ultimate Chatbot Cheat Sheet to Go From Clueless Noob to Prompt Prodigy Fast! Complete AI Beginner’s Course to Catch the GPT Gold Rush Before It Leaves You BehindFrom EverandChatGPT Money Machine 2024 - The Ultimate Chatbot Cheat Sheet to Go From Clueless Noob to Prompt Prodigy Fast! Complete AI Beginner’s Course to Catch the GPT Gold Rush Before It Leaves You BehindNo ratings yet
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityFrom EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityRating: 5 out of 5 stars5/5 (1)
- ChatGPT Side Hustles 2024 - Unlock the Digital Goldmine and Get AI Working for You Fast with More Than 85 Side Hustle Ideas to Boost Passive Income, Create New Cash Flow, and Get Ahead of the CurveFrom EverandChatGPT Side Hustles 2024 - Unlock the Digital Goldmine and Get AI Working for You Fast with More Than 85 Side Hustle Ideas to Boost Passive Income, Create New Cash Flow, and Get Ahead of the CurveNo ratings yet
- Algorithms to Live By: The Computer Science of Human DecisionsFrom EverandAlgorithms to Live By: The Computer Science of Human DecisionsRating: 4.5 out of 5 stars4.5/5 (722)
- AI Superpowers: China, Silicon Valley, and the New World OrderFrom EverandAI Superpowers: China, Silicon Valley, and the New World OrderRating: 4.5 out of 5 stars4.5/5 (398)
- Cyber War: The Next Threat to National Security and What to Do About ItFrom EverandCyber War: The Next Threat to National Security and What to Do About ItRating: 3.5 out of 5 stars3.5/5 (66)
- Chaos Monkeys: Obscene Fortune and Random Failure in Silicon ValleyFrom EverandChaos Monkeys: Obscene Fortune and Random Failure in Silicon ValleyRating: 3.5 out of 5 stars3.5/5 (111)
- Generative AI: The Insights You Need from Harvard Business ReviewFrom EverandGenerative AI: The Insights You Need from Harvard Business ReviewRating: 4.5 out of 5 stars4.5/5 (2)
- Digital Gold: Bitcoin and the Inside Story of the Misfits and Millionaires Trying to Reinvent MoneyFrom EverandDigital Gold: Bitcoin and the Inside Story of the Misfits and Millionaires Trying to Reinvent MoneyRating: 4 out of 5 stars4/5 (51)
- Scary Smart: The Future of Artificial Intelligence and How You Can Save Our WorldFrom EverandScary Smart: The Future of Artificial Intelligence and How You Can Save Our WorldRating: 4.5 out of 5 stars4.5/5 (55)
- The Infinite Machine: How an Army of Crypto-Hackers Is Building the Next Internet with EthereumFrom EverandThe Infinite Machine: How an Army of Crypto-Hackers Is Building the Next Internet with EthereumRating: 3 out of 5 stars3/5 (12)
- ChatGPT Millionaire 2024 - Bot-Driven Side Hustles, Prompt Engineering Shortcut Secrets, and Automated Income Streams that Print Money While You Sleep. The Ultimate Beginner’s Guide for AI BusinessFrom EverandChatGPT Millionaire 2024 - Bot-Driven Side Hustles, Prompt Engineering Shortcut Secrets, and Automated Income Streams that Print Money While You Sleep. The Ultimate Beginner’s Guide for AI BusinessNo ratings yet
- The Things We Make: The Unknown History of Invention from Cathedrals to Soda CansFrom EverandThe Things We Make: The Unknown History of Invention from Cathedrals to Soda CansNo ratings yet
- The Intel Trinity: How Robert Noyce, Gordon Moore, and Andy Grove Built the World's Most Important CompanyFrom EverandThe Intel Trinity: How Robert Noyce, Gordon Moore, and Andy Grove Built the World's Most Important CompanyNo ratings yet
- Mini Farming: Self-Sufficiency on 1/4 AcreFrom EverandMini Farming: Self-Sufficiency on 1/4 AcreRating: 4 out of 5 stars4/5 (76)
- Reality+: Virtual Worlds and the Problems of PhilosophyFrom EverandReality+: Virtual Worlds and the Problems of PhilosophyRating: 4 out of 5 stars4/5 (24)
- The Master Algorithm: How the Quest for the Ultimate Learning Machine Will Remake Our WorldFrom EverandThe Master Algorithm: How the Quest for the Ultimate Learning Machine Will Remake Our WorldRating: 4.5 out of 5 stars4.5/5 (107)
- Chip War: The Quest to Dominate the World's Most Critical TechnologyFrom EverandChip War: The Quest to Dominate the World's Most Critical TechnologyRating: 4.5 out of 5 stars4.5/5 (227)
- The Internet Con: How to Seize the Means of ComputationFrom EverandThe Internet Con: How to Seize the Means of ComputationRating: 5 out of 5 stars5/5 (6)
- The Simulated Multiverse: An MIT Computer Scientist Explores Parallel Universes, The Simulation Hypothesis, Quantum Computing and the Mandela EffectFrom EverandThe Simulated Multiverse: An MIT Computer Scientist Explores Parallel Universes, The Simulation Hypothesis, Quantum Computing and the Mandela EffectRating: 4.5 out of 5 stars4.5/5 (20)