Professional Documents
Culture Documents
Lab 3
Uploaded by
Tomas Rodriguez RamirezOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Lab 3
Uploaded by
Tomas Rodriguez RamirezCopyright:
Available Formats
Lab ID: 9.9K1116A163.DHI2.
AAA Login Authentication and Exec
Authorization
Objective
Configure the router named Regional to work with the local database, and enable a password and line
authentication in order to provide Authentication, Authorization, and Accounting (AAA) services. In the
first task of this lab, you will use AAA to authenticate against the local database for the enable, line, and
local methods. In the second task, you will configure exec authorization against the local user database.
In the third task, you will configure the HQ router to authenticate against the Cisco Secure Access Control
System (ACS) database.
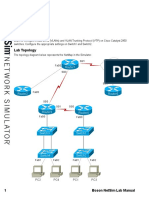
Lab Topology
The topology diagram below represents the NetMap in the Simulator. For this lab, your network design
includes two routers, HQ and Regional, which are connected by a serial link. Workstation, a PC, is
connected to a Fast Ethernet port on HQ, and a Terminal Access Controller Access Control System Plus
(TACACS+) server is connected to a Fast Ethernet port on Regional. Upon the initial loading of the lab, all
devices will be configured with the IP addresses and routing protocols needed for connectivity.
S0 S0
10.1.1.1 10.1.1.2
HQ Regional
DCE 10.1.1.0/30
Fa0/0 Fa0/0
192.168.1.1 192.168.2.1
192.168.1.0/24 192.168.2.0/24
E0 E0
192.168.1.2 192.168.2.254
Workstation ACS Server
Command Summary
Command Description
aaa authentication enable default enables AAA authentication to determine whether a user
method1 [method2…] can access privileged EXEC mode
aaa authentication login {default | list- enables AAA login
name} method1 [method2 …]
aaa authentication login default enable configures login authentication to use the enable
passwords
aaa authorization exec {default | list- configures exec authorization to use methods from the list
name} method1 [method2...]
1 Boson NetSim Lab Manual
Command Description
aaa new-model enables the AAA model
authorization exec [default | list-name] enables AAA authorization to determine whether a user can
access privileged EXEC mode
configure terminal enters global configuration mode from privileged EXEC
mode
enable enters privileged EXEC mode
enable password password sets the enable password
end ends and exits configuration mode
exit exits one level in the menu structure
line vty 0 4 enters configuration mode for virtual terminal (vty) lines
login authentication {default | list-name} enables login to a TACACS+ server
show running-config displays the active configuration file
tacacs-server host ip-address identifies the TACACS+ server
tacacs-server key shared-key identifies the password required to use the TACACS+
server for AAA
telnet ip-address starts the terminal emulation program from a PC, router,
or switch; permits you to access devices remotely over the
network
username name privilege privilege-level sets the privilege level for the user
password password
username name password password creates a local user name and password pair
Lab Tasks
Task 1: Configure Local Database Authentication by Using AAA
Unless otherwise instructed, perform the following steps on Regional1
1. Turn on AAA services.
2. In the local database, create a user with the user name regionaluser and password regionalpass.
3. Set the enable password to training.
4. Configure login authentication to use the enable password as the default method.
5. Log out of the router.
6. Access the router through the console port. Which password should you use here, and why? ____
______________________________________________________________________________
7. Create a login authentication method named local_authent, and set it to authenticate users against
the local database.
8. Apply local_authent to the vty lines.
2 Boson NetSim Lab Manual
9. From Workstation, telnet to Regional (10.1.1.2). How did Regional authenticate you when you used
Telnet to connect? _______________________________________________________________
10. Disconnect the Telnet session.
Task 2: Configure AAA Exec Authorization by Using the Local User Database
1. In the local database on Regional, create a user with the user name regionaladmin and password
adminpass. Assign privilege level 15 to this user.
2. Telnet from Workstation to Regional (10.1.1.2), and authenticate as user regionaladmin.
3. Which privilege level have you been placed at, and why? _________________________________
______________________________________________________________________________
4. Disconnect the Telnet session.
5. On Regional, create an exec authorization method named local_author. Configure authorization to
be performed against the local router’s database.
6. On Regional, apply local_author as an authorization method for the vty lines.
7. Telnet from Workstation to Regional (10.1.1.2), and authenticate as user regionaladmin.
8. Which privilege level have you been placed at, and why? _________________________________
______________________________________________________________________________
9. Disconnect the Telnet session.
Task 3: Configure the Router to Authenticate to the ACS Database
In this task, you will configure the HQ router to authenticate against the ACS database. ACS Server has
been preconfigured with the credentials listed in the table below:
Credential Value
TACACS+ server address 192.168.2.254
TACACS+ key boson
ACS user name cisco
ACS user password ciscopass
ACS user-specific enable password ciscoenable
Unless otherwise instructed, perform the following steps on HQ.
1. Log in to HQ as user hqadmin with the password hqpass.
2. On HQ, configure ACS Server’s IP address so the router can communicate and authenticate with the
server. TACACS+ communication should be authenticated by using the key boson and IP address
192.168.2.254.
3 Boson NetSim Lab Manual
3. Create a login authentication method named aaa_login, and configure it to authenticate against
ACS Server. You should configure the local user database to be the backup authentication method.
4. Create an exec authorization method named aaa_exec, and configure it to authorize exec sessions
against ACS Server. You should configure the local user database to be the backup authorization
method.
5. Apply the aaa_login and aaa_exec methods to the vty lines.
6. Configure enable authentication to use ACS Server for primary authentication and to use the local
enable password as a backup.
7. From Workstation, telnet to HQ (192.168.1.1). Log in by using the credentials listed in the table at
the beginning of the task.
8. What credentials did you use to log in to HQ, and why? __________________________________
______________________________________________________________________________
9. What credentials would you use if ACS Server failed? ___________________________________
10. From Workstation, enter privileged EXEC mode on HQ. Which password did you use to enter
privileged EXEC mode, and why? ___________________________________________________
______________________________________________________________________________
11. Disconnect the Telnet session.
12. Can multiple enable passwords exist on a router? _______________________________________
13. Log back in to the HQ router.
Once you have completed this lab, be sure to check your work by using the grading function.
You can do so by clicking the Grade Lab icon ( ) in the toolbar or by pressing Ctrl+G.
4 Boson NetSim Lab Manual
Lab Solutions
Task 1: Configure Local Database Authentication by Using AAA
1. On Regional, you should issue the following command to turn on AAA services:
Regional(config)#aaa new-model
2. On Regional, you should issue the following command to create the appropriate user in the local
database:
Regional(config)#username regionaluser password regionalpass
3. On Regional, you should issue the following command to set the enable password:
Regional(config)#enable password training
4. On Regional, you should issue the following command to configure login authentication to use the
enable password as the default method:
Regional(config)#aaa authentication login default enable
5. On Regional, you should issue the following commands to log out of the router:
Regional(config)#end
Regional#exit
6. On Regional, you should use the enable password to log in to the router.
Password:training
Regional>enable
Password:training
Regional#
When the default login authentication method is configured to use the enable password, the router
uses the enable password or the enable secret password as the login credential.
7. On Regional, you should issue the following command to create the appropriate login authentication
method and set it to authenticate users against the local database:
Regional(config)#aaa authentication login local_authent local
8. On Regional, you should issue the following commands to apply local_authent to the vty lines:
Regional(config)#line vty 0 4
Regional(config-line)#login authentication local_authent
5 Boson NetSim Lab Manual
9. From Workstation, issue the following command to telnet to Regional. Regional will now use the
local user database to authenticate Telnet sessions on the vty lines. You can log in as regionaluser
with the password regionalpass.
C:>telnet 10.1.1.2
Username:regionaluser
Password:regionalpass
Regional>
10. You should issue the following command to disconnect the Telnet session:
Regional>exit
[Connection to 10.1.1.2 closed by foreign host]
Task 2: Configure AAA Exec Authorization by Using the Local User Database
1. On Regional, use the enable password to log back in to the console. You should then issue the
following commands to create the appropriate user in the local user database and assign the correct
privilege level to the user:
Password:training
Regional>enable
Password:training
Regional#configure terminal
Regional(config)#username regionaladmin privilege 15 password adminpass
2. From Workstation, issue the following command to telnet to Regional; use regionaladmin as the
user name and adminpass as the password:
C:>telnet 10.1.1.2
Username:regionaladmin
Password:adminpass
Regional>
3. You have been placed at privilege level 1, which is user EXEC mode. Although you have
authenticated as regionaladmin, AAA is not configured to check the authorization level on the vty
lines. User EXEC mode is denoted by the following prompt:
Regional>
4. You should issue the following command to disconnect the Telnet session:
Regional>exit
[Connection to 10.1.1.2 closed by foreign host]
6 Boson NetSim Lab Manual
5. On Regional, use the enable password to log back in to the console. You should then issue the
following commands to create an exec authorization method that is performed against the local user
database:
Password:training
Regional>enable
Password:training
Regional#configure terminal
Regional(config)#aaa authorization exec local_author local
6. On Regional, you should issue the following commands to apply local_author to the vty lines:
Regional(config)#line vty 0 4
Regional(config-line)#authorization exec local_author
7. From Workstation, issue the following command to telnet to Regional; use regionaladmin as the
user name and adminpass as the password:
C:>telnet 10.1.1.2
Username:regionaladmin
Password:adminpass
Regional#
8. You have been placed at privilege level 15, which is privileged EXEC mode. After the local_author
method is applied to the vty lines, AAA will use the local database to check the authorization level as
well as authenticate the user. Privileged EXEC mode is denoted by the following prompt:
Regional#
9. You should issue the following command to disconnect the Telnet session:
Regional#exit
[Connection to 10.1.1.2 closed by foreign host]
Task 3: Configure the Router to Authenticate to the ACS Database
1. Log in to HQ by using the following user name and password:
Username:hqadmin
Password:hqpass
HQ>enable
HQ#configure terminal
2. On HQ, you should issue the following commands to configure the IP address of ACS Server and to
configure TACACS+ communications to authenticate by using the key boson:
HQ(config)#tacacs-server host 192.168.2.254
HQ(config)#tacacs-server key boson
7 Boson NetSim Lab Manual
3. On HQ, you should issue the following command to create a login authentication method that
authenticates against ACS Server first and to configure the local user database as a backup:
HQ(config)#aaa authentication login aaa_login group tacacs+ local
4. On HQ, you should issue the following command to create an exec authorization method that
authorizes exec sessions against ACS Server first and uses the local user database as a backup:
HQ(config)#aaa authorization exec aaa_exec group tacacs+ local
5. On HQ, you should issue the following commands to apply the aaa_login and aaa_exec methods to
the vty lines:
HQ(config)#line vty 0 4
HQ(config-line)#login authentication aaa_login
HQ(config-line)#authorization exec aaa_exec
6. On HQ, you should issue the following command to configure enable authentication to use ACS
Server first and to use the local enable password as a backup:
HQ(config)#aaa authentication enable default group tacacs+ enable
7. From Workstation, issue the following command to telnet to HQ. Log in with the user name cisco
and password ciscopass. The vty lines are configured to use the aaa_login and aaa_exec
methods to authenticate and authorize users, respectively. Both methods obtain credentials primarily
by communicating with ACS Server.
C:>telnet 192.168.1.1
Username:cisco
Password:ciscopass
HQ>
8. You had to use a user name of cisco and a password of ciscopass to log in to HQ because these
are the credentials configured on the ACS server.
9. If the ACS server failed, you would use the backup method configured in aaa_login. The backup in
this case is the local user database. You would use the user name hqadmin and password hqpass
to log in to HQ from Workstation.Below is an example of the login steps using the backup method;
you do not need to issue these commands in this lab.
C:>telnet 192.168.1.1
Username:hqadmin
Password:hqpass
HQ>
8 Boson NetSim Lab Manual
10. From within the Telnet session from Workstation to HQ, issue the enable command and then
the password ciscoenable to enter privileged EXEC mode on HQ. In step 6, you should have
configured AAA to communicate primarily with ACS Server to authenticate access to privileged
EXEC mode. On ACS Server, the enable password is ciscoenable for the user name cisco.
HQ>enable
Password:ciscoenable
11. You should issue the following command to exit the Telnet session:
HQ#exit
[Connection to 192.168.1.1 closed by foreign host]
12. Yes, multiple enable passwords can exist on a router.
13. To log back in to the HQ router, you should issue the following commands:
Username:hqadmin
Password:hqpass
HQ>enable
Username:cisco
Password:ciscoenable
HQ#
9 Boson NetSim Lab Manual
Sample Configuration Script
HQ HQ (continued)
HQ#show running-config interface FastEthernet0/1
Building configuration... no ip address
Current configuration : 1163 bytes no ip directed-broadcast
! !
Version 15.b router rip
service timestamps debug uptime network 10.0.0.0
service timestamps log uptime network 192.168.1.0
no service password-encryption !
! ip classless
hostname HQ no ip http server
aaa new-model !
! tacacs-server host 192.168.2.254
aaa authentication login default local tacacs-server key boson
aaa authentication login aaa_login group tacacs+ local !
aaa authentication enable default group tacacs+ enable line con 0
aaa authorization exec aaa_exec group tacacs+ local login local
! line aux 0
username hqadmin password hqpass line vty 0 4
! login authentication aaa_login
ip subnet-zero authorization exec aaa_exec
! !
ip cef no scheduler allocate
no ip domain-lookup end
!
interface Serial0/0/0
ip address 10.1.1.1 255.255.255.252
no ip directed-broadcast
clock rate 64000
!
interface Serial0/0/1
no ip address
no ip directed-broadcast
!
interface FastEthernet0/0
ip address 192.168.1.1 255.255.255.0
no ip directed-broadcast
!
Copyright © 1996–2017 Boson Software, LLC. All rights reserved. NetSim software and documentation are protected by copyright law.
10 Boson NetSim Lab Manual
You might also like
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (120)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- Ab Initio FAQ's Part1Document61 pagesAb Initio FAQ's Part1Yogesh Singh83% (6)
- CIS Cisco IOS 15 Benchmark v4.0.0Document151 pagesCIS Cisco IOS 15 Benchmark v4.0.0Sandro MeloNo ratings yet
- Lantronix Modbus Protocol UsersGuideDocument28 pagesLantronix Modbus Protocol UsersGuideJose Luis Castro AguilarNo ratings yet
- IP Access Lists: Objective Lab TopologyDocument5 pagesIP Access Lists: Objective Lab TopologyTomas Rodriguez RamirezNo ratings yet
- Lab 9Document16 pagesLab 9Tomas Rodriguez RamirezNo ratings yet
- Lab 3Document5 pagesLab 3Tomas Rodriguez RamirezNo ratings yet
- Dgii F 606 02600930602 201905Document1 pageDgii F 606 02600930602 201905Tomas Rodriguez RamirezNo ratings yet
- Lab 1Document11 pagesLab 1Tomas Rodriguez RamirezNo ratings yet
- MikroTik Routers and Wireless - Products - hAP Ac Lite TCDocument7 pagesMikroTik Routers and Wireless - Products - hAP Ac Lite TCTomas Rodriguez RamirezNo ratings yet
- Lab 6 PDFDocument8 pagesLab 6 PDFTomas Rodriguez RamirezNo ratings yet
- Lab 4Document6 pagesLab 4Tomas Rodriguez RamirezNo ratings yet
- Lab 7Document8 pagesLab 7Tomas Rodriguez RamirezNo ratings yet
- Lab 1Document10 pagesLab 1Tomas Rodriguez RamirezNo ratings yet
- Lab 2Document13 pagesLab 2Tomas Rodriguez RamirezNo ratings yet
- Lab 5Document12 pagesLab 5Tomas Rodriguez RamirezNo ratings yet
- OSPF Authentication II: Objective Lab TopologyDocument9 pagesOSPF Authentication II: Objective Lab TopologyTomas Rodriguez RamirezNo ratings yet
- Lab 1Document19 pagesLab 1Tomas Rodriguez RamirezNo ratings yet
- Lab 3Document16 pagesLab 3Tomas Rodriguez RamirezNo ratings yet
- Lab 4Document8 pagesLab 4Tomas Rodriguez RamirezNo ratings yet
- Lab 1Document5 pagesLab 1Tomas Rodriguez RamirezNo ratings yet
- Lab 2Document9 pagesLab 2Tomas Rodriguez RamirezNo ratings yet
- Lab 3Document16 pagesLab 3Tomas Rodriguez RamirezNo ratings yet
- Lab 8Document6 pagesLab 8Tomas Rodriguez RamirezNo ratings yet
- Lab 7Document10 pagesLab 7Tomas Rodriguez RamirezNo ratings yet
- Lab 3Document4 pagesLab 3Tomas Rodriguez RamirezNo ratings yet
- Lab 4Document8 pagesLab 4Tomas Rodriguez RamirezNo ratings yet
- Lab 5Document13 pagesLab 5Tomas Rodriguez RamirezNo ratings yet
- Lab 4Document14 pagesLab 4Tomas Rodriguez RamirezNo ratings yet
- Lab 2Document11 pagesLab 2Tomas Rodriguez RamirezNo ratings yet
- Disponible en JM Datasheet Tester CCTV IpDocument2 pagesDisponible en JM Datasheet Tester CCTV IpTomas Rodriguez RamirezNo ratings yet
- Lab 1Document11 pagesLab 1Tomas Rodriguez RamirezNo ratings yet
- Ace TroubleshootingDocument182 pagesAce TroubleshootingjtfoleyNo ratings yet
- FirewallsDocument31 pagesFirewallsNaveena KarakambadiNo ratings yet
- Click To Download PDFDocument53 pagesClick To Download PDFlacusclyne87No ratings yet
- AX Series Advanced Traffic Manager: Installation Guide For The AX 1030 / AX 3030Document18 pagesAX Series Advanced Traffic Manager: Installation Guide For The AX 1030 / AX 3030stephen virmwareNo ratings yet
- Cisco IOS Quick Reference Cheat Sheet 2.1Document5 pagesCisco IOS Quick Reference Cheat Sheet 2.1Raja Sekar MNo ratings yet
- Enabling Remote Access To The: Cisco Application Control Engine Module Administration Guide OL-9373-01Document28 pagesEnabling Remote Access To The: Cisco Application Control Engine Module Administration Guide OL-9373-01Ganesh NagarajanNo ratings yet
- SNMP Gateway ENDocument2 pagesSNMP Gateway ENThai TranNo ratings yet
- Unix:: Sdif - S Rlogin Telnet SSH User@Remoteserver CTRL + D Id Whoami Who Finger (1) Finger (1) - SDocument4 pagesUnix:: Sdif - S Rlogin Telnet SSH User@Remoteserver CTRL + D Id Whoami Who Finger (1) Finger (1) - Sovidiu0702No ratings yet
- Lab 3.1 Configuring SDM On A RouterDocument34 pagesLab 3.1 Configuring SDM On A Routergargamel_220No ratings yet
- Cisco Certkey 200-301 v2021-04-05 by - Harvey 273qDocument366 pagesCisco Certkey 200-301 v2021-04-05 by - Harvey 273qjoseNo ratings yet
- MegaMon TelnetDocument21 pagesMegaMon TelnetRusdiantoMahmud100% (1)
- Configuration Guide - Basic Configuration (V200R002C00 - 02)Document238 pagesConfiguration Guide - Basic Configuration (V200R002C00 - 02)Stephanie TannerNo ratings yet
- Internet NewDocument134 pagesInternet NewshantanurilNo ratings yet
- 9.3.8 Lab - Exploring NmapDocument6 pages9.3.8 Lab - Exploring NmapSven NosbroNo ratings yet
- Del NetDocument27 pagesDel NetHirak GhoshNo ratings yet
- Networking Q&ADocument46 pagesNetworking Q&AK Ravi KumarNo ratings yet
- Chapter 2 - Securing Network DevicesDocument5 pagesChapter 2 - Securing Network DevicesDesmond Calini0% (1)
- IqeyeDocument190 pagesIqeyeSebastien JoekelNo ratings yet
- Template Config Tdm-Ip Acx1000 MLMT 19092019-V1Document336 pagesTemplate Config Tdm-Ip Acx1000 MLMT 19092019-V1lamvan tuNo ratings yet
- VH2402S Configuration GuideDocument116 pagesVH2402S Configuration GuidealmanisNo ratings yet
- OpenBSD Proxy ServerDocument24 pagesOpenBSD Proxy ServerdrummerrNo ratings yet
- Skills Assessment - Student Training: (Answer Key)Document18 pagesSkills Assessment - Student Training: (Answer Key)xo4yxaNo ratings yet
- Sal Supported ProductsDocument11 pagesSal Supported ProductssandeepNo ratings yet
- FMUX04E ManualDocument64 pagesFMUX04E Manualwilmerpatricio22No ratings yet
- NPL Viva QuestionsDocument5 pagesNPL Viva QuestionsSainath ParkarNo ratings yet
- Bullet LTE - Brochure.rev.1.1Document2 pagesBullet LTE - Brochure.rev.1.1Frensel PetronaNo ratings yet
- Fortiadc 5.0.0 Cli Reference PDFDocument446 pagesFortiadc 5.0.0 Cli Reference PDFAyanNo ratings yet
- UNOS On GNS3 Through Qemu: StepsDocument5 pagesUNOS On GNS3 Through Qemu: StepsYogeshwar Sharma 219467No ratings yet