Professional Documents
Culture Documents
Exchange 2010 Network Port Reference
Uploaded by
nagarajs50Original Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Exchange 2010 Network Port Reference
Uploaded by
nagarajs50Copyright:
Available Formats
Exchange Network Port Reference: Exchange 2010 Help
Page 1 of 17
Exchange Network Port Reference
Applies to: Exchange Server 2010 SP2 Topic Last Modified: 2011-04-28 This topic provides information about ports, authentication, and encryption for all data paths used by Microsoft Exchange Server 2010. The Notes sections following each table clarify or define non-standard authentication or encryption methods.
Transport Servers
Exchange 2010 includes two server roles that perform message transport functionality: Hub Transport server and Edge Transport server. The following table provides information about ports, authentication, and encryption for data paths between these transport servers and other Exchange 2010 servers and services.
Transport server data paths
Default Supported Encryption authentication authentication supported? Yes, using Transport Layer Security (TLS) Encrypted by default?
Data path
Required ports
Hub Transport server to Hub Transport server
25/TCP (SMTP)
Kerberos
Kerberos
Yes
Hub Transport server to Edge Transport server Edge Transport server to Hub Transport server Edge Transport server to Edge Transport server
25/TCP (SMTP)
Direct trust
Direct trust
Yes, using TLS
Yes
25/TCP (SMTP)
Direct trust
Direct trust
Yes, using TLS
Yes
25/TCP SMTP
Anonymous, Certificate
Anonymous, Certificate
Yes, using TLS
Yes
Mailbox server to Hub Transport server via the 135/TCP (RPC) Microsoft Exchange Mail Submission Service
NTLM. If the Hub Transport and the Mailbox Yes, using server roles are NTLM/Kerberos RPC on the same encryption server, Kerberos is used.
Yes
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 2 of 17
Hub Transport to Mailbox server via 135/TCP (RPC) MAPI
NTLM. If the Hub Transport and the Mailbox Yes, using server roles are NTLM/Kerberos RPC on the same encryption server, Kerberos is used.
Yes
Unified Messaging server to Hub 25/TCP (SMTP) Transport server Microsoft Exchange EdgeSync service from Hub 50636/TCP (SSL) Transport server to Edge Transport server
Kerberos
Kerberos
Yes, using TLS
Yes
Basic
Basic
Yes, using LDAP over SSL (LDAPS)
Yes
Active Directory access from Hub Transport server
389/TCP/UDP (LDAP), 3268/TCP (LDAP GC), 88/TCP/UDP (Kerberos), Kerberos 53/TCP/UDP (DNS), 135/TCP (RPC netlogon)
Kerberos
Yes, using Kerberos encryption
Yes
Active Directory Rights Management 443/TCP (HTTPS) Services (AD RMS) access from Hub Transport server SMTP clients to Hub Transport 587 (SMTP) server (for example, end25/TCP (SMTP) users using Windows Live Mail)
NTLM/Kerberos NTLM/Kerberos
Yes, using SSL
Yes*
NTLM/Kerberos NTLM/Kerberos
Yes, using TLS
Yes
Notes on Transport Servers
All traffic between Hub Transport servers is encrypted by using TLS with self-signed certificates that are installed by Exchange 2010 Setup. Note: In Exchange 2010, TLS can be disabled on Hub Transport servers for internal SMTP communication with other Hub Transport servers in the same Exchange organization. We don't recommend doing this unless absolutely required. For more information, see 1 Disabling TLS Between Active Directory Sites to Support WAN Optimization .
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 3 of 17
All traffic between Edge Transport servers and Hub Transport servers is authenticated and encrypted. Mutual TLS is the underlying mechanism for authentication and encryption. Instead of using X.509 validation, Exchange 2010 uses direct trust to authenticate the certificates. Direct trust means that the presence of the certificate in Active Directory or Active Directory Lightweight Directory Services (AD LDS) acts as validation for the certificate. Active Directory is considered a trusted storage mechanism. When direct trust is used, it doesn't matter if the certificate is self-signed or signed by a certification authority (CA). When you subscribe an Edge Transport server to the Exchange organization, the Edge Subscription publishes the Edge Transport server certificate in Active Directory for the Hub Transport servers to validate. The Microsoft Exchange EdgeSync service updates AD LDS with the set of Hub Transport server certificates for the Edge Transport server to validate. EdgeSync uses a secure LDAP connection from the Hub Transport server to subscribed Edge Transport servers over TCP 50636. AD LDS also listens on TCP 50389. Connections to this port don't use SSL. You can use LDAP utilities to connect to the port and check AD LDS data. By default, traffic between Edge Transport servers in two different organizations is encrypted. Exchange 2010 Setup creates a self-signed certificate, and TLS is enabled by default. This allows any sending system to encrypt the inbound SMTP session to Exchange. By default, Exchange 2010 also tries TLS for all remote connections. Authentication methods for traffic between Hub Transport servers and Mailbox servers differ when the Hub Transport server roles and Mailbox server roles are installed on the same computer. When mail submission is local, Kerberos authentication is used. When mail submission is remote, NTLM authentication is used. Exchange 2010 also supports Domain Security. Domain Security refers to the functionality in Exchange 2010 and Microsoft Outlook 2010 that provides a low-cost alternative to S/MIME or other message-level over-the-Internet, security solutions. Domain Security provides you with a way to manage secure message paths between domains over the Internet. After these secure message paths are configured, messages that have successfully traveled over the secure path from an authenticated sender are displayed to Outlook and Outlook Web Access users as "Domain Secured". For more information, see Understanding Domain Security2. Many agents can run on Hub Transport servers and Edge Transport servers. Generally, antispam agents rely on information that's local to the computer on which the agents run. Therefore, little communication with remote computers is required. Recipient filtering is the exception. Recipient filtering requires calls to either AD LDS or Active Directory. As a best practice, run recipient filtering on the Edge Transport server. In this case, the AD LDS directory is on the same computer as the Edge Transport server and no remote communication is required. When recipient filtering has been installed and configured on the Hub Transport server, recipient filtering accesses Active Directory. The Protocol Analysis agent is used by the Sender Reputation feature in Exchange 2010. This agent also makes various connections to outside proxy servers to determine inbound message paths for suspect connections. All other anti-spam functionality uses data gathered, stored, and accessed only on the local computer. Frequently, the data, such as safelist aggregation or recipient data for recipient filtering, is pushed to the local AD LDS directory by using the Microsoft Exchange EdgeSync service. Information Rights Management (IRM) agents on Hub Transport servers make connections to Active Directory Rights Management Services (AD RMS) servers in the organization. AD RMS is a Web service that's secured by using SSL as a best practice. Communication with AD RMS servers occurs by using HTTPS, and Kerberos or NTLM is used for authentication, depending on the AD RMS server configuration. Journal rules, transport rules, and message classifications are stored in Active Directory and accessed by the Journaling agent and the Transport Rules agent on Hub Transport servers.
Mailbox Servers
Whether NTLM or Kerberos authentication is used for Mailbox servers depends on the user or process context that the Exchange Business Logic layer consumer is running under. In this context, the consumer is any application or process that uses the Exchange Business Logic layer. As a result, many
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 4 of 17
entries in the Default Authentication column of the Mailbox server data paths table are listed as NTLM/Kerberos. The Exchange Business Logic layer is used to access and communicate with the Exchange store. The Exchange Business Logic layer is also called from the Exchange store to communicate with external applications and processes. If the Exchange Business Logic layer consumer is running as Local System, the authentication method is always Kerberos from the consumer to the Exchange store. Kerberos is used because the consumer must be authenticated by using the Local System computer account, and a two-way authenticated trust must exist. If the Exchange Business Logic layer consumer isn't running as Local System, the authentication method is NTLM. For example, NTLM is used when you run an Exchange Management Shell cmdlet that uses the Exchange Business Logic layer. The RPC traffic is always encrypted. The following table provides information about ports, authentication, and encryption for data paths to and from Mailbox servers.
Mailbox server data paths
Default Supported Encryption authentication authentication supported? Encrypted by default?
Data path
Required ports
Active Directory access
389/TCP/UDP (LDAP), 3268/TCP (LDAP GC), 88/TCP/UDP (Kerberos), 53/TCP/UDP (DNS), 135/TCP (RPC netlogon)
Kerberos
Kerberos
Yes, using Kerberos encryption
Yes
Admin remote access (Remote Registry) Admin remote access (SMB/File) Availability Web service (Client Access to Mailbox)
135/TCP (RPC)
NTLM/Kerberos NTLM/Kerberos
Yes, using IPsec
No
445/TCP (SMB)
NTLM/Kerberos NTLM/Kerberos
Yes, using IPsec
No
135/TCP (RPC)
Yes, using NTLM/Kerberos NTLM/Kerberos RPC encryption
Yes
Clustering
135/TCP (RPC) See Notes on Mailbox Servers after this table.
NTLM/Kerberos NTLM/Kerberos
Yes, using IPsec
No
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 5 of 17
Content indexing
135/TCP (RPC)
Yes, using NTLM/Kerberos NTLM/Kerberos RPC encryption NTLM/Kerberos NTLM/Kerberos Yes NTLM/Kerberos NTLM/Kerberos Yes
Yes
Log shipping 64327 (customizable) Seeding 64327 (customizable)
No No
Volume shadow copy Local Message Block (SMB) NTLM/Kerberos NTLM/Kerberos No service (VSS) backup Mailbox Assistants
No
135/TCP (RPC)
NTLM/Kerberos NTLM/Kerberos No
No
MAPI access
135/TCP (RPC)
Yes, using NTLM/Kerberos NTLM/Kerberos RPC encryption
Yes
Microsoft Exchange Active Directory Topology service access
135/TCP (RPC)
Yes, using NTLM/Kerberos NTLM/Kerberos RPC encryption
Yes
Microsoft Exchange System Attendant 135/TCP (RPC) service legacy access (Listen to requests) Microsoft Exchange System Attendant service legacy access to Active Directory Microsoft Exchange System Attendant service
NTLM/Kerberos NTLM/Kerberos No
No
389/TCP/UDP (LDAP), 3268/TCP (LDAP GC), 88/TCP/UDP (Kerberos), 53/TCP/UDP (DNS), 135/TCP (RPC netlogon)
Kerberos
Kerberos
Yes, using Kerberos encryption
Yes
135/TCP (RPC)
Yes, using NTLM/Kerberos NTLM/Kerberos RPC encryption
Yes
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 6 of 17
legacy access (As MAPI client) Offline address book (OAB) 135/TCP (RPC) accessing Active Directory Recipient Update Service RPC access
Kerberos
Kerberos
Yes, using RPC encryption
Yes
135/TCP (RPC)
Kerberos
Kerberos
Yes, using RPC encryption
Yes
Recipient update to Active Directory
389/TCP/UDP (LDAP), 3268/TCP (LDAP GC), 88/TCP/UDP (Kerberos), 53/TCP/UDP (DNS), 135/TCP (RPC netlogon)
Kerberos
Kerberos
Yes, using Kerberos encryption
Yes
Notes on Mailbox Servers
The Clustering data path listed in the preceding table uses dynamic RPC over TCP to communicate cluster status and activity between the different cluster nodes. The Cluster service (ClusSvc.exe) also uses UDP/3343 and randomly allocated high TCP ports to communicate between cluster nodes. For intra-node communications, cluster nodes communicate over User Datagram Protocol (UDP) port 3343. Each node in the cluster periodically exchanges sequenced, unicast UDP datagrams with every other node in the cluster. The purpose of this exchange is to determine whether all nodes are running correctly and to monitor the health of network links. Port 64327/TCP is the default port used for log shipping. Administrators can specify a different port for log shipping. For HTTP authentication where Negotiate is listed, Kerberos is tried first, and then NTLM.
Client Access Servers
Unless noted, client access technologies, such as Outlook Web App, POP3, or IMAP4, are described by the authentication and encryption from the client application to the Client Access server. The following table provides information about port, authentication, and encryption for data paths between Client Access servers and other servers and clients.
Client Access server data paths
Default Supported Encryption authentication authentication supported? Yes, using Kerberos encryption Encrypted by default?
Data path
Required ports
Active Directory access
389/TCP/UDP (LDAP), Kerberos 3268/TCP (LDAP GC), 88/TCP/UDP (Kerberos),
Kerberos
Yes
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 7 of 17
53/TCP/UDP (DNS), 135/TCP (RPC netlogon) Basic/Integrated Basic, Digest, Windows NTLM, 80/TCP, 443/TCP (SSL) authentication Negotiate (Negotiate) (Kerberos)
Autodiscover service
Yes, using HTTPS
Yes
Availability service 80/TCP, 443/TCP (SSL) NTLM/Kerberos NTLM, Kerberos
Yes, using HTTPS
Yes
Outlook accessing Yes, using 80/TCP, 443/TCP (SSL) NTLM/Kerberos NTLM/Kerberos OAB HTTPS Basic, Digest, Forms Based Authentication, Yes, using NTLM (v2 only), HTTPS Kerberos, Certificate Yes, using SSL, TLS Yes, using SSL, TLS
No
Forms Based Outlook Web App 80/TCP, 443/TCP (SSL) Authentication
Yes, using a selfsigned certificate
POP3
110/TCP (TLS), 995/TCP (SSL) 143/TCP (TLS), 993/TCP (SSL)
Basic, Kerberos Basic, Kerberos
Yes
IMAP4
Basic, Kerberos Basic, Kerberos
Yes
Outlook Anywhere (formerly known 80/TCP, 443/TCP (SSL) Basic as RPC over HTTP ) Exchange ActiveSync application
Basic or NTLM
Yes, using HTTPS
Yes
80/TCP, 443/TCP (SSL) Basic
Basic, Certificate
Yes, using HTTPS
Yes
Client Access 5060/TCP, 5061/TCP, server to Unified 5062/TCP, a dynamic Messaging server port
By IP address
By IP address
Yes, using Session Initiation Protocol (SIP) over TLS
Yes
Client Access Negotiate server to a (Kerberos with Mailbox server 80/TCP, 443/TCP (SSL) NTLM/Kerberos fallback to that is running an NTLM or earlier version of optionally Exchange Server Basic,)
Yes, using IPsec
No
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 8 of 17
POP/IMAP plain text Client Access server to Exchange 2010 Mailbox server Client Access server to Client Access server (Exchange ActiveSync) Client Access server to Client Access server (Outlook Web Access) Client Access server to Client Access server (Exchange Web Services) Client Access server to Client Access server (POP3) Client Access server to Client Access server (IMAP4)
RPC. See Notes on Client Access Servers.
Kerberos
Yes, using NTLM/Kerberos RPC encryption
Yes
80/TCP, 443/TCP (SSL) Kerberos
Kerberos, Certificate
Yes, using HTTPS
Yes, using a selfsigned certificate
80/TCP, 443/TCP (HTTPS)
Kerberos
Kerberos
Yes, using SSL
Yes
443/TCP (HTTPS)
Kerberos
Kerberos
Yes, using SSL
Yes
995 (SSL)
Basic
Basic
Yes, using SSL
Yes
993 (SSL)
Basic
Basic
Yes, using SSL
Yes
Office Communications Server access to Client Access server (when 5075-5077/TCP (IN), Office 5061/TCP (OUT) Communications Server and Outlook Web App integration is enabled) Note:
mTLS (Required)
mTLS (Required)
Yes, using SSL
Yes
Integrated Windows authentication (NTLM) isn't supported for POP3 or IMAP4 client connectivity. For more information, see the "Client Access Features" sections in Discontinued Features3.
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 9 of 17
Notes on Client Access Servers
In Exchange 2010, MAPI clients such as Microsoft Outlook connect to Client Access servers. The Client Access servers use many ports to communicate with Mailbox servers. With some exceptions, those ports are determined by the RPC service and aren't fixed. For HTTP authentication where Negotiate is listed, Kerberos is tried first, and then NTLM. When an Exchange 2010 Client Access server communicates with a Mailbox server running Exchange Server 2003, it's a best practice to use Kerberos and disable NTLM authentication and Basic authentication. Additionally, it's a best practice to configure Outlook Web App to use forms-based authentication with a trusted certificate. For Exchange ActiveSync clients to communicate through the Exchange 2010 Client Access server to the Exchange 2003 back-end server, Windows Integrated Authentication must be enabled on the Microsoft-ServerActiveSync virtual directory on the Exchange 2003 back-end server. To use Exchange System Manager on an Exchange 2003 server to manage authentication on an Exchange 2003 virtual directory, download and install the hot fix referenced in Microsoft Knowledge Base article 937031, Event ID 1036 is logged on an Exchange 2007 server that is running the CAS role when mobile devices connect to the Exchange 2007 server to access mailboxes on an Exchange 2003 back-end server4. Note: Although the Knowledge Base article is specific to Exchange 2007, it's also applicable to Exchange 2010. When a Client Access server proxies POP3 requests to another Client Access server, the communication occurs over port 995/TCP, regardless of whether the connecting client uses POP3 and requests TLS (on port 110/TCP) or connects on port 995/TCP using SSL. Similarly, for IMAP4 connections, port 993/TCP is used to proxy requests regardless of whether the connecting client uses IMAP4 and requests TLS (on port 443/TCP) or connects on port 995 using IMAP4 with SSL encryption
Unified Messaging Servers
IP gateways and IP PBXs support only certificate-based authentication that uses mutual TLS for encrypting SIP traffic and IP-based authentication for Session Initiation Protocol (SIP)/TCP connections. IP gateways don't support either NTLM or Kerberos authentication. Therefore, when you use IP-based authentication, the connecting IP address or addresses are used to provide authentication mechanism for unencrypted (TCP) connections. When IP-based authentication is used in Unified Messaging (UM), the UM server verifies that the IP address is allowed to connect. The IP address is configured on the IP gateway or IP PBX. IP gateways and IP PBXs support mutual TLS for encrypting SIP traffic. After you successfully import and export the required trusted certificates, the IP gateway or IP PBX will request a certificate from the UM server, and then it will request a certificate from the IP gateway or IP PBX. Exchanging the trusted certificate between the IP gateway or IP PBX and the UM server enables the IP gateway or IP PBX and UM server to communicate over an encrypted connection by using mutual TLS. The following table provides information about port, authentication, and encryption for data paths between UM servers and other servers.
Unified Messaging server data paths
Default Supported Encryption authentication authentication supported? Encrypted by default?
Data path
Required ports
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 10 of 17
Active Directory access
389/TCP/UDP (LDAP), 3268/TCP (LDAP GC), 88/TCP/UDP (Kerberos), 53/TCP/UDP (DNS), 135/TCP (RPC netlogon)
Kerberos
Kerberos
Yes, using Kerberos encryption
Yes
Unified Messaging Phone interaction (IP PBX/VoIP Gateway)
5060/TCP , 5065/TCP, 5067/TCP (unsecured), 5061/TCP, 5066/TCP, 5068/TCP (secured), a dynamic port from the range By IP address 16000-17000/TCP (control), dynamic UDP ports from the range 1024-65535/UDP (RTP) Integrated Windows authentication (Negotiate)
By IP address, MTLS
Yes, using SIP/TLS, SRTP
No
Unified Messaging Web Service Unified Messaging server to Client Access server
80/TCP, 443/TCP (SSL)
Basic, Digest, Yes, using NTLM, Negotiate SSL (Kerberos)
Yes
5075, 5076, 5077 (TCP)
Integrated Windows authentication (Negotiate)
Basic, Digest, Yes, using NTLM, Negotiate SSL (Kerberos)
Yes
Unified Messaging server to Dynamic RPC Client Access server (Play on Phone) Unified Messaging server to Hub Transport server Unified Messaging server to Mailbox server
NTLM/Kerberos
NTLM/Kerberos
Yes, using RPC encryption
Yes
25/TCP (TLS)
Kerberos
Kerberos
Yes, using TLS
Yes
135/TCP (RPC)
NTLM/Kerberos
NTLM/Kerberos
Yes, using RPC encryption
Yes
Notes on Unified Messaging Servers
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 11 of 17
When you create a UM IP gateway object in Active Directory, you must define the IP address of the physical IP gateway or IP PBX (Private Branch eXchange). When you define the IP address on the UM IP gateway object, the IP address is added to a list of valid IP gateways or IP PBXs (also called SIP peers) that the UM server is allowed to communicate with. When you create the UM IP gateway, you can associate it with a UM dial plan. Associating the UM IP gateway with a dial plan allows the Unified Messaging servers that are associated with the dial plan to use IP-based authentication to communicate with the IP gateway. If the UM IP gateway has not been created or it isn't configured to use the correct IP address, authentication fails and the UM servers don't accept connections from that IP gateway's IP address. Also, when you implement mutual TLS and IP gateway or IP PBX and UM servers, the UM IP gateway must be configured to use the FQDN. After you configure the UM IP gateway with an FQDN, you must also add a host record to the DNS forward lookup zone for the UM IP gateway. In Exchange 2010, a UM server can either communicate on port 5060/TCP (unsecured) or on port 5061/TCP (secured), and can be configured to use both. For more information, see Understanding Unified Messaging VoIP Security and Understanding 6 Protocols, Ports, and Services in Unified Messaging .
5
Windows Firewall Rules Created by Exchange 2010 Setup
Windows Firewall with Advanced Security is a stateful, host-based firewall that filters inbound and outbound traffic based on firewall rules. Exchange 2010 Setup creates Windows Firewall rules to open the ports required for server and client communication on each server role. Therefore, you no longer need to use the Security Configuration Wizard (SCW) to configure these settings. To learn more about 7 Windows Firewall with Advanced Security, see Windows Firewall with Advanced Security and IPsec . This table lists the Windows Firewall rules created by Exchange Setup, including the ports opened on each server role. You can view these rules using the Windows Firewall with Advanced Security MMC snap-in. Rule name Server roles Port Program
MSExchangeADTopology - RPC (TCP-In)
Client Access, Hub Dynamic Transport, Bin\MSExchangeADTopologyService.exe RPC Mailbox, Unified Messaging Client Access, Hub Transport, Dynamic Bin\Microsoft.Exchange.Management.Monitoring.exe Edge RPC Transport, Unified Messaging Dynamic Bin\Microsoft.Exchange.ServiceHost.exe RPC
MSExchangeMonitoring - RPC (TCP-In)
MSExchangeServiceHost - RPC (TCP-In)
All roles
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 12 of 17
MSExchangeServiceHost RPCEPMap (TCP-In) MSExchangeRPCEPMap (GFW) (TCP-In)
All roles
RPCEPMap RPCEPMap
Bin\Microsoft.Exchange.Service.Host
All roles
Any
MSExchangeRPC (GFW) (TCPIn)
Client Access, Hub Dynamic Transport, Any RPC Mailbox, Unified Messaging 143, 993 (TCP) 143, 993 (TCP) 110, 995 (TCP) 110, 995 (TCP) 5075, 5076, 5077 (TCP) 5075, 5076, 5077 (TCP)
MSExchange - IMAP4 (GFW) (TCP-In)
Client Access
All
MSExchangeIMAP4 (TCP-In)
Client Access
ClientAccess\PopImap\Microsoft.Exchange.Imap4Service.exe
MSExchange - POP3 (FGW) (TCP-In)
Client Access
All
MSExchange - POP3 (TCP-In)
Client Access
ClientAccess\PopImap\Microsoft.Exchange.Pop3Service.exe
MSExchange - OWA (GFW) (TCP Client -In) Access
All
MSExchangeOWAAppPool (TCP- Client In) Access
Inetsrv\w3wp.exe
MSExchangeAB-RPC (TCP-In)
Client Access
Dynamic Bin\Microsoft.Exchange.AddressBook.Service.exe RPC RPCEPMap
MSExchangeAB-RPCEPMap (TCP Client -In) Access
Bin\Microsoft.Exchange.AddressBook.Service.exe
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 13 of 17
MSExchangeAB-RpcHttp (TCPIn)
Client Access
6002, 6004 (TCP)
Bin\Microsoft.Exchange.AddressBook.Service.exe
RpcHttpLBS (TCP-In)
Client Access
Dynamic System32\Svchost.exe RPC
Client MSExchangeRPC - RPC (TCP-In) Access, Mailbox Client Access, Mailbox Client Access, Mailbox Client Access Client Access
Dynamic Bing\Microsoft.Exchange.RpcClientAccess.Service.exe RPC
MSExchangeRPC - PRCEPMap (TCP-In)
RPCEPMap
Bing\Microsoft.Exchange.RpcClientAccess.Service.exe
MSExchangeRPC (TCP-In)
6001 (TCP)
Bing\Microsoft.Exchange.RpcClientAccess.Service.exe
MSExchangeMailboxReplication (GFW) (TCP-In) MSExchangeMailboxReplication (TCP-In)
808 (TCP) 808 (TCP)
Any
Bin\MSExchangeMailboxReplication.exe
MSExchangeIS - RPC (TCP-In)
Mailbox
Dynamic Bin\Store.exe RPC RPCEPMap 6001, 6002, 6003, 6004 (TCP) 6001 (TCP)
MSExchangeIS RPCEPMap (TCPMailbox In)
Bin\Store.exe
MSExchangeIS (GFW) (TCP-In) Mailbox
Any
MSExchangeIS (TCP-In)
Mailbox
Bin\Store.exe
MSExchangeMailboxAssistants Mailbox RPC (TCP-In) MSExchangeMailboxAssistants Mailbox RPCEPMap (TCP-In)
Dynamic Bin\MSExchangeMailboxAssistants.exe RPC RPCEPMap
Bin\MSExchangeMailboxAssistants.exe
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 14 of 17
MSExchangeMailSubmission RPC (TCP-In) MSExchangeMailSubmission RPCEPMap (TCP-In) MSExchangeMigration - RPC (TCP-In) MSExchangeMigration RPCEPMap (TCP-In) MSExchangerepl - Log Copier (TCP-In)
Mailbox
Dynamic Bin\MSExchangeMailSubmission.exe RPC RPCEPMap
Mailbox
Bin\MSExchangeMailSubmission.exe
Mailbox
Dynamic Bin\MSExchangeMigration.exe RPC RPCEPMap 64327 (TCP)
Mailbox
Bin\MSExchangeMigration.exe
Mailbox
Bin\MSExchangeRepl.exe
MSExchangerepl - RPC (TCP-In) Mailbox
Dynamic Bin\MSExchangeRepl.exe RPC RPCEPMap
MSExchangerepl - RPC-EPMap (TCP-In)
Mailbox
Bin\MSExchangeRepl.exe
MSExchangeSearch - RPC (TCPMailbox In) MSExchangeThrottling - RPC (TCP-In) MSExchangeThrottling RPCEPMap (TCP-In)
Dynamic Bin\Microsoft.Exchange.Search.ExSearch.exe RPC Dynamic Bin\MSExchangeThrottling.exe RPC RPCEPMap
Mailbox
Mailbox
Bin\MSExchangeThrottling.exe
MSFTED - RPC (TCP-In)
Mailbox
Dynamic Bin\MSFTED.exe RPC RPCEPMap
MSFTED - RPCEPMap (TCP-In)
Mailbox
Bin\MSFTED.exe
MSExchangeEdgeSync - RPC (TCP-In) MSExchangeEdgeSync RPCEPMap (TCP-In) MSExchangeTransportWorker RPC (TCP-In)
Hub Dynamic Bin\Microsoft.Exchange.EdgeSyncSvc.exe Transport RPC Hub RPCTransport EPMap
Bin\Microsoft.Exchange.EdgeSyncSvc.exe
Hub Dynamic Bin\edgetransport.exe Transport RPC
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 15 of 17
MSExchangeTransportWorker RPCEPMap (TCP-In) MSExchangeTransportWorker (GFW) (TCP-In) MSExchangeTransportWorker (TCP-In)
Hub RPCTransport EPMap
Bin\edgetransport.exe
Hub 25, 587 Any Transport (TCP) Hub 25, 587 Bin\edgetransport.exe Transport (TCP)
Hub Transport, MSExchangeTransportLogSearch Dynamic Bin\MSExchangeTransportLogSearch.exe Edge - RPC (TCP-In) RPC Transport, Mailbox Hub Transport, MSExchangeTransportLogSearch RPCEdge - RPCEPMap (TCP-In) EPMap Transport, Mailbox Unified Any Messaging Unified Any Messaging Unified 5060, Messaging 5061 Unified 5060, Messaging 5061
Bin\MSExchangeTransportLogSearch.exe
SESWorker (GFW) (TCP-In)
Any
SESWorker (TCP-In)
UnifiedMessaging\SESWorker.exe
UMService (GFW) (TCP-In)
Any
UMService (TCP-In)
Bin\UMService.exe
5065, UMWorkerProcess (GFW) (TCP- Unified 5066, In) Messaging 5067, 5068 5065, Unified 5066, Messaging 5067, 5068
Any
UMWorkerProcess (TCP-In)
Bin\UMWorkerProcess.exe
UMWorkerProcess - RPC (TCPIn)
Unified Dynamic Bin\UMWorkerProcess.exe Messaging RPC
Notes on Windows Firewall Rules Created by Exchange 2010 Setup
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 16 of 17
On servers that have Internet Information Services (IIS) installed, Windows opens the HTTP (port 80, TCP) and HTTPS (port 443, TCP) ports. Exchange 2010 Setup doesn't open these ports. Therefore, these ports don't appear in the preceding table. On Windows Server 2008 and Windows Server 2008 R2, Windows Firewall with Advanced Security allows you to specify the process or service for which a port is opened. This is more secure because it restricts usage of the port to the process or service specified in the rule. Exchange Setup creates firewall rules with the process name specified. In some cases, an additional rule that isn't restricted to the process is also created for compatibility purposes. You can disable or remove the rules that aren't restricted to the processes and keep the corresponding rules restricted to processes if your deployment supports them. The rules not restricted to processes are distinguished by the word (GFW) in the rule name. A number of Exchange services use remote procedure calls (RPCs) for communication. Server processes that use RPCs contact the RPC Endpoint Mapper to receive dynamic endpoints and register those endpoints in the Endpoint Mapper database. RPC clients contact the RPC Endpoint Mapper to determine the endpoints used by the server process. By default, the RPC Endpoint Mapper listens on port 135 (TCP). When configuring the Windows Firewall for a process that uses RPCs, Exchange 2010 Setup creates two firewall rules for the process. One rule allows communication with the RPC Endpoint Mapper, and the other rule allows communication with the dynamically assigned endpoint. To learn more about RPCs, see How 8 RPC Works . For more information about creating Windows Firewall rules for dynamic RPC, see 9 Allowing Inbound Network Traffic that Uses Dynamic RPC . Note: You can't modify the Windows Firewall rules created by Exchange 2010 Setup. You can create custom rules based on them, and then disable or delete them. For more information, see Microsoft Knowledge Base article 179442, How to configure a firewall for 10 domains and trusts .
Links Table
1 2 3 4 5 6 7 8 9
http://technet.microsoft.com/en-us/library/ee633456.aspx http://technet.microsoft.com/en-us/library/bb124392.aspx http://technet.microsoft.com/en-us/library/aa998911.aspx http://go.microsoft.com/fwlink/?linkid=3052&kbid=937031 http://technet.microsoft.com/en-us/library/bb124092.aspx http://technet.microsoft.com/en-us/library/aa998265.aspx http://go.microsoft.com/fwlink/?LinkId=179177 http://go.microsoft.com/fwlink/?LinkId=69495 http://go.microsoft.com/fwlink/?LinkId=168278 http://go.microsoft.com/fwlink/?linkid=3052&kbid=179442
10
Community Content
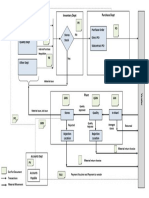
Network Ports Diagram Edit
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
Exchange Network Port Reference: Exchange 2010 Help
Page 17 of 17
Some time ago I've created a network diagram; the diagram is available in PDF and Visio format. http://eightwone.com/2011/04/05/exchange-2010-sp1-network-ports-diagram-v03/
11/1/2011 Michel de Rooij
2012 Microsoft. All rights reserved.
http://technet.microsoft.com/en-us/library/bb331973(d=printer).aspx
1/5/2012
You might also like
- The Telecom Handbook - Jane LainoDocument348 pagesThe Telecom Handbook - Jane LainoVarsha1003No ratings yet
- 3CX Phone System Manual V12.5Document96 pages3CX Phone System Manual V12.5Sergio Andres Amado NavarroNo ratings yet
- Sample - VAL004 Req For Val Plans Protocols 7 Mar 06Document3 pagesSample - VAL004 Req For Val Plans Protocols 7 Mar 06nagarajs50No ratings yet
- AIX 5L System Administration Student BookDocument815 pagesAIX 5L System Administration Student Bookic3man16No ratings yet
- Hanuman BahukDocument44 pagesHanuman BahukRaj Kumar M67% (3)
- 2015 VMP TemplateDocument10 pages2015 VMP Templatekulbhushan singh100% (2)
- FDA Guideline CSVDocument66 pagesFDA Guideline CSVnagarajs50100% (2)
- Secure Communication Channels: Secure Sockets Layer (SSL)Document5 pagesSecure Communication Channels: Secure Sockets Layer (SSL)Mani ShankarNo ratings yet
- Karthaveeryarjuna Mantra SadhanaDocument22 pagesKarthaveeryarjuna Mantra SadhanaKambhampati Sandilya67% (9)
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerFrom EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerNo ratings yet
- SSL and TLS: Privacy & IntegrityDocument4 pagesSSL and TLS: Privacy & IntegrityVishesh TripathiNo ratings yet
- Exchange Hybrid Deployment and Office 365 MigrationDocument25 pagesExchange Hybrid Deployment and Office 365 Migrationtest100% (1)
- Hybrid Migration With Exchange and Office 365Document38 pagesHybrid Migration With Exchange and Office 365apj500No ratings yet
- FTTH DesignguideDocument52 pagesFTTH Designguideanadigupta100% (1)
- WHO - Guideline Validation Computerized Systems-Appendix5 QAS16-667Document27 pagesWHO - Guideline Validation Computerized Systems-Appendix5 QAS16-667ppiccoliniNo ratings yet
- WHO - Guideline Validation Computerized Systems-Appendix5 QAS16-667Document27 pagesWHO - Guideline Validation Computerized Systems-Appendix5 QAS16-667ppiccoliniNo ratings yet
- Road Map For CSVDocument8 pagesRoad Map For CSVnagarajs50No ratings yet
- Road Map For CSVDocument8 pagesRoad Map For CSVnagarajs50No ratings yet
- Eil Telecom-CctvDocument22 pagesEil Telecom-CctvHriday AgarwalNo ratings yet
- Exchange Network Port ReferenceDocument15 pagesExchange Network Port ReferenceSukanta MukherjeeNo ratings yet
- Autodiscover MobDocument5 pagesAutodiscover MobHg HgNo ratings yet
- Exchange 2010 PosterDocument1 pageExchange 2010 PosterGautam SharmaNo ratings yet
- Exchange Port DocumentDocument7 pagesExchange Port DocumentKUMAR SHANTANUNo ratings yet
- Exchange ArchitectureDocument12 pagesExchange Architecture743737469No ratings yet
- ProtocolsDocument5 pagesProtocolsSakibul HassanNo ratings yet
- Exchange Server Architecture - Microsoft DocsDocument7 pagesExchange Server Architecture - Microsoft DocsHg HgNo ratings yet
- Evaluation of Some SMTP Testing, Email Verification, Header Analysis, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsFrom EverandEvaluation of Some SMTP Testing, Email Verification, Header Analysis, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsNo ratings yet
- SSL Tls HttpsDocument32 pagesSSL Tls HttpsShivansh PundirNo ratings yet
- Cisco Ironport and Exchange 2016Document10 pagesCisco Ironport and Exchange 2016shan1512No ratings yet
- The Design and Implementation of A SSL Proxy For Content SwitchDocument4 pagesThe Design and Implementation of A SSL Proxy For Content SwitchTania MitkovaNo ratings yet
- TLS Encryption Protocol ExplainedDocument2 pagesTLS Encryption Protocol ExplainedSalman ShahidNo ratings yet
- Exchange Security Best PracticesDocument4 pagesExchange Security Best PracticestousifaslamNo ratings yet
- Information Security Unit3Document6 pagesInformation Security Unit3anushk jainNo ratings yet
- Secure Socket Layer sec B.docDocument24 pagesSecure Socket Layer sec B.docGurdeep SidhuNo ratings yet
- Office 365 Mailflow TroubleshootingDocument7 pagesOffice 365 Mailflow TroubleshootingWilson DanielNo ratings yet
- Postfix SSL HowtoDocument6 pagesPostfix SSL Howtov1jayv1ctorNo ratings yet
- CCNA Resumen SinopticoDocument7 pagesCCNA Resumen SinopticoHeather MillerNo ratings yet
- TlsDocument18 pagesTlsasd666dsaNo ratings yet
- How SMTP DANE Works to Secure Email DeliveryDocument16 pagesHow SMTP DANE Works to Secure Email DeliverySebastianNo ratings yet
- WIA1005 Network Technology Foundation: Application Layer and Build A Small NetworkDocument33 pagesWIA1005 Network Technology Foundation: Application Layer and Build A Small NetworkAina NajihahNo ratings yet
- Pop3s & SMTPSDocument6 pagesPop3s & SMTPSKolawole OgundareNo ratings yet
- Pop3s & SMTPSDocument9 pagesPop3s & SMTPSKolawole OgundareNo ratings yet
- Exchange 2010 UnderstandDocument493 pagesExchange 2010 UnderstandSeKoFieNo ratings yet
- AutodiscoverDocument8 pagesAutodiscoverHg HgNo ratings yet
- ECE541 Data Networks 1: Application Layer Functionality and ProtocolsDocument27 pagesECE541 Data Networks 1: Application Layer Functionality and ProtocolsUnicorn54No ratings yet
- Wireless Ethical HackingDocument26 pagesWireless Ethical HackingGurdeep SidhuNo ratings yet
- Application Layer ProtocolsDocument33 pagesApplication Layer ProtocolsSarah AliNo ratings yet
- Evaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WP Email Tools: Evaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsFrom EverandEvaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WP Email Tools: Evaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsNo ratings yet
- Differences between SSL, TLS, TCP and UDP protocolsDocument10 pagesDifferences between SSL, TLS, TCP and UDP protocolsLILIAN KOMBANo ratings yet
- Server ConfigurationDocument12 pagesServer ConfigurationHaresh JiNo ratings yet
- Transport Layer SecurityDocument8 pagesTransport Layer Securityfawas hamdiNo ratings yet
- Self - Request - Stack: 2.3.2. Program StackingDocument9 pagesSelf - Request - Stack: 2.3.2. Program StackingSignia DiseñoNo ratings yet
- IGNOU BCA CS-69 Free Solved Assignment 2012Document9 pagesIGNOU BCA CS-69 Free Solved Assignment 2012anjworl3614No ratings yet
- ServersDocument4 pagesServersmirandasuryaprakash_No ratings yet
- Protocol Overview: NETBEUI, NetBIOS, TCP/IP, SMTP, POP3, IMAP, HTML, HTTP, HTTPS, SSL, Telnet, FTPDocument1 pageProtocol Overview: NETBEUI, NetBIOS, TCP/IP, SMTP, POP3, IMAP, HTML, HTTP, HTTPS, SSL, Telnet, FTPraul6075No ratings yet
- SSL - Secure Sockets LayerDocument12 pagesSSL - Secure Sockets LayerAli. RaoNo ratings yet
- Unit VIIDocument8 pagesUnit VIIabdul jawadNo ratings yet
- TLS/SSL Secures Data Transmission and AuthenticationDocument3 pagesTLS/SSL Secures Data Transmission and Authenticationfawas hamdiNo ratings yet
- Protecting Exchange 2010 WhitepaperDocument5 pagesProtecting Exchange 2010 WhitepaperjjosssNo ratings yet
- CNS CieDocument18 pagesCNS CieSyed Rahman AhmedNo ratings yet
- Telnet HTTP FTPDocument11 pagesTelnet HTTP FTPRohit VermaNo ratings yet
- Comprehensive Guide to Setting Up TLS on IronPort ESADocument5 pagesComprehensive Guide to Setting Up TLS on IronPort ESAsvinoth1981No ratings yet
- Application Layer Protocols in Computer Networks 17.01.2024Document8 pagesApplication Layer Protocols in Computer Networks 17.01.2024aloishp36No ratings yet
- Exchange 2016 ArchitectureDocument8 pagesExchange 2016 ArchitectureMario CelanoNo ratings yet
- SSL - Secure Sockets LayerDocument15 pagesSSL - Secure Sockets Layerhareem100No ratings yet
- Protocols Devices STDDocument18 pagesProtocols Devices STDRavi RoshanNo ratings yet
- CH 5Document91 pagesCH 5avantikabakshiNo ratings yet
- ITCNA - Chapter 6 - Supporting Network ServicesDocument52 pagesITCNA - Chapter 6 - Supporting Network ServicesLinda BurgNo ratings yet
- Transport Layer SecurityDocument36 pagesTransport Layer SecurityVinay KumarNo ratings yet
- Secure Shell (SSH) Protocol: Notes For Lecture-36 MCA 206: Advanced Computer NetworksDocument4 pagesSecure Shell (SSH) Protocol: Notes For Lecture-36 MCA 206: Advanced Computer NetworksVaibhav JainNo ratings yet
- Explain The Differences Between Secure Socket LayerDocument4 pagesExplain The Differences Between Secure Socket LayerLILIAN KOMBANo ratings yet
- Practical Issues With TLS Client CertificateDocument13 pagesPractical Issues With TLS Client Certificatelucassamuel_777No ratings yet
- Ex 2013 SP 1 ArchitectureDocument1 pageEx 2013 SP 1 ArchitectureArturoMartínezVásquezNo ratings yet
- iON Manufacturing BrochureDocument8 pagesiON Manufacturing Brochurenagarajs50No ratings yet
- Avaya Video ConferencingDocument4 pagesAvaya Video Conferencingnagarajs50No ratings yet
- ERP WorkFlowDocument1 pageERP WorkFlownagarajs50No ratings yet
- iON Manufacturing SolutionDocument6 pagesiON Manufacturing SolutionArmaan ChhaprooNo ratings yet
- IBM Lotus GuideDocument202 pagesIBM Lotus GuideLokesh VermaNo ratings yet
- Avascular NecrosisDocument13 pagesAvascular Necrosisnagarajs50No ratings yet
- CBSE Class 10 Sample Paper Marking Scheme 2018 - FIT-MSDocument8 pagesCBSE Class 10 Sample Paper Marking Scheme 2018 - FIT-MSKrishna Bharathi SNo ratings yet
- FMX CoDocument10 pagesFMX Conagarajs50No ratings yet
- 27 Pi 011 3 Recommendation On Computerised SystemsDocument54 pages27 Pi 011 3 Recommendation On Computerised SystemspedjaljubaNo ratings yet
- Avascular NecrosisDocument13 pagesAvascular Necrosisnagarajs50No ratings yet
- Avascular NecrosisDocument13 pagesAvascular Necrosisnagarajs50No ratings yet
- c7Document12 pagesc7eduardo acuniaNo ratings yet
- Guidelines On Validation - Appendix 5 2Document1 pageGuidelines On Validation - Appendix 5 2nagarajs50No ratings yet
- Annex 11Document5 pagesAnnex 11antonygamalpharmaNo ratings yet
- Guidance For Industry: Computerized Systems Used in Clinical InvestigationsDocument13 pagesGuidance For Industry: Computerized Systems Used in Clinical Investigationsx7w34TNo ratings yet
- Cisco CommandsDocument20 pagesCisco Commandsnagarajs50No ratings yet
- Jagannath TempleDocument3 pagesJagannath Templenagarajs50No ratings yet
- Making the Most of Your TimeDocument26 pagesMaking the Most of Your TimeAnnita ChaswalNo ratings yet
- Hytera MRT Solution Introduction PDFDocument76 pagesHytera MRT Solution Introduction PDFItamar ZimmermanNo ratings yet
- Managed Services Checklist - University of MindanaoDocument8 pagesManaged Services Checklist - University of MindanaoRenerio DeplayanNo ratings yet
- Gigaset Da710 ManualDocument18 pagesGigaset Da710 ManualEfiNo ratings yet
- Ccna Voip Quiz 1Document16 pagesCcna Voip Quiz 1deadmen10No ratings yet
- Mapping Old and New Number TEC DocumentsDocument41 pagesMapping Old and New Number TEC DocumentsSourav RoyNo ratings yet
- Mobile Extension PDFDocument4 pagesMobile Extension PDFRichNo ratings yet
- Farfisa Hovedkatalog 11 12Document51 pagesFarfisa Hovedkatalog 11 12ggggabyNo ratings yet
- KX Ns 500neDocument394 pagesKX Ns 500neGhada SokniNo ratings yet
- Digital Switching ConceptsDocument25 pagesDigital Switching ConceptsDutta AvinashNo ratings yet
- 20 - Mitel 5000 Gateways and MiVoice 5000 - Implementation ManualDocument103 pages20 - Mitel 5000 Gateways and MiVoice 5000 - Implementation ManualAsnake TegenawNo ratings yet
- Telecom Egypt Business Trunk Access SolutionDocument17 pagesTelecom Egypt Business Trunk Access SolutionRafiq MagdyNo ratings yet
- Emergency Notification Server: Installation ManualDocument41 pagesEmergency Notification Server: Installation ManualMarcelo Ratto CampiNo ratings yet
- Opt 11e Cisco E1-R2 CasDocument19 pagesOpt 11e Cisco E1-R2 CasJosé GómezNo ratings yet
- NorsokDocument26 pagesNorsokOchie RomeroNo ratings yet
- Panasonic KX-TCD515 ManualDocument96 pagesPanasonic KX-TCD515 ManualccpjunkNo ratings yet
- Huawei eLTE Solution OkDocument16 pagesHuawei eLTE Solution OkImuntNo ratings yet
- Ansi Tia Eia 606 ADocument6 pagesAnsi Tia Eia 606 AmdscorreaNo ratings yet
- C C08 HuaweiDocument63 pagesC C08 HuaweiAdel DataNo ratings yet
- G S M WC DM A LT E G PS Date Issued Applicant List of Customer Premises Equipment (Cpe)Document55 pagesG S M WC DM A LT E G PS Date Issued Applicant List of Customer Premises Equipment (Cpe)kazi AkramNo ratings yet
- Thuyet Minh He Thong Dien Nhe - VNSDocument53 pagesThuyet Minh He Thong Dien Nhe - VNSViệt Dũng Đinh ĐỗNo ratings yet
- Video Door Phones CatalogueDocument12 pagesVideo Door Phones CatalogueNamrata NaveleNo ratings yet
- SkyNodeS200 120215343Document2 pagesSkyNodeS200 120215343GeeNo ratings yet
- KX-NS300 Installation ManualDocument288 pagesKX-NS300 Installation ManualHai Ha88% (16)
- PBX Administrators GuideDocument219 pagesPBX Administrators GuideChuck KingNo ratings yet
- Mobile GlossaryDocument9 pagesMobile GlossaryDavid SinghNo ratings yet
- ZS-3208function& SettingDocument17 pagesZS-3208function& SettingZaen ZuryNo ratings yet