Professional Documents
Culture Documents
bAGIAN1eXAM fINNAL
Uploaded by
Rusman Hendro SusantoOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
bAGIAN1eXAM fINNAL
Uploaded by
Rusman Hendro SusantoCopyright:
Available Formats
1.
Which type of network attack occurs when an unauthorized person tries to persuade a user to share a network user ID and password? brute force denial of service data manipulation social engineering 2 What is the function of the DNS server? It assigns IP addresses to clients. It accepts HTTP requests from clients. It maps a hostname to a corresponding IP address. It manages the domain that clients are assigned to. 3 A computer joins the network and announces itself to all hosts on the LAN. What type of message does the computer send out? Broadcast Simulcast Multicast Unicast 4 What does it mean when a problem is being escalated by a helpdesk? The helpdesk is following up on a resolved problem. The helpdesk has made the problem a lower priority. The helpdesk has solved the problem and is closing the ticket. The helpdesk is moving the problem to a higher level support staff. 5 Which network design layer provides a connection point for end user devices to the network? access core distribution network 6 A user is unable to send e-mail. To begin troubleshooting this problem, the network technician uses the browser on the PC and tries to access some popular Internet websites. Which troubleshooting approach is being followed? bottom-up divide-and-conquer top-down trial and error 7
Refer to the exhibit. H1 can ping H2, H3, and the Fa0/0 interface of router R1. H2 and H3 but not H1 can ping H4 and H5. What is a possible cause for the H1 failure? Router R1 has no route to the destination network. Switch S1 does not have an IP address configured. The link between router R1 and switch S2 has failed. Host H1 does not have a default gateway configured.
Which value would be considered the physical address for data that is sent across an Ethernet segment? IP address port address MAC address network address
Which part of the electromagnetic spectrum is commonly used to exchange data between a PDA and a computer? FM Radar Infrared Ultraviolet
10 What is specified by the network number in an IP address? the network to which the host belongs the physical identity of the computer on the network the node of the subnetwork which is being addressed the broadcast identity of subnetwork 11
Refer to the exhibit. A home network is configured with the information in the graphic. A user tries to manually create a new connection to the network using the SSID Ciscoclass. However, a connection cannot be made. What could be the problem? The SSID is case-sensitive. The SSID must contain at least one number. The SSID should be used with the default name. The SSID must contain a minimum of 32 characters. 12 What type of message is sent to a specific group of hosts? Static Unicast Dynamic Multicast Broadcast 13 What will be one result of using a wireless infrastructure when designing the communications infrastructure for a new building? Wireless devices will be easy to add or relocate. Infrastructure installation will be difficult and expensive. There will be less interference from outside electronic sources. Data transmitted over wireless networks will be more secure than when transmitted over wired networks. 14 Which picture shows a USB port on a PC?
15
Refer to the exhibit. If H4 sends a message to H1 and the destination MAC address is in the MAC table for both Switch1 and Switch2, which host devices will receive the message? only H1 hosts H1 and H4 all hosts that are connected to Switch1 all hosts that are connected to Switch1 and Switch2 16 Which portion of the packet does a router use to forward the packet to the destination? source IP address user data destination IP address control information destination MAC address 17
Refer to the exhibit. Given the use of default masks, which network will router R1 use as the destination network for communications from PC1 to PC2? 128.0.0.0 128.107.0.0 128.107.1.0 192.0.0.0 192.135.0.0 192.135.14.0 18 What does the term "attenuation" mean in data communication? loss of signal strength as distance increases time for a signal to reach its destination leakage of signals from one cable pair to another strengthening of a signal by a networking device 19 Which three address ranges can be used to depict private IP addresses? (Choose three.) 10.0.0.0 to 10.0.0.255 127.16.0.0 to 127.16.255.255 150.150.0.0 to 150.150.255.255 172.16.1.0 to 172.16.1.255 192.168.22.0 to 192.168.22.255 200.100.50.0 to 200.100.50.255 20 Which two statements are true about local applications? (Choose two.) They run on the network. An example of a local application is e-mail. They are accessed from a remote computer. They are stored on the local hard disk. They run on the computer where they are installed. 21 What are two examples of peripheral output devices? (Choose two.) barcode reader digital camera external DVD headphones printer 22 Which address range shows private IP addresses that can be assigned to the hosts on a LAN? 0.0.0.0/8 10.0.0.0/8 1.0.0.0/8 10.255.255.255/8 172.0.0.0/16 172.16.255.255/16 172.16.0.0/16 172.255.255.255/16 192.168.0.0/24 192.168.255.0/24 23 How does a crossover cable make it possible for two "like devices" (for example, two switches) to communicate? The transmit pins are disconnected and only the receive pins are used.
The transmit pins on one device are connected to the transmit pins on the other device. The receive pins on one device are connected to the receive pins on the other device. The transmit pins on one device are connected to the receive pins on the other device. 24 Which two values represent the network number and default mask for the address 209.165.200.225? (Choose two.) 209.0.0.0 209.165.0.0 209.165.200.0 255.0.0.0 255.255.0.0 255.255.255.0 25
Refer to the exhibit. Assume that the command output is from a wireless DHCP client that is connected to a Linksys integrated router. What can be deduced from the output? The DHCP configuration on the router needs to be verified. The WEP key or SSID needs to be verified. The wireless connection is operational. The wireless NIC driver or the NIC itself needs to be reinstalled. 26 Under what circumstance would it be appropriate to use private IP addresses? for communication between two ISPs for a network that is directly connected to the Internet for addresses that are used exclusively within an organization. for a host with more than one direct connection to the Internet 27
Refer to the exhibit. Which option correctly represents the encapsulation of a packet that is sent by Host1 to the web server?
28 A local PC has the correct configuration that is required to access the network. A ping command that is sourced at the PC does not receive a response from a remote device. Which operating system command might be used to determine where the connection failed? netstat tracert ipconfig nslookup 29 A network administrator is setting up an application filtering firewall. Company security policy states that FTP sessions that are coming from the Internet and use the standard FTP port must be blocked. Which TCP/UDP port must the administrator block on the firewall to be in compliance? 21 23 53 80 30 Which protocol is used to transfer files among network devices and perform file-management functions? DNS FTP HTML HTTP 31
Refer to the exhibit. An organization needs to connect PC systems that use private IP addressing to the Internet. The organization has multiple systems that need to access the Internet, but were only able to purchase one public IP address. What should be activated on the Linksys integrated router to achieve this goal? authentication DHCP encryption firewall NAT WEP 32 What wireless technology has the ability to communicate with many devices at the same time, makes use of the 2.4 GHz band, and is limited to low-speed, short-range communications? RF ISM infrared Bluetooth
33 Which two causes of networking problems are related to the physical layer? (Choose two.) damaged cables and connectors incorrect addressing incorrect subnet mask overheated components incorrect default gateway 34 What destination IP address is used in a unicast packet? a specific host a group of hosts all hosts on the network the network broadcast address 35 Which statement is true about UTP cable termination? Cables with RJ-45 connectors are always preterminated. An RJ-45 connector is used on only one end of the UTP cable. Up to 2 to 3 inches of cable may be untwisted at each end of the cable to allow for easier installation of the RJ-45 connector. The RJ-45 connector should be pushed over the wire jacket for a smooth connection. 36 Which term is associated with logical addressing? IP addresses port addresses physical addresses Media Access Control addresses 37 What is true about a wireless access point that is equipped with an omnidirectional antenna? concentrates signal in one direction typically used in bridging applications radiates the signal equally in all directions provides the greatest transmission distance of all antenna types that are used by APs 38 An administrator is troubleshooting a network problem that involves the inability of users to reach Internet sites. During troubleshooting, the administrator is able to successfully ping web sites by their IP address, but pings to domain names are unsuccessful. Which service is most likely at fault? DHCP DNS FTP NAT 39 A college network administrator is planning a wireless LAN to provide service in the student lounge and outdoor patio. The requirements include a range of at least 80 meters and a speed of 30 Mb/s. Which wireless LAN standard meets these requirements? 802.11 802.11a 802.11b 802.11g 40
Refer to the exhibit. The security policy of an organization allows employees to connect to the office intranet from their homes. Which type of security policy is this?
acceptable use incident handling network maintenance remote access 41 Which statement describes an IP address that is configured on a network host? It is a hardware address that identifies a particular host. It is a logical network address that identifies a particular host. It is a logical address that identifies the physical location of a host. It is a hardware address that identifies the physical location of a host. 42
Refer to the exhibit. Assume that the exhibited output is from a host that is connected to a Linksys integrated router. What is the first thing that should be checked if using a bottom-up troubleshooting approach? the default gateway on the host the IP address on the host the IP address on the router the link status LED on the front of the router the subnet mask on the host 43 For devices that do not autosense, which connection requires a crossover cable? hub port to router port PC to hub port PC to switch port PC port to PC port 44 Which attribute must be the same for wireless devices on one network to be able to communicate with devices on a different network? DNS server MAC address default gateway operating system wireless equipment vendor 45
Refer to the exhibit. Which statement is true based on the information that is shown in the exhibit? All wireless devices that are connected to this AP must have an assigned SSID of College. Any wireless client that is attached to this AP must have the same IP address and SSID. The AP is not physically wired to the local LAN. This configuration is found only in an ad hoc wireless network. 46 Which type of computer has an integrated mouse?
desktop laptop mainframe server pocket PC 47 Which statement accurately describes a recommended strategy for end users to employ when they interact with a help desk technician? Provide as much information about the problem as possible. Expect first-level help desk technicians to solve the problem, because they are highly-trained personnel. Hand over the problem to the help desk professionals, then do not interfere with them. At the beginning of the call, ask for the name and number of the supervisor of the help desk technician. 48 Which installation option should be chosen when the current operating system is too damaged to work properly? upgrade multi-boot clean install virtualization 49 What are two ways that a user can interact with an operating system shell? (Choose two.) CLI OS GUI NIC kernel 50 What is the name for the contract between a customer and an ISP that specifies requirements for uptime and service response time? DSL IAB NAP SLA 51 What two commands can be used to form a new binding if client information does not agree with the DHCP client table? (Choose two.) ipconfig /release ipconfig /all ipconfig /flushdns ipconfig /renew ipconfig 52 As an assignment, a computer science student needs to present data in binary format. What are the two possible values that the student can use? (Choose two.) 0 1 2 A F
You might also like
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Temptations in MinistryDocument115 pagesTemptations in MinistryJoseph Koech100% (1)
- 4 Exploring Your Personality Q and Scoring Key (Transaction Analysis)Document3 pages4 Exploring Your Personality Q and Scoring Key (Transaction Analysis)Tarannum Yogesh DobriyalNo ratings yet
- Book of Lost Spells (Necromancer Games)Document137 pagesBook of Lost Spells (Necromancer Games)Rodrigo Hky91% (22)
- How To Calibrate OscilloscopeDocument2 pagesHow To Calibrate OscilloscopeninoNo ratings yet
- Marketing Budget: Expenses Q1 Q2 Q3 Q4 Totals Budget %Document20 pagesMarketing Budget: Expenses Q1 Q2 Q3 Q4 Totals Budget %Miaow MiaowNo ratings yet
- Transport in Plants: Test Yourself 9.1 (Page 178)Document3 pagesTransport in Plants: Test Yourself 9.1 (Page 178)lee100% (3)
- L P 10Document13 pagesL P 10Bình Minh HoàngNo ratings yet
- Axel LeijonhufvudDocument7 pagesAxel LeijonhufvudDario CoceresNo ratings yet
- Telegra Manual - DatasheetDocument79 pagesTelegra Manual - DatasheetNilanjan Chakravortty100% (1)
- Science Web 2014Document40 pagesScience Web 2014Saif Shahriar0% (1)
- Socio-cultural influences on educationDocument4 pagesSocio-cultural influences on educationofelia acostaNo ratings yet
- Gantt Chart Engr110 - Gantt Chart Template 3Document1 pageGantt Chart Engr110 - Gantt Chart Template 3api-375485735No ratings yet
- Theory Is An Explanation Given To Explain Certain RealitiesDocument7 pagesTheory Is An Explanation Given To Explain Certain Realitiestaizya cNo ratings yet
- TOS 22402 Winter 19th I SCHEME Paper Model Answer PaperDocument25 pagesTOS 22402 Winter 19th I SCHEME Paper Model Answer Paperirshadmirza753No ratings yet
- Consumer BehaviourDocument48 pagesConsumer BehaviourdooncollegeNo ratings yet
- Economics and The Theory of Games - Vega-Redondo PDFDocument526 pagesEconomics and The Theory of Games - Vega-Redondo PDFJaime Andrés67% (3)
- How To Oven and Sun Dry Meat and ProduceDocument12 pagesHow To Oven and Sun Dry Meat and ProduceLes BennettNo ratings yet
- LM385Document14 pagesLM385vandocardosoNo ratings yet
- TelanganaDocument16 pagesTelanganaRamu Palvai0% (1)
- Dental System SoftwareDocument4 pagesDental System SoftwareHahaNo ratings yet
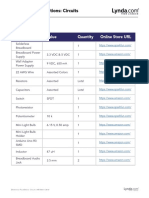
- Electronics Foundations - Basic CircuitsDocument20 pagesElectronics Foundations - Basic Circuitsccorp0089No ratings yet
- Direction: Read The Questions Carefully. Write The Letters of The Correct AnswerDocument3 pagesDirection: Read The Questions Carefully. Write The Letters of The Correct AnswerRomyross JavierNo ratings yet
- Effect of Dust On The Performance of Wind Turbines PDFDocument12 pagesEffect of Dust On The Performance of Wind Turbines PDFJallal ArramachNo ratings yet
- Joel Werner ResumeDocument2 pagesJoel Werner Resumeapi-546810653No ratings yet
- OS9000 AOS 6.1.5 R01 Network Configuration GuideDocument846 pagesOS9000 AOS 6.1.5 R01 Network Configuration GuideclaupasinaNo ratings yet
- Pmls 1 Final Exam Reviewer: Clinical Chemistry ContDocument14 pagesPmls 1 Final Exam Reviewer: Clinical Chemistry ContPlant in a PotNo ratings yet
- Security Testing MatDocument9 pagesSecurity Testing MatLias JassiNo ratings yet
- HCCM System Technical Specification v1Document12 pagesHCCM System Technical Specification v1Ankita ChowdhuryNo ratings yet
- Digital MarketingDocument70 pagesDigital MarketingTarun N. O'Brain Gahlot0% (2)
- SPSS-TEST Survey QuestionnaireDocument2 pagesSPSS-TEST Survey QuestionnaireAkshay PatelNo ratings yet