Professional Documents
Culture Documents
SAP System Administration Made Easy 4.0B
Uploaded by
Pierre LafranceCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
SAP System Administration Made Easy 4.0B
Uploaded by
Pierre LafranceCopyright:
Available Formats
6\VWHP$GPLQLVWUDWLRQ0DGH(DV\
2UDFOHRQ8QL[DQG:LQGRZV17
Release 4.0B
R
SAP Labs, Inc.
Palo Alto, California
Overviewing R/3 System and Roles
Overview
1998 SAP Labs, Inc. 151
Chapter 15: Overviewing R/3 System and Roles
Contents
Overview............................................................................................................................................................................................................151
System Landscapes..........................................................................................................................................................................................151
The One-System Landscape.......................................................................................................................................................................152
The Two-System Landscape.......................................................................................................................................................................153
The Three-System Landscape....................................................................................................................................................................154
Client Definition.................................................................................................................................................................................................154
Role of the Client...............................................................................................................................................................................................154
Transports for System Landscape Maintenance.........................................................................................................................................155
Client Copy versus Client Transport ...............................................................................................................................................................156
Transporting Clients ....................................................................................................................................................................................156
Copying Clients ...........................................................................................................................................................................................157
Deleting a Client ................................................................................................................................................................................................157
Useful OSS Notes..............................................................................................................................................................................................157
Overview
Begin the implementation of SAP by defining all R/ 3 Systems and clients necessary for your production
environment. Depending on the size of your R/ 3 installation and the projects planned, you may require
several R/ 3 Systems that serve different purposes in your system group. These systems form the system
landscape, and clients are distributed within this landscape. Once the system landscape is defined, an
implementation strategy is needed to setup and maintain the systems and clients.
System Landscapes
In general, there are three kinds of system landscapes:
One-system
Two-system
Three-system
The following sections describe these different types and the advantages and disadvantages of each.
Overviewing R/3 System and Roles
System Landscapes
152 1998 SAP Labs, Inc.
A client is a commercially and organizationally independent unit in the R/ 3 System, which means that it
has its own data environment. In general, four different types of clients exist, and each type has a different
functionality, as illustrated below:
CUST Customizing and development client
TEST Unit test client
QTST - Quality assurance testing
PROD - Production client
The One-System Landscape
Because all clients in a one-system landscape reside in the same R/ 3 System but are used for different
purposes (development, testing, master copy, and production), SAP strongly recommends that customers
do not use this configuration. The obvious advantage to this landscape is that there is less hardware to
purchase and maintain for a single R/ 3 System. In the long run, however, the initial savings do not pay
off because of the problems and limitations associated with this configuration. Another notable
disadvantage is that it is not possible to test a R/ 3 upgrade in a single-system landscape. Please see the
following list for additional advantages and disadvantages.
Advantages
Minimal hardware resources
Fewer administrative requirements
Disadvantages
Development immediately effects production environment
Global customizing will immediately affect production
Other clients can impact production performance
Upgrades of production without suitable testing
Not possible to test a R/ 3 upgrade in a one-system landscape
CUST
TEST
PROD
Development & Production
QTST
Overviewing R/3 System and Roles
System Landscapes
1998 SAP Labs, Inc. 153
As a consequence of these limitations, no further development is possible after production work has
started. Changes to repository objects can only be made when production operations are stopped for
development and testing. If the system is stopped, the production downtime could adversely affect your
company.
The Two-System Landscape
CUST
TEST
PROD
Development
Production
QTST
A two-system landscape allows development and production to be performed in two separate systems.
Development and testing must still take place in the same system, which means that development and
testing activities could interrupt each other. Normally, SAP recommends using a three-system landscape,
but the minimum requirement for most needs is a two-system landscape.
The limitations of the two-system landscape arise because development and quality assurance testing
must both take place in the development system. Since no separate quality assurance system is available,
all objects transported to the production system immediately become active. Complicated development
projects often involve transporting partial functionality, without always taking dependencies into account.
This step can cause inconsistencies in the production system and affect the production process.
The following list provides additional advantages and disadvantages.
Advantages
Production data secure
Production performance not affected by other clients
Development efforts separate from production
Disadvantages
Development and quality assurance testing within the same system
Transport of changes from the development system immediately become active in production
Inability to verify the transport contents
Overviewing R/3 System and Roles
Client Definition
154 1998 SAP Labs, Inc.
The Three-System Landscape
The recommended three-system landscape is the one most commonly used, and can meet the needs of
most customers. In a three-system landscape, new developments can be tested without affecting the
production environment, and upgrades can be performed without limitations. The quality assurance
system integrates development efforts and allows you to check the validity and consistency of transported
objects before moving them into production.
Ideally, client roles should be distributed across three different R/ 3 Systems.
Advantages
Production data secure
Production performance not affected by other clients
Independent test environment
Transports are verified before delivery to production
Disadvantages
An increase in hardware requirements
Client Definition
A client represents a commercially and organizationally independent unit in the R/ 3 System with its own
separate data environment, including:
Customizing
Master and transaction data
User master records
The client can be formed under legal, economic, or administrative perspectives. All business data is
protected against access by other clients. The client is characterized by a three-digit client number.
Role of the Client
The role of a client indicates whether a production, test, training, demonstration, or prototype client is
involved. When you configure a client, the attribute role of the client can be used to describe its use.
CUST
TEST QTST PROD
Development
Quality Assurance Production
Overviewing R/3 System and Roles
Role of the Client
1998 SAP Labs, Inc. 155
The following clients can exist in a R/ 3 System:
Customizing client Used for customizing the R/ 3 System
Test client Enables you to unit test Customizing
Quality Assurance client Checks the validity and consistency of transported objects before moving
them into production.
Production client Used for production work
Transports for System Landscape Maintenance
Use the following tools to setup a system landscape:
Change request: All newly created or changed Repository objects are collected in change requests. The
contents of these change requests can be transported together to another R/ 3 System.
Client copy: The client copy tool copies all client dependent customizing applications and user
data to another client in the same R/ 3 System. The tool depends on profiles, allowing
for variations in which data is actually included in a client copy.
Client transport: The client transport tool can transport most of the customizing settings (both client-
independent and client-dependent), application data, and user master data to
another R/ 3 System. Like the client copy tool, client transport requires a profile for
definition of inclusion.
To establish a three-system landscape, you will need to use the transport tools:
Use the client copy tools to setup additional clients in the same system.
Use client transports to copy a client from one system to another.
Overviewing R/3 System and Roles
Client Copy versus Client Transport
156 1998 SAP Labs, Inc.
Use change requests to allow new or modified Repository objects and customizing to be imported into
other systems.
To transport a client to another system:
With a profile select the data to be copied
Export the data to a transport file
Import the data into the target system
Adapt the runtime environment to the current state of the data (if client validation exits)
Client Copy versus Client Transport
There are two ways to copy a client:
Client transport
Client copy
During a client transport, the client is exported out of one R/ 3 System and imported to a different R/ 3
System. During a client copy, a client is replicated within the same R/ 3 System to make a new client. The
diagram below illustrates the two processes:
Client Transport
Client Copy
R/3 Sys. 1
R/3 Sys. 1
R/3 Sys. 2
Client 2
Client 2
Client 1
Client 1
Transporting Clients
The client copy and client transport tools are necessary to actual setup various systems. Client copies
provide a mechanism to duplicate a client in the same R/ 3 System. Client transport allows the movement
of a client from one R/ 3 System to another.
There are two types of client transportsa client export (also refer as client transport) and a remote client
copy. We will discuss client export in chapter 17 of this guidebook. A client transport involves extracting
client-dependent information from the database to a file on the hard drive. This file can then be later
imported into any number of R/ 3 Systems.
Overviewing R/3 System and Roles
Deleting a Client
1998 SAP Labs, Inc. 157
When a client is copied to another system, by default, the client-independent tables are not copied.
However, when you setup a new system, ensure that all customized tables are transported. Select the
option for client-independent tables when performing client-transport.
Copying Clients
The Client Copy tool allows you to copy the customizing environment of a source client to a target client.
To setup the new client:
Prior to client copy, delete the target client
Copy the data from the source client to the target client.
Schedule subsequent processing activities to regenerate the runtime environment (client validation
exits). Reports, screens and name ranges have to be adapted to the current state of the data.
Significant time is required to copy the data because all the client-specific data in the R/ 3 system has to be
replicated. When copying just the customizing data, up to 150 MB is involved, so the process only requires
a few hours (depending on the hardware and system load). Because of time considerations, we
recommend that you execute the client copy program in the background.
You can view the status of an online copying process on the monitor. The status of a background process
can be requested with transaction SCC3 at any time.
Due to its long runtime, the client copy program, if processing is aborted, allows you to restart at any
point.
Deleting a Client
Two different methods exist to delete a client. You can perform the deletion either at the operating system
level or from within the R/ 3 System. The following chapters detail both methods.
Useful OSS Notes
Note # Description
70547 CC-TOPIC: Client transport
70128 CC-TOPIC: Info/ Docu/ Help for copying clients
62739 Configuring a central transport host
40672 System changeability and client control
31557 The multi-client concept of R/ 3 Overview
05206 Client compare for tables: Which tool?
Overviewing R/3 System and Roles
Useful OSS Notes
158 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
Installing a Central Instance of SAP R/3 Version 3.1H with Oracle on Windows NT (Ch. 5)
Completing and Checking the Central Instance Installation of R/3 With Oracle on Win. NT (Ch. 6)
Overviewing Customization and Workbench Development (Ch. 71)
Using the Customizing Organizer for IMG Customization (Ch. 72)
Using the Workbench Organizer to Modify an ABAP/4 Program (Ch. 73)
R/3 Basis Knowledge Products
SAP Software Logistics CD Reference Pre-Installation Systems and Roles
Technical Implementation Pre-Installation Roles and Responsibilities,
System and Roles
Technical Implementation Implementation Define Procedures
Basis Courses
Workbench Organizer, Transport System & Upgrade (BC325)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Copying a Client within a R/3 System
Overview
1998 SAP Labs, Inc. 161
Chapter 16: Copying a Client within a R/3 System
Contents
Overview............................................................................................................................................................................................................161
Creating a New Target Client within the Source Client .................................................................................................................................161
Performing the Client Copy in the New Target Client....................................................................................................................................166
Viewing the Client Copy Activities ..................................................................................................................................................................169
Useful OSS Notes............................................................................................................................................................................................1613
Overview
When a separate client is needed to test, customize, or train, you can create this client by copying an
existing one. During the client copy, ensure that:
The tables copied are not changed in the source client
No one is working in the target client
The following example will show you how to copy client 000 to client 100. Client 100 is used later as a
development/ customizing client.
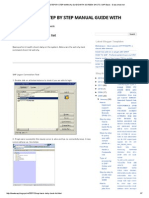
Creating a New Target Client within the Source Client
Login to the source client (for example,
000).
1. Enter the Source Client number in
the Client field.
2. Enter DDIC in the username field.
3. Enter the password for DDIC.
4. Press Enter to accept the user
default language or enter a
language code (e for English.)
1
2
3
4
Copying a Client within a R/3 System
Creating a New Target Client within the Source Client
162 1998 SAP Labs, Inc.
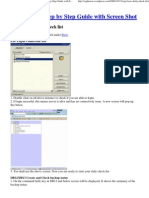
5. Choose Tools Administration
Administration Client admin.
Client maintenance.
Alternative:
6. Choose Table View Display
Change.
7. Click Enter.
8. Click the New entries button to
create a new target client.
5
6
7
8
Copying a Client within a R/3 System
Creating a New Target Client within the Source Client
1998 SAP Labs, Inc. 163
9. Enter the new target client number
(any new three digit number, for
example, 100).
Do not use client numbers 000, 001, or
066 for your new clients because they
are reserved by SAP.
10. Enter the new client name.
11. Enter the City in which the client is
located.
The Logical System field applies
only to the ALE application.
12. Enter a currency code in the Std
currency field (enter usd for U.S.
dollars).
13. Enter a category (in this example,
Customizing).
14. Because this client will be used for
development/ customization, select
Automatic Recording of Changes
15. Click the possible entries button to
select Changes to Repository and
client-ind. customizing allowed.
16. Click the Save icon to proceed to the
next screen.
17. Click the Back icon to return to
previous screen.
For more information about the Client-
independent object changes field, position
the cursor in this field and press F1.
9
10
11
12
13
14
15
16 17
Copying a Client within a R/3 System
Creating a New Target Client within the Source Client
164 1998 SAP Labs, Inc.
The chart below defines when certain change options can be used. It can serve as a helpful reference and
provide examples of the change options for both clients and systems. The X indicates for which clients or
systems the attribute may be used. Notice that multiple attributes may apply to some clients or systems. In
such a situation, the most appropriate attribute depends on the landscape structure.
Clients: DEV TEST QTST PRD TRAIN SANDBOX
Client -dependent change opt ions
Changes w/ o automatic recording X
Automatic recording of changes X
No changes allowed X X X
No transports allowed X X
Client -independent change opt ions
Changes to Repository and client-
ind. customizing allowed
X
No changes to client-independent
customizing objects
X X
No changes to Repository objects X X
No changes to Repository and
client-independent custom obj.
X X X X X
DEV Development client (development/ customizing)
TEST Unit test client
QTST Quality Assurance or Test client (to test the customization or new development)
PRD Production Client (used as daily production)
TRAIN Training Client (used to train end users in the use of the customer-specific
developed/ customized functions)
SANDBOX Playground client (test other advanced R/ 3 function, self-train, etc.)
Copying a Client within a R/3 System
Creating a New Target Client within the Source Client
1998 SAP Labs, Inc. 165
18. You should see the new target
client in the list.
19. Enter the transaction /nEND to exit
the system.
20. Click Yes.
Before you begin the actual copy process, do the following:
Turn Archiving off in the database by using sapdba (see chapter 109, Changing the Archive
Mode).
Check your available tablespace allocation with transaction code DB02 (see chapter 92,
Analyzing Current Tablespaces Sizes. You may need to expand these tablespaces by adding
a datafile using sapdba. When finished, refresh the statistics to get an accurate result.
We recommend that you first perform a test run:
1. Go to transaction code SCCL
2. Check the test box
3. Run the copy
4. Ensure a successful run
Remember, a client copy test run can take just as long as the actual client copy.
Since the operation is computationally intensive, client copies should be run when users
are not on the system.
18
19
20
Copying a Client within a R/3 System
Performing the Client Copy in the New Target Client
166 1998 SAP Labs, Inc.
Performing the Client Copy in the New Target Client
To logon to the R/ 3 System:
1. Enter the client number in the
Client field (in this example, 100).
2. Enter sap* in the username field.
3. Enter the password for SAP*.
4. Press Enter to accept the user
default language or enter a
language code (e for English.)
5. Choose Tools Administration
Administration Client admin.
Client copy Local client copy.
Alternative:
6. In the Selected profile field, enter
SAP_ALL to copy data from the
source client (in this example,
SAP_USR).
7. Enter the Source client number (in
this example, 000).
8. Click the Execute in backgrd. button
to run the client copy as a
background job.
1
2
3
4
5
6
7
8
Copying a Client within a R/3 System
Performing the Client Copy in the New Target Client
1998 SAP Labs, Inc. 167
The following profiles are delivered from SAP:
PROFILE DESCRIPTION
SAP_ALL All data of a client.
SAP_APPL All Customizing data and application data, incl. the user profiles are copied.
SAP_CUST All Customizing tables, incl. the user profiles are copied.
SAP_UAPP All Customizing data and application data, incl. the user profiles and user data are
copied.
SAP_UCUS All Customizing tables, incl. user master data and user profiles are copied.
SAP_USR Authorization and user masters.
9. Click Schedule job.
10. In the Verification screen, click Yes.
9
10
Copying a Client within a R/3 System
168 1998 SAP Labs, Inc.
11. To schedule the job to run
immediately, click the Immediate
button. Otherwise, select Date/Time
to choose an appropriate start time
(in this example, click Immediate).
12. Click the Save icon.
13. Enter an Output device (in this
example, LP01).
14. Click the Save button.
The message The background job was
successfully scheduled; result displayed
in SCC3 appears.
Depending on the size of the R/ 3 client and profile that you selected, client copy could take
from five minutes (if copying authorization and user masters only) up to a few hours.
11
12
13
14
Copying a Client within a R/3 System
Viewing the Client Copy Activities
1998 SAP Labs, Inc. 169
Viewing the Client Copy Activities
Follow this step-by-step procedure to ensure that your client copy was successful:
1. From the System Administration
window, choose Administration
Client admin. Copy logs.
Alternative:
2. To see the client copy activity detail,
first select the desired target client
(in this example, 100) by positioning
the cursor on its line.
3. Click Choose.
After the client copy is completed,
the Status text should read
Successfully completed.
4. After the process is completed,
position the cursor on the line item
containing your source client.
5. Click Choose.
1
2
3
5
4
Copying a Client within a R/3 System
Viewing the Client Copy Activities
1610 1998 SAP Labs, Inc.
A Log Analysis screen appears that
shows the client copy.
6. Click the Log button to see a
detailed analysis of the client copy.
6
Copying a Client within a R/3 System
Viewing the Client Copy Activities
1998 SAP Labs, Inc. 1611
This screen shows a detailed log of
the client copy.
7. To view the log in even greater
detail, click the Display more button.
This step increases the number in
the Expand level in overall log field (1
is the lowest level, 4 is the highest
level).
7
Copying a Client within a R/3 System
Viewing the Client Copy Activities
1612 1998 SAP Labs, Inc.
This screen shows the most
detailed log (level 4) of the client
copy.
If your client copy fails:
1. Examine your tablespaces with DB02, and then refresh the statistics to get current
information. Refer to chapter 92, Analyzing Current Tablespaces Sizes.
2. Check your archive directory <drive>:\ oracle\ saparch. If it is full, you have an archive
stuck condition. Using sapdba, backup the saparch directory and rerun the client copy
with archive mode set to off.
Copying a Client within a R/3 System
Useful OSS Notes
1998 SAP Labs, Inc. 1613
Useful OSS Notes
Note # Description
70290 CC-INFO: Exceptions in the client copy
70128 CC TOPIC: Info/ Docu/ Help for copying clients
67205 CC INFO: Copying large, productive clients
For further details refer to
R/3 System Administration Made Easy
Deleting a SAP Client Using a SAP Executable (Ch. 19)
Deleting a Client Using R/3 Functionality (Ch. 20)
R/3 Basis Knowledge Products
System Logistics CD Reference Pre-Installation Systems and Roles Setting Up a System
Landscape
R/3 System Online Help
Online Documentation CD Transport Control Using the R/3 Transport Program R/3 Transport:
General Information
Basis Courses
Workbench Organizer, Transport System & Upgrade (BC325)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Transporting a R/3 Client to another R/3 System
Overview
1998 SAP Labs, Inc. 171
Chapter 17: Transporting a R/3 Client to another R/3 System
Contents
Overview............................................................................................................................................................................................................171
Creating the Transport Request ......................................................................................................................................................................171
Scheduling the Client Transport Background Job ........................................................................................................................................174
Checking the Transport Log ............................................................................................................................................................................178
Useful OSS Notes............................................................................................................................................................................................1711
Overview
This chapter describes the first part of the export process, creating a transport request with transaction
SCC8. The process is completed when the client is imported to the target R/ 3 System (see chapter 18,
Importing a Client from another R/3 System).
Transporting a R/ 3 client from one R/ 3 System to another involves the following steps:
The export described in this chapter
The creation of the client entry described in Creating the Target Client (chapter 18)
The import described in Importing the Data into the Target R/ 3 System (chapter 18)
The post-processing activities described in Performing Post Import Activities (chapter 18)
When you export from a R/ 3 client, transport client data from one R/ 3 System to another. This process is
different from a client copy were a duplicate client is made within the same System. Exported files are
found in the <drive>:\ usr\ sap\ trans\ data and <drive>:\ usr\ sap\ trans\ cofiles directories. The following
step-by-step procedure shows how to export a R/ 3 client.
Creating the Transport Request
Login to the client that you want to
export.
1. Enter the client number in the
Client field (in this example, 001).
2. Enter DDIC in the username field.
3. Enter the password for DDIC.
4. Press Enter to accept the user
default language or enter a
language code (e for English.)
1
2
3
4
Transporting a R/3 Client to another R/3 System
Creating the Transport Request
172 1998 SAP Labs, Inc.
5. Choose Tools Administration
Administration Client
admin. Client transport Client
export.
Alternative:
SCC8 is the preferred transaction
instead of SCC2.
6. From the Selected profile field, click
the possible entries button to list the
default profiles.
7. Based on the Description, click the
Profile name containing the
elements you want to transport (for
example, SAP_CUST).
8. Click Choose.
5
6
7
8
Transporting a R/3 Client to another R/3 System
Creating the Transport Request
1998 SAP Labs, Inc. 173
9. From the Target system field, click
the possible entries button to list the
choices.
10. Select the target system
identification, <SAPSID> (in this
example, PRD).
11. Click Choose.
12. Click the Enter button to review the
parameters.
9
11
10
12
Transporting a R/3 Client to another R/3 System
Scheduling the Client Transport Background Job
174 1998 SAP Labs, Inc.
Scheduling the Client Transport Background Job
1. Ensure that the Selected profile
entries are correct.
You can now select the Test run
checkbox to ensure that you have
correctly configured everything
before transporting the client.
2. Click Execute in backgrd.
3. Click Schedule Job to schedule the
background job to transport client
001.
1
3
2
Transporting a R/3 Client to another R/3 System
Scheduling the Client Transport Background Job
1998 SAP Labs, Inc. 175
4. Verify the parameters, then click
Yes to continue.
An INFO client export screen
appears.
5. After reading the instructions, click
Enter.
4
5
Transporting a R/3 Client to another R/3 System
Scheduling the Client Transport Background Job
176 1998 SAP Labs, Inc.
6. Click Immediate to start the job.
7. Click the Save icon.
6
7
Transporting a R/3 Client to another R/3 System
Scheduling the Client Transport Background Job
1998 SAP Labs, Inc. 177
8. From the Output device field, click
the possible entries button to list the
choices.
9. Click Save.
The messages Format set to
X_65_132 and The background job
was successfully scheduled; result
displayed in SCC3 appears.
10. Do not panic if you see this screen.
It means that the client copy has
already started and is preventing
two client copies from running
together.
When you see this screen, simply
click OK.
8
9
10
Transporting a R/3 Client to another R/3 System
Checking the Transport Log
178 1998 SAP Labs, Inc.
Checking the Transport Log
To monitor the progress of the client export:
1. Choose
Tools Administration Administr
ation Client admin. Copy logs.
Alternative:
2. In the beginning the Status text
should display Initializing
3. To refresh the status, enter the
transaction /nSCC3.
3
2
1
Transporting a R/3 Client to another R/3 System
Checking the Transport Log
1998 SAP Labs, Inc. 179
While you wait for the export process,
invoke Qslice.exe (a program that is
included in the Microsoft Resource Kit)
to monitor the progress of the process
online. The graphics at the right-hand
side shows you that Oracle73.exe and
r3trans.exe are currently active. The bar
shows you the CPU usage by the
programs.
The Client Copy Log Analysis screen
appears. Ensure that the Status text
says Successfully completed for the
Target Client EXP.
4. Click once on the log entry of the
EXP client transport that just
completed.
5. Click Choose.
4
5
Transporting a R/3 Client to another R/3 System
1710 1998 SAP Labs, Inc.
6. Click once on the line item again.
7. Click Choose.
A summary of the Client Copy Log
Analysis appears.
To view the complete technical
information on the export process, click
the Log button.
6
7
Transporting a R/3 Client to another R/3 System
Useful OSS Notes
1998 SAP Labs, Inc. 1711
Useful OSS Notes
Note # Description
70547 CC-TOPIC: Client transport
70128 CC-TOPIC: Info/ Docu/ Help for copying clients
For further details refer to
R/3 System Administration Made Easy
Importing a R/3 Client from another R/3 System (Ch. 18)
R/3 Basis Knowledge Products
Software Logistics CD Reference Implementation QA Procedures Planning Imports
R/3 System Online Help
Online Documentation CD System Administration Transport System/Transport Control
Basis Courses
Workbench Organizer, Transport System & Upgrade (BC325)
Importing a R/3 Client from another R/3 System
Overview
1998 SAP Labs, Inc. 181
Chapter 18: Importing a R/3 Client from another R/3 System
Contents
Overview............................................................................................................................................................................................................181
Before You Begin..............................................................................................................................................................................................181
Creating the Target Client ................................................................................................................................................................................182
Sharing the Transport Directory of the Source R/3 System in the Target R/3 System...............................................................................186
Importing the Data into the Target R/3 System..............................................................................................................................................188
Performing Post-Import Activities...................................................................................................................................................................189
Checking the Import Logs..............................................................................................................................................................................1812
Useful OSS Notes............................................................................................................................................................................................1816
Overview
The goal of performing a client export and import is to move a client between two R/ 3 Systems.
Importing of a client from another system depends upon the exporting process explained in chapter 17,
Transporting a R/3 Client to another R/3 System, which describes how to export a client with transaction
SCC8. The end of the export process results in files created in the source systems directories.
<drive>:\ usr\ sap\ trans\ cofiles
<drive>:\ usr\ sap\ trans\ data
The target R/ 3 System shares these files so that a transport can be performed. In the following example,
certain assumptions are made:
Source R/ 3 System: PNSFO36
Source <SAPSID>: DEV
Source Client: 001
Target R/ 3 System: DODGERS
Target <SAPSID>: PRD
Target Client: 100
Before You Begin
Check if the transport file tpparam in directory <drive>:\ usr\ sap\ trans\ bin is correctly configured.
Ensure that the transport system has been initialized with transaction SE06.
Importing a R/3 Client from another R/3 System
Creating the Target Client
182 1998 SAP Labs, Inc.
You cannot reverse or undo a transport! SAP does provide such a function in the transport
system. The R3trans function SAFETYEXPORT will not provide this functionality because:
The order of transport requests being reloaded would have to be the exact opposite of the
import sequence. This reason alone makes reversing individual transports impossible.
The transport process includes actions that are irreversable, especially (but not limited to):
- Executing XPRAs (eXecute PRogram After import)
- Structure changes in the database (new tables, fields, indices)
- Mixed transport of INSERTs and DELETEs
If an error occurs, the alternatives are to restore a data backup or continue onwards. If you
regularly perform large or critical transports, it makes sense to first import to a test system.
Creating the Target Client
Logon to any client (for this example, we use client 000) of the target R/ 3 System as user SAP*. Then follow
the step-by-step procedure below to create the target client:
1. Choose Tools Administration
Administration Client
admin. Client maintenance.
Alternative:
2. Click the Display/Change button.
The message Warning: the table is
client-independent (see Help for
further Info) appears.
1
2
Importing a R/3 Client from another R/3 System
Creating the Target Client
1998 SAP Labs, Inc. 183
3. Click New entries.
4. Enter the new target client number
(any new three digit number, for
example, 100).
Do not use 000, 001, or 066 for your
new clients because they are reserved
by SAP.
5. Enter the City where the client is
located.
The Logical System field applies
only to the ALE application.
6. Enter a currency code in the Std
currency field (enter usd for U.S.
dollars).
7. Because this client will be used for
development/ customization, select
Automatic Recording of Changes
8. Click the possible entries button to
select Changes to Repository and
client-ind. customizing allowed.
9. Click the Save icon to proceed to the
next screen.
10. Click the Back icon to return to the
previous screen.
3
4
5
6
7
8
9 10
Importing a R/3 Client from another R/3 System
Creating the Target Client
184 1998 SAP Labs, Inc.
For more information about the client-independent object changes field, position the cursor in
this field and press F1.
11. Double-click the desired client
category type to select it (in this
example, Test is selected.
Do not select the Productive category. If
you do, the post-import process can
not be performed.
12. In the Client-independent object
changes field, click the possible
entries button.
11
12
Importing a R/3 Client from another R/3 System
Creating the Target Client
1998 SAP Labs, Inc. 185
13. Select the desired option and click
Enter.
14. Click Save.
15. Choose System Log off.
13
14
15
13
Importing a R/3 Client from another R/3 System
Sharing the Transport Directory of the Source R/3 System in the Target R/3 System
186 1998 SAP Labs, Inc.
16. Click Yes.
Sharing the Transport Directory of the Source R/3 System in the Target R/3 System
The following three data files result from creating the export process:
<drive>\ usr\ sap\ trans\ data\ KT<transport number>.<SAPSID> (such as KT00010.DEV) as data file for
client-independent tables
<drive>\ usr\ sap\ trans\ data\ KO<transport number>.<SAPSID> (such as RT00010.DEV) as data file for
client-specific tables
<drive>\ usr\ sap\ trans\ data\ SX<transport number>.<SAPSID> (such as SX00010.DEV) as data file for
texts
The following two data files result from the creation of the export process:
<drive>\ usr\ sap\ trans\ cofiles\ KT<transport number>.<SAPSID> (such as KT00010.DEV) as cofile for
client-independent tables
<drive>\ usr\ sap\ trans\ cofiles\ KO<transport number>.<SAPSID> (such as KT00010.DEV) as cofile for
client-dependent tables
The target R/ 3 System shares these two files so that transport can be performed. The following procedure
assumes that a network connection exists between the source and target systems. If this is not the case, then
this step should be performed with the help of some form of magnetic media.
1. Right-click the Windows NT Start
button and choose Explore.
16
1
Importing a R/3 Client from another R/3 System
Sharing the Transport Directory of the Source R/3 System in the Target R/3 System
1998 SAP Labs, Inc. 187
2. Choose Tools Map Network Drive.
3. Select the drive that you wish to
declare as the shared drive (in this
example, drive T).
4. Enter the shared drive name of the
source R/ 3 server (in this example,
\\pnsfo36\sapmnt.)
5. Click OK.
The shared directory T with its
subdirectories are displayed.
2
3
4
5
Importing a R/3 Client from another R/3 System
Importing the Data into the Target R/3 System
188 1998 SAP Labs, Inc.
Importing the Data into the Target R/3 System
1. On the R/ 3 System, click the
Windows NT Start button and
choose Programs Command
Prompt.
To obtain the proper transport request number, change to directory trans\ cofiles and execute
dir to view the KO and KT transport request file names. The highest number is the most recent
transport request number.
2. Change the directory to the shared
transport directory (in this
example, T).
3. To change to the proper directory,
enter cd trans\bin at the
command prompt.
4. To ensure the buffers have been
added by the R/ 3 Transport
System, enter tp showbuffer <Target
SAPSID> (in this example, tp
showbuffer prd).
1
2
4
3
Importing a R/3 Client from another R/3 System
Performing Post-Import Activities
1998 SAP Labs, Inc. 189
First import client-independent data,
then client-dependent data.
5. To import client-independent data,
enter tp import <Source
SAPSID>KO<Nr.> client<Target
Client Nr.> <Target SAPSID> (in
this example, tp import
DEVKO00010 client100 PRD).
6. To import client-dependent data,
enter tp import <Source
SAPSID>KT<Nr.> client<Target
Client Nr.> <Target SAPSID> (in
this example, tp import
DEVKT00010 client100 PRD).
Performing Post-Import Activities
Logon to the target system in the client that has just been imported (100 in this example) as user SAP*.
Enter pass as the password, or the current password if user master records have been imported.
To logon to the target client of the
target R/ 3 System:
1. Enter the client number in the
Client field (in this example, 100).
2. Enter sap* in the username field.
3. Enter the password for sap*.
4. Press Enter to accept the user
default language or enter a
language code (e for English.)
5
6
1
2
3
4
Importing a R/3 Client from another R/3 System
Performing Post-Import Activities
1810 1998 SAP Labs, Inc.
5. Choose Tools Administration
Administration Client
admin. Client Transport Client
Import.
Alternative:
6. Review the parameters and click
Execute in backgrd. button.
7. Click Schedule Job.
5
6
7
Importing a R/3 Client from another R/3 System
1998 SAP Labs, Inc. 1811
8. Click Immediate.
9. Click Save.
10. Enter the proper Output device.
11. Click Save.
The messages Format set to
X_65_132 and The background job
was successfully scheduled; result
displayed in SCC3 appears.
8
9
10
11
Importing a R/3 Client from another R/3 System
Checking the Import Logs
1812 1998 SAP Labs, Inc.
Checking the Import Logs
After completing the import procedure, check the log files to ensure that the process concluded
successfully.
1. Choose Tools Administration
Client admin. Copy logs.
Alternative:
2. The status of the post import
process appears. Click on the line
item that displays Processing
3. Click Choose.
4. Click the line item that displays
Processing again.
5. Click Choose.
2
1
3
5
4
Importing a R/3 Client from another R/3 System
Checking the Import Logs
1998 SAP Labs, Inc. 1813
The processing information
appears.
Another way to view the post
import process is to review
background job status.
6. To monitor the post-import
process, enter the transaction
/nSMX.
6
Importing a R/3 Client from another R/3 System
Checking the Import Logs
1814 1998 SAP Labs, Inc.
The screen informs you that the
CLIENTEXPORT/IMPORT 100 job
is running.
7. Click Job overview to review
detailed information.
Accept the default values.
8. Click Enter to continue.
7
8
Importing a R/3 Client from another R/3 System
1998 SAP Labs, Inc. 1815
9. The job is marked as an active job.
Depending on the amount of data you
have, the process may take a while.
You may use any OS activity
monitoring tool (for example,
QSLICE.EXE) to see the activities of the
processes (for example, oracle73.exe and
disp+work.exe).
9
Importing a R/3 Client from another R/3 System
Useful OSS Notes
1816 1998 SAP Labs, Inc.
Useful OSS Notes
Note # Description
70547 CC-TOPIC: Client transport
70128 CC-TOPIC: Info/ Docu/ Help for copying clients
34395 tp return codes and programs used by tp
11677 Transports with event-controlled RDDIMPDP
For further details refer to
R/3 System Administration Made Easy
Transporting a R/3 Client to another R/3 System (Ch. 17)
R/3 Basis Knowledge Products
System Logistics CD Reference Implementation QA ProceduresPlanning Imports
R/3 System Online Help
Online Documentation CD System Administration Transport System/Transport Control
Basis Courses
Workbench Organizer, Transport System & Upgrade (BC325)
Deleting a Client Using R/3 Functionality
Overview
1998 SAP Labs, Inc. 201
Chapter 20: Deleting a Client Using R/3 Functionality
Contents
Overview............................................................................................................................................................................................................201
Heres How.....................................................................................................................................................................................................201
Monitoring the Delete Client Background Job...............................................................................................................................................204
Useful OSS Notes..............................................................................................................................................................................................208
Overview
Deleting a client permanently removes the client from a R/ 3 System. Essentially, this process is the reverse
process of creating a client (Client Copy, Client Transport, etc.). Before deleting any client, consult with all
R/ 3 users to ensure that the client should indeed be deleted. (It is recommended that clients be deleted
using SCC5.)
In this chapter, we perform the deletion from within the client.
Deleting a client is permanent and unrecoverable. Ensure that the client is not in use!
Deleting a client using the R/ 3 transaction code SCC5 mentioned in this chapter will clean up
the SAPSCRIPT and Batch-input data. SCC5 requires much smaller rollback-segments than
using R3TRANS to delete a client that is mentioned in chapter 19, Deleting a SAP Client Using a
R/3 Executable. R3TRANS runs faster than SCC5. SAP recommends using the method discussed
in this chapter.
Heres How
Logon to the client that you would like
to delete:
1. Enter the client number in the
Client field (in this example, 100).
2. Enter sap* in the username field.
3. Enter the password for sap*.
4. Press Enter to accept the user
default language or enter a
language code (e for English.)
1
2
3
4
Deleting a Client Using R/3 Functionality
Heres How
202 1998 SAP Labs, Inc.
5. Choose Tools Administration.
6. Choose Administration Client
admin. Special functions Delete
client.
Alternative:
7. Click the Background button to
delete the client in background.
There are two options that you
may choose:
Test run allows you to
simulate client delete and
obtain a report for the
process.
Delete entry from T000 cleans
up the client information in
table T000 that stores the
client information.
To use the default/ current R/ 3
server, you do not need to
provide any server name into
Background servers field. To
choose a different server, just
enter the servers name.
8. Click the Schedule job button.
5
6
7
8
Deleting a Client Using R/3 Functionality
Heres How
1998 SAP Labs, Inc. 203
9. Click Yes.
10. Click Immediate.
11. Click the Save icon.
9
10
11
Deleting a Client Using R/3 Functionality
Monitoring the Delete Client Background Job
204 1998 SAP Labs, Inc.
12. Enter a printer name in the Output
Device field.
13. Click the Save button.
The message The background job was
successfully scheduled; result
displayed in SCC3 appears.
Monitoring the Delete Client Background Job
Follow the steps below to monitor the Delete Client background job:
1. Choose Tools Administration
Administration Client admin.
Copy logs.
Alternative:
12
13
1
Deleting a Client Using R/3 Functionality
Monitoring the Delete Client Background Job
1998 SAP Labs, Inc. 205
2. Select the line item that indicates
the target client we want to delete
(in this example, 100).
3. Click Choose.
4. Select the line item that indicates
the target client we want to delete
(in this example, 100).
2
3
4
Deleting a Client Using R/3 Functionality
Monitoring the Delete Client Background Job
206 1998 SAP Labs, Inc.
The client deletion is still running.
5. Click Refresh to view the latest
status.
6. To view the status online, click
Monitor.
The bar chart shows you the
current activities.
5 6
Deleting a Client Using R/3 Functionality
Monitoring the Delete Client Background Job
1998 SAP Labs, Inc. 207
7. Using QuickSlice, we can see that
oracle73.exe, the tenth disp+work.exe
are running. This view tells you
that the Oracle database is busy
deleting client dependent data
(client 100). Meanwhile, the
Background Work Processes are
busy communicating with the
database.
7
7
Deleting a Client Using R/3 Functionality
Useful OSS Notes
208 1998 SAP Labs, Inc.
Congratulations on successfully
deleting a client!
Useful OSS Notes
Note # Description
35952 Client deleted, space still filled in database
Deleting a Client Using R/3 Functionality
Useful OSS Notes
1998 SAP Labs, Inc. 209
For further details refer to
R/3 System Administration Made Easy
Deleting a R/3 Client Using a R/3 Executable (Ch. 19)
R/3 System Online Help
Online Documentation CD Transport Control Client Copy Tools
Basis Components System Administration Transport
System/Transport Control
Basis Courses
Workbench Organizer, Transport System, and Upgrade (BC325)
Overviewing R/3 Profile Maintenance Tool
Overview
1998 SAP Labs, Inc. 241
Chapter 24: Overviewing R/3 Profile Maintenance Tool
Contents
Overview............................................................................................................................................................................................................241
What are Profiles?.............................................................................................................................................................................................242
Instance Profile............................................................................................................................................................................................244
Default Profile..............................................................................................................................................................................................244
Start Profile..................................................................................................................................................................................................244
Process of Profile Maintenance.......................................................................................................................................................................245
R/3 Profiles Definition.......................................................................................................................................................................................248
How Do I Maintain Profiles?.............................................................................................................................................................................249
Basic Tasks.................................................................................................................................................................................................249
Extended Tasks.........................................................................................................................................................................................2410
Hints and Questions .......................................................................................................................................................................................2411
Useful hints for Profile Maintenance..........................................................................................................................................................2411
Warning: Values are not allowed.......................................................................................................................................................2411
Changed Parameters become Not Active .........................................................................................................................................2411
Frequently Asked Questions .....................................................................................................................................................................2411
Useful OSS Notes............................................................................................................................................................................................2413
Overview
This chapter introduces the R/ 3 Basis tools that help you configure the R/ 3 Application Servers. When
setting up a R/ 3 application server, configure the following parameters:
The runtime environment of the instance (resources such as main memory size, shared memory, roll,
and paging size)
Services available to the instance (dialog, background processes, etc.)
The location of other services (database host)
Operating system files, called profiles, store the setup information. For each component of the
configuration exists a parameter, and the profiles assign values to these parameters. The R/ 3 System uses
three different profile types:
Instance
Default
Start
You can modify each of these. However, changes in profiles are infrequent for most productive R/ 3
Systems.
The instance profile provides an application server with configuration parameters that define the available
instance resources (main memory, shared memory, etc.), and determines how to allocate memory to the
R/ 3 application buffers. Typically, these parameter settings adapt the instance based on the desired
resources.
Overviewing R/3 Profile Maintenance Tool
What are Profiles?
242 1998 SAP Labs, Inc.
To assign the same parameter value for all application servers, enter it in the default profilefor example,
the name of the database host or the computer on which the message server is running. When you start a
R/ 3 instance on a host, the start profile defines which R/ 3 services are started (for example, message
server, dialog, gateway, or enqueue process). The SAP program startsap is responsible for initiating these
service processes, and it uses a start profile to begin the startup process.
All host computers in a R/ 3 System can access these profiles. Several R/ 3 instances may simultaneously
use a single profile. Separate profiles are not required for each R/ 3 instance. In general, you could change
the configuration of an application server either manually or dynamically without downtime of the server.
Only after restarting the R/ 3 instance are manual profile changes activated.
An R/ 3 application server always uses the profile file at the operating system level when it is started.
The chapters 2436 about R/3 Profile Maintenance describe how to maintain profiles from the Computing
Center Management System (CCMS). The CCMS profile maintenance tool analyzes and assists in making
changes to the profiles. The tool not only checks the accuracy of each profile, it also checks the integrity of
your cumulative system setup. The benefits of using the CCMS over editing profiles at the operating
system level will be discussed later in this chapter (see Process of Profile Maintenance).
From release 3.0A, you can manage your profiles from the CCMS. You should not directly edit the active
profiles at the operating system level.
System configuration changes occur infrequently for most productive R/ 3 Systems. Alterations are
required only in exceptional cases. For example, SAP service processes may need to be moved between
instances. Changes for non-productive systems can be frequent. In either of these two cases, having an
easy mechanism for maintaining these changes and establishing a high degree of integrity is important.
SAP provides the profile maintenance tool for these tasks.
In this section, we begin by describing R/ 3 profiles and how the profile maintenance process works. We
then show you how to maintain profiles. We divided the actions into basic tasks and extended tasks. To
prevent or solve problems, useful hints and frequently asked questions appear at the end of this section.
What are Profiles?
A profile is an operating system file that contains instance setup information. During R/ 3 installation, the
following three profiles are automatically created in the file system:
Instance profile: <SAPSID>_<Instance>_<hostname> (such as DEV_DVEBMGS00_pfsn036)
Default profile: DEFAULT.PFL (such as DEFAULT.PFL)
Start profile: START_<Instance>_<hostname> (such as START_DVEBMGS00_pfsn036)
Overviewing R/3 Profile Maintenance Tool
What are Profiles?
1998 SAP Labs, Inc. 243
<SAPSID> is the SAP system name, <Instance> is the SAP instance name, and <hostname> is the name of
the server related to this profile. When the first instance of a R/ 3 System is installed, the system creates a
default profile. Otherwise, the existing default profile is simply updated.
The global file directory stores the R/ 3 profiles in:
Windows NT systems: \ \ <SAPGLOBALHOST>\ sapmnt\ <SAPSID>\ sys\ profile
UNIX systems: /usr/sap/<SAPSID>/SYS/profile
<SAPSID> is the SAP system name and <SAPGLOBALHOST> is the name of the NT machine where the
global profile directory is physically located. This global directory should be accessible from all host
computers in a R/ 3 System. Several R/ 3 instances can simultaneously use a single profile. Separate
profiles are not required for each R/ 3 instance.
In the following graphic, the location of R/ 3 Profiles on Windows NT; SAPSID is DEV; Instance is
DVEBMGS00; and the hostname is pnsfo36:
The same parameter can be in a default or instance profile. The SAP startup process first looks for a profile
parameter in the instance profile. If the parameter is not found, then the default profile is searched. If the
parameter cannot be found in either of these locations, the default value is taken from the startup program
coding.
The profile file is structured as follows:
# This is a comment in a SAP profile:
Parametername1 = Value1
Parametername2 = Value2
Parameter names with a common root logically belong together. For example, the root of parameters that
control the dispatcher within an application server is: rdisp/ .
Overviewing R/3 Profile Maintenance Tool
What are Profiles?
244 1998 SAP Labs, Inc.
Instance Profile
The instance profile provides an application server with configuration parameters that adapt the instance
based on the desired resources. They also define the available instance resources (main memory, shared
memory, roll memory, etc.), and how to allocate memory to the R/ 3 application buffers. To start
application servers on several computers using identical parameter settings, a single instance profile can
be used. It is generally unnecessary for each application server to have its own instance profile.
You can choose any name for an instance profile. The SAP naming convention is:
Profile used by several instances
<SID>_<instance_name> (such as, DEV_DVEBMGS00)
Profile used by one instance
<SID>_<instance_name>_<hostname> (such as, DEV_DVEBMGS00_PNSFO36)
Default Profile
To assign the same parameter value for all application serversfor example, the name of the database host
or the computer where the message server is runningenter this value in the default profile. Although,
you may list any parameter, we recommend that you use the following values:
Parameter Definition Parameter Name in Profile
Name of the database host SAPDBHOST
Name of the update server rdisp/vbname
Name of the enqueue server rdisp/enqname
Name of the server for handling background processing events rdisp/btcname
Name of the computer on which the message server is running rdisp/msname
Name of the TCP service under which the message server can be reached rdisp/msserv
Name of the computer on which the SNA Gateway is running rdisp/sna_gateway
Name of the TCP service under which the SNA Gateway can be reached rdisp/sna_gw_service
You cannot choose a name for the default profile. It is always called DEFAULT.PFL.
Start Profile
When you start a R/ 3 instance on a host, the start profile defines which of the following R/ 3 services are
started, such as the message server, dialog, gateway, or enqueue processes. The SAP program startsap is
responsible for starting these service processes, and it uses a start profile to begin the startup process. To
start the same SAP service processes on several computers, you can use a single start profile. Each R/ 3
instance does not need to have its own start profile.
Processes that can be started include:
Application server
Message server
SNA Gateway
Unix only: System log send daemon System log receive daemon
Overviewing R/3 Profile Maintenance Tool
Process of Profile Maintenance
1998 SAP Labs, Inc. 245
Aside from the general profile parameters, other parameters include:
SAPSYSTEMNAME
name of the R/ 3 System
SAPSYSTEM
instance number
INSTANCE_NAME
name of the R/ 3 instance
Parameter names that are only permitted in a start profile are:
Execute_xx
This starts the operating system commands, which prepare the R/ 3 System to start. For example, you
can use this parameter to start the SAP related database or to set up links to executables on Unix
platforms.
Start_Program_xx
This starts a R/ 3 instance, for example, on an application server.
Stop_Program_xx
This starts an operating system command or SAP program after the R/ 3 instance was stopped, for
example, the halting or removal of shared memory areas that were used by the R/ 3 System.
The number xx (xx = 00-99) defines the execution sequence. The programs specified in Execute_parameter
begin before the programs listed in the Start_Program parameters. After the R/ 3 instance has been stopped,
the programs specified in the Stop_Program parameters are started.
Use the following SAP naming convention when choosing a start profile name:
Profile used by several instances
START_<instance_name> (such as, START_DVEBMGS00)
Profile used by one instance
START_<instance_name>_<hostname> (such as, START _DVEBMGS00_PNSFO36)
Process of Profile Maintenance
You should only edit the profiles from the R/ 3 System using the CCMS profile maintenance tool, not at the
O/ S level. This tool archives the profiles as operating system files and stores a reference copy in the
database. The database copy contains a reference character used to create the profiles at the operating
system level. This process is called activating a profile, that at the operating system level, only gets
overwritten if specified in the profile maintenance tool (the system prompts you to save a profile). At the
operating system level, the reverse procedure is called importing a profile into the database.
Overviewing R/3 Profile Maintenance Tool
Process of Profile Maintenance
246 1998 SAP Labs, Inc.
The following graphic shows the process of importing R/ 3 Profiles from a flat file to the R/ 3 System:
The R/ 3 profiles are automatically generated or updated at the operating system level when you:
First install a R/ 3 System
Upgrade to a new R/ 3 release
Add a new application server
Unfortunately, the installation program cannot save these profiles straight to the database. Therefore, you
must import the R/ 3 profiles before they can be edited by the profile maintenance tool. Two ways exist to
import profiles using the profile maintenance tool:
Importing R/ 3 profiles from all active application servers
You can import the default profile and all start and instance profiles used by the active instances. This
procedure is helpful after you have installed your R/ 3 System or a new R/ 3 release.
Importing individual profiles
This function should be used if a new application server has been installed, or a profile was modified
at the operating system level.
If you have imported the R/ 3 profiles, you can maintain the values of the profile parameters with three
different tools:
Administration data
Basic maintenance
Extended maintenance
These tools help edit and display profiles. Do not work with editors on the operating system level. You can
also use R/ 3 profile maintenance to work on profiles that belong to different application servers at the
same time.
When you modify and store a profile, the old status in the database is not overwritten. Instead, a separate
version with the changed values is created. The R/ 3 System allocates an individual number for each
Overviewing R/3 Profile Maintenance Tool
Process of Profile Maintenance
1998 SAP Labs, Inc. 247
profile version. Thus, the history of profile changes is stored in the database and each version can be
restored at any time.
After a modification, you can complete extensive verification checks of one or more profiles. These checks
include:
Making profile syntax checks
Spell-checking the parameter names
Semantic checks
These checks, for example, verify whether the value of a certain R/ 3 profile parameters is within the
allowed range of values of the parameters. The result of these checks appears in the form of a log, which
contains two message types: warnings and error messages.
The following graphic shows the activation process of a newly modified R/ 3 profile in the database with
flat file changes:
Changes do not take effect immediately in the associated R/ 3 instance. To activate the changes, you have
to activate the changed profile by creating a new profile file at the operating system level. Then stop and
restart the R/ 3 instance(s) for which you want the profile change to become effective.
Overviewing R/3 Profile Maintenance Tool
R/3 Profiles Definition
248 1998 SAP Labs, Inc.
R/3 Profiles Definition
System parameters are defined and stored:
In the coding
In the default profile
The default profile / usr/ sap/ SID/ SYS/ profile/ DEFAULT.PFL overwrites the settings from the
coding.
In the instance profile
The instance profile usr/ sap/ <SAPSID>/ SYS/ profile/ ... overwrites the settings in the coding and in
the default profile.
As of release 3.0E some parameters can be dynamically changed during system operation. Many
parameters do not normally require changes and are therefore defined only in the code. For this reason,
although the parameters exist, they may not be listed in the profile files.
If you change profile parameters, they only become active after the instance has been restarted. (Only on
Windows NT and AS/ 400, when a work process is restarted while the system is running, the new
parameters will be valid for this process. This is not valid for Unix.)
Parameter maintenance is done in the following fashion:
By editing the profile files, up to and including Release 2.2
Before making changes, make a backup copy. Changes must be documented. No tab characters may be
used.
With transaction RZ10 in Release 3.0
The profile file is activated when this is used. You are not allowed to edit the files on the operating
system level.
You can display the parameters as follows:
Call up the report RSPFPAR (using Transaction SA38) to display the parameters for the instance that
you are logged on to. (Report RSPARAM does the same, but RSPFPAR is more comfortable.) When
you double-click on the corresponding line the origin of the current value appears on screen.
Use Transaction TU02 to display the parameters for all the instances.
From Release 3.0, you can display the parameters in the profile maintenance (RZ10).
On the operating system level, you can display the parameters using:
sappfpar name=<SID> nr=<nn>
or
sappfpar pf=<full_path_of_profile>
The transaction AL11 (DIR_PROFILE) displays the profile files.
Documentation is available as follows:
On the documentation CD
Up to release 2.2*:
In the hypertext structure BC_SYSPROPAR (use transaction SO70)
Overviewing R/3 Profile Maintenance Tool
How Do I Maintain Profiles?
1998 SAP Labs, Inc. 249
As of release 3.0C:
Using transaction RZ11
In Basic and Extended Maintenance (transaction RZ10) using the F1 key
As of release 3.1G:
Run RSPFPAR to get a list of all active parameters (see above).
To display the parameter documentation, set the cursor to the corresponding line and click on the "?" icon
(or press the F1 key).
How Do I Maintain Profiles?
We divided the activities to maintain the R/ 3 profiles into two parts: basic and extended tasks. All of the
activities for these tasks are carried out with the profile maintenance tool.
To start this tool from the main screen,
choose Tools Administration
Computer Center Management System
Configuration Profile Maintenance.
Alternative:
Basic Tasks
The following items describe how to perform the basic tasks to maintain R/ 3 profiles:
Importing profiles of active servers
If you are using the profile maintenance tool for the first time, you need to import all the necessary R/ 3
profiles from all application servers.
Importing individual profiles
If a new application server has been installed or a profile was modified at the operating system level,
you must import the individual profiles.
Changing profile parameters
The R/ 3 profile parameters can be maintained in three ways:
Administration data
Maintain the name of the file where the profile should be activated.
Basic maintenance
Maintain the most important profile parameters.
Extended maintenance
Overviewing R/3 Profile Maintenance Tool
How Do I Maintain Profiles?
2410 1998 SAP Labs, Inc.
Creating, changing, or deleting entries for all profile parameters
Checking R/ 3 profiles
After you changed parameters in the profiles, you should:
- Perform syntax checks
- Spell-check the parameter names and semantic checks
Activating R/ 3 profiles
If a new version of a profile has been created and checked, activate the new version, so that a new
profile file is created at the operating system level.
Checking active parameters
When restarting the R/ 3 System, you should check whether the parameters have been correctly
changed.
Extended Tasks
This section describes the extended tasks used to maintain R/ 3 profiles:
Creating a profile
If a new profile is needed, you can manually create it.
Copying a profile
If a new profile is needed, you can copy an existing profile.
Deleting a profile
When a profile is not used anymore, you can delete it from the database and the corresponding profile
files from the operating system level.
Switching back to an older profile version
If an old version of a profile has to be activated, switch back by copying or deleting profiles.
Comparing a profile in the database with an active version
You can confirm whether a profile file has been manually changed at operating system level by
comparing the profile information in the database with the profile existing on the operating system.
Dynamic switching of profile parameters.
You can change and switch special R/ 3 profile parameters for instance profiles without restarting the
system.
Overviewing R/3 Profile Maintenance Tool
Hints and Questions
1998 SAP Labs, Inc. 2411
Hints and Questions
Useful hints for Profile Maintenance
The following useful hints for profile maintenance were compiled to help you to identify and resolve
problems:
Warning: Values are not allowed
When you maintain the system profiles with the CCMS tools with the transaction RZ10, the warningValues
are not allowed appears. It occurs only when parameters with numeric values are affected. The reason is
that the value to be set deviates from the default value for this parameter, or is not within the permissible
area as determined in the transaction RZ11.
Two alternatives exist to solve the problem:
Wrong typing of the value (warning makes sense and the value must be corrected)
Value makes sense (such as recommend by SAPs Earlywatch Service)
In the second case you can solve the problem by changing the default value or permissible area for this
parameter by using transaction RZ11 (see note 52744: RZ10 profile maintenance: Values are not allowed)
Changed Parameters become Not Active
If the changed system parameters become inactive, the most frequent causes are:
R/ 3 System has not been restarted
Profiles are used only during the startup process. Thus, changed system parameters are activated after
a restart. For a system with several instances, you have to restart only the instance for which you have
changed the parameters.
Profile has not been activated
If you maintain the profiles within CCMS with transaction RZ10, they are stored in the database.
During the startup process, profiles on operating system level are used. Thus, after maintaining
profiles within CCMS you also have to create a new version of the profile on operating system level.
Do this by activating the profile (see Activating the R/ 3 Profile Changes).
Frequently Asked Questions
Q1: Where are system parameters defined?
A1: System parameters are defined and stored:
In the coding.
In the default profile, where the default profile overwrites the setting from the coding.
In the instance profile, where the instance profile overwrites the settings in the coding and the default
profile.
As of release 3.0E, some parameters can be changed dynamically during system operation.
Overviewing R/3 Profile Maintenance Tool
Hints and Questions
2412 1998 SAP Labs, Inc.
Q2: Are all system parameters listed in the profiles?
A2: Many parameters do not normally require changes and are therefore defined only in the code. Thus
parameters exist that are not listed in the default profile or instance profile.
Q3: How can system parameters be displayed?
A3: You can display the parameters as follows:
Call up the report RSPFPAR using transaction SE38 to display the parameters for the instance on
which you are currently logged on. When you double-click on the corresponding line, the origin of the
current value appears.
Use transaction TU02 to display the active parameters.
On the operating system level, you can display the parameters using sappfpar.
Q4: Where can I find documentation?
A4: Documentation is available:
On the documentation CD.
Using transaction RZ11 (type in the parameter name, click on the Display button and the click on the
Documentation button.).
In basic or extended maintenance - transaction RZ10 - using the F1 key.
Q5: Should the profiles for each instance be defined individually, or is it better to have a common profile
of them?
A5: The instance profiles are managed centrally, stored in the directory:
Windows NT: \ \ <SAPGLOBALHOST>\ sapmnt\ <SAPSID>\ sys\ profile
Unix: / usr/ sap/ / <SAPSID>/ SYS/ profile
Therefore, several instances can access the same profile. In some cases, instance profiles must be
individually maintained, because each system needs individual settings of the system parameters. In
particular it applies:
If different hardware is used for the instances
If the applications are different (for example, FI on one instance and PP on another)
If different code pages are used (for example, West European, Cyrillic, or Japanese)
For the database server
If several systems have common system parameters settings, use a common profile. This gives you the
following advantages:
- Simplified maintenance
- Lower rate of errors
Overviewing R/3 Profile Maintenance Tool
Useful OSS Notes
1998 SAP Labs, Inc. 2413
Useful OSS Notes
Note # Description
31395 System parameters: Defined where? Displayed how?
21636 RAM extension: Which changes to profile?
39412 How many work processes to configure?
For further details refer to
R/3 System Administration Made Easy
Introducing R/3 Release 3.1x Architecture (Ch. 1)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Computer Center Management System R/3 System Administration
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Importing Profiles of Active Servers
Overview
1998 SAP Labs, Inc. 251
Chapter 25: Importing Profiles of Active Servers
Contents
Overview............................................................................................................................................................................................................251
Importing All R/3 Profiles from Active Servers ..............................................................................................................................................251
Viewing the Imported Profiles..........................................................................................................................................................................252
Overview
Importing the profiles of active servers is complicated during the post-installation process of a new R/ 3
System or when adding an application server. Profiles exist as flat files in your R/ 3 Server and are
imported into R/ 3s database so that they can be effectively maintained. The following step-by-step
procedure shows how to import these profiles.
Importing All R/3 Profiles from Active Servers
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Choose Utilities Import profiles
Of active servers.
After importing the profiles, they should always be maintained using this tool, not at the
operating system level.
1
2
Importing Profiles of Active Servers
Viewing the Imported Profiles
252 1998 SAP Labs, Inc.
The Display of Profile Check Log
screen appears after first importing
the R/ 3 profiles.
3. Scroll through the log to quickly
check for errors.
4. Click Back to return to the previous
Edit profiles screen.
Viewing the Imported Profiles
After importing all of the profiles from the file system level to the R/ 3 database, check them:
1. From Profile click the possible entries
button to display a list of all R/ 3
profiles.
3 4
1
Importing Profiles of Active Servers
Viewing the Imported Profiles
1998 SAP Labs, Inc. 253
The list of all imported R/ 3 profiles
to the database appears.
2. Choose the Profile name.
3. Click Enter to copy.
The Default, Instance, and Start profiles used by the R/ 3 instances are then imported. These profiles are
checked and a log appears. (The profile names in the database are taken from the corresponding file names
on the operating system.) When you have finished importing profiles, position the cursor in the Profile
field and select PF4. The names of the imported profiles will be displayed.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
2
3
Importing Individual Profiles
Overview
1998 SAP Labs, Inc. 261
Chapter 26: Importing Individual Profiles
Contents
Overview............................................................................................................................................................................................................261
Heres How.....................................................................................................................................................................................................261
Overview
The creation of an instance profile results in a new R/ 3 application server is added to your R/ 3 System. To
manage the new instance profile, you must import it.
Heres How
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Enter the profile name (in this
example, test_pro).
3. Click Create or choose Profile
Create.
3
1
2
Importing Individual Profiles
Heres How
262 1998 SAP Labs, Inc.
4. Enter a Short description of the
profile.
5. Specify the Administration Data (in
this example, the default values are
displayed).
6. Select the Profile type.
7. Click Copy.
8. After transferring the
administration data, click Import or
choose Profile Import.
4
5
7
8
6
Importing Individual Profiles
Heres How
1998 SAP Labs, Inc. 263
9. From the list, specify the operating
system file to which the profile
should be imported.
You can display all the profile files
in the global profile directory by
clicking the Possible entries icon.
10. Click Copy. (The message
/usr/sap/DEV/SYS/profile/DEV_DVE
BMGS00_pnsfo36 imported appears.)
11. To save the new profile, choose
Profile Save or simply click Save.
12. R/ 3 will ask if you want to activate
the profile. Click Yes to activate.
Otherwise, click No. (The message
Profile TEST_PRO [version 0000001]
saved and activated appears.)
9
10
11
12
Importing Individual Profiles
Heres How
264 1998 SAP Labs, Inc.
13. After reading the Caution dialog
window, click the Enter icon or
press Enter to continue.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
13
Changing a Profiles Parameters
Overview
1998 SAP Labs, Inc. 271
Chapter 27: Changing a Profiles Parameters
Contents
Overview............................................................................................................................................................................................................271
Changing Administration Data Parameters....................................................................................................................................................271
Changing Basic Maintenance Parameters......................................................................................................................................................274
Changing Extended Maintenance Parameters...............................................................................................................................................275
Overview
To edit individual R/ 3 profiles you have the following three tools:
Administration Data
Basic Maintenance
Extended Maintenance
Changing Administration Data Parameters
The Administrative Data tool enables you to quickly and conveniently edit parameters. The following
example shows how to change the Short description of a profile is provided in the procedures below.
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. From Profile use the possible entries
button.
2
1
Changing a Profiles Parameters
Changing Administration Data Parameters
272 1998 SAP Labs, Inc.
3. Double-click on the line of the
profile you wish to change (in this
example, DEFAULT).
4. Select the Administration data
button.
5. Click Change to alter its original
value.
From this screen, you can modify the
following administration data:
Short description of the profile
File name in which the profile
should be activated
Reference server for profile
parameter check
Profile type
6. After changing the data, click Copy.
(In this example, the Short
Description was changed.)
3
4
6
5
6
Changing a Profiles Parameters
Changing Administration Data Parameters
1998 SAP Labs, Inc. 273
7. To save the profile with changes,
click the Save icon or choose Profile
Save.
8. R/ 3 will ask if you want to activate
the profile. Click Yes, to activate.
Otherwise, click No. (The message
Profile DEFAULT [version 000002]
saved and activated appears.)
9. After you have read the Caution
dialog box, click Enter.
Remember, when changing a profile, R/ 3 automatically creates a new version. You can go to
a previous version by using the procedure explained in chapter 34, Switching Back to an Older
Version of a Profile.
7
8
9
Changing a Profiles Parameters
Changing Basic Maintenance Parameters
274 1998 SAP Labs, Inc.
Changing Basic Maintenance Parameters
The Basic maintenance tool enables you to quickly and conveniently edit parameters. The following
example shows you how to change the ABAP program buffer size.
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Choose the profile you wish to
modify from the Profile field (in this
example,
DEV_DVEBMGS00_PNSFO36).
3. Select the Basic maintenance button.
4. Click Change to alter its original
value.
From this screen, you can change the
following basic maintenance
information:
General data
Buffer and work processes
Number of work processes
5. In this example, the ABAP program
name buffer size has been changed
to 70,000 KB. You may use the
>>, >, <, << buttons to
change the parameters for any of
the listed items.
6. Click Copy or choose Profile
Copy.
5
6
2
3
4
1
Changing a Profiles Parameters
Changing Extended Maintenance Parameters
1998 SAP Labs, Inc. 275
7. Click the Save icon or choose Profile
Save.
The profile data is automatically
checked before you leave the Basic
maintenance screens. Any errors or
inconsistencies will be displayed.
8. R/ 3 will ask if you want to activate
the profile. Click Yes, to activate.
Otherwise, click No. (The message
Profile DEV_DVEBMGS00_
PNSFO36 [version 000002] saved and
activated appears.)
9. After you read the Caution dialog
box, click Enter.
Changing Extended Maintenance Parameters
The Extended maintenance tool enables you to maintain profiles on an individual parameter level. This
tool comprises an editor that creates, modifies, and deletes individual parameters. To change the system
default client follow the step-by-step procedure below.
7
8
9
Changing a Profiles Parameters
Changing Extended Maintenance Parameters
276 1998 SAP Labs, Inc.
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Choose the profile you want to
change from the Profile field (in this
example,
DEV_DVEBMGS00_PNSFO36).
3. Select the Extended maintenance
button.
4. Click Change to alter its original
value.
Because the list contains many
parameters, use the Find function.
(The system default client belongs to
the group login, therefore, we could
use login as the keyword for
searching purposes.)
5. Choose System List Find
Two colors indicate the values of parametersin this example black and red. Colors are used
for ease of viewing and do not indicate errors.
3
2
4
5
1
Changing a Profiles Parameters
Changing Extended Maintenance Parameters
1998 SAP Labs, Inc. 277
6. Enter login.
7. Click Find.
If parameters of the group login are
defined in the profile, then a pop-up
menu will list them. To replace a
parameter value, follow the remaining
steps:
8. Click on the line login/system_client.
9. Click the Position cursor button.
10. Change the indicated parameter to
the value you need.
11. Click Copy or choose Profile
Copy.
If the copy process is successful,
the message The changed profile was
transferred appears.
6
7
8
10
11
9
Changing a Profiles Parameters
Changing Extended Maintenance Parameters
278 1998 SAP Labs, Inc.
12. Click Back.
13. Click Save or choose Profile Save.
The profile data is checked
automatically before you leave the
Extended maintenance screens. Any
errors or inconsistencies will be
displayed.
14. R/ 3 will ask if you want to activate
the profile. Click Yes, to activate.
Otherwise, click No. (The message
Profile DEV_DVEBMGS00_
PNSFO36 [version 000003] saved and
activated appears.)
14
12
13
Changing a Profiles Parameters
Changing Extended Maintenance Parameters
1998 SAP Labs, Inc. 279
15. After you read the Caution dialog
box, click Enter.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
15
Checking Profiles
Overview
1998 SAP Labs, Inc. 281
Chapter 28: Checking Profiles
Contents
Overview............................................................................................................................................................................................................281
Heres How.....................................................................................................................................................................................................281
Overview
Before you leave either the Basic or Extended maintenance screens, the profile data is automatically
checked and errors or inconsistencies are displayed. Choose Profile Save to:
Check the profile for errors and inconsistencies
Check the consistency of all profiles involved in the switch between operation modes
Save profile data in the database
Activate a profile if corresponding profile files are created at the operating system level
Heres How
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
To check a single profile:
2. Click the possible entries button to
obtain the Profile name and Version.
3. Click Check or choose Profile
Check.
The message No errors in profile
DEFAULT [version 000002] appears.
3
2
1
Checking Profiles
Heres How
282 1998 SAP Labs, Inc.
CHECK RULES FOR PROFILE CLASSES
Parameter Class Check Rule
Integer value Value smaller than default value Error
Value larger than default by a factor of 10 Warning
Time value Value smaller than 0 Error
Permissible characters: 09
Boolean value Valid value set: 0, 1
ON, OFF
YES, NO
TRUE, FALSE
Other values Error
File directory Directory does not exist Warning
No write authorization Warning
File name File does not exist Error
TCP computer name Computer is not known to TCP Error
TCP service name Service name is not known to TCP Error
SAP server name Server name is not known to R/ 3 System Error
File mask Check is not possible
Strings Check is not possible
Cannot be changed by customer If particular parameters are changed by the customer Error
Special parameters If value does not contain a particular character string Error
Start profile If one program at least is not started Error
Parameters within a single profile are divided into classes, and a separate check rule exists for each class.
In addition to a single profile check, the R/ 3 System tests to see if all profiles are consistent with each
other. For example, all start profiles are checked to see whether exactly one message server has started.
Other features of checking R/ 3 profiles are:
All profiles of an active R/ 3 System (/nRZ10 Utilities Check all profiles Of active servers)
All profiles used for operation mode (/nRZ10 Utilities Check all profiles Of operation mode)
Checking Profiles
Heres How
1998 SAP Labs, Inc. 283
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Activating Profiles
Overview
1998 SAP Labs, Inc. 291
Chapter 29: Activating Profiles
Contents
Overview............................................................................................................................................................................................................291
Heres How.....................................................................................................................................................................................................291
Overview
Before using a newly created or modified profile, you must:
1. Activate the profile
2. Stop the R/ 3 System
3. Restart the R/ 3 System
The following step-by-step procedure will show you how to activate your most recently created profile.
Heres How
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Enter the Profile name and the most
recent Version of the profile to be
activated (in this example,
TEST_PRO is the Profile name and
000001 is the Version).
1
2
2
Activating Profiles
Heres How
292 1998 SAP Labs, Inc.
3. Choose Profile Activate.
The message Profile TEST_PRO
[version 000001] activated appears.
4. Click Enter to continue.
Once you have activated the profile, restart the R/ 3 System to use the new profile values.
Another information screen tells
you that to activate the new
changes, you need to restart the
application server.
5. Click Enter to exit.
An active profile that already exists in the R/ 3 System is automatically backed up, and is given the
extension .bak. You can copy and display this backup file even if the R/ 3 System is unavailable.
3
5
Activating Profiles
Heres How
1998 SAP Labs, Inc. 293
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Checking Active Profile Values
Overview
1998 SAP Labs, Inc. 301
Chapter 30: Checking Active Profile Values
Contents
Overview............................................................................................................................................................................................................301
Heres How.....................................................................................................................................................................................................301
Overview
One of the features of the R/ 3 Profile maintenance is to ensure that:
The parameters are valid R/ 3 parameters
The value of the parameter should fall into a defined range of value
The following steps show you how to check active profile value.
Heres How
To check the active profile values of an instance:
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Choose Goto Profile values Of a
server.
The message Choose an application
server appears.
1
2
Checking Active Profile Values
Heres How
302 1998 SAP Labs, Inc.
3. Double-click on the server name to
choose an application server.
A list appears, containing:
4. Parameter names in alphabetic
order.
5. Active values of the individual
parameters.
Scroll through the list.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
3
4 5
Creating a Profile
Overview
1998 SAP Labs, Inc. 311
Chapter 31: Creating a Profile
Contents
Overview............................................................................................................................................................................................................311
Heres How.....................................................................................................................................................................................................311
Overview
There are two ways to create new R/ 3 profiles. You can either manually create them or copy them from
another R/ 3 profile. This chapter shows you how to manually create a profile.
Heres How
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Enter the profile name you want to
create in the Profile field.
3. Click Create or choose Profile
Create.
1
2
3
Creating a Profile
Heres How
312 1998 SAP Labs, Inc.
4. Enter the name of the operating
system file, reference server, and
profile type, or accept the default
values.
5. Click Copy.
Adjust the parameter values:
6. Select the Basic maintenance or
Extended maintenance button (in this
example, the Basic maintenance
button has been selected).
7. Click Change.
4
5
6
7
Creating a Profile
Heres How
1998 SAP Labs, Inc. 313
8. Modify the parameters as needed
(in this example, the System name,
System number, and Instance name,
and the number of work processes
have been modified).
9. Click Enter (if any errors exist, an
error screen appears).
10. Click Copy or choose Profile
Copy.
11. To save the profile, choose Profile
Save.
The profile data is automatically
checked before leaving the
maintenance screens. Any errors or
inconsistencies will be displayed.
This example of an error screen
shows that R/ 3 has detected
incorrect parameter values (click
Yes to display the error or click No
to correct without display).
12. Click Yes to display the incorrect
value.
The message Invalid profile
parameters detected appears.
8
11
9
10
12
Creating a Profile
Heres How
314 1998 SAP Labs, Inc.
13. Scroll down and locate the error
message.
In this example, an error resulted
from a lower-than-acceptable
parameter value.
14. Enter the correct value.
15. Click Copy or choose Profile
Copy.
The message The changed profile was
transferred appears.
16. Click the Back icon.
13
14
15
16
Creating a Profile
Heres How
1998 SAP Labs, Inc. 315
17. An Activate profile dialog box asks if
you want to activate the profile.
Click Yes to activate. Otherwise,
click No.
The message Profile NEW_PRO
[version 000001] saved and activated
appears.
18. After you read the Caution dialog
box, click Enter.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ 360/ BC361/ BC362/ BC370)
17
18
Copying a Profile
Overview
1998 SAP Labs, Inc. 321
Chapter 32: Copying a Profile
Contents
Overview............................................................................................................................................................................................................321
Heres How.....................................................................................................................................................................................................321
Overview
Use the copy function to create a new profile with some, or all, of the features of another source profile.
Heres How
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Enter the Profile name.
3. Enter the Version.
4. Click Copy or choose Profile
Copy.
1
2
4
3
Copying a Profile
Heres How
322 1998 SAP Labs, Inc.
The Copy Profile screen with the
source profile name and version
and target profile name appears.
5. Enter the Profile name to be copied
(for example, DEV_NEW_PROFILE).
6. Click Copy.
A new version of
DEV_NEW_PROFILE will be
generated based on the profile
DEV_DVEBMGS00_DODGERS.
The message Profile
DEV_NEW_PROFILE [version
000001] was generated appears.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
5
6
Deleting a Profile
Overview
1998 SAP Labs, Inc. 331
Chapter 33: Deleting a Profile
Contents
Overview............................................................................................................................................................................................................331
Deleting a Single Profile...................................................................................................................................................................................331
Deleting All Versions of a Profile.....................................................................................................................................................................332
Preparing Profile Sample for Deletion.........................................................................................................................................................332
Deleting the Profiles ....................................................................................................................................................................................335
Overview
You can either delete single profiles or all versions of a profile.
Deleting a Single Profile
Deleting a single profile means deleting the latest version of a R/ 3 profile. The following step-by-step
procedure shows you how to delete the profile.
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Enter the Profile name and Version
of the profile you want to delete.
1
2
Deleting a Profile
Deleting All Versions of a Profile
332 1998 SAP Labs, Inc.
3. Choose Profile Delete
Individual profile.
4. Click Yes if you want to delete the
particular profile from the
database.
5. A dialog window appears and asks
if you want to delete the profile at
the operating system level. Click
Yes if you want to delete the
particular file; otherwise, click No.
The message Profile NEW_PRO
[version 000001 deleted appears.
Deleting All Versions of a Profile
Before deleting all versions of a R/ 3 profile, we will prepare an example of multiple versions of an R/ 3
Profile (in the following example, TEST_PRO). Later, we will delete all versions of profile TEST_PRO.
Preparing Profile Sample for Deletion
We will use TEST_PRO as an example of a multiple version profile. Currently, TEST_PRO has version 1
only. The following steps show you how to add another version of the profile.
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
3
4
5
1
Deleting a Profile
Deleting All Versions of a Profile
1998 SAP Labs, Inc. 333
2. From the Profile field, enter the
profile name you want to modify
or click the possible entries button to
list the profiles.
3. Click Change.
4. For this example, we will modify
the Short Description by adding
additional comments.
5. Click Copy.
2
4
5
3
Deleting a Profile
Deleting All Versions of a Profile
334 1998 SAP Labs, Inc.
6. Click Save or choose Profile Save
to save current modification.
7. Click Yes to activate the new
version.
The message Profile TEST_PRO
[version 000002] saved and activated
appears.
8. After reading the message, click
Enter.
6
7
8
Deleting a Profile
Deleting All Versions of a Profile
1998 SAP Labs, Inc. 335
Deleting the Profiles
To delete all versions of a profile:
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. From the Profile field, enter the
profile name you want to modify
or click the possible entries button to
list the profiles.
3. Choose Profile Delete All
versions Of a profile.
1
3
2
Deleting a Profile
Deleting All Versions of a Profile
336 1998 SAP Labs, Inc.
4. Click Yes if you want to delete all
versions of the profile.
5. A dialog window appears and asks
if you want to delete the profile
residing at the operating system
level. Click Yes if you want to
delete it; otherwise, click No.
The message All versions of profile
TEST_PRO deleted appears.
6. Click the possible entries button.
The deleted profile is no longer in
the list.
7. Click Cancel to continue.
4
5
6
7
Deleting a Profile
Deleting All Versions of a Profile
1998 SAP Labs, Inc. 337
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Switching Back to an Older Version of a Profile
Overview
1998 SAP Labs, Inc. 341
Chapter 34: Switching Back to an Older Version of a Profile
Contents
Overview............................................................................................................................................................................................................341
Overview
To revert to an older version of the R/ 3 profile:
Copy the older version and activate it to make it the current version (see chapter 32, Copying a Profile).
Delete the current profile version(s) up to the older version that you want to use (see chapter 33,
Deleting a Profile).
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Comparing a Profile in a Database with an Active Profile
Overview
1998 SAP Labs, Inc. 351
Chapter 35: Comparing a Profile in a Database with an Active Profile
Contents
Overview............................................................................................................................................................................................................351
Heres How.....................................................................................................................................................................................................351
Overview
You can compare two R/ 3 profiles to check their similarities or differences. The following steps show you
how to compare a profile in the database with a file in the operating system.
Heres How
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. From the Profile field, enter the
profile name you want to compare
or click the possible entries button to
list the profiles.
1
2
Comparing a Profile in a Database with an Active Profile
Heres How
352 1998 SAP Labs, Inc.
3. Choose Profile Comparison
Profile in database With active
profile.
If any discrepancies exist, a log is
displayed. Otherwise, the message
Profile data in database and active
profile are consistent appears.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
3
Dynamic Switching of Profile Parameters
Overview
1998 SAP Labs, Inc. 361
Chapter 36: Dynamic Switching of Profile Parameters
Contents
Overview............................................................................................................................................................................................................361
Heres How.....................................................................................................................................................................................................361
Overview
As of R/ 3 Release 3.0E, it is possible to dynamically switch some of the parameters. This step means that
changes to specific parameters take effect, without having to restart the application server.
Heres How
1. Choose Tools Administration
Computer Center Management
System Configuration Profile
Maintenance.
Alternative:
2. Enter the Profile name and Version
in the appropriate fields (in this
example, the Profile name is
DEV_DVEBMGS00_PNSFO36; the
Version is 000003).
Click the possible entries button to
display a list of profiles.
1
2
Dynamic Switching of Profile Parameters
Heres How
362 1998 SAP Labs, Inc.
3. Choose Profile Dyn. switching
Display parameters.
The list of switchable memory
management parameters appears.
4. Change the relevant profile
parameters using extended
maintenance (as described in
chapter 27) and save these
parameters.
5. From the profile maintenance main
screen, choose Profile Dyn.
switching Execute or click the
Switch parameter.
6. From the list of active application
servers, select the checkbox of the
application server.
7. Click Continue.
3
4
5
6
7
Dynamic Switching of Profile Parameters
Heres How
1998 SAP Labs, Inc. 363
8. Click the Back icon to return to the
R/ 3 Profile Maintenance main
screen.
The profile can be used
immediately after the change. You
need not restart the system. At the
end, a parameter switching log
appears.
For further details refer to
R/3 System Administration Made Easy
Overviewing R/3 Profile Maintenance Tool (Ch. 24)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Configuration
R/3 System Online Help
Online Documentation Basis Components System Administration Computing Center
Management System R/3 System Administration Profiles
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
8
Overviewing System Administration
Overview
1998 SAP Labs, Inc. 621
Chapter 62: Overviewing System Administration
Contents
Overview............................................................................................................................................................................................................621
Introduction to Starting and Stopping the R/3 System and Database.........................................................................................................621
Overview
A R/ 3 System consists of two instances: a R/3 instance and database instance. Both instances must be started
for the system to be active.
Introduction to Starting and Stopping the R/3 System and Database
Here are several possible methods to start and stop the instances:
SAP Database Administration (SAPDBA)
is a utility that starts from the
command prompt. SAPDBA executes
SQL statements to start and stop the
System.
SAP Service Manager is a Windows NT
application.
Overviewing System Administration
Introduction to Starting and Stopping the R/3 System and Database
622 1998 SAP Labs, Inc.
SAP Executables are commands that can
be used in batch files or other scripts.
startsap R3
stopsap R3
startsap DB
stopsap DB
Computing Center Management System
(CCMS) stops the Central R/ 3 instance
from within the System or starts and
stops application instances if you are
running multiple application servers.
The following table shows which instance each method is able to start or stop (that is, default status):
SAPDBA Service Manager SAP Executables CCMS
Start Database X X X
Stop Database X X
Start R/ 3 X X X (app. instances)
Stop R/ 3 X X X
The R/ 3 instance and the database instance can be started and stopped separately with two exceptions:
The R/ 3 instance cannot begin unless the database instance has been started.
The database instance cannot be stopped unless the R/ 3 instance has been stopped.
Overviewing System Administration
Introduction to Starting and Stopping the R/3 System and Database
1998 SAP Labs, Inc. 623
For further details refer to
R/3 System Administration Made Easy
Introducing R/3 Release 3.1x Architecture (Ch. 1)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Administration
R/3 System Online Help
Online Documentation CD Basis Components Database Administration
Basis Courses
Technical Core Competence (BC310)
Starting and Stopping the R/3 System Using CCMS
Overview
1998 SAP Labs, Inc. 641
Chapter 64: Starting and Stopping the R/3 System Using CCMS
Contents
Overview............................................................................................................................................................................................................641
Stopping R/3 Using CCMS................................................................................................................................................................................641
Starting R/3 With the SAP Service Manager...................................................................................................................................................642
Overview
This chapter shows you how to stop the R/ 3 System by using the Computing Center Management System
(CCMS) and then how to re-start the R/ 3 System by using the SAP Service Manager.
Stopping R/3 Using CCMS
1. Choose Tools Administration
Computing Center Management
system.
Alternative:
2. Choose Control System Monitor.
3. Select the instance you want to stop
by clicking on its graphic in the
Display area.
1
2
3
Starting and Stopping the R/3 System Using CCMS
Starting R/3 With the SAP Service Manager
642 1998 SAP Labs, Inc.
4. Choose Control Stop SAP
Instance.
To start an R/ 3 instance, choose Control
Start SAP Instance.
5. Click Yes.
6. This message indicates that the R/ 3
System has been shutdown. Since
we do not want to reconnect at this
time, click No.
Since the R/ 3 System and the
application instance are on a
centralized instance, the shutdown
process will end the current login.
Starting R/3 With the SAP Service Manager
1. To restart the service, click the
Windows NT Start button and
choose Programs SAP R3 SAP
Service Manager for DEV_00.
1
5
6
4
Starting and Stopping the R/3 System Using CCMS
Starting R/3 With the SAP Service Manager
1998 SAP Labs, Inc. 643
2. Click Start.
Wait until all the indicator lights
turn from gray to green. The
System is not restarted until this
happens.
3. Choose File Exit to close the
window.
For further details refer to
R/3 System Administration Made Easy
Starting and Stopping the R/3 System Using the SAP Service Manager (Ch. 63)
Diagnosing the R/3 System Startup (Ch. 65)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Administration Startup and
Shutdown How to Start and Stop an R/3 Instance Starting and
Stopping the R/3 Instance
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS R/3 System
Administration Starting and Stopping the R/3 System Starting and
Stopping Instances
Basis Courses
Technical Core Competence (BC310/ BC314)
2
Monitoring Work Processes
Overview
1998 SAP Labs, Inc. 661
Chapter 66: Monitoring Work Processes
Contents
Overview............................................................................................................................................................................................................661
Heres How.........................................................................................................................................................................................................661
Useful OSS Notes..............................................................................................................................................................................................664
Overview
The Process Overview screen displays detailed information to help you monitor system work processes and
fine-tune performance. Displayed information includes:
The number of work processes
Programs being run by the work process
Process and error status
Amount of CPU time used by the process
Heres How...
1. Choose Tools Administration
Monitoring System monitoring
Process overview.
Alternative:
2. Click CPU to view the time usage
of each work process.
1
2
Monitoring Work Processes
Heres How...
662 1998 SAP Labs, Inc.
The CPU time usage of each work
process appears.
3. To view detailed information on a
process in this list, position the
cursor in the entry line of the
process. (In this example, the first
process in the list has been chosen.)
4. Click Detail info.
An activity snapshot of the instance is available with the Process Monitor. This is a useful tool for
getting a quick overview of the instance status.
Field Descript ion
No. Work Process number
Ty. Type of service
PID OS PID (Process ID) number
Status Current Action
Cause Cause ID
Start Status of work process
Err Number of detected Errors in the work process
Sem Semaphore resource being used (see OS monitor for further information)
CPU CPU accumulation
Time Time in process accumulation
Program Name of the ABAP running
4
3
Monitoring Work Processes
Heres How...
1998 SAP Labs, Inc. 663
5. Use the Page-up and Page-down
buttons to scroll the screen for
more information.
The CPU time field allows you to
monitor how much activity has been
allocated to a particular work process.
5
5
Monitoring Work Processes
Useful OSS Notes
664 1998 SAP Labs, Inc.
Useful OSS Notes
Note # Description
42074 Using the R/ 3 dispatcher monitor dpmon
For further details refer to
R/3 System Online Help
Online Documentation CD Basis Components System Administration System Services Tools for
Monitoring the Systems Displaying and Controlling Work Processes
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Viewing Transaction Codes
Overview
1998 SAP Labs, Inc. 671
Chapter 67: Viewing Transaction Codes
Contents
Overview............................................................................................................................................................................................................671
Finding the Transaction Code for the Current Screen ..................................................................................................................................671
Overview
Menu paths and transaction codes are two ways to get to a desired screen within the R/ 3 System. While
following a menu path is generally more intuitive, it is slower than using a transaction code. To get to a
desired screen quickly with a transaction code, simply follow the step-by-step procedure below.
Finding the Transaction Code for the Current Screen
1. To view the transaction code of any
screen, from that screen choose
System Status.
2. The Transaction field found in SAP
data will show you how to quickly
get to the same screen in the future.
Enter /n before the transaction code to
go from one screen to another. For
example, if you are in the User
Maintenance screen and want to send a
system message, simply enter /nSM02
in the Command Field. You will go
directly to the System Message window
without having to first exit the User
Maintenance window.
2
1
Viewing Transaction Codes
Finding the Transaction Code for the Current Screen
672 1998 SAP Labs, Inc.
Other information found in the
Syst em St at us Window:
1. License Expirat ion: The date your
user license expires. Note that the
date is in the American format
(Month/ Day/ Year). If the license
has not been applied for yet, this
screen will be blank.
2. Node Name: This is equivalent to
your Host Name.
3. Dat abase Name: This is equivalent
to the System ID.
For further details refer to
R/3 System Administration Made Easy
Locking and Unlocking Transaction Codes (Ch. 68)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Administration
R/3 System Online Help
Online Documentation CD Basis Components System Administration System Services Utilities
Basis Courses
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
1
2
3
Locking and Unlocking Transaction Codes
Overview
1998 SAP Labs, Inc. 681
Chapter 68: Locking and Unlocking Transaction Codes
Contents
Overview............................................................................................................................................................................................................681
Locking a Transaction Code............................................................................................................................................................................681
Unlocking a Transaction Code ........................................................................................................................................................................683
Overview
Locking a transaction code immediately prevents users from using the function represented by the
transaction. For example, locking transaction SA38 (ABAP/4 Reporting) would prevent users from running
ABAP/4 reports from the System menu.
Locking a Transaction Code
1. To view a list of all of the
transaction codes, choose Tools
Administration Administration
Tcode administration.
Alternative:
2. Locate the transaction code you
want to lock.
If you are looking for a particular
Transaction Code, you can search for it
using a wild card. For example, enter
SE* to display all transaction codes
starting with SE.
1
2
Locking and Unlocking Transaction Codes
Locking a Transaction Code
682 1998 SAP Labs, Inc.
3. Position the cursor on the
transaction code you want to lock
(in this example, SE01).
4. Choose Transaction code
Lock/unlock. Or select the Locked
checkbox and click the Enter icon.
5. The checkmark in the Locked
checkbox indicates that the
transaction code is locked.
6. To verify that the transaction code
has been locked, try to run the
transaction by entering it in the
Command field.
A dialog box informs you that the
transaction has been locked.
7. Click OK.
3
4
5
6
7
Locking and Unlocking Transaction Codes
Unlocking a Transaction Code
1998 SAP Labs, Inc. 683
Unlocking a Transaction Code
1. Enter the transaction /nSM01.
2. Locate the transaction you want to
unlock (in this example, SE01).
3. Position the cursor on the
transaction you want to unlock.
4. Choose Transaction Code
Lock/unlock.
1
2
3
4
Locking and Unlocking Transaction Codes
Unlocking a Transaction Code
684 1998 SAP Labs, Inc.
5. To verify that the transaction has
been unlocked, run the transaction.
The transaction code will now
properly execute (in this example,
transaction /nSE01 has returned us
to the Transport System window).
For further details refer to
R/3 System Administration Made Easy
Viewing Transaction Codes (Ch. 67)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Administration
R/3 System Online Help
Online Documentation CD Basis Components System Administration
5
Monitoring System Updates
Overview
1998 SAP Labs, Inc. 691
Chapter 69: Monitoring System Updates
Contents
Overview............................................................................................................................................................................................................691
Producing an Update Error as an Example ....................................................................................................................................................691
Monitoring a Flawed Update Process .............................................................................................................................................................694
Update Components and U1 and U2 Updates................................................................................................................................................695
Useful OSS Notes..............................................................................................................................................................................................697
Overview
The R/ 3 System provides a utility that monitors updates made to your system and ensures that it is
working normally. The Updating process records changes made by users in the systems database. This
utility provides a comprehensive set of tools which analyze and correct problems that can occur during an
update.
This utility enables you to:
Activate and deactivate system-wide updating
Display and debug update records that caused an abnormal termination in an update task, or that have
not yet been processed
Reprocess an update record that caused an abnormal termination (a test mode is also available for
repeating an update without making any changes to the database)
Display the data in an update record that abnormally terminated, so that the update can be manually
repeated
Manually process the unprocessed update records that accumulated while updating was stopped
Manually process a particular unprocessed update record or set of records (you can further select from
U1 (critical data) or U2 (statistics) update records)
Delete update records
Display and reset update statistics
Producing an Update Error as an Example
The following example shows you a Duplicate Key problem that is encountered during an upgrade. This
example is for illustration purposes only. It is not recommended that you do it in your system.
By inserting a Duplicate Key in this example, we expect the R/ 3 System to encounter problems during the
update process.
Monitoring System Updates
Producing an Update Error as an Example
692 1998 SAP Labs, Inc.
1. To execute the ABAP program
VBTST300, enter the transaction
/nSE38.
2. Enter VBTST300 into the Program
field.
3. Click Execute.
1
2
3
Monitoring System Updates
Producing an Update Error as an Example
1998 SAP Labs, Inc. 693
By default, the following
parameters and their values are
displayed.
4. From the Operation field, change
the value U to I, so that Duplicate
Key problems are produced during
the update process.
5. Click Execute.
This screen shows the result of the
execution.
4
5
Monitoring System Updates
Monitoring a Flawed Update Process
694 1998 SAP Labs, Inc.
Monitoring a Flawed Update Process
1. To go to the Update Records: Main
Menu choose Tools
Administration Monitoring
Update.
Alternative:
2. By default, the current Client
number is displayed (in this
example, 001).
3. The current User name is also
displayed (in this example, WLEE).
4. Select the Status of the transaction
(in this example, All).
5. Click Enter.
Update requests can be selected and displayed by means of their Status. Choose the following
options from the Status menu:
Terminated: Displays all canceled requests
To be updated: Displays all update requests not yet executed.
V1: Displays primary update status
V2: Displays secondary update status
All: Displays all requests, whether canceled, pending, or in progress.
1
2
3
4
5
Monitoring System Updates
Update Components and V1 and V2 Updates
1998 SAP Labs, Inc. 695
Update Components and V1 and V2 Updates
In the R/ 3 System, the processing of an update record, along with the execution of the database changes
can be broken down into several parts. These parts describe the update components. By further breaking the
update process down into several smaller parts, it is possible to organize update operations along object-
oriented lines, with one component assuming responsibility for the changes made to one data object.
A distinction should be made between primary (V1) and secondary (V2) update components.
Differentiating between update components based on priority lets the system process critical database
changes ahead of less-critical changes. Critical (or primary) changes are those that have control functions
in the R/ 3 System, such as the placement of an order or a change in the inventory of a material. Some less-
critical secondary changes include purely statistical updates, such as the calculation of results.
Since primary database changes need to be done quickly, these changes are assigned to primary
transaction components that generate updates. Secondary database operations, which are not as time-
critical, are declared secondary components. Therefore, the dispatcher attaches a lower priority to these
operations when assigning update requests to update work processes.
All of the primary components of an update must be processed before the processing of secondary
components.
Both the primary and the secondary components are processed sequentially in a single application server.
Each cluster of components is processed in a single work process. If no V2 update processes (work
processes dedicated to processing V2 update components) are available, the V2 components are processed
by a V1 update process.
1. This screen indicates an Error has
occurred while entering the
transaction /nSE38 by user WLEE.
2. Click Update modules.
A message from the SAP office
appears.
1
2
Monitoring System Updates
Update Components and V1 and V2 Updates
696 1998 SAP Labs, Inc.
3. Select the module name (in this
example, TH_VB_TEST_01) by
clicking once on its line.
4. Click Update status.
5. The popup window indicates that
the Update process was terminated;
its error message is ABAP/4
processor: RAISE EXCEPTION.
6. Click ABAP/4 short dump to view
more detailed information.
The ABAP/4 dump screen appears.
7. Click the Page-Down button to view
other error messages.
3
4
5
6
7
Monitoring System Updates
Useful OSS Notes
1998 SAP Labs, Inc. 697
Useful OSS Notes
Note # Description
25801 New work process type UP2
For further details refer to
R/3 System Administration Made Easy
Overviewing System Administration (Ch. 62)
R/3 Basis Knowledge Products
System Management CD System Services The System Log Viewing and Retrieving a Dump
Analysis
R/3 System Online Help
Online Documentation CD Basis Components System Services Managing Update Records
Basis Courses
Advanced R/ 3 Administration (BC305)
Viewing the Dump Analysis
Overview
1998 SAP Labs, Inc. 701
Chapter 70: Viewing the Dump Analysis
Contents
Overview............................................................................................................................................................................................................701
Heres How.....................................................................................................................................................................................................701
Overview
Dump Analysis is an extensive list of information designed to help a user quickly pinpoint and resolve
program errors.
The ABAP/4 Development Workbench issues a short dump when a report or transaction is terminated
because of a serious error. The system records the error in the system log and writes a snapshot of the
program at the time of its termination to a special database table called SNAP. The following step-by-step
procedure shows you how to view the Dump Analysis to get more information about the nature of the
error(s).
Heres How
1. Choose Tool Administration
Monitoring Dump analysis.
Alternative:
2. Choose Edit Display list or click
the display list icon.
1
2
2
Viewing the Dump Analysis
Heres How
702 1998 SAP Labs, Inc.
3. Place the cursor in the line of the
dump you wish to view.
4. Choose Short dump Dump
analysis.
5. Choose Goto Overview.
6. This ABAP/4 Short Dump List
overview screen allows you to
analyze the problem based on the
sections of the dump. You can
double-click on any of these
sections to display information
about the nature of the error(s).
3
4
5
6
Viewing the Dump Analysis
Heres How
1998 SAP Labs, Inc. 703
For further details refer to
R/3 System Administration Made Easy
Overviewing System Administration (Ch. 62)
R/3 Basis Knowledge Products
System Management CD Reference Implementation System Management
R/3 System Online Help
Online Documentation CD Basis Components System Administration System Services The
System Log Dump Analysis
Basis Courses
Advanced R/ 3 Administration (BC305)
Overviewing R/3 System Workload and Buffer Performance Monitor
Overview
1998 SAP Labs, Inc. 761
Chapter 76: Overviewing R/3 System Workload and Buffer Performance
Monitor
Contents
Overview............................................................................................................................................................................................................762
Workload Monitor..............................................................................................................................................................................................762
What Can You Check with the Workload Monitor? .....................................................................................................................................762
Using the Workload Monitor ........................................................................................................................................................................763
Buffers in the R/3 System.................................................................................................................................................................................763
Client Cache................................................................................................................................................................................................763
Pool .............................................................................................................................................................................................................764
SAP Configuration Check.................................................................................................................................................................................764
Useful OSS Notes..............................................................................................................................................................................................764
Activity
Tables/Indices
Global
Alerts Workload Setup/Buffers
Local
Remote
Network
Operating System
Exceptions Analyses
Statistics Records
Buffers
Calls
Parameter Changes
Activity
System Configuration
Parameter Changes
Activity
System Configuration
Parameter Changes
LAN Check with ping
Network Monitor
Exclusive Lockwaits
Parameter Changes
System Log
DUMP Analyses
SAP-Directories
Active Users
Except/User
Performance Monitoring
SAP System
Database System
Network Monitor
Global
Operating System
File System
Call Statistics
Current Workload
Local
Operating System
File System
Remote
Database
Processes
Instances
Users, local
Users, global
Download Statistics
Performance Report
SAPOSCOL Destination
This section contains the System Performance layout and recommendations to ensure optimal
performance of your system. You should consider all possible factors before changing any of
the parameters. The procedures described in this section do not replace the EarlyWatch Service
that all R/ 3 customers should use.
Overviewing R/3 System Workload and Buffer Performance Monitor
Overview
762 1998 SAP Labs, Inc.
Overview
The R/ 3 buffers frequently store user data and make this data available to the local application server
instance. This process helps reduce access and workload on the database server, which does not need to be
repeatedly accessed to obtain the same information. It also reduces network traffic, improving system
performance.
Buffered data includes:
ABAP/ 4 programs
Screens
ABAP/ 4 Dictionary data
Company-specific data, which typically remains unchanged during system operation
You can change, or tune, buffer size to optimize performance for a particular hardware configuration.
Since many interdependencies must be considered when changing buffer sizes, this is not a
straightforward task.
You can also use table buffering to fine-tune applications which means that some or all of the contents of
frequently changed tables can be held in local buffers.
Workload Monitor
The R/ 3 Workload Monitor provides all the functionality necessary to monitor service levels provided to
the end users. This monitor is also used to analyze bottlenecks. When reviewing system performance, you
should normally start by analyzing the workload statistics. You can analyze workload statistics for the
server you are working on or all other servers. You can also use the Workload Monitor to find out how the
workload is distributed over the servers and transactions. Furthermore, you can display the totals for all
servers and compare the performance of individual servers over specified time periods.
What Can You Check with the Workload Monitor?
You can display views of the R/ 3 statistics data such as:
Workload for today or a recent period
Daily statistics records
Daily monitor response times
Performance history for recent periods for all servers or users
Performance history periods compared
You can also display detailed information on response times and consumption on any application server
in your R/ 3 System.
Overviewing R/3 System Workload and Buffer Performance Monitor
Buffers in the R/3 System
1998 SAP Labs, Inc. 763
Using the Workload Monitor
You can use the Workload Monitor to display the:
Number of configured R/ 3 instances
Services supported by the R/ 3 instances
Number of users working on the different instances
Most frequently used transactions
Response time distribution
Differences between the response times for the different instances
Buffers in the R/3 System
The R/ 3 System has a modular software client/ server architecture. The R/ 3 System can have a three-tier
architecture consisting of one database server, one or more application servers and many presentation
servers, or a two-tier architecture consisting of one machine to support the database and application
server, with several presentation servers.
Client Cache
Each R/ 3 instance (application server) has its own buffers. These buffers are also known as client caches
because they cache the customers programs in memory. The R/ 3 buffers are allocated in memory areas
local to the work process and in individual shared memory areas accessible by all the work processes.
These memory areas are executed for the application server.
Overviewing R/3 System Workload and Buffer Performance Monitor
SAP Configuration Check
764 1998 SAP Labs, Inc.
Some of the many buffers:
Program buffer This buffer occupies a whole shared memory segment.
Generic buffer This buffer is held in a shared memory pool. All work processes can access this
pool.
Screen buffer These are the local work process buffers. Only one work process may
Roll area access these buffers at a time.
Pool
Some SAP shared memory segments are grouped into one shared memory segment known as a pool. This
grouping is done to meet the operating system limits on the number of shared memory allocations per
process. In most operating systems, you can allocate as many shared memory segments as required. The
limits depend on the kernel configuration.
SAP Configuration Check
Poor configuration of the R/ 3 System can cause general performance degradation. Examples of poor
configurations include inefficient workload distributions of the different SAP services, or untuned setups
of SAP instances.
Useful OSS Notes
Note # Description
71346 Collective note: Monitoring: ST04, DB02, ST10, ST03
45580 How are syslog files deleted?
33576 Memory Management (from Release 3.0C, Unix and NT)
23863 MEMORY MANAGEMENT 3.0
15374 Checklist: Performance analysis
11886 Central SysLog cut off
Overviewing R/3 System Workload and Buffer Performance Monitor
Useful OSS Notes
1998 SAP Labs, Inc. 765
For further details refer to
R/3 System Administration Made Easy
All chapters about R/ 3 System Workload and Buffer Performance Monitor (Ch. 7681)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools SAP System
R/3 System Online Help
Online Documentation CD Computer Center Management System CCMS Monitors Buffer
Monitor
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Analyzing the R/3 System Workload
Overview
1998 SAP Labs, Inc. 771
Chapter 77: Analyzing the R/3 System Workload
Contents
Overview............................................................................................................................................................................................................771
Heres How.....................................................................................................................................................................................................772
Reviewing the Top 40 Response Times..........................................................................................................................................................777
Reviewing the Transaction Profile ..................................................................................................................................................................778
Overview
When analyzing system performance, you should review the workload statistics. You can analyze
workload statistics for the server you are working on, or all the servers. Use the Workload Monitor to find
out how the workload statistics are distributed over the servers and transactions, to display the totals for
all servers, and to compare the performance of individual servers over specified time periods.
CPU Time
Presentation
Server
Roll
in
Roll
out
Load
Time
Process Time
Wait
Time
DB Time
Dispatch Time
Response Time
Application Server Database Server
N
e
t
w
o
r
k
N
e
t
w
o
r
k
Analyzing the R/3 System Workload
Heres How
772 1998 SAP Labs, Inc.
Review the following statistic definitions before analyzing your R/ 3 workload:
Definition Description
Average response time Response time is measured from the time a work process is instructed by the
dispatcher to perform the execution to the time the result is returned to the
SAPgui. The response time between the SAPgui and the dispatcher is not
included in this value.
Average wait time The amount of time an unprocessed dialog step waits in the dispatcher queue for
a free work process. A high server workload could produce higher wait times.
Average CPU time CPU time used in the work process.
Average load time The amount of time needed to load and generate objects such as ABAP/ 4 source
code and screen information from a database.
Database calls The number of parsed requests sent to the database.
Database requests The number of logical ABAP/ 4 requests for data in the database. These requests
are passed through the SAP DB interface and parsed into individual database
calls. Take note of the proportion of database calls to database requests. If access
to information in a table is buffered in the SAP buffers, database calls to the
database server are not needed. Therefore, the ratio of calls/ requests gives an
overall indication as to the efficiency of table buffering. A good ratio would be
1:10.
Dispatch time The amount of time occupied in the work process. (Response time minus Wait
time.)
Average DB request
time
The logical database request time required for a dialog step. The time depends
on the CPU capacity of the database server, network server and buffering, and
on the input/ output capabilities of the database server.
Average roll ins Average processing time for roll ins
Average roll outs Average processing time for roll outs
Heres How
1. To go to the SAP R/3 CCMS
Performance Monitoring menu,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
1
Analyzing the R/3 System Workload
Heres How
1998 SAP Labs, Inc. 773
2. To view the Workload Analysis, from
the Performance Monitoring
window, choose Workload
Analysis.
Alternative:
The only application server for this
example is dodgers.
3. Click Choose for analysis.
4. Click the server name once to select
an application server (in this
example, pnsfo36).
5. Click the Enter icon.
2
3
4
5
Analyzing the R/3 System Workload
Heres How
774 1998 SAP Labs, Inc.
6. Select a time period. You can
choose daily, weekly, or monthly
statistics. From this screen you can
also compare the performance
development of a day, a week, and
a month for specific time periods or
for specific servers. (In this
example, Previous weeks has been
selected.)
7. Click the Enter icon.
8. Double-click on one of the weeks
listed to select the time period.
6
7
8
Analyzing the R/3 System Workload
Heres How
1998 SAP Labs, Inc. 775
The following is an example of the workload overview of a R/ 3 Server:
9. The Average Response Time is only for the application server. It has the value of 313.7 ms (= 0.3 second).
The Average Response Time of most transactions is approximately less than 2 seconds.
10. The Average CPU Time is 194.2 ms (= 61.9% of the Average Response Time) which is higher than the
normal value. CPU intensive tasks have occurred during the time interval. The Average CPU Time
should be approximately 40% of the Average Response Time. If it is above 40%, the problem may be
one of the following:
Input/ output (I/ O) bottleneck
Network problem
Slow or old CPU speed
Too much swapping
Wrong allocation of I/ O intensive files, such as
- Swap files
- Oracle online redo log files
9-13
14-17
18
19
Analyzing the R/3 System Workload
Heres How
776 1998 SAP Labs, Inc.
- Oracle offline redo log files
- Oracle data files
11. The Average Wait Time is 6.9 ms (= 2.2% of the Average Response Time) which is a little bit high. The
Average Wait Time should be less than 1% of the Average Response Time. (A high server workload can
produce higher wait times.) If it is above 1%, there may not be enough work processes, or work
processes are too busy.
12. The Average Load Time is 18.7 ms (= 5.96% of the Average Response Time) which is normal. Load Time
normally represents the time for loading and generating ABAP/ 4 source code and screen information
from a database. The Average Load Time should be less than 10% of the Average Response Time. If it is
above 10%, there may be missing indices, or R/ 3 buffers are too small.
13. The Average Database Request time is 95.8 ms (= 30.5% of the Average Response Time) which is normal.
Average Database request time should be around 40% of average response time. If it is above 40%,
there may be missing indices, too many extents, database CPU bound, or database memory bound.
The Operating System affects approximately 10% of the above values.
Database Calls are the number of parsed requests sent to a database. There have been 159,892 calls in this
example since the R/ 3 System started up.
14. Database Requests are the number of logical ABAP/ 4 requests for data in the database. These requests
are passed through the SAP database interface and parsed into individual database calls. Take note of
the proportion of database calls to database requests. If access to information in a table is buffered in
the SAP buffers, database calls to the database server are not needed. There are 250,137 requests that
are divided into three kinds of requests:
Direct reads
Sequential reads
Changes
15. The time of Direct Reads for each Database Request is 63,774 ms, which is too high. The normal value
should be less than 10 ms.
16. The time of Sequential Reads for each Database Request is 16.2 ms, which is a little too high. The normal
value should be less than 10 ms.
17. The time of Changes and Commits for each Database Request is 10.9 ms, which is normal because this
value should be less than 25 ms.
Note that the R/ 3 System in this example has been used to import a whole client from another R/ 3
System, and therefore there are many read and write activities. These values are not indicative of a
correctly configured and tuned R/ 3 System.
18. Select Dialog or Background to switch between statistics.
From the Workload Monitor, you can display further statistics for the server(s) and the selected time
interval. These statistics help you pinpoint which transactions have the highest resource consumption.
Analyzing the R/3 System Workload
Reviewing the Top 40 Response Times
1998 SAP Labs, Inc. 777
19. Click Top Time to view the top 40 response times.
Reviewing the Top 40 Response Times
Points of interest to analyze are the:
Programs which always have high response times
Number of sessions the program is using
Number of KB of information transferred
Possibility of starting the program at another time (for example, at night)
The following is an example of the top 40 response time statistics of a R/ 3 System:
1. In this example, program RSCOLL00 took significant amount of response time that includes CPU time,
Load time, etc.
RSCOLL00 is a R/ 3 performance collector program that runs periodically to collect performance data of
your R/ 3 System.
2. You can switch between the response time list and the database requests list by clicking Top requests or
Top Time.
3. Click the Back icon to return the main Performance Workload Overview screen.
1
2
3
Analyzing the R/3 System Workload
Reviewing the Transaction Profile
778 1998 SAP Labs, Inc.
Reviewing the Transaction Profile
1. Click the Transaction profile button
to view the time consumption for
each transaction code.
2. Click in the Response time avg (ms) column to select the column you wish to sort.
Notice that RSCOLL00 (COLLECTOR_FOR_PERFORMANCE background job) took significant amount
of time among all other R/ 3 programs.
3. Click the Sort icon.
1
2
3
Analyzing the R/3 System Workload
Reviewing the Transaction Profile
1998 SAP Labs, Inc. 779
The average response time for a transaction should not be greater than one second, with the exception of
the following transactions:
Type of Transaction Transaction
Code
Approximate Response Time
Create Sales Order VA01 < 1,500 ms
Change Sales Order VA02 < 1,500 ms
Display Sales Order VA03 < 1,000 ms
Create billing document VF01 < 1,500 ms
Create delivery VL01 < 2,000 ms
Maintain master HR data PA30 < 1,000 ms
Create material MM01 < 700 ms
Post account document FB01 < 600 ms
Change account document FB02 < 500 ms
Display account document FB03 < 400 ms
Your response times may vary depending on your hardware and customizing.
Analyzing the R/3 System Workload
Reviewing the Transaction Profile
7710 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about R/ 3 System Workload and Buffer Performance Monitors (Ch. 7681)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools SAP System Workload Monitor
Functionality of Workload Monitor Workload Overview of a Server
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computer Center
Management System CCMS Monitors Buffers Monitor Working
with Buffers Monitor
Basis Components System Administration Computer Center
Management System CCMS Monitors Workload Monitors
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Analyzing the R/3 Buffers
Overview
1998 SAP Labs, Inc. 781
Chapter 78: Analyzing the R/3 Buffers
Contents
Overview............................................................................................................................................................................................................781
Heres How.........................................................................................................................................................................................................781
Overview
With the CCMS Buffer Performance Monitor, you can analyze the state of R/ 3 buffers and evaluate their
quality. You can then use this analysis to pinpoint areas in which buffer sizes can be changed to improve
performance. The information displayed has been collected since server startup.
Heres How
1. To go to the SAP R/3 CCMS
Performance Monitoring menu,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
2. To view the SAP Setup/buffers, from
the Performance Monitoring window,
choose Setup/buffers Buffers.
Alternative:
1
2
Analyzing the R/3 Buffers
Heres How
782 1998 SAP Labs, Inc.
After starting R/ 3, the Hitratio % of the buffers have values of less than 95% (the normal
value is greater than 95%). The Hitratio % should increase after a few days of use.
Ratings lower than 90% can be tolerated for certain buffers, such as the single record buffer
or the calendar buffer. These buffers do not impede the overall system performance.
As a rule of thumb, the value of the Swaps is considered high if it is greater than 1,000. If this
happens, you need to increase the size of the buffers (if you have enough free memory) by
maintaining the related instance parameters. After restarting the system, the Swaps objects
will be reset to 0.
Swaps occur when objects are removed from the buffer and cannot be replaced until a new
database access retrieves the data.
3
7
4
8
5
9
6
Analyzing the R/3 Buffers
Heres How
1998 SAP Labs, Inc. 783
The Tune Summary Screen is divided into four parts:
R/ 3 Application Server Buffers (see ref. 3 above)
As a rule of thumb, the following R/3 Hitratio percents should have the following minimum values:
- Short NTAB (Name tab): 99%
- Program: 97%
- CUA: 99%
- Screen: 99%
- Generic key: 90%
- Single key: 80%
SAP Memory (see ref. 4)
SAP Cursor Cache (see ref. 5)
Call Statistics (see ref. 6)
In addition, two important parameters need to be constantly monitored for the various buffers.
They are the Hitratio [%] column (ref. 7) and the Swaps column (ref. 8).
Over time, the Swaps need to be observed. Even if the buffer is sufficient, we recommend
that you recycle the server since fragmentation of the buffer could occur over time.
Buffer Bottleneck occurs if buffer Swaps begin happening, or Max. Use of Extended memory
equals Current Use.
The R/3 Repository Buffers consist of four buffers in shared memory, one for each of the following:
Table Definitions TTAB Buffer Table DDNTT
Field Descriptions FTAB Buffer Table DDNTF
Short Name Type SNTAB Short Summary of TTAB and FTAB buffers
Initial Record Layouts IREC Buffer Record layouts that are initialized depending
on the field type
9. To view the detailed information on R/ 3 buffers, click on the Detail analysis menu button.
Analyzing the R/3 Buffers
Heres How
784 1998 SAP Labs, Inc.
This window provides a link to a
more detailed analysis of the
buffers.
Paging may occur if too much memory is taken from the operating system and given to the
R/ 3 buffers!
If there is a limitation on main memory, the R/ 3 buffer memory could be decreased. From a
performance standpoint, this configuration is the most beneficial.
Analyzing the R/3 Buffers
Heres How
1998 SAP Labs, Inc. 785
The following table provides information on the instance parameters that should be maintained for the
various buffers.
Buffer Instance Parameter
Program Buffer (PXA) abap/ buffersize
abap/ pxa
abap/ programs
CUA buffer (CUA) rsdb/ cua/ buffersize
Screen Buffer (SCRE) zcsa/ presentation_buffer_area
sap/ bufdir_entries
Generic key table buffer (TABL) zcsa/ db_max_buftab
zcsa/ table_buffer_area
rtbb/ frame_length
Single key table buffer (TABLP) rtbb/ max_tables
rtbb/ buffer_length
rtbb/ frame_length
Table description buffer (TTAB) rsdb/ ntab/ entrycount
Field catalog buffer (FTAB) rsdb/ ntab/ entrycount
rsdb/ ntab/ ftabsize
Initial record buffer (IRBD) rsdb/ ntab/ entrycount
rsdb/ ntab/ irbdsize
Short nametab buffer (SNTAB) rsdb/ ntab/ entrycount
rsdb/ ntab/ sntabsize
Analyzing the R/3 Buffers
Heres How
786 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about R/ 3 System Workload and Buffer Performance Monitor (Ch. 7681)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools SAP System SAP Buffers R/3
Buffers and Buffer Monitor Tuning Buffers
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Buffer Monitor Working with Buffer Monitors Displaying
Table Buffers
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Analyzing Buffer Statistics
Overview
1998 SAP Labs, Inc. 791
Chapter 79: Analyzing Buffer Statistics
Contents
Overview............................................................................................................................................................................................................791
Heres How.........................................................................................................................................................................................................791
Overview
This chapter shows how to use the CCMS Buffer Performance Monitor to display statistics about buffer and
memory usage over a period of time.
Heres How...
1. To go to the SAP R/3 CCMS
Performance Monitoring menu,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
2. To view the SAP Setup/buffers from
the Performance Monitoring window,
choose Setup/Buffers Buffers.
Alternative:
2
1
Analyzing Buffer Statistics
Heres How...
792 1998 SAP Labs, Inc.
3. Click the Detail analysis menu
button.
4. Click the Program button.
3
4
Analyzing Buffer Statistics
Heres How...
1998 SAP Labs, Inc. 793
5. If you want to view detailed R/ 3
buffer information, click the
Previous buffer, Next buffer, Buffered
objects, or History buttons.
If the program buffer has swapped
objects and the numbers continue to
increase, consider:
Increasing the ABAP/buffer size
parameter, which is located in the
file instance profile (for example,
DEV_DVEBMGS00_pnsfo36).
Shutting down the R/ 3 System and
re-booting it, since program buffer
fragmentation can occur after the
system has been in use for a while.
6. Click the Back icon to return to the
previous screen.
7. Click Back icon to return to the
previous screen.
5
6
7
Analyzing Buffer Statistics
Heres How...
794 1998 SAP Labs, Inc.
8. To view the activities of the
program buffer history click the
History button.
An example of History of R/ 3 Buffers and Memory:
8
9
Analyzing Buffer Statistics
Heres How...
1998 SAP Labs, Inc. 795
9. In the time that has elapsed since this example, the R/ 3 System was re-booted and the free buffer size
changed from 0 to 120.
For further details refer to
R/3 System Administration Made Easy
All chapters about R/ 3 System Workload and Buffer Performance Analysis (Ch. 7681)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools SAP System SAP Buffers R/3 Buffers
and Buffer Monitor Tuning Buffers
R/3 System Online Help
Online Documentation CD Basis Components System Administration Computer Center
Management System CCMS Monitors Buffers Monitor Working
with Buffers Monitor
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Analyzing Parameters of R/3 Buffers
Overview
1998 SAP Labs, Inc. 801
Chapter 80: Analyzing Parameters of R/3 Buffers
Contents
Overview............................................................................................................................................................................................................801
Heres How.....................................................................................................................................................................................................801
Viewing Parameters ..........................................................................................................................................................................................803
Overview
This chapter explains how to analyze R/ 3 buffer history to find the correct buffer sizes.
Heres How
1. To go to the SAP R/3 CCMS
Performance Monitoring menu,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
2. To view the SAP Setup/buffers from
the Performance Monitoring window,
choose Setup/Buffers Buffers.
Alternative:
2
1
Analyzing Parameters of R/3 Buffers
Heres How
802 1998 SAP Labs, Inc.
3. Click the Detail analysis menu
button.
4. Click the Parameters button.
3
4
Analyzing Parameters of R/3 Buffers
Viewing Parameters
1998 SAP Labs, Inc. 803
Viewing Parameters
There is one application server for this
R/ 3 System:
1. Select one of the hostnames by
clicking once on the item line (in
this example, pnsfo36).
2. Click the History of file button.
3. This screen shows the history of
parameter changes. In this
example, since 10/ 31/ 97, the
abap/buffersize has been changed
from 65,000 to 70,000.
To view only the active parameters
(without the history of changes), click
the Active parameters button.
1
2
3
Analyzing Parameters of R/3 Buffers
Viewing Parameters
804 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about R/ 3 System Workload and Buffer Performance Monitor (Ch. 7681)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools SAP System SAP Buffers Using
Buffer Statistics
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS Monitors
Buffer Monitor Tuning Buffers
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Analyzing Buffer Storage
Overview
1998 SAP Labs, Inc. 811
Chapter 81: Analyzing Buffer Storage
Contents
Overview............................................................................................................................................................................................................811
Analyzing Buffers..............................................................................................................................................................................................811
Overview
The CCMS Buffers Monitor lets you analyze the state of the R/ 3 buffers and evaluate their quality. By doing
so, you can pinpoint areas in which buffer sizes can be changed to improve performance.
Analyzing Buffers
1. To go to the SAP R/3 CCMS
Performance Monitoring menu,
choose Tools Administration
Computer Center Management
System Monitor Performance
Menu.
Alternative:
2. To view the SAP Setup/buffers from
the Performance Monitoring window,
choose Setup/Buffers Buffers.
Alternative:
2
1
Analyzing Buffer Storage
Analyzing Buffers
812 1998 SAP Labs, Inc.
3. Click the Detail analysis menu
button.
4. Click the Storage button.
3
4
Analyzing Buffer Storage
Analyzing Buffers
1998 SAP Labs, Inc. 813
This screen contains generated
Storage information.
A Pool is a group of SAP shared memory segments.
Analyzing Buffer Storage
Analyzing Buffers
814 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
Analyzing R/3 Buffers (Ch. 78)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools SAP System SAP Buffers Storage
Check
R/3 System Online Help
Online Documentation CD Computer Center Management System CCMS Monitors Buffer Monitor
Buffers in the R/3 System
Basis Components System Administration Computer Center
Management System Buffers Monitor Working with Buffers Monitor
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC314/ BC360/ BC361/ BC362/ BC370)
Overviewing the Oracle Performance Monitor
Overview
1998 SAP Labs, Inc. 821
Chapter 82: Overviewing the Oracle Performance Monitor
Contents
Overview............................................................................................................................................................................................................821
Database Performance Check..........................................................................................................................................................................822
Policies and Procedures..............................................................................................................................................................................823
System Environment ...........................................................................................................................................................................823
Procedures ..........................................................................................................................................................................................823
Roles and Responsibilities ..................................................................................................................................................................823
Database System Controlling ..........................................................................................................................................................................823
Policies and Procedures..............................................................................................................................................................................823
System Environment ...........................................................................................................................................................................823
Policies ................................................................................................................................................................................................824
Procedures ..........................................................................................................................................................................................824
Roles and Responsibilities ..................................................................................................................................................................824
Useful OSS Notes..............................................................................................................................................................................................824
Overview
Activity
Tables/Indices
Global
Alerts Workload Setup/Buffers
Local
Remote
Network
Operating System
Exceptions Analyses
Statistics Records
Buffers
Calls
Parameter Changes
Activity
System Configuration
Parameter Changes
Activity
System Configuration
Parameter Changes
LAN Check with ping
Network Monitor
Exclusive Lockwaits
Parameter Changes
System Log
DUMP Analyses
SAP-Directories
Active Users
Except/User
Performance Monitoring
SAP System
Database System
Network Monitor
Global
Operating System
File System
Call Statistics
Current Workload
Local
Operating System
File System
Remote
Database
Processes
Instances
Users, local
Users, global
Download Statistics
Performance Report
SAPOSCOL Destination
This section contains the System Performance layout and recommendations to ensure optimal
performance of your R/ 3 System. Consider all the possible factors before changing any
parameters. The procedures described in this chapter do not replace the EarlyWatch Service that
all R/ 3 customers should use.
Overviewing the Oracle Performance Monitor
Database Performance Check
822 1998 SAP Labs, Inc.
Database Performance Check
The database system is the most complex subsystem in the R/ 3 client/ server architecture. A system
administrator must be able to analyze the database and determine whether bottlenecks in the database are
causing poor performance for all users. Some questions the system administrator should consider and be
able to answer are:
Are there resource constraints in the database configuration?
Are there exclusive lockwaits?
Are there any poorly-performing SQL statements?
SAP chose to implement its own database monitor rather than use the native monitoring tools provided by
database vendors for the following reasons:
To adequately separate monitoring and administration
To monitor the database in read-only mode
To provide a standard interface to support staff for monitoring database activity
To get information from both the database and the R/ 3 System for monitoring specific database
resources (The R/ 3 System, in particular, due to its three-tier client/ server architecture, places special
demands on database monitoring software.)
All information comes from Oracles own monitoring views and tables. Oracle provides information on the
state of the database in virtual tables, called dynamic performance tables or V$ tables, which are held
in memory. The SAP/ Oracle Database Monitor uses these and other Oracle administrative tables to collect,
evaluate, and present its information. The SAP/ Oracle Database Monitor is written in ABAP/ 4, which is,
or can be, directly or regularly started.
Database performance problems can be caused by database configuration or application problems. Here is
a list of possible problem areas:
1. Database Configuration
Bad hit ratio of database buffer
Bad hit ratio of shared pool objects
Disks with high response times
2. Application Problems
Expensive Statements
Bad statements / bad execution (optimizer)
Bad indices (low fill level)
Lock Wait Situations
Lock held too long
Parallel modifications
Overviewing the Oracle Performance Monitor
Database System Controlling
1998 SAP Labs, Inc. 823
Policies and Procedures
This section offers samples of policies and procedures for monitoring database performance.
System Environment
Software Components
System Name Software
DEV CCMS
QAS CCMS
PD1 CCMS
PD2 CCMS
Database Monitoring is a permanent process, and R/ 3 CCMS is used for this task.
Additional checks to be performed:
Type of check DEV QAS PD1 PD2
Table extents T T D D
Tablespace Fill level T T D D
Missing Indices T T D D
D: Daily T: every 2 days
Procedures
After defining and setting the thresholds, the CCMS Alert Monitor has to be watched regularly for each
system. This level of monitoring is of special importance on production machines.
Roles and Responsibilities
Task Role
Watching systems permanently Operator/ DBA
Database System Controlling
Policies and Procedures
System Environment
Software Components
System Name Software
DEV SAPDBA 3.1H
QAS SAPDBA 3.1H
PD1 SAPDBA 3.1H
PD2 SAPDBA 3.1H
Overviewing the Oracle Performance Monitor
Useful OSS Notes
824 1998 SAP Labs, Inc.
Policies
Database maintenance tasks will be performed in special maintenance time frames using SAPDBA (for
example, Saturday during evening hours).
Procedures
All aspects of the database maintenance are covered by SAPDBA. See SAPDBA manual for a detailed
description of SAPDBA.
Roles and Responsibilities
Task Role
Reorganize Tables DBA
Reorganize Tablespaces DBA
Creating Missing Indices DBA
Enlarging Tablespaces DBA
Distributing Database files DBA
Tuning Database DBA
Useful OSS Notes
Note # Description
71346 Collective note: Monitoring: ST04, DB02, ST10, ST03
45580 How are syslog files deleted?
15374 Checklist: Performance analysis
11886 Central SysLog cut off
Overviewing the Oracle Performance Monitor
Useful OSS Notes
1998 SAP Labs, Inc. 825
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle
R/3 System Online Help
Online Documentation CD CCMS CCMS Monitors Database Monitor SAP/Oracle Database
Monitor
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Analyzing Database Activity
Overview
1998 SAP Labs, Inc. 831
Chapter 83: Analyzing Database Activity
Contents
Overview............................................................................................................................................................................................................831
Performance Analysis.......................................................................................................................................................................................831
Overview
The database buffer pool contains the database System Global Area (SGA ) block of memory and reduces
time-intensive disk accesses. A high-quality SGA means that there are only a few disk accesses, and that
user calls are mostly requests to the SGA database.
Performance Analysis
What follows is the Performance Analysis and recommendations of the underlying Oracle database:
A recently started database instance may show misleading statistics with regard to hit ratios.
To prevent misleading results, you should let the database warm up before initiating the
performance analysis. To warm up the database, let it run for at least four hours, or until it has
a significantly high total data buffer reads level (for example, 1,000,000 reads).
1. To go to the SAP R/3 CCMS
Performance Monitoring window,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
1
Analyzing Database Activity
Performance Analysis
832 1998 SAP Labs, Inc.
2. To view the Oracle general database
from the Performance Monitoring
window, choose Database
Activity.
Alternative:
3. A typical Data Buffer Size should be
between 16 MB (16.384 KB) and 32
MB (32.768 KB). In this example,
39,320 KB is adequate. Data buffer
quality should be at least 95%. In
this example, the value of the Data
buffer Quality is 99.2%.
If the data buffer has a quality level
of 70% or less, it indicates that the
data buffer is too small. The data
buffer size can be changed by
modifying the value of db_block_size
which is defined in the
init<SAPSID>.ora file.
4. The ratio of Reads to Physical reads
should be greater than 10:1. Here,
the ratio is 18,450,597 : 150,919
which corresponds to a 122 : 1 ratio.
This is okay because it is greater
than a 10:1 ratio.
These fields indicate that of the
18,450,597 Reads, 150,919 block
reads have resulted from blocks
being physically read from
disk.
The Physical writes field
indicates that 54,009 Oracle
blocks have been written to
disk by the Database Writer
process.
2
3
4
5
6
7 8
9
10
11
Analyzing Database Activity
Performance Analysis
1998 SAP Labs, Inc. 833
5. The value of the Busy Wait is 18 (=0.00009 % of 18,240,597 Reads). A normal value for the Busy Wait is
less than 5% of Data Buffer (Oracle Block) Read. Higher values for the Busy Waits indicate excessive
contention. In this example, 18 is an adequate value.
6. The value of the Shared Pool Size is 28,227 KB. In this case, a normal value is at least 20 MB (20,480 KB)
or more. It should be higher than 10% of the physical memory (in this example, 256 MB). For the above,
20 MB / 256 MB * 100% = 7.8% which is lower than 10%. The Shared Pool Size should be increased.
7. The DD Cache quality value is 59.1% (a normal value is greater than 90%). If it is between 80% and 90%,
and the User Calls/ Recursive Calls ratio is 4:1 or higher, then the DD Cache quality is fine. If none of the
conditions are fine, you may need to increase the Shared Pool Size. The low quality of the Cache could
result from the System not being used enough (startup).
8. The value of the Log Buffers Allocation Retries is 9 (= 0.004% of 217,376 Entries). A normal value is less
than 1% of Entries, so this percentage is within normal parameters.
9. The percentage of Table scans: Long tables is 198 (which is 0.07% of the total 275,894 User Calls). This
percentage should be very low, usually less than 1%.
10. The ratio of User Calls to Recursive Calls is 0.05:1 (= 275,894 / 5,858,686). A normal value should be more
than 4:1 (the larger the better.) Since the System has recently been rebooted, it is not unusual for the
percentage to be low. However, a few days later the percentage should increase significantly and
return to a normal value.
The ratio of Reads to User Calls is 67:1 (= 18,450,597 / 275,894). A normal value should be around 15:1
to 20:1. If the ratio is 50:1 or higher, there may be expensive SQL statement, or the R/ 3 System has not
been used more than one full business day.
11. The ratio of User Calls to Parses is 2.3:1 (= 275,894 / 121,713). A normal value should be greater than
4:1. If it is lower than 4:1, you may need to increase the Shared Pool Size.
To view detailed information regarding Oracle performance, choose Database Activity Detail
Analysis Menu from the Performance Monitoring window.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Implementation Monitoring Tools Database
Monitors Introduction to the R/3 Database Monitor for
Oracle SAP/Oracle Performance Monitoring Strategies Monitoring the
Database Buffer (Oracle)
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS Monitors
Database Monitor SAP/Oracle Database Monitor SAP/Oracle
Performance Monitoring Strategies Monitoring the Data Buffer (Oracle)
Analyzing Database Activity
Performance Analysis
834 1998 SAP Labs, Inc.
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Analyzing Exclusive Lockwaits
Overview
1998 SAP Labs, Inc. 841
Chapter 84: Analyzing Exclusive Lockwaits
Contents
Overview............................................................................................................................................................................................................841
Heres How.........................................................................................................................................................................................................841
Overview
A lockwait occurs when a large number of R/ 3 user requests are channeled into a relatively small number
of R/ 3 work processes (at the application server).
A user holding a lock occupies a R/ 3 work process. Other users trying to apply the same lock will have to
wait. This waiting period is called a lockwait. As the number of lockwaits increases, fewer and fewer R/ 3
user requests can be processed by available R/ 3 work processes. In the worst case scenariowhen the
number of lockwaits equals the number of R/ 3 work processesa small number of users can cause the
entire R/ 3 System to freeze.
For example, an order taker puts a lock on available material, gets distracted, and does not confirm the
order. No other order taker will be able to lock the same item until the initial lock is released. A typical way
of solving this problem is to find the person holding the lock so that he or she can confirm the order and
release it. If this is not possible, the lock is deleted. This will roll back the transaction of the lock-holder and
release the material for other users.
You can search for exclusive lockwaits where at least one process is locked through a lock held by another
process. The process of holding the lock and the waiting process(es) is described in the following step-by-
step procedure.
Heres How...
1. To go to the SAP R/3 CCMS
Performance Monitoring screen,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
1
Analyzing Exclusive Lockwaits
Heres How...
842 1998 SAP Labs, Inc.
2. To go to the Database Performance
Analysis window, choose Database
Exclusive lockwaits.
Alternative:
3. This screen indicates that there are
No exclusive lock-waits found, which
is desirable.
Lockwaits can cause poorly timed holds on resources that result in inefficient system
performance. Lockwait situations can also cause an instant halt to the system performance. It is
necessary to find out which SAP Object or Objects lock a process. If a lockwait is caused by a
long-running job and is interfering with other processes, SAP administrators should identify
the user running the job and decide whether it should be postponed until a more convenient
time. If the lockwait is caused by a bad program, appropriate action, such as deleting the process
that causes the lock, should be taken.
3
2
Analyzing Exclusive Lockwaits
Heres How...
1998 SAP Labs, Inc. 843
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed Analysis (Oracle) Detail
Analysis Menu (Oracle)
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor Detailed
Analysis (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Analyzing the Dictionary Buffer
Overview
1998 SAP Labs, Inc. 851
Chapter 85: Analyzing the Dictionary Buffer
Contents
Overview............................................................................................................................................................................................................851
Heres How.........................................................................................................................................................................................................851
Overview
The Dictionary Buffer information is read into memory from the dictionary tables stored on disk. When an
Oracle instance is first started, this cache is empty and must be loaded as the dictionary information is
accessed. For this reason, hit ratios are generally low at database instance startup and stabilize over time.
Heres How...
Follow this step-by-step procedure to analyze the dictionary buffer:
1. To go to the SAP R/3 CCMS general
performance menu, choose Tools
Administration Computer Center
Management System Control
Performance Menu.
Alternative:
2. To go to the Database Performance
Analysis screen, choose Database
Activity.
Alternative:
2
1
Analyzing the Dictionary Buffer
Heres How...
852 1998 SAP Labs, Inc.
3. Click the Detail analysis menu
button.
4. Click the Dictionary buffer button.
4
3
Analyzing the Dictionary Buffer
Heres How...
1998 SAP Labs, Inc. 853
5. Click once in the first row of the
Used(%) column to select it.
6. Click the Sort button to view the
Used(%) list from the highest to the
lowest value.
7. Notice that the Used(%) for some of
the Dictionary Cache Objects has
reached 100%. This is not a critical
issue because the system quickly
allocates the Dictionary Cache
Objects as needed, and fixes itself.
7
5
6
Analyzing the Dictionary Buffer
Heres How...
854 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed Analysis (Oracle) Detail
Analysis Menu (Oracle)
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor
SAP/Oracle Performance Monitoring Strategies Detailed Analysis of the
Dictionary Buffer (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Analyzing Database Performance
Overview
1998 SAP Labs, Inc. 861
Chapter 86: Analyzing Database Performance
Contents
Overview............................................................................................................................................................................................................861
Heres How.........................................................................................................................................................................................................861
Overview
Monitoring call activity determines the work done on the system separated by both user and internal
operations.
Heres How...
1. To go to the SAP R/3 CCMS
Performance Monitoring window,
choose Tools Administration
Computer Center Management
System Monitor Performance
Menu.
Alternative:
2. To go to the Database Performance
Analysis window, choose Database
Activity.
Alternative:
1
2
Analyzing Database Performance
Heres How...
862 1998 SAP Labs, Inc.
3. Click the Detail analysis menu
button to view other options.
4. Click the Performance database
button.
3
4
Analyzing Database Performance
Heres How...
1998 SAP Labs, Inc. 863
5. The ratio of User calls to Recursive
calls is about 3:2 (544,795 : 371,630);
the ideal ratio is 5:1. The ratio in this
newly-established R/ 3 System will
improve with use over time.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed Analysis (Oracle)
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor Detailed
Analysis (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
5
Analyzing Database Parameter Changes
Overview
1998 SAP Labs, Inc. 871
Chapter 87: Analyzing Database Parameter Changes
Contents
Overview............................................................................................................................................................................................................871
Heres How.....................................................................................................................................................................................................871
Overview
This section determines both the current and historical settings of the init<SID>.ora parameters. Note that
changes to these parameters only take effect after the database instance has been restarted.
Heres How
1. To go to the SAP R/3 CCMS general
performance menu, choose Tools
Administration Computer Center
Management System Control
Performance Menu.
Alternative:
2. To go to the Database Performance
Analysis window, choose Database
Activity.
Alternative:
1
2
Analyzing Database Parameter Changes
Heres How
872 1998 SAP Labs, Inc.
3. Click the Detail analysis menu
button.
4. Click the Parameter changes button.
3
4
Analyzing Database Parameter Changes
Heres How
1998 SAP Labs, Inc. 873
5. This example indicates that
06/10/1997 was the last date that this
parameter was changed.
6. Click the History of file button.
7. This example indicates that the
Database Parameters value
SHARED_POOL_SIZE was
changed from 26,214,400 to
26,200,000 on 11/17/1997.
5
6
7
Analyzing Database Parameter Changes
Heres How
874 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed Analysis (Oracle) Detail
Analysis Menu (Oracle)
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor Detailed
Analysis (Oracle) Detail Analysis Menu (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Analyzing the V$ROWCACHE
Overview
1998 SAP Labs, Inc. 881
Chapter 88: Analyzing the V$ROWCACHE
Contents
Overview............................................................................................................................................................................................................881
Heres How.........................................................................................................................................................................................................881
Overview
The Shared Pool (that is, the memory area in the SGA) is used by Oracle to hold several key memory
structures. Most important among these structures are the Data Dictionary Cache and the Shared SQL Area.
The Data Dictionary Cache contains information about naming, definition, and access, for Oracle objects. It
is regularly referenced by Oracle, as well as some application programs and database users. This chapter
shows you how to analyze the Dictionary Cache statistics (V$ROWCACHE).
Heres How...
1. To reach the SAP R/3 CCMS
general performance menu, choose
Tools Administration Computer
Center Management System
Control Performance Menu.
Alternative:
2. To go to the Database Performance
Analysis window, choose Database
Activity.
Alternative:
2
1
Analyzing the V$ROWCACHE
Heres How...
882 1998 SAP Labs, Inc.
3. Click the Detail analysis menu
button.
To review the Database Performance, it is
necessary to display the v$values of the
database. Refer to the Oracle database
training manual for more information.
4. Click the Display V$ values button.
3
4
Analyzing the V$ROWCACHE
Heres How...
1998 SAP Labs, Inc. 883
5. Choose Goto Statistics
V_Rowcache to reach the V$ values.
6. The percentage ratio of the total
Gets and Getmisses should be less
than 15% for the database and less
than 10% if using SAP. In this
example, the total number of all
Gets is 5,112 and the total number
of Getmiss is 1,428 which results in
a ratio of 28%. This ratio is a little
too high. If the percentage ratio is
significantly higher than 15% (for
example, 30%), the Shared Pool
needs to be enlarged.
To enlarge the Shared Pool Size (if you have enough additional memory), locate the file in the
directory <drive>:\ ORANT\ DATABASE\ INIT<SAPSID>.ORA (for example,
C:\ ORANT\ DATABASE\ INITDEV.ORA) and change the value parameter shared_pool_size.
You may have to experiment to achieve an optimal ratio of Gets to Getmisses.
5
6
Analyzing the V$ROWCACHE
Heres How...
884 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to
the R/3 Database Monitor for Oracle Detailed Analysis (Oracle)
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor Detailed
Analysis (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Analyzing the Databases Tables and Indices
Overview
1998 SAP Labs, Inc. 891
Chapter 89: Analyzing the Databases Tables and Indices
Contents
Overview............................................................................................................................................................................................................891
Heres How.........................................................................................................................................................................................................891
Overview
This chapter shows you how to do internal database and consistency checks between the database and the
R/ 3 System.
Check the status of the database tables and database indices frequently. Slightly fragmented
tables can adversely affect system performance!
Heres How...
1. To go to the SAP R/3 CCMS general
performance menu, choose Tools
Administration Computer Center
Management System Control
Performance Menu.
Alternative:
2. To view the databases tables and
indices information, choose
Database Tables/Indexes.
2
1
Analyzing the Databases Tables and Indices
Heres How...
892 1998 SAP Labs, Inc.
3. From the Data Base Performance:
Tables and Indexes screen, you can
check the following:
Internal database consistency
Tables without indices
Database and R/ 3 System
Missing database objects (tables
and indices)
Missing objects in the SAP Data
Dictionary.
Click Refresh to get the most
current statistics. Otherwise,
old statistics will be displayed.
To do further analyses, from this screen select Goto Check Installation DB <->ABAP
Dict. The missing objects will be displayed.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor Detailed
Analysis (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Analyzing Missing Indices Contents
Overview
1998 SAP Labs, Inc. 901
Chapter 90: Analyzing Missing Indices Contents
Overview............................................................................................................................................................................................................901
Checking for Missing Indices ..........................................................................................................................................................................901
Useful OSS Notes..............................................................................................................................................................................................903
Overview
You can verify whether objects such as tables or indices defined in the ABAP/4 Dictionary are also defined
in the database system. Indices will only be missing if you ignore an error message (such as Table created or)
when creating a table or when deleting an index.
Indices are sometimes accidentally deleted during an incorrect reorganization. When this happens, access
times may increase and duplicate records may be created which make access unsafe.
Checking for Missing Indices
1. To check for missing indices, go to
the SAP R/3 CCMS Performance
Monitoring window. Choose Tools
Administration Computer
Center Management System
Control Performance Menu.
Alternative:
2. From the Performance Monitoring
screen, choose Database
Tables/Indexes.
2
1
Analyzing Missing Indices Contents
Checking for Missing Indices
902 1998 SAP Labs, Inc.
3. Click the Missing Indexes button.
4. In this example, the directories
listed under Indexes missing in the
database indicate that there are no
missing indices. If you find missing
indices, be sure to recreate them to
achieve optimal performance.
Primary indices (ending in 0) ensure that line keys (row keys) are unique. Missing primary
indices are therefore critical. If a primary index is missing, you should consult SAP for help
with its restoration. There is no simple procedure for restoring an index if a large number of
duplicate keys were created in a table.
Secondary indices (not ending in 0) are used for special scans and are only relevant for their
performance. You may restore a secondary index for SAP tables using the Database Utility of
the ABAP/4 Dictionary (transaction / nSE14). You can likewise access this utility from the
individual index analysis functions.
3
4
Analyzing Missing Indices Contents
Useful OSS Notes
1998 SAP Labs, Inc. 903
Useful OSS Notes
Note # Description
44395 SAPDBA: Missing indexes after reorg run
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed Analysis (Oracle)
R/3 System Online Help
Online Documentation CD Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor Detailed
Analysis (Oracle) Table without Indexes (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Monitoring Space-Critical Objects
Overview
1998 SAP Labs, Inc. 911
Chapter 91: Monitoring Space-Critical Objects
Contents
Overview............................................................................................................................................................................................................911
Heres How.....................................................................................................................................................................................................911
Overview
This chapter shows you how to examine Space-critical objects to do internal database checks and consistency
checks between the database and the R/ 3 System. Related issues include situations where an object cannot
be allocated and overflow problems.
Heres How
1. To go to the SAP R/3 CCMS
Performance Monitoring window,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
2. To view information on the
databases tables and indices from
the Performance Monitoring window,
choose Database Tables/Indexes.
1
2
Monitoring Space-Critical Objects
Heres How
912 1998 SAP Labs, Inc.
3. Click the Space critical objects button.
4. The message There are no critical
tables/indexes appears in the status
bar at the bottom of the window. In
this example, no space-critical
objects were found for this R/ 3
server.
If space-critical objects are found, you may want to check the tablespace status and the extent of
tables and indices (see chapter 93, Viewing and Extending Tablespaces, and chapter 94, Analyzing
Extents of Tables and Indices).
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for an R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed Analysis (Oracle)
R/3 System Online Help
Online Documentation Basis Components System Administration CCMS CCMS
Monitors Database Monitor SAP/Oracle Database Monitor Detailed
Analysis (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
3
4
Analyzing Current Tablespace Sizes
Overview
1998 SAP Labs, Inc. 921
Chapter 92: Analyzing Current Tablespace Sizes
Contents
Overview............................................................................................................................................................................................................921
Heres How.........................................................................................................................................................................................................921
Overview
After installing the system and before transferring data, you should verify that space exists in all
tablespaces. Do this regularly when your system is productive. If you find full tablespaces, you must
analyze whether they should be extended and/ or reorganized.
Heres How...
1. To go to the SAP R/3 CCMS
Performance Monitoring window,
follow the path Tools
Administration Computer Center
Management System Control
Performance Menu.
Alternative:
2. To view information on the
Databases tables and indices, from
the Performance Monitoring window,
follow the path Database
Tables/Indexes.
2
1
Analyzing Current Tablespace Sizes
Heres How...
922 1998 SAP Labs, Inc.
3. Click on the Current sizes button.
The Memory Management:
Tablespaces window appears.
4. This list is sorted by Used%. Notice
that all of the Used Tablespace
values are less than 90%the
standard values for the system.
If the Used% of Tablespace is larger
than 90%, you should extend the
Tablespace (see chapter 93, Viewing and
Extending Tablespaces).
4
3
Analyzing Current Tablespace Sizes
Heres How...
1998 SAP Labs, Inc. 923
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for an R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Detailed Analysis (Oracle) Checking
for Full Tablespaces
R/3 System Online Help
Online Documentation Basis Components System Administration CCMS CCMS Monitors
Database Monitor SAP/Oracle Database Monitor Detailed Analysis
(Oracle) Checking for Full Tablespaces
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Viewing and Extending Tablespaces
Overview
1998 SAP Labs, Inc. 931
Chapter 93: Viewing and Extending Tablespaces
Contents
Overview............................................................................................................................................................................................................931
Check Current Tablespace Sizes.....................................................................................................................................................................931
How to Extend Tablespaces which are Allocated Above 90% (as a Rule of Thumb) .................................................................................933
Overview
When the database system can no longer assign extents in a tablespace (Oracle error 1547), you must extend
the tablespace by adding a data file. The data file creates new storage space.
The extension of a tablespace changes the structure of the database. The database can only be completely
restored if you back up the new file and the control file. SAP recommends that you backup the extended
tablespace with the SAPDBA backup program BRBACKUP.
It is highly recommended that you perform a full system data backup before extending a
tablespace! Perform the following steps only if a backup has been completed! Table extensions
should only be performed by qualified system administrators.
Check Current Tablespace Sizes
1. Click the Windows NT Start button
and choose Programs Command
Prompt.
2. At the Command Prompt, enter
sapdba.
2
1
Viewing and Extending Tablespaces
Check Current Tablespace Sizes
932 1998 SAP Labs, Inc.
3. Enter c to choose Tablespace
administration.
4. Enter c to choose Free space and
fragmentation of all tablespaces.
You can also view the tablespace
allocations from within SAP by
entering the transaction /nDB02.
Look for the percent of tablespace
allocation under %-Alloc. As a rule of
thumb, write down the names of those
that are greater than or equal to 90%.
5. Press Return to continue to view
the next page.
3
4
5
Viewing and Extending Tablespaces
How to Extend Tablespaces which are Allocated Above 90% (as a Rule of Thumb)
1998 SAP Labs, Inc. 933
6. Press Return to continue.
How to Extend Tablespaces which are Allocated Above 90% (as a Rule of Thumb)
1. Enter a to alter a tablespace.
2. Enter the name of the first
tablespace you want to alter (in this
example, PSAPES31HI).
3. Enter f to Alter tablespace
<tablespace> and Add Datafile.
1
2
3
6
Viewing and Extending Tablespaces
How to Extend Tablespaces which are Allocated Above 90% (as a Rule of Thumb)
934 1998 SAP Labs, Inc.
4. Enter s to Start (Add datafile).
5. Press Return to continue.
6. Press Return to continue.
4
5
6
Viewing and Extending Tablespaces
How to Extend Tablespaces which are Allocated Above 90% (as a Rule of Thumb)
1998 SAP Labs, Inc. 935
7. Enter q and press Return to go back
to the Tablespace administration
screen (assuming that a database
backup has already been
performed).
Repeat steps 17 to alter additional
tablespaces.
8. When the tablespace extensions are
finished, enter q to return to the
SAPDBA main menu.
9. Enter q to Quit sapdba.
10. Enter y to confirm that you want to
quit.
7
8
9
10
Viewing and Extending Tablespaces
How to Extend Tablespaces which are Allocated Above 90% (as a Rule of Thumb)
936 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for an R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
DBA Oracle CD Reference Production Growth Management Managing Tablespace
Extension
R/3 System Online Help
Online Documentation CD Basis Components Database Administration Oracle Tablespace
Administration
Basis Courses
Database Administration ORACLE (BC505)
Analyzing Extents of Tables and Indices
Overview
1998 SAP Labs, Inc. 941
Chapter 94: Analyzing Extents of Tables and Indices
Contents
Overview............................................................................................................................................................................................................941
Heres How.........................................................................................................................................................................................................941
Useful OSS Notes..............................................................................................................................................................................................943
Overview
Eventually, the extents of a table or index may reach their maximum limit. These extents need to be
monitored and reorganized as the values begin to approach the threshold. Before you transfer data to a
table or index, you should check if tables are close to reaching their maximum number of extents.
Heres How...
1. To go to the SAP R/3 CCMS
Performance Monitoring window,
choose Tools Administration
Computer Center Management
System Control Performance
Menu.
Alternative:
2. To view information on the
Databases tables and indices from
the Performance Monitoring window,
choose Database Tables/Indexes.
1
2
Analyzing Extents of Tables and Indices
Heres How...
942 1998 SAP Labs, Inc.
3. Click the Checks button.
4. Click the Extents of tables and indexes
button.
3
4
Analyzing Extents of Tables and Indices
Useful OSS Notes
1998 SAP Labs, Inc. 943
5. If the difference between the MaxExtents column and the Extents column is less than 100, database
reorganization is needed for the particular object(s). In this example, the differences are fine, because
the largest Extent is 74 and the lowest MaxExtent is 300. If database reorganization is needed, use the
SAPDBA to reorganize database objects. See chapter 95, Performing Database Reorganization.
The MaxExtents value for the SAP tables is usually 300 or 505. If there is a table or index in
which the number of extents comes close to this value, take notice. The value may reach the
MaxExtent value and cause a terminated transaction. If you find tables with problems with the
maximum number of extents, we recommend that you reorganize the table or the index. If a
reorganization is not possible, you can temporarily increase the MaxExtents value for the table
or the index.
Useful OSS Notes
Note # Description
39650 Maximum number of extents per tablespace
09321 Next-extents in ORACLE system tables are too large
5
Analyzing Extents of Tables and Indices
Useful OSS Notes
944 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for an R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
System Monitoring CD Reference Monitoring Tools Database Monitors Introduction to the
R/3 Database Monitor for Oracle Diagnosing SAP/Oracle Performance
Problems Monitoring Table and Index Fragmentation
R/3 System Online Help
Online Documentation CD Computer Center Monitor System CCMS Monitors Database Monitor
SAP/Oracle Database Monitor Detailed Analysis (Oracle)
Basis Courses
Workload Analysis (BC315)
Technical Core Competence (BC310/ BC360)
Performing Database Reorganization
Overview
1998 SAP Labs, Inc. 951
Chapter 95: Performing Database Reorganization
Contents
Overview............................................................................................................................................................................................................951
Checking Statistics...........................................................................................................................................................................................951
Using Archiving Mode During the Reorganization ........................................................................................................................................951
Advantages of a Reorganization in NOARCHIVELOG Mode: ....................................................................................................................951
Data Security for a Reorganization in NOARCHIVELOG Mode..................................................................................................................952
Checking Extents using SAPDBA before Performing a Reorganization.....................................................................................................952
Checking Extents using R/3 before Performing a Reorganization...............................................................................................................956
Performing the Reorganization........................................................................................................................................................................959
Checking Number of Extents After Performing Reorganization Using SAPDBA .....................................................................................9515
Useful OSS Notes............................................................................................................................................................................................9519
Overview
Over time, tablespaces in the database may become fragmented and cause performance problems. A
reorganization can de-fragment a tablespace and increase its performance.
Checking Statistics
You can use the following tools to inspect the statistics relevant for a reorganization:
The Performance Monitor of the R/ 3 System (see online help of the Computing Center Management System)
Command line option sapdba -check.
Command line option sapdba -analyze.
SAPDBA option Reorganization Check extents and fragmentation.
SAPDBA option Tablespace administration.
Using Archiving Mode During the Reorganization
Because a reorganization always involves the transport of mass data, a large number of redo logs are
written. If you deactivate the ARCHIVELOG mode, there is no significant acceleration of the
reorganization. Since the archive process ARCH runs parallel to the remaining background database
processes, the CPU is only briefly more heavily loaded if you operate the database in ARCHIVELOG mode.
Therefore, the reorganization is not significantly slowed down.
Advantages of a Reorganization in NOARCHIVELOG Mode:
1. You can safeguard against the risk of an archive getting stuck. You also have the benefit of saving space
in the archiving directory of the offline redo log files <drive>:\ oracle\ <SAPSID\ saparch.
Performing Database Reorganization
Checking Extents using SAPDBA before Performing a Reorganization
952 1998 SAP Labs, Inc.
BRARCHIVE does not have to run for the period of the reorganization because no offline redo log files
are created.
2. Time is saved in the event of a recovery, as you can resume from the backup done after the
reorganization (this is mandatory with the NOARCHIVELOG method).
Data Security for a Reorganization in NOARCHIVELOG Mode
SAP recommends deactivating ARCHIVELOG mode only under certain conditions because it interrupts the
continuity of the redo log files. Once reorganization is complete, you must reactivate the ARCHIVELOG
mode and do a complete offline backup of the database.
Checking Extents using SAPDBA before Performing a Reorganization
Use SAPDBA to check the number of extents before performing a reorganization.
1. To show the current login NT user,
enter the command net config
workstation.
The Windows NT User DEVADM
should be seen directly beneath the
name of the local computer. If it is
not shown, log off and try again.
2. Click the Windows NT Start button
and choose Programs Command
Prompt.
3. Enter the command sapdba to start
the SAP Database Administration
program.
3
2
1
Performing Database Reorganization
Checking Extents using SAPDBA before Performing a Reorganization
1998 SAP Labs, Inc. 953
4. To reach the Reorganization menu,
enter option d.
5. Enter a to check extents and
fragmentation.
6. From the Check menu, reselect a to
check objects with at least a
specified number of extents.
4
5
6
Performing Database Reorganization
Checking Extents using SAPDBA before Performing a Reorganization
954 1998 SAP Labs, Inc.
7. Enter d to specify the least number
of extents the object must have for
the check.
8. Enter your specified number at the
Enter number of extents prompt (for
example, 10).
9. Now, select s to start the check.
10. The number of objects with up to
ten extents will appear at the
bottom of your screen. (In this
example, three objects have been
selected. Record the tablespace
names for future steps in this
chapter.)
11. Press the Return key to proceed.
7
8
9
10
11
Performing Database Reorganization
Checking Extents using SAPDBA before Performing a Reorganization
1998 SAP Labs, Inc. 955
12. Enter option q to return to the
Check screen.
13. From the Check screen, return to the
previous screen by entering q.
14. Re-enter q to return to the
Reorganization screen.
12
13
14
Performing Database Reorganization
Checking Extents using R/3 before Performing a Reorganization
956 1998 SAP Labs, Inc.
15. Re-enter q to quit SABDBA.
16. Enter y to confirm.
Checking Extents using R/3 before Performing a Reorganization
To check the number of extents before performing a reorganization using R/ 3:
1. Enter the transaction /nDB02 to
view the Database Performance
screen. 1
15
16
Performing Database Reorganization
Checking Extents using R/3 before Performing a Reorganization
1998 SAP Labs, Inc. 957
2. Click Checks.
3. Select the Extents of tables and indexes
button.
2
3
Performing Database Reorganization
Checking Extents using R/3 before Performing a Reorganization
958 1998 SAP Labs, Inc.
4. To begin sorting, click anywhere in
the Extents column.
5. Click Sort.
4
5
Performing Database Reorganization
Performing the Reorganization
1998 SAP Labs, Inc. 959
As a rule of thumb to judge which table, index, or tablespace needs to be reorganized, simply
calculate the difference between MaxEntents and Extents. If the difference is less than 100, then
you should reorganize. In this example, the difference of MaxExtents and the Extents of Table
D010Q of tablespace PSAPEL31HD is 289 (300-11). Since 289 exceeds 100, there is no need to
perform a reorganization! To show you how to reorganize a table, we will use D010Q as an
example.
In cases where reorganization is not possible, you may temporarily increase the MaxExtents
value for the table and index.
6. Click the Windows NT Start button
and choose Programs SAP R3
SAP Service Manager for PRD_01.
7. Click Stop to shutdown R/ 3.
8. Click OK to verify intentional
shutdown.
Performing the Reorganization
Before performing a reorganization, you must first backup the database! Refer to chapter 102,
Performing a Full System Backup using NT Backup and chapter 105, Performing Offline Backup
using SAPDBA for a detailed explanation of backup procedures.
The R/ 3 System must be stopped before continuing the following steps. Refer to chapter 63,
Starting and Stopping the R/3 System Using Service Manager for a detailed explanation of how to
stop the R/ 3 System.
6
7
8
Performing Database Reorganization
Performing the Reorganization
9510 1998 SAP Labs, Inc.
1. To show the current login NT user,
enter the command net config
workstation.
The Windows NT User DEVADM
should be shown directly beneath
the name of the local computer. If it
is not shown, log off and try again.
2. Click the Windows NT Start button
and choose Programs Command
Prompt.
3. Enter sapdba to start the SAP
Database Administration program.
4. Enter d to select Reorganization.
1
2
3
4
Performing Database Reorganization
Performing the Reorganization
1998 SAP Labs, Inc. 9511
You can reorganize several different ways, with a:
Single table and index
List of tables and indices
Single tablespace
Tablespace and data files
Reorganizing with a tablespace and data files will de-fragment the tablespace and compress
the data files used by that tablespace. In this example, we will reorganize the table D010Q of
tablespace PSAPEL31HD.
5. Enter c to select Reorganize single
table and index.
6. Enter b to select the Table or index
name.
7. Enter the name of the table to be
reorganized.
5
6
7
Performing Database Reorganization
Performing the Reorganization
9512 1998 SAP Labs, Inc.
8. Enter s to start the reorganization.
9. If you have backed up the database,
proceed with y. If not, enter n and
perform the full database backup
first.
Since our database has been backed
up, enter y to proceed.
Working
8
9
Performing Database Reorganization
Performing the Reorganization
1998 SAP Labs, Inc. 9513
10. Enter 1 to select Start script(s)
immediately.
Depending on the size of the table,
transport may take a while. After
transport, an index is created.
Reorganization is complete when
you see this message: Reorganization
SUCCESSFULLY completed.
11. Press Return to continue.
10
11
Performing Database Reorganization
Performing the Reorganization
9514 1998 SAP Labs, Inc.
12. Enter q to return to the previous
screen.
13. Re-enter q to return to the SAP
Database Administration screen.
14. Enter q to leave the SAP Database
Administration program.
15. Enter y to confirm that you really
want to quit.
12
13
14
15
Performing Database Reorganization
Checking Number of Extents After Performing Reorganization Using SAPDBA
1998 SAP Labs, Inc. 9515
Checking Number of Extents After Performing Reorganization Using SAPDBA
1. To show the current login NT user,
enter the command net config
workstation.
The Windows NT User DEVADM
should be shown directly beneath
the name of the local computer. If it
is not shown, log off and try again.
2. Click the Windows NT Start button
and choose Programs Command
Prompt.
3. Enter the command sapdba to start
the SAP Database Administration
program.
1
2
3
Performing Database Reorganization
Checking Number of Extents After Performing Reorganization Using SAPDBA
9516 1998 SAP Labs, Inc.
4. Enter d to begin the reorganization
process.
5. Enter a to Check extents and
fragmentation.
6. Enter a again to specify that you
want to check objects with a certain
number of extents.
4
5
6
Performing Database Reorganization
Checking Number of Extents After Performing Reorganization Using SAPDBA
1998 SAP Labs, Inc. 9517
7. Enter d to define a higher or equal
value of number of extents that you
want to view.
8. Since we have previously used 10,
re-enter this number.
9. Enter s to start the process.
10. Table D010Q is not included in the
list of the tables which has greater
than or equal to 10 extents. In this
case, the extent of table D010Q has
been reduced.
11. Press the Return key to continue.
7
8
9
10
11
Performing Database Reorganization
Checking Number of Extents After Performing Reorganization Using SAPDBA
9518 1998 SAP Labs, Inc.
12. Enter q to return.
13. Re-enter q.
14. Re-enter q to return to the SAP
Database Amdinistration screen.
12
13
14
Performing Database Reorganization
Useful OSS Notes
1998 SAP Labs, Inc. 9519
15. Enter q to quit.
16. Enter y to confirm that you really
want to quit.
Useful OSS Notes
Note # Description
44935 SAPDBA: Missing indexes after reorg run
44595 SAPDBA: General procedure for reorganizations
43487 Collective note: SAPDBA Reorganization
40521 Reorganization (external tools)
39650 Max. number of extents per tablespace
38006 Ora -1631 max extents reached. Which table?
29348 SAPDBA - Reorganization of single Table; PSAPTEMP
19193 SAPDBA - Size and reorg. of table space PSAPTEMP
12921 Reorganization of SYSTEM tablespace
12621 SAPDBA - speeding up reorganization
15
16
Performing Database Reorganization
Useful OSS Notes
9520 1998 SAP Labs, Inc.
For further details refer to
R/3 System Administration Made Easy
All chapters about Managing the Oracle Database for a R/ 3 System (Ch. 8295)
R/3 Basis Knowledge Products
Oracle Database Administration CD Reference Implementation Database Tools Database Tool
SAPDBA
R/3 System Online Help
Online Documentation CD Basis Components System Administration Database
Administration Oracle Database Administration Database
Reorganization
Basis Courses
Database Administration ORACLE (BC505)
R/3 System Administration Made Easy
41
Chapter 4: 8cheduled Daily Tasks
Contents
Overview..................................................................................................................42
Checklists ................................................................................................................43
Critical Tasks...........................................................................................................47
Verify that R/3 Is Running.........................................................................................47
Verify that the Backups Ran Successfully ................................................................47
R/3 Tasks ...............................................................................................................413
Check that All Application Servers Are Up (Transaction SM51).............................413
CCMS Central Alert Monitor (Transaction RZ20) ...................................................414
Failed Updates (Transaction SM13) .......................................................................419
System Log (Transaction SM21) ............................................................................423
Background Jobs (Transaction SM37)....................................................................427
Graphical Job Monitor (Transaction RZ01).............................................................429
Locks (Transaction SM12) ......................................................................................431
Active Users (Transactions SM04 and AL08).........................................................433
Check the Spool (Transaction SP01)......................................................................436
Batch Input Jobs, In-Error or To Be Processed (Transaction SM35) .....................438
Work Processes (Transactions SM50 and SM51)..................................................440
ABAP Dump Analysis (Transaction ST22) .............................................................442
Workload Analysis of the System (Transaction ST03) ...........................................445
Buffers (Transaction ST02).....................................................................................450
Database Tasks.....................................................................................................452
Checking the Database...........................................................................................452
Database Alert ........................................................................................................452
Database Error Logs...............................................................................................454
Operating System Tasks......................................................................................456
System Logs ...........................................................................................................456
Other Tasks ...........................................................................................................460
Check the Uninterruptible Power Supply................................................................460
Chapter 4: Scheduled Daily Tasks
Overview
Release 4.0B
42
Overview
Daily tasks are divided into the following categories:
< Problems that need to be fixed
< Indicators of developing problems
We have provided sample checklists that you may use and modify depending upon your
specific needs. The checklists provided for your convenience include:
< Critical tasks
< R/ 3 System
< Database
< Operating system
< Other
< Notes
Chapter 4: Scheduled Daily Tasks
Checklists
R/3 System Administration Made Easy
43
Checklists
System: __________
Date: ____/ ____/ ____
Admin: _____________________
Critical Tasks
Task Transaction -
Description
Procedure Check off/
initial
Check that the R/ 3 System
is up.
Log on to the R/ 3 System
DB12
Backup Logs:
Overview
Check database backup
Database backup run time
Check operating system level backup
Operating system backup run time
Check that daily backups
executed without errors.
R/3
Task Transaction -
Description
Procedure Check off/
initial
Check that all application
servers are up.
SM51 SAP
Servers
Check that all servers are up.
Check the CCMS alert
monitor (4.0+).
RZ20 CCMS
Monitor (4.0)
Look for alerts.
Check work processes
(started from SM51).
SM50
Process
Overview
All work processes with a running or a
waiting status
< Set date to one year ago
< Enter * in the user ID
< Set to all updates
Look for any failed
updates (update
terminates).
SM13
Update
Records
Check for lines with Err.
Chapter 4: Scheduled Daily Tasks
Checklists
Release 4.0B
44
R/3 {contd.}
Task Transaction
Description
Procedure Check off/
initial
Set date and time to before the last log
review.
Check System Log SM21- System
Log
Check for:
< Errors
< Warnings
< Security messages
< Abends
< Database problems
< Any other different event
Enter * in User ID
Verify that all critical jobs were
successful.
SM37 Select
Background
jobs
Review any cancelled jobs.
Review for cancelled and
critical jobs
RZ02
Graphical Job
Monitor
Same as for SM37
Enter an asterisk (*) for user ID. Check for old locks SM12 Lock
Entry List
Check for entries for prior days.
Check users on system SM04 Users
AL08 Users
Review for an unknown or different user
ID and terminal. This task should be done
several times a day.
Check for spool problems SP01 Spool:
Request
Screen
Look for spool jobs that have been in
process for over an hour.
Check job log SM35 Batch
input: Initial
Screen
Check for:
< Jobs to be processed
< Jobs in error
Check work processes SM50/51
Processes
Chapter 4: Scheduled Daily Tasks
Checklists
R/3 System Administration Made Easy
45
R/3 {contd.}
Task Transaction
Description
Procedure Check off/
initial
Review and resolve
dumps.
ST22 - ABAP
Dump
Analysis
Look for an excessive number of dumps.
Look for dumps of an unusual nature.
Review workload
statistics.
ST03
Workload:
Analysis of
<sid>
Review buffer statistics. ST02 Tune
Summary
Look for swaps.
Database
Task Where Procedure Check off/
initial
AL02
Database alert
Review error log for
problems.
ST04 DB
Performance
Analysis:
Oracle
Chapter 4: Scheduled Daily Tasks
Checklists
Release 4.0B
46
Operating 8ystem
Task Where Procedure Check off/
initial
AL16 OS
Alerts
Review UNIX system logs
for problems.
OS06 OS
Monitor
Review operating system log
NT system
log
Look for any errors or failures.
Check for failed logon attempts to the
SAP servers.
NT security
log
Look for errors or failures.
Review NT system logs for
problems.
NT
application
log
Look for errors or failures.
Other
Task Where Procedure Check off/
initial
Check the uninterruptible
power supply (UPS).
UPS program
log
Review for:
< Events
< UPS self test
< Errors
Notes
Problem Action Resolution
Chapter 4: Scheduled Daily Tasks
Critical Tasks
R/3 System Administration Made Easy
47
Critical Tasks
There are a few critical tasks that should be completed as soon as you arrive in the office
each day. These tasks answer the following questions:
< Is the R/ 3 System running?
< Did the backups execute and complete successfully?
If the answer to either question is no, then the situation must be resolved quickly because:
< If the R/ 3 System is down, no work can be done.
< If the backups failed, and a disaster occurs, you could lose all the data since your most
recent good backup.
Verify that R/3 s Running
Your first task when you arrive at work is to check that the R/ 3 System is running. This task
is a high-level check to see if R/ 3 is up, and whether or not you can connect to it.
Why
If the system is not running, your users will be calling to find out what happened and when
the system will be up again.
As a basic level check, if you can connect to the R/ 3 System, the following questions are
answered:
< Is the R/ 3 System working?
< Is the network between you and the R/ 3 System working?
How
From a workstation, log on with the SAPgui.
If you can log on, the test is successful.
Verify that the Backups Ran 8uccessfully
What
You need to verify that the backups that were supposed to run last night, ran successfully.
Backups of the R/ 3 database and related nondatabase operating system level files are
essential to recover the R/ 3 System.
Types of nondatabase files include:
< Database log dumps
< Data files for third-party applications that do not store their data in the system, such as
external tax files
< Transport files
< Inbound and outbound interface files
< Externally stored print files
Chapter 4: Scheduled Daily Tasks
Critical Tasks
Release 4.0B
48
Why
If there is a problem with any of the backups, the problem needs to be quickly resolved. If a
database failure occurs that requires a restore, and the last backup failed, you will have to
recover using the last successful backup that you have. If you do not have a good (usable)
backup, you will have to go further back. This requires the application of more logs the
further back you go, and increases the time required to restore the database and bring it
current.
Once the problem has been fixed, if it does not significantly impact performance, execute an
online backup. Even if it impacts performance, your company may make it policy to run the
online backup. This gives you a more recent backup.
At the operating system level, some of these files may need to be in sync with the R/ 3
database. Restoring the R/ 3 System without these files results in an incomplete (unusable)
restore (for example, external tax files that need to be in sync with the system data or the tax
systems reports will not match the R/ 3 reports).
When
These critical tasks need to be done first thing in the morning. If there is a graveyard
operations shift, it should be done once the backup job is complete. The graveyard shift is
the third-shift of the day, typically covering the period from 10:00 PM to 7:00 AM.
Any failed backup must be immediately investigated and resolved. Do not maintain a we
will just run the backup again tonight and see if it works attitude. If that backup fails, you
have another day without a backup.
Chapter 4: Scheduled Daily Tasks
Critical Tasks
R/3 System Administration Made Easy
49
Database
Guided Tour
1. In the Command field, enter transaction DB12 and choose Enter
(or choose Tools CCMS, then DB Administration Backup logs).
2. Record the date and time that
appears next to the button Last
successful DB backup.
3. If there was a failed backup, the
button Last unsuccessful database
backup will appear.
4. Choose Overview of database backup
logs.
5. Examine the Start of backup and
End of backup times, and then
compute the runtime.
6. Compare the actual backup
runtime to the expected runtime.
If the actual backup time is shorter
or longer than expected,
investigate for potential problems.
7. RC (return code) definitions:
< 0000 (Successful)
< 0001 (Success with warnings)
< 0003 (Error in initialization)
< 0005 (Error in processing)
< 9999 (Started)
2
7
5
4
Chapter 4: Scheduled Daily Tasks
Critical Tasks
Release 4.0B
410
Operating 8ystem Level Backups
General process is as follows:
< Record the usual or expected run time for the backup.
< Compare the actual backup time to the expected (usual) run time for the backup.
If the backup takes longer or shorter than this time, there may be a problem that needs
to be investigated.
Any failed backup must be immediately investigated and resolved.
UNX
For your UNIX level backup, review using the appropriate UNIX backup application.
NT
We assume that you are using the NTBackup application. If you are using another program,
use that programs documentation to determine its status after backup.
NTBackup records some log information in the NT event logs. A more specific log is written
to a file as specified when NTBackup is run.
Guided Tour
1. From Windows NT, choose Start
Programs Administrative tools
Event viewer.
Create a shortcut on your desktop to
the Administrative tools group.
2. Choose Log Application.
3. Under Source, look for the
NTBackup entries.
4. Check for error messages, which
are indicated in red.
3
2
Chapter 4: Scheduled Daily Tasks
Critical Tasks
R/3 System Administration Made Easy
411
Possible causes for errors include:
< Tape door or lever is not
completely closed.
< Tape head is dirty.
< Tape is damaged or worn out.
< No tape inserted in tape drive.
< File has been written to and
changed between the time that
the backup was done and when
the file verification was made.
5. To view the details for a line entry,
double-click on the line. This view
will give you a bit more
information.
Review the NTBackup log
If the event log indicates problems,
1. Review the NTBackup log to determine more specifically what the error was.
2. Then using that information, take corrective action.
The NTBackup log is by default: c:\ winnt\ backup.log.
If the NTBackup writes to a different file or directory, you need to review that file.
Chapter 4: Scheduled Daily Tasks
Critical Tasks
Release 4.0B
412
1. In Explorer, select the directory
c:\ Winnt.
2. Double-click on Backup.log.
Backup.log is a text file. This step
assumes that you have Notepad
associated with the extension log.
3. Scroll through the file to look for
any problems.
4
5
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
413
R/3 Tasks
Check that All Application 8ervers Are Up {Transaction 8M51}
What
Transaction SM51 allows you to look at all the servers in your system (for example, the PRD
database server and all of its application servers). You do not have to log into each server
individually.
Why
< If one of your dialog application servers is not up, the users who normally log on to that
application server will not have a server to log on to.
< If the batch application server is down, batch jobs that are specified to run on that server
will not run.
Guided Tour
1. In the Command field, enter transaction SM51 and choose Enter
(or choose Tools Administration, then Monitor System monitoring Servers).
2. Review the list of instances under
Server name.
Verify that all your instances are
listed. If it is listed, it is up and
running.
2
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
414
CCM8 Central Alert Monitor {Transaction RZ20}
What
Transaction RZ20 is a centralized alert monitor and is new with Release 4.0. With this
transaction, you can monitor the servers in your landscape, such as development, QA,
testing, production, and so on. You no longer have to individually log into each system to
search for alerts. If there is an alert, the monitor will link to many of the other transactions
later in this chapter.
See chapter 5, Changing Alert Threshold, for setting the alert threshold levels.
You can do many of your system monitoring tasks with the Central Alert Monitor.
The Central Alert Monitor is not a replacement for examining the other checklist tasks, as
not all alerts have been included in the 4.0 Release
Oracle database alerts have been added in Release 4.5.
Why
An alert indicates a potentially serious problem that should be quickly resolved. If not
contained, these problems could degenerate into a disaster.
Guided Tour
1. In the Command field, enter transaction RZ20 and choose Enter
(or choose Tools CCMS, then Control/Monitoring Alert Monitor 4.0).
2. Click the node next to the server to
expand the server options.
2
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
415
3. Double-click on the monitor (for
example, Basic monitor) under the
server Monitor sets (for example,
the server monitor set is SAO).
4. Look for any alerts, which are
indicated in red.
5. Click the node next to the <sid>
(for example, SAO) to drill down
for additional details.
This example follows an alert down to
the paging rates.
6. Select the alert (for example
Page_Out).
7. Choose Display alerts.
5
6
3
7
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
416
To get detail for the alert:
8. Select the alert item.
9. Choose Choose detail (magnifying
glass icon).
10. Review the details.
11. Choose Back.
To acknowledge the alert:
12. Select the alert item(s).
< Alert (red)
< Warning (yellow)
13. Choose Complete alerts.
You still have to perform a task based
upon the alert.
Acknowledging the alert only
means you received the alert
notification, nothing else.
12
13
11
9
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
417
14. When all alerts and warnings are
acknowledged, the alert will
change to green (example
Page_In).
14
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
418
Beginning Your Alert Analysis
To get more details on the alert, you
can start the analysis tool.
From the previous screen:
1. Select the alert (for example,
Page_Out).
2. Choose Start Analysis tool.
This screen is only an example. The
final transaction you go to differs
depending on which branch of the
alert tree you follow.
1
2
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
419
Failed Updates {Transaction 8M13}
What
A failed update or an update terminate is an update to the database that failed. These
failed updates occur when a user entry or transaction is not entered or updated in the
database. The following analogy should help clarify this concept:
Analogy:
1. A secretary gives a file clerk a folder (similar to a save or execute).
2. The file clerk gives the secretary a receipt (similar to the R/ 3 document number).
3. On the way to the file cabinet, the clerk falls, and gets hurt.
The folder never makes it to the cabinet (this is the failed update).
4. The end result is the folder is not in the cabineteven though the secretary has the
receipt.
For performance reasons, the database update is done in asynchronous mode. In this mode,
the user continues to work while the system takes over the update process and waits for the
database update to complete.
In synchronous mode, users would have to wait until the database has successfully updated
before they could continue to work.
Why
The users probably received a document number, so they assume that the entry is in the
system; however, if a failed update occurred, it is not. If this were a customer order, unless
the order is reentered, the customers would not get their order and no trace of it would be
found in the system!
When
You should check the system for failed updates several times a day.
During a dayshift, the checks can be distributed:
< First thing in the morning
< Late morning
< Early afternoon
< Late afternoon
If you have a global operation, your schedule should be adjusted to account for other time
zones and someone in that time zone should participate in the monitoring.
The longer you wait after the update terminate has occurred, the more difficult it is for users
to remember what they did when the update terminate occurred. If you wait too long, the
user will not remember.
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
420
On Windows NT, from R/ 3 Release 3.0F and higher, system log entries are written to the
NT event log. You might consider configuring an event log monitor to page you when an
update terminate occurs. This reduces the need to constantly check the SM13 transaction. It
also reduces the exposure between when the times update terminate occurs, and when you
find out about it, and therefore when you can get to the user.
Guided Tour
1. In the Command field, enter transaction SM13 and choose Enter
(or choose Tools Administration, then Monitor Update).
2. Enter * in Client.
3. Enter * in User.
4. Under Status, select All.
5. Change the date to a year ago (for
example, 12/04/1997) in From
date.
6. Choose Enter.
7. Look for entries with an Err in the
Status column.
These entries are failed updates or
update terminates. You may also
see other entries listed without the
Err status.
If you have no failed updates, you
may stop here. If you do have
failed updates, continue with the
next section, Managing Update
Terminates.
7
4
5
6
3
2
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
421
Managing Update Terminates
If you have failed updates, proceed with the following steps:
1. Double-click on an entry with an
Err status.
This screen shows in what module
(Mod.name) and where in the
process (Mod.ID) that the update
terminate occurred.
2. Double-click on the entry with an
Err status.
3. Choose ABAP short dump.
If a short dump exists, it will
appear.
2
3
1
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
422
4. This screen shows an ABAP dump
for the update terminate.
Some problems that can occur with an update terminate include:
< No short dump
In this case, the only clues you have are the:
User ID
Date
Time
Transaction
< Difficulty reading the short dump
Do not be discouraged because you cannot understand a short dump. The ability to read
a short dump comes with experience and practice. Some of a short dumps content is
only useful to the developer. You may recognize a pattern of characters as a part
number, document number, vendor code, and so on.
< Short dump with little usable information
< Update terminate occurring downstream from the actual transaction
The data in the short dump may be of little value in finding the root source of the update
terminate (for example, if the terminate occurred in the FI posting of an SD transaction,
you do not know which SD transaction document caused the problem).
< Update terminate occuring in a batch job
There is no indication of which batch job (by job name) caused the update terminate.
Not being able to identify the batch job that was the source of an update terminate is a
known issue.
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
423
5. The users need to be contacted. They should check for the missing entry and reprocess
the missing transaction.
Do not attempt to reapply the failed update! There are conditions under which this can
lead to corruption of the database.
Always advise users to reenter the transaction.
User Training
Assuming you are not using SAPoffice, when a user receives a popup message, it usually
signals a problem. The message reads:
You have express mail in your inbox.
The user should immediately stop and get assistance to determine what has happened. R/ 3
uses express mail to notify the user of a failed update. It is during this short period
immediately after the error has occurred that the user has the best chance of correcting the
error.
8ystem Log {Transaction 8M21}
What
The system log is the R/ 3 Systems log of events, errors, problems, and other system
messages.
Why
The log is important because unexpected or unknown warnings and errors could
indicate a serious problem.
Notes
The ability to properly monitor the system log comes with experience. Over time, you
will become familiar with what log entries normally appear in your system log, and
pick out the unusual ones that need investigation.
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
424
Guided Tour
1. In the Command field, enter transaction SM21 and choose Enter
(or choose Tools Administration, then Monitoring System log).
2. Enter the beginning date and time
that you want to review from the
log in From date/time.
You can also enter an end date
and time if you want to view a
specific time period.
3. Choose Reread system log.
To make reviewing the log easier, under Problem classes select one of the following, one at a
time:
< Problems only
< Problems and warnings
< All messages
These options allow you to view the system log in the following priority layers:
< Problems
< Problems and warnings
< All messages
2
3
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
425
4. If you select Problems only, you
will see this screen.
4. If you select All messages, you will
see this screen.
5. Notice that the warning messages
on this screen (indicated by the
yellow W under the column C, and
the text entry Perform rollback) did
not appear in the previous screen.
6. You can get more information on
certain entries. In this example,
double-click on the short dump.
What to look for:
< Unusual entries
Before you can recognize the unusual entries, you will need to become familiar with which entries are
in the log under normal conditions (for your installation for a specific system).
< Column C for the error status
Errors are the red Ks and warnings are the yellow Ws. These entries may have been examined when
you did the Alert Monitor (RZ20).
5
6
5
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
426
To minimize the video-processing overhead, many NT servers are configured with a video
color depth of 16 colors. On these servers, increase the video color depth to 256 colors to
see the alerts in color, or view the log from a computer that has the video set to a color
depth of 256 colors (or more).
7. Choose Analyze errors.
8. This screen is the short dump. You
can access this screen using
transaction ST22.
7
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
427
Background Jobs {Transaction 8M37}
What
Background jobs are batch jobs scheduled to run at specific times during the day.
Why
If you are running critical jobs, you need to know if the job failed because there may be
other processes, activities, or tasks that are dependent on these jobs.
How
You should have a list of all the critical jobs scheduled to run. For each of these jobs, you
should have a list that shows:
< When they are scheduled to run
< The expected run time
< Emergency contact (names and phone numbers) if a job fails or has problems
< Restart or problem procedure for the job
Guided Tour
1. In the Command field, enter transaction SM37 and choose Enter
(or choose System Service, then Jobs Job overview).
2. Enter * to get all jobs in Job name.
3. Enter either * (for all users) or the
user ID that the batch jobs run
under (to limit the display to those
scheduled under a specific user ID
in User name).
4. Enter a start date in From.
5. Enter an end date in To.
6. Under Only jobs with status, select:
< Active
< Finished
< Terminated
7. Choose Enter.
6
2
4
7
3
5
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
428
8. Check for failed or cancelled jobs.
Analyze why jobs failed or were
cancelled and make the necessary
corrections.
9. Check critical jobs such as MRP,
check payment jobs, and so on.
You need to know the job name
that they run under to do this.
To check a job log:
10. Select the job.
11. Then choose Job log.
Check job performance and record
run times. A deviation from the usual
run time on a job may indicate a
problem and should be investigated.
8 11
10
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
429
Graphical Job Monitor {Transaction RZ01}
What
The graphical job monitor is useful when coordinating many background jobs because it
allows you to see individual job statistics.
Why
The graphical job monitor is a more visually oriented format in which status is indicated by
color:
< Aborted job (red)
< Active job (blue)
If a job ran past its expected end time, and other jobs are scheduled to start, the graphical job
monitor lets you see the conflict.
Guided Tour
1. In the Command field, enter transaction RZ01 and choose Enter.
2. Choose Time unit Hour to get a
more usable time scale. 2
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
430
3. Choose Legend to get a popup
legend of the colors or patterns
used.
3
3
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
431
Locks {Transaction 8M12}
What
A lock is a mechanism that prevents other users from changing the record on which you
are working. An example that illustrates the importance of using this function follows.
Example: You are changing a customer mailing address. Someone else is changing the
customers telephone number at the same time. You save your change first; then the other
person saves their change. The other persons change overwrites your change, and your
change will be lost.
Why
There may be old locks still in place from transactions that did not release, or from when
the user was cut off from the network. Unless cleared, these locks prevent access or change
to the record until the system is cycled. The easiest way to locate them is to look for locks
from prior days.
Important: We presume that the profile parameter rdisp/gui_auto_logout has been set. This
parameter defines an automatic logout of the user if there is no activity for the set number of
minutes.
Setting the auto_logout parameter is recommended for security. It is also an item that your
external auditors may test for.
The parameter auto_logout is a global setting that applies to all users on the instance.
You cannot have different logout times for different groups of users, on the same
instance.
The only way to have different logout times for different groups of users is to have
specific groups (for example, Finance) log in to specific instances (for example, the
Finance application server) where the auto_logout parameter is set in the instance profile
of that instance.
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
432
Guided Tour
1. In the Command field, enter transaction SM12 and choose Enter
(or choose Tools Administration, then Monitor Lock entries).
2. Enter * in Client.
3. Clear the User name field.
4. Choose Enter.
5. Look for locks from previous days
in the Time column.
The presence of a lock from a
previous day could mean that the
user was disconnected from the
network and the R/ 3 System.
Deleting a lock is a dangerous task!
Do not delete a lock without checking to first see if it is in use. You risk corrupting the
database if you delete a lock that is in use.
To clear a lock, complete these steps on the systems application and the database servers:
1. Check that the user is not logged on any of the servers with transaction SM04 (no
application servers) or AL08 (with application servers).
If the user is not on the system, but transaction SM04 shows them on the system, delete
their sessions as described in chapter 9, Deleting a Users Session. This step, by itself, may
clear the lock.
3
2
4
5
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
433
2. Check that there are no processes running under the user ID using transaction SM50 or
SM51 (see Processes later in this chapter).
3. Check that there are no batch jobs running under the user ID using transaction SM37
(see Background Jobs earlier in this chapter).
4. Check that there are no updates in process for that user ID using transaction SM13 (see
Failed Updates earlier in this chapter).
5. Once you know that there is no activity using the users ID, select the lock entry for
deletion.
Double-check the user ID of the entry that you selected to delete. If you delete the wrong
lock, you could corrupt the database.
6. Choose Lock entries Delete.
Clear only one lock entry at a time.
Do not use the mass delete option. The mass delete option will delete all the locks, not just
the ones for the user you have selected.
Active Users {Transactions 8M04 and AL08}
What
These transactions display all the users who are currently logged on to the system. They
show both the users ID and terminal name.
Why
In a smaller company, the administrator can recognize user IDs logged on to unfamiliar
terminals. This may indicate that someoneother than the designated useris using that
user ID.
If a user is logged on to more than one terminal, this may indicate:
< The user ID is being used by someone else.
< The user ID is being used/ shared by several people.
User IDs should not be shared for several reasons.
< One reason is that if a problem arises, you will not know who created the problem.
This makes the problem difficult for you to fix and prevent from happening again.
< Prudent security practices do not allow for sharing of user IDs.
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
434
Your external auditors may also perform this test to test your security.
Problems
Transaction SM04 may show a user as active, when in fact the user has actually logged off.
Because the user session was not properly closed, the system thinks that the user is still
logged on.
This condition can be caused by the following (among others):
< A network failure, which cuts off the user
< The user turning off their computer without logging off from the R/ 3 System.
8ingle-nstance 8ystem {Transaction 8M04}
Guided Tour
1. In the Command field, enter transaction SM04 and choose Enter
(or choose Tools Administration, then Monitor System monitoring User overview).
2. Select the user ID (for example,
NAKAYAMAG) to view the
session the user has open.
3. Choose Sessions.
The Overview of Sessions screen
shows what sessions the user has
open.
4. Choose Enter.
2
4
3
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
435
Multi-nstance 8ystem {Transaction AL08}
If you have several instances in your system, using AL08 is an easier method, as you can
see all users in all instances on the system at once.
1. In the Command field, enter transaction AL08 and choose Enter
(or choose Tools CCMS, then Control/Monitoring All work processes, and then Goto Global users
overview).
2. The Current Active Users screen
shows all the instances in your
system.
3. For each instance is listed the users
logged into that instance/
application server.
2
3
2
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
436
Check the 8pool {Transaction 8P01}
What
The spool is the R/ 3 Systems output manager. Data sent to the printer is sent to the R/ 3
spool and then sent to the operating system to print.
Why
There may be problems with the printer at the operating system level. These problems need
to be resolved immediately for time-critical print jobs (for example, checks, invoices,
shipping documents, and so on) or there may be an operational impact.
You should check for active spool jobs that have been running for over an hour. These long-
running jobs could indicate a problem with the operating system spool or the printer.
Guided Tour
1. In the Command field, enter transaction SP01 and choose Enter
(or choose System Services Output controller).
2. Clear User name.
3. Set the From date to a week ago.
4. Clear Client.
5. Choose Enter.
2
5
4
3
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
437
6. Look for jobs with an error in the
Output Status column. In this
example, no errors appear.
6
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
438
Batch nput Jobs, n-Error or To Be Processed {Transaction 8M35}
What
This transaction shows jobs that need to be processed or started, and jobs with errors that
need to be resolved.
Why
This transaction is important because it alerts you to batch input jobs that:
< Need to be processed
These are jobs that are waiting to be processed (for example, a posting from an interface
file). If not processed, the data will not post to the system.
< Are in error
These are jobs that have failed due to an error. The danger is that only a portion of the
job may have posted to the system. This increases the potential for data corruption of a
different sort, as only part of the data is in the system.
Guided Tour
1. In the Command field, enter transaction SM35 and choose Enter
(or choose System Services Batch input Edit).
2. Enter a start date of at least a week
ago (or even further back if people
are not good about resolving these
jobs) in Creation date from.
3. Under Session status, select both:
< To be processed
< Incorrect
These selections display only the
batch jobs that need to be
processed and those with errors
that need to be resolved.
4. Choose Enter.
3
2
4
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
439
5. Contact the responsible user to
notify them or determine why
these jobs are in:
A. Sessions still to be processed
B. Errors in sessions
5A
5B
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
440
Work Processes {Transactions 8M50 and 8M51}
What
Process overview transactions allow users to view the status of work processes and monitor
for problems. Transaction SM51 is a central transaction from which you can select the
instance to monitor. SM51 starts transaction SM50 for each application server. Transaction
SM50 is used for a system without application servers.
Why
Transaction SM51 is one place to look for jobs or programs that may be hung, which
would be indicated by long run times. If batch jobs are not running, transaction SM50 may
provide a hint of the problem, if all the batch work processes are in use.
For a 8ystem with Application 8ervers
Guided Tour
1. In the Command field, enter transaction SM51 and choose Enter
(or choose Tools Administration, then Monitor System monitoring Servers).
2. Select the instance you want to
view (for example,
pa100767_SAO_01).
3. Choose Processes.
4. This is the Process Overview
transaction (SM50) for that
instance.
2
3
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
441
For a 8ystem Without Application 8ervers
Guided Tour
In the Command field, enter transaction SM50 and choose Enter
(or choose Tools Administration, then Monitor System monitoring Process overview).
What to look for:
A. Dialog work processes (DIA) that
have long time values.
These values could indicate a
problem, or a long running step in
batch programs, which sometimes
start dialog work processes.
B. Work processes with a stopped
status. These can sometimes be a
problem because a process may
have stalled or failed.
Some of the column definitions are:
Column Text Definitions
No Work process number
Ty Type of work process
PID OS PID (Process ID) number
Status Current status of the work process
Err Number of detected errors in the work process
CPU Cumulative CPU time that the current process is taking
Time Cumulative wall time that the current process is taking
Program Name of the ABAP program
Clie Client number
User User ID that is using the work process
Table Table that the action is being performed on
A
B
B A
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
442
ABAP Dump Analysis {Transaction 8T22}
What
An ABAP dump (also known as a short dump) is generated when a report or transaction
terminates as the result of a serious error. The system records the error in the system log
(transaction SM21) and writes a snapshot (dump) of the program termination to a special
table.
This transaction can also be called from the system log (transaction SM21).
Why
You use an ABAP dump to analyze and determine why the error occurred, and take
corrective action.
Guided Tour
1. In the Command field, enter transaction ST22 and choose Enter
(or choose Tools Administration, then Monitor Dump analysis).
There are two selection methods to display the list of dumps.
< For simple selection; today or yesterday (go to step 2)
< For free selection (go to step 5)
8imple 8election
2. Under No. of short dumps, if you
see a value other than zero (0) in
Today or Yesterday, dumps have
occurred that need to be
examined.
3. Select Today.
4. Choose Display list to get a list of
short dumps for the day.
Go to step 8.
2 3
4
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
443
Free 8election
5. Choose Selection.
6. Enter your selection criteria in the
ABAP Dump Analysis screen.
7. Choose Execute.
8. Double-click on the dump you
want to analyze.
8
7
5
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
444
9. This screen shows the short
dump.
Despite being called a short dump, ABAP dumps may be more than 75 pages in length. We
recommend you save the dump to a file on your PC and print out only the portion you need.
If the SAP hotline asks for a copy of the short dump. It is easier to e-mail or upload the file (see
Online Service System Note 40024), rather than fax the entire dump.
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
445
Workload Analysis of the 8ystem {Transaction 8T03}
What
Workload analysis is used to determine system performance.
How
You should check statistics and record trends to get a feel for the systems behavior and
performance. Understanding the system when it is running well helps you determine what
changes may need to be made when it is not.
Guided Tour
1. In the Command field, enter transaction ST03 and choose Enter
(or choose Tools Administration, then Monitor Performance, then Workload Analysis).
2. Choose Data base server (for
example, nspalss1) or This
application server.
2
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
446
3. Select a time period to analyze.
Options include:
< Single stat. records
< Todays workload
< Performance database
< Last minute load
< Local alert monitor
For this example, choose Last
minute load.
4. Enter how many minutes back to
analyze, or choose Other selection
to specify a date and time period
to analyze.
For this example, choose Other
selection.
5. Under Time interval to be analyzed
is, enter the date and time range to
be analyzed.
6. Choose Enter.
3
4
5
6
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
447
7. Examine Av. response time.
If this value is less than 1,000 ms (1
second), the response time meets
the target response time.
Judgment must be applied when
reviewing statistical values. If you just
started the R/ 3 System, the buffers
will be empty and many of the
statistics will be unfavorable. Once the
buffers are loaded, values can be
properly evaluated.
Thus this example of an Av response
time of over 4 seconds must be
evaluated with other factors in mind.
If your default profile for decimal point,
(point or comma) is not set, the
display may be misread. The R/ 3 user
default for a decimal point is a comma.
8. Choose Transaction profile.
Analysis of transaction ST03 is covered in the BC315 Workload Analysis and Tuning class.
We recommend that you take this class.
7
8
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
448
9. Click on any cell in the Response
time avg column (for example, 77).
10. Choose Sort.
11. From this screen, you can review
transactions in order of average
response time.
See the following table for known
long-running transactions.
10
9
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
449
A few standard functional transactions will exceed the one-second guideline. They include:
Type Transaction Approx . time (ms)
Create Sales Order VA01 1,500
Change Sales Order VA02 1,500
Display Sales Order VA03 1,000
Create Billing Document VF01 1,500
Create Delivery VL01 2,000
Maintain Master HR data PA30 1,000
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
Release 4.0B
450
Buffers {Transaction 8T02}
What
The buffer tune summary transaction displays the R/ 3 buffer performance statistics. It is
used to tune buffer parameters of R/ 3 and, to a lesser degree, the R/ 3 database and
operating system.
Why
The buffer is important because significant buffer swapping reduces performance. Look
under Swaps for red entries. Regularly check these entries to establish trends and get a feel
of the buffer behavior.
Guided Tour
1. In the Command field, enter transaction ST02 and choose Enter
(or choose Tools Administration, then Monitor Performance, and then Setup/Buffers
Buffers).
A
B
Chapter 4: Scheduled Daily Tasks
R/3 Tasks
R/3 System Administration Made Easy
451
2. The two important things to review on the above screen are:
A. Hit Ratio, for which the target value is 95 percent and higher
Soon after starting the system, this value is typically low, because certain buffers are
empty. The hit ratio will increase as the system is used and the buffers are loaded. It
usually takes a day to load the buffers that are normally used.
B. Swaps, for which the target value is less than 1,000
Swaps occur when the necessary data is not in the buffer. The system has to retrieve
the data from the database. The swap value is reset to zero (0) when the system is
restarted.
Analysis of transaction ST02 is covered in the BC315 Workload Analysis and Tuning
class. We recommend that you take this class.
Chapter 4: Scheduled Daily Tasks
Database Tasks
Release 4.0B
452
Database Tasks
Checking the Database
Oracle
To see if the database is running correctly:
1. Review the database check job using transaction DB16 (scheduled using DB13Check
database).
2. Review the tablespace percent utilization every day.
3. Identify an action point where you will increase a tablespace by adding another data
file (for example, 85 percent).
4. Schedule a job (using DB13-Adapt next extents) to adapt the next extent size for your
Oracle database.
This step significantly reduces the frequency of table reorganizations.
Database Alert
Guided Tour
Database alerts do not appear on the
4.0 Alert Monitor (RZ20). The database
alerts and Alert Monitor are added in
Release 4.5A.
1. In the Command field, enter
transaction AL02 and choose Enter
(or choose Tools Administration,
then Monitor Performance, and
then Alerts Global Database
system).
2. Clicking on a category with an
alert brings up another screen
with additional detail.
In this example, we selected
Freespace management.
2
Chapter 4: Scheduled Daily Tasks
Database Tasks
R/3 System Administration Made Easy
453
3. Drill down on Tablespace
PSAPBTABD to see the next
screen.
This screen shows the forecast
based on history.
Apply your knowledge of the
system and your business when
reviewing any forecasts.
The example shows two events
that cause the reduction in
freespace. The forecast however is
based on a steady state average of
the two events.
A. The vertical line indicates
today.
B. Left of the vertical line is the
past.
C. Right of the vertical line is the
future.
3
A B C
Chapter 4: Scheduled Daily Tasks
Database Tasks
Release 4.0B
454
Database Error Logs
What
The database error log is the record of database-level errors.
Why
Database error logs may indicate a database problem that is not reported in other locations.
Guided Tour
1. In the Command field, enter transaction ST04 and choose Enter
(or choose Tools CCMS, then Control/Monitoring Performance Menu, then Database Activity).
2. Choose Goto Database log.
3. In the Database Messages window,
select Only alerts.
This selection reduces the amount
of text to look through in the first
pass.
During a second pass through this
transaction, select All messages.
4. Choose Display.
4
3
2
Chapter 4: Scheduled Daily Tasks
Database Tasks
R/3 System Administration Made Easy
455
5. Scroll down the log to check for
error messages.
Chapter 4: Scheduled Daily Tasks
Operating System Tasks
Release 4.0B
456
Operating 8ystem Tasks
8ystem Logs
What
The system logs are where the operating system and some applications write event records.
Depending on the operating system, there may be multiple logs.
Why
There may be indications of a developing problem (for example, a hard drive generating
errors or a failing drive that needs to be replaced).
Getting a Ouick Visual View
Guided Tour
Use the operating system alert monitor for a quick visual review.
1. In the Command field, enter transaction AL16 and choose Enter
(or choose Tools CCMS, then Control/Monitoring Performance Menu, and then Alerts Local
Operating system).
2. Review this screen for potential
problems.
Chapter 4: Scheduled Daily Tasks
Operating System Tasks
R/3 System Administration Made Easy
457
Going to the Operating 8ystem Log
To get the operating system log, perform the following steps:
1. In the Command field, enter transaction OS06 and choose Enter
(or choose Tools CCMS, then Control/Monitoring Performance Menu, and then Alerts Local
Activity).
2. Choose Detail analysis menu.
3. Choose Operating system log.
3
2
Chapter 4: Scheduled Daily Tasks
Operating System Tasks
Release 4.0B
458
These screens show the operating
system logs.
In this example, it is the NT event
log.
In this example, it is the UNIX log.
Chapter 4: Scheduled Daily Tasks
Operating System Tasks
R/3 System Administration Made Easy
459
NT Event Logs
What
NT has three event logs:
< System
< Security
< Application
Why
There may be indications of a developing problem. If the security audit parameters have
been properly set, you could detect unauthorized attempts to access files.
Configuring the security audit function is a tradeoff among the:
< Need to log security events.
< System resources used to track and maintain the log. The more detailed the log, the
more degraded the system performance.
< Effort required to audit the log (dependent on the size of the log).
Guided Tour
The following steps show you how to open the NT event logs.
1. On the NT desktop, choose Start Programs Administrative Tools Event Viewer.
2. The different logs can be selected
under Log.
3. Look for unusual entries.
These entries require regular
monitoring to recognize an
unfamiliar event, such as errors,
failures, or security-related entries
which do not normally occur.
2
Chapter 4: Scheduled Daily Tasks
Other Tasks
Release 4.0B
460
Other Tasks
Check the Uninterruptible Power 8upply
What
The uninterruptible power supply (UPS) that you use should be monitored by a control
program. The control program, triggered by a power event, records the event and initiates a
shutdown process of the R/ 3 environment (R/ 3, the database, related applications, and the
operating system), and finally the server. In addition, most UPSs have a self-test and
capacity calibration function. The results of these tests are logged. The logging depends on
the program.
Why
You need to review the power events that triggered the UPS control program.
While the UPS protects the server, the control program should be recording power
events such as power dips, brown outs, power failures, and so on. This recording could
help you or the facilities person solve electrical problems in the facility. For example, if
you regularly see a power dip or outage at a particular time, this may be the indication of
a problem elsewhere in the building.
You need to verify that:
< The UPS is functioning
< The self-tests completed successfully
The batteries in the UPS must be periodically replaced. If the batteries are low, the
capacity test will indicate that the batteries do not have sufficient capacity to shutdown
the system before failing.
How
< Review the log for the UPS control program.
R/3 System Administration Made Easy
51
Chapter 5: 8cheduled Weekly Tasks
Contents
Checklists ................................................................................................................52
R/3 Tasks .................................................................................................................54
Monitoring and Plotting Database Growth (Transaction DB02)................................54
Checking for Tables Nearing their Maximum Extents...............................................57
Check Spool (Transaction SP01)..............................................................................59
Transports into the Production System...................................................................511
Database Tasks.....................................................................................................511
Checking the Database...........................................................................................511
Operating System Tasks......................................................................................512
Checking File System Space Usage.......................................................................512
Changing the Alert Threshold .................................................................................515
Other Tasks ...........................................................................................................516
Reviewing Hardware or a System Monitor Paging System....................................516
Cleaning the Tape Drive .........................................................................................518
Chapter 5: Scheduled Weekly Tasks
Checklists
Release 4.0B
52
Checklists
System: __________
Date: ____/ ____/ ____
Admin: _____________________
The R/3 8ystem
Task Transaction Procedure Check
off/initial
Check database for free space. DB02 DB
Performance:
Tables
Record free space.
Monitor database growth. DB02 DB
Performance:
Tables
Check spool for problems and
that spool is properly cleared.
SP01 - Spool
Transport into PRD STMS, or TP All properly approved transports
imported into PRD
Database
Task Where Procedure Check
off/initial
DBCC Check output from DBCC job for
errors (SQL Server).
Run MS-SQL server update
statistics.
Check for successful completion of
update stats job.
Operating 8ystem
Task Where Procedure Check
off/initial
Check file system for adequate
space.
RZ20 CCMS
Alert
Files system
Review space usage and that
sufficient free space exists in the file
systems.
Chapter 5: Scheduled Weekly Tasks
Checklists
R/3 System Administration Made Easy
53
Other
Task Where Procedure Check
off/initial
Check system monitoring
systems for update.
System monitor Review for any events that should
be added or deleted.
Check system monitor alert
mechanisms.
System monitor Test e-mail.
Test paging.
Clean tape drive. Tape drive Clean using cleaning cartridge.
Notes
Problem Action Resolution
Chapter 5: Scheduled Weekly Tasks
R/3 Tasks
Release 4.0B
54
R/3 Tasks
Monitoring and Plotting Database Growth {Transaction DB02}
What
This task involves monitoring the growth of the database and projecting future growth to
determine when to plan to expand the database.
Why
You need to plan when to expand database capacity with the least disruption to company
operations. If this expansion requires additional disk storage, you will need to purchase and
install the drives. This requires lead-time that should be incorporated into the planning
timeline. The drives should be installed during a noncritical period.
Running out of database capacity during a critical period can result in an emergency!
Murphy says:
The drives you need will not available from any of your suppliers when you critically
need them.
What
To effectively monitor database growth:
< Record and plot the database and freespace sizes
< Check for table and indices that are close to their maximum extents (maxextents)
< Check for fast growth tables (for example, VBFS)
Alter the percent-used factor for fast growers that have grown too large.
When
If your system experiences rapid changes, this task should be performed daily, rather than
weekly.
Chapter 5: Scheduled Weekly Tasks
R/3 Tasks
R/3 System Administration Made Easy
55
Guided Tour
1. In the Command field, enter transaction DB02 and choose Enter
(or choose Tools CCMS, then Control/Monitoring Performance Menu, and then Database
Table/Indexes).
2. Choose Space statistics.
3. Record and plot the free space
values.
4. Choose Graphics.
3
4
2
Chapter 5: Scheduled Weekly Tasks
R/3 Tasks
Release 4.0B
56
This screen shows a graph of free
space in the database, and a
projection into the future.
A. Now
B. Past history
C. Future forecast
Use care when you interpret the
graph. Forecasts are based on
historical usage that may or may not
be valid in the future.
5. Choose Back.
6. Choose Tablespaces.
This screen shows remaining free
space by individual tablespace.
7. To get the history of an individual
tablespace, double-click on it.
For Oracle, monitoring tablespace
usage is a critical task.
5
6
A B C
7
Chapter 5: Scheduled Weekly Tasks
R/3 Tasks
R/3 System Administration Made Easy
57
On the Tablespace history screen,
notice:
A. Free (Kbyte), the remaining free
space
B. Used (Kbyte), the amount of space
in use
8. Choose Months, Weeks, or Days for
an alternate view of this data.
9. Record and plot the tablespace
usage and freespace to estimate
when you will need to extend the
tablespaces, or get additional drive
space for the tablespaces.
Checking for Tables Nearing their Maximum Extents
What
Tables have a maximum number of times that they can grow, before a reorganization is
needed, this is the MaxExtents value.
Why
The MaxExtents value for Oracle 8.x is theoretically unlimited. But in practice, the number
of extents should not be allowed to get too large.
An excessive number of extents will create a performance issue, because a table would be
spread over many fragments. If the fragments are physically spread over the disk,
retreiving data would require more time than if the data was physically close together.
The table reorganization is essentially defragmenting the table.
8
B A
Chapter 5: Scheduled Weekly Tasks
R/3 Tasks
Release 4.0B
58
Guided Tour
1. In the Command field, enter transaction SE38 and choose Enter
(or choose Tools ABAP Workbench, then Development ABAP Editor)
(An alternate transaction is SA38, System Services Reporting).
2. Choose Enter.
3. Enter RSORATC5 in Program.
4. Choose Execute.
5. Enter 100 in More extents than.
This reduces the amount of table
to review.
6. Choose Execute.
7. Read the value in the Extents
column.
8. If it is within 100 extents of the
MaxExtents column, a
reorganization of the object/
tablespace is needed.
3
4
5
2
7 8
6
Chapter 5: Scheduled Weekly Tasks
R/3 Tasks
R/3 System Administration Made Easy
59
Check 8pool {Transaction 8P01}
What
The SAP Spool is the output manager for R/ 3. From the SAP spool, the print job goes to the
operating systems print spooler or manager.
You need to check that old spool jobs are being properly cleared by the daily batch job.
Why
Old spools will take up database space or file system space, depending on how the spool
system has been configured. Whether it is database or file system space, potentially
available space is being used by these spools.
Look for any errors that may indicate problems in the printing process.
Guided Tour
1. In the Command field, enter transaction SP01 and choose Enter
(or choose System Services Output controller).
2. Clear the following fields:
< User name
< From (date)
< to (date)
< Client
2
Chapter 5: Scheduled Weekly Tasks
R/3 Tasks
Release 4.0B
510
3. Scroll down the screen to find the
oldest date. This date should be in
the time frame defined for the
RSPO0041 job that deletes old
spools (see Online Service System
note 16083).
If it is not, the job may not be
properly deleting the old jobs and
needs to be analyzed.
4. To add the user name on the
screen, choose User name.
Two reasons for failure of the RSPO0041 job are:
< The user ID under which the job is run does not have the proper security authorization
to execute the program.
< The job is routed to an invalid printer.
5. The Client User option helps you
see which user from which client
is related to the spool jobs. This
information is helpful if there are
spool errors.
4
5
Chapter 5: Scheduled Weekly Tasks
Database Tasks
R/3 System Administration Made Easy
511
Transports into the Production 8ystem
What
A transport is the mechanism that R/ 3 uses to move changes from system to system or
client to client.
When
Complete the transport in the production system during a quiet period (for example,
Sunday afternoon or evening) when users are not logged on the system.
Ideally, a full system backup should have been completed before transports are imported.
Why
During a transport, objects may be overwritten. If an object is being used in the target
system when a transport is performed, the transport may cause inconsistent results or
terminate the transaction.
In the worst case scenario, a transport may break the production system and you will
need to restore the system.
How
To learn how to do transports, see the section, Transporting Objects, in chapter 10,
Nonscheduled System Administration Tasks. Transports are a nonscheduled task because
they are only done when necessary (that is, when you have a transport that needs to be
moved). You may also have the occasional emergency transport that must be moved at a
time other than at your normal weekly transport time.
Database Tasks
Checking the Database
What
There are two database checks; DB system check and DB verfication.
< DB system check is for a health check of the database.
< DB verification checks the internal Oracle block structure for block corruptions.
Why
If there is a problem with the database, a restore of the database will have the same
problem. The DB verification give assurance that the backup is of a good database.
How
See chapter 14, Checking the Database.
Chapter 5: Scheduled Weekly Tasks
Release 4.0B
512
Operating 8ystem Tasks
Checking File 8ystem 8pace Usage
What
The file system should have sufficient free space to permit normal operations to run. Over
time, various operations will write files that will use up file space. These files need to be
periodically reviewed and moved, or backed up and deleted.
A few of the items that consume file space and must be considered when monitoring file
space usage include:
< Transports
< Hot Packages
< Extract files from the R/ 3 System
< Program logs
< Backup logs
< Error logs
< Inbound interface files
< Third-party programs that store their data outside the R/ 3 database
In addition to these items, check to see that house cleaning programs are running
properly (See Online Service System note 16083).
Why
If your file system fills up, the R/ 3 System may stop because it cannot write a file. This
stoppage will, in turn, stop any business operations that use the system.
In the Oracle database, this is a critical situation for the Oracle redo archive logs. If the file
system fills and Oracle cannot write anymore redo archive logs, Oracle will stop, causing
R/ 3 to stop.
To plan for such a situation:
< Predict and plan for disk space needs.
< Determine if storage space expansion is needed.
If storage space expansion is needed, purchase and installation plans need to be made.
The expansion should be planned to minimize operational disruption.
< Determine if house cleaning is needed.
If archiving is required for data files, archive to quality storage media such as optical
disk, CD, or similar long-term media.
Chapter 5: Scheduled Weekly Tasks
Operating System Tasks
R/3 System Administration Made Easy
513
Guided Tour
You can use the R/ 3 Alert Monitor, or you can go to the operating system to check file system space usage.
In this step-by-step procedure, we use the R/ 3 Alert Monitor, because we can set alert points.
1. In the Command field, enter transaction RZ20 and choose Enter
(or choose Tools CCMS, then Control/Monitoring Alert Monitor 4.0).
2. To expand the system to be
checked, click the node (for
example, SAO).
3. Double-click on the monitor, for
example Basic monitor.
3
2
Chapter 5: Scheduled Weekly Tasks
Operating System Tasks
Release 4.0B
514
4. Drill down as follows:
SAP domain <Instance> (SAO)
<server_instance_system number>
(pa100767_SAO_01)
OperatingSystem Filesystems.
The drives are color coded to
indicate alert status:
< Green (OK)
< Yellow (Warning)
< Red (Critical)
7. Expand the drive (for example, E:)
to its statistics (Freespace and
Percentage_Used):
These are statistics at the drive
(not directory) level.
View these statistics while keeping
your particular system in mind.
For example, on your system,
drive E may contain the database
which takes up all the space on
that drive. Keeping this in mind,
you can expect and ignore the
warning message. Or change the
alert threshold for that specific
drive. See Changing the Alert
Threshold on page 515.
5
Chapter 5: Scheduled Weekly Tasks
Operating System Tasks
R/3 System Administration Made Easy
515
Changing the Alert Threshold
To customize the points when the
alert indicator changes from green to
yellow, yellow to red, and back from
red to yellow, and yellow to green:
1. Click the node of the specific drive
for which you want to change the
threshold.
2. Select an alert.
3. Choose Customizing.
4. Choose Change.
5. Choose Thrshld values.
6. Enter new values for when the
alerts will change (for example,
1000).
These threshold values are specific
to your system, and even to
specific drives in your system.
7. Choose Save.
1
3
6
7
4
5
2
Chapter 5: Scheduled Weekly Tasks
Other Tasks
Release 4.0B
516
Other Tasks
Reviewing Hardware or a 8ystem Monitor Paging 8ystem
What
A hardware or system monitor paging system generates alert messages (including e-mail)
and pages based on your predefined parameters. Depending on the software, the following
can be monitored:
< Hardware items, such as servers, routers, and printers
< Logs, such as operating system, applications, and database
By monitoring the NT event logs, you can monitor events from the SAP system log. This
way, critical events such as an Update Terminate can be detected and acted on as soon as
they happen.
The following screen is courtesy of TNT Software.
Chapter 5: Scheduled Weekly Tasks
Other Tasks
R/3 System Administration Made Easy
517
The previous screenshot shows what one of these monitors looks like. It has three functional
windows:
< Notification Rules
This is the mechanism to pass or filter events, and what action will be taken on the
events that are passed.
< Events
These are the events that have been passed to the monitor program. (They got through
the filters in the notification rules.)
< Monitored device
These are the monitored servers and IP devices.
This example, however, has not been configured to pick up and report on SAP events.
Initially, there will be a lot of tuning as you adjust the parameters of the system. Over time,
parameter adjustments will become less and less.
Why
You may need to change alert parameters to filter noncritical events and to generate alerts
for critical events. Some of these tasks are as follows:
< Account for new events
Critical, you need to generate a page
Important, you need to generate a message (for example, e-mail)
< Determine if an event that used to be filtered now needs to generate an alert
< Filter out events (both old and new) that should not generate alert messages
Filtering is necessary to manage the messages that are reviewed. If too many irrelevant
messages get through the filter, it becomes difficult to review the alert message log.
< Adjust for personnel changes
Occasionally, there may be other events that require action (for example, shift or duty
changes for organizations with several people on call).
You need to test that all alert mechanisms are functional
The paging/ messaging function needs to be tested regularly. If it is unable to send a page,
you will not receive the page when a critical alert occurs.
Not sending a page can be caused by:
< Someone changing something in the e-mail or phone system that prevents alert
messages from being sent
< A phone patch cable that has become disconnected from the modem
Chapter 5: Scheduled Weekly Tasks
Other Tasks
Release 4.0B
518
How
To review the paging system:
< Review the various monitored logs (such as the NT event logs) to look for events that
should generate an alert message (e-mail or page).
The monitor program needs to be configured to pick these up and properly process
them.
< Review the log of the alert monitor for alert events that should be filtered out.
The monitor program needs to be configured to filter or ignore such events.
< Test all alert mechanisms, such as pager, e-mail, and so on to make sure that they are
functional.
If you receive regular daily e-mail messages, then the e-mail testing is being done for
you.
Cleaning the Tape Drive
Clean the tape drive as part of a preventive maintenance program to minimize a backup
failure due to a dirty head.
Murphy says: The backup that failed is the backup you will need.
To keep your tape drive clean:
< Follow the tape drive manufacturers instructions for your tape drive.
Some drives specify a specific interval of use for cleaning, typically based on hours of
use. Adjust your cleaning frequency to account for your usage. Remember, that these are
recommendationsnot rules. If you consistently have recording errors or head dirty
messages, then decrease the time between cleanings. If you have to clean your tape
drives more or less frequently, this task should be moved to the appropriate interval.
Some drives (for example, DLT) do not require regular cleaning. They only need
cleaning when the clean head indicator light is activated.
< Use the manufacturers approved cleaning cartridge for the tape drive.
< Use the cleaning cartridge according to the manufacturers instructions.
< Between uses, store the cleaning cartridge according to the manufacturers instructions.
Keep your server room clean.
A dusty or dirty environment will not only make you clean your tape drive more often, but
will also coat the inside of the server with dust and cause a cooling problem.
R/3 System Administration Made Easy
61
Chapter 6: 8cheduled Monthly Tasks
Contents
Checklists ................................................................................................................62
R/3 Tasks .................................................................................................................65
Memory Defragmentation .........................................................................................65
Database Tasks.......................................................................................................66
Plotting Database Growth.........................................................................................66
Operating System Tasks........................................................................................67
Performing a Full Server Backup..............................................................................67
Reviewing File System Usage ..................................................................................67
Other Tasks .............................................................................................................68
Checking Consumable Supplies...............................................................................68
Chapter 6: Scheduled Monthly Tasks
Checklists
Release 4.0B
62
Checklists
System: __________
Date: ____/ ____/ ____
Admin: _____________________
The R/3 8ystem
Task Transaction Procedure Check off/initial
Defragment the memory Cycle the R/ 3 System
Database
Task Where Procedure Check off/initial
Plot database growth DB02Database
Performance:
Tables
Record usage and plot
Operating 8ystem
Task Where Procedure Check off/initial
Backup file server Perform a full server backup
Record file system usage. Plot
usage.
Is additional storage space
needed?
Is house cleaning needed?
Review file system usage
Chapter 6: Scheduled Monthly Tasks
Checklists
R/3 System Administration Made Easy
63
Other
Task Where Procedure Check off/initial
Spare tape cleaning cartridge
available for all tape drives.
< DAT
< DLT
Spare tape cartridges available
for all drive types.
< DAT
< DLT
Spare data cartridges available
for removable media devices:
< Zip
< MO (Magneto-Optical)
< CD (Recordable)
Preprinted forms:
< Shipping documents
< Invoices
< Checks
Special supplies, such as
magnetic toner cartridge.
Normal supplies:
< Laser printer toner
< Paper (for printers)
< Batteries
< Diskette
< Pens, and so on
Check consumable supplies
Chapter 6: Scheduled Monthly Tasks
Checklists
Release 4.0B
64
Notes
Problem Action Resolution
Chapter 6: Scheduled Monthly Tasks
R/3 Tasks
R/3 System Administration Made Easy
65
R/3 Tasks
Memory Defragmentation
What
A computers memory behaves similar to that of a hard disk. As different programs execute,
they are loaded into and later deleted out of memory. Over time, like a hard disk, the usage
of the computers memory becomes fragmented with unused spaces scattered throughout.
Why
At a certain point you may have sufficient free memory (that is, the total of all the unused
spaces), but not a contiguous (single) piece of memory large enough to allow certain
programs to execute. At that point, those types of programs attempting to run that need
contiguous memory will fail because they cannot be loaded into memory.
How
To defragment the systems memory:
1. Stop R/ 3.
This step includes stopping R/ 3 on all application and database servers.
See chapter 10, the section Start/Stop R/3.
2. Restart R/ 3.
You only need to restart R/ 3, you do not need to cycle the server.
Whenever R/ 3 is restarted, the buffers are refreshed. This process means that the first
person who accesses the buffered object will have a long response because the system must
get the data from disk and load it into the buffer. The second person will have a normal
(quick) response time. This process repeats until all normally used objects are loaded into
the buffer. This usually takes up to a day to accomplish.
Chapter 6: Scheduled Monthly Tasks
Database Tasks
Release 4.0B
66
Database Tasks
Plotting Database Growth
What
Plotting database growth is a basic requirement to planning for database and hardware
expansion.
Why
Hardware expansion typically requires that the server be brought down before installation
of additional hardware. The time required to complete this shutdown, and possible
problems that may occur, need to be considered when planning the expansion. Because of
the system shutdown, possible problems, and significant lead times, the expansion needs to
be coordinated with the users.
Plan ahead for critical periods such as year-end, when you do not want the system to be
changed. You need to do your change before or after the critical period. If the decision is to
make the change after this time, consider whether you have sufficient capacity to get
through the critical period.
How
To effectively plan for this expansion, record the database and tablespace sizes and plot
their growth curve over time. This information should give you a rough estimate as to when
you will need to expand the storage space. Remember, if new SAP functionality is
implemented, the slope of the growth curve will change. For additional information, see
chapter 5, the section Monitor and Plot Database Growth.
Chapter 6: Scheduled Monthly Tasks
Operating System Tasks
R/3 System Administration Made Easy
67
Operating 8ystem Tasks
Performing a Full 8erver Backup
What
An offline backup of the entire server is done at the operating system level. This process
requires that the R/ 3 System and the database be down so that no files are open.
Why
Performing an offline backup is necessary for files that cannot be backed up if the R/ 3
System or the database is active. With this full-server backup, you know you have
everything on the server. If you experience major system problems, you will have a
defined point from where everything is backed up and from where you can begin a restore.
When
A full-server backup should be performed before and after major changes on the server,
such as:
< Installing new software
< Upgrading installed software
< Changing hardware
If a change has a catastrophic effect (a disaster), you will need to recover the server to its
before-the-change state.
How
To perform a full server backup:
1. Stop the R/ 3 System.
2. Stop the database.
3. Stop all services (NT).
4. Execute the backup using your backup program (database and file system).
5. Check backup times and logs.
6. Cycle the server.
Reviewing File 8ystem Usage
The monthly tasks for reviewing file system usage are the same as the weekly tasks, but are
completed monthly. For additional information, see chapter 5, the section Review File System
Usage.
Chapter 6: Scheduled Monthly Tasks
Other Tasks
Release 4.0B
68
Other Tasks
Checking Consumable 8upplies
What
Consumable supplies are those that you use regularly. Examples are: cleaning cartridges,
data cartridges (tape and disk), laser printer toner, ink cartridges, batteries, forms,
envelopes, etc.
Within the group of consumable supplies are critical supplies. These are supplies which if
they run out, could affect or stop the business operations. Examples are preprinted forms
with your companys name or other special printing, and magnetic toner cartridges.
The amount of spare supplies purchased and on-hand should be enough to handle normal
and slightly abnormal usage and to allow for time to purchase replacements.
Why
Running out of supplies will create an inconvenience, or even an operational problem.
Critical 8upplies
If an item is critical, and you run out of it, business operation may stop.
Example, if you run out of the magnetic toner cartridge for the check printer, you will not be
able to generate checks out of the system. At this point, either you cannot print checks to
pay your vendors, or you have to manually type the checks (if you have blank manual check
stock on hand).
Special or custom supplies such as the following require special consideration:
< Special magnetic ink toner cartridges to print the MICR characters on checks.
Not every computer supplier will stock these special cartridges.
< Preprinted forms (with company header, instructions, or other custom printing).
Because of the custom nature of these items, there is usually a significant lead time to
restock these items.
If it is a critical item, stock extras, the first spare may be bad or defective.
Murphy says: When you need something immediately, it will be Friday evening and
vendors and stores will be closed.
Chapter 6: Scheduled Monthly Tasks
Other Tasks
R/3 System Administration Made Easy
69
How
To check consumable supplies:
< Check the expiration date on supplies that are subject to aging.
This applies to supplies in use and those in inventory (not yet in use).
< Check supplies that have a time in service expiration, such as hours, cycles, etc.
Example, certain DAT tapes are rated for 100 full backups. After that they should be
discarded and replaced with new tapes. (This usage limit can be entered into the
SAPDBA control file.)
< Keep in touch with your purchasing agent and the market place.
Market conditions may make certain supplies difficult to purchase. In such conditions,
the lead time and quantities to be purchased need to be increased.
For example, at one time, 120 meter DAT tapes cartridges were difficult to buy. . . at any
price.
< Track usage rates and adjust stocking levels and purchasing plans as needed.
Other Considerations
Certain supplies may have long lead times for purchase, manufacture, or shipping.
Do not make your lack of planning the purchasing agents emergency. If you do this too
often, you will soon use up your favors. Then when you really need help, the
purchasing agent may not be as willing to help you.
Chapter 6: Scheduled Monthly Tasks
Other Tasks
Release 4.0B
610
R/3 System Administration Made Easy
71
Chapter 7: 8cheduled Ouarterly Tasks
Contents
Checklists ................................................................................................................72
R/3 Tasks .................................................................................................................74
Backups ....................................................................................................................74
Security .....................................................................................................................74
Database Tasks.......................................................................................................78
Performing a Database Test Restore .......................................................................78
Operating System Tasks........................................................................................79
Cleaning Out Old Transport Files .............................................................................79
Other Tasks ...........................................................................................................710
Checking Maintenance Contracts...........................................................................710
Check your UPS Shutdown Process ......................................................................711
Chapter 7: Scheduled Quarterly Tasks
Checklists
Release4.0B
72
Checklists
System: __________
Date: ____/ ____/ ____
Admin: _____________________
The R/3 8ystem
Task Transaction Procedure Check off/
initial
Archive quarterly backup Send quarter-end backup tapes to long-term
offsite storage.
SU01User
Maintenance
Review user ID for terminated users that
should be locked or deleted.
SM31Table
Maintenance
Review list of prohibited passwords (Table
USR40).
Security review
RZ10Edit
System
Profile
Review system profile parameters for
password standards.
Review scheduled jobs SM37
Background
Jobs
Review all scheduled jobs to determine if they
are still appropriate.
Database
Task Where Procedure Check off/
initial
Archive quarterly backup Send quarter-end backup tape to long-term
offsite storage.
Review all scheduled jobs Review all scheduled jobs to determine if they
are still appropriate.
Restore database to a test server. Test database recovery
process
Test the restored database.
Chapter 7: Scheduled Quarterly Tasks
Checklists
R/3 System Administration Made Easy
73
Operating 8ystem
Task Where Procedure Check off/
initial
Archive quarterly backup Send quarter-end backup tape to
long-term offsite storage.
Archive old transport files Transport directories;
log, data, cofiles
Archive the old transport files.
Cleanup SAPDBA logs SAPDBA cleanup Maintain init<SID>.dba
Other
Task Where Procedure Check-
off/initial
Check for expiration date. Check maintenance
contacts
Check for usage changes.
Notes
Problem Action Resolution
Chapter 7: Scheduled Quarterly Tasks
R/3 Tasks
Release4.0B
74
R/3 Tasks
Backups
< Make certain you get a usable backup at the quarters end.
< Send quarter-end backup tapes offsite for an extended period.
8ecurity
Review that All Named Users Are Valid
All users who have left the company should have their R/ 3 access terminated immediately.
By locking or deleting these user IDs, you limit access to only those users who should have
access to R/ 3. Periodic review assures the task of locking or deleting has been completed.
Proper audit control requires that a user who no longer has a valid business need to access
R/ 3 should not be allowed to keep that access.
Deleting or locking these user IDs also prevents anyone who had been using the terminated
user ID from accessing the system under that ID.
One of the audit procedures that your external auditors will use is to test whether a person
who does not need to access R/ 3 has a live user ID.
Reviewing Whether All Named Users Are Valid
Guided Tour
1. In the Command field, enter transaction SU01 and choose Enter
(or choose Tools Administration, then User maintenance Users).
2. Clear the User field.
3. Choose possible entries.
3
Chapter 7: Scheduled Quarterly Tasks
R/3 Tasks
R/3 System Administration Made Easy
75
4. Clear all fields.
5. Choose List Enter.
6. Review the active users.
Verify that the users are indeed
valid users.
7. This screen allows you to view the
Group that the user is in. If
maintained properly, groups are
an aid in determining active users.
In a large company, you should do a
random audit on at least 20 users, to
have a valid sample. The minimum
number should be determined by
your auditors.
For additional information on how to lock a user, see chapter 9, Nonscheduled Tasks User Administration
Tasks.
5
7
4
6
Chapter 7: Scheduled Quarterly Tasks
R/3 Tasks
Release4.0B
76
Eliminating 8ome Easy Passwords
What
There are certain passwords (for example, 123, QWERTY, abc, sex, sap, <your company name>)
that are well known or easy to guess by someone trying to break into the R/ 3 System. You
can prevent these passwords from being used by loading them into a table (USR40) that the
system checks when the user attempts to save a new password.
Why
A password is the key to enter the system, similar to the key to enter your home. If users
choose easy-to-guess or well-known passwords, security becomes an issue and your system
is potentially at risk.
Your external auditors may check to see if you have a mechanism to secure against users
using easy-to-guess passwords.
How
See chapter 9, the section Maintaining a Table of Prohibited Passwords; then in chapter 10, the
section Table Maintenance Using Transaction SM31.
Chapter 7: Scheduled Quarterly Tasks
R/3 Tasks
R/3 System Administration Made Easy
77
Reviewing Password 8tandards Using Transaction RZ10
What
There are security parameters for the users password (for example, the minimum password
length, the time interval that the user must change their password, and so on).
The following is a list of the most important password parameters:
< Minimum password length: login/min_password_lng
A longer password is more difficult to break or guess.
The standard for many companies is five (5) characters.
< Password expiration time: login/password_expiration_time
This is the length of time before the user must change their password.
The length of time most auditors recommend is thirty (30) days.
The maximum that should be used is ninety (90) days.
< Password lockout: login/fails_to_user_lock
This parameter locks out users after attempting to log in with an invalid password for a
defined number of times.
The standard is to lock a user after three (3) failed attempts.
Why
Properly assigned parameters make it more difficult to break into the system.
Your external auditors may check to see if you have set the security parameters.
How
To set up password parameters, maintain system profiles with transaction RZ10. See
chapter 11, the section Changing System Profile Parameters.
Chapter 7: Scheduled Quarterly Tasks
Database Tasks
Release4.0B
78
Database Tasks
Performing a Database Test Restore
What
A database test restore is a test in which the production database is restored onto another
server to test that the recovery process functions as intended.
Why
Periodically it is prudent to test the restore process to:
< Verify that backup tapes are being created properly.
If you cannot recover the full database using your regular backup tapes, you want to
know about it before you really need to restore the database.
< Find out if changes have been made which need to be accounted for in the disaster
recovery process.
Murphy says: When you need to restore, you will find that a backup tape is not usable.
How
See comments in chapter 3, Backup and Recovery. Because the restore process is a critical task,
you need to work with your consultants on this process.
Chapter 7: Scheduled Quarterly Tasks
Operating System Tasks
R/3 System Administration Made Easy
79
Operating 8ystem Tasks
Cleaning Out Old Transport Files
What
Transport files are used to transport or move SAP objects and customizing changes between
clients and systems.
Why
If left unchecked, transport files could gradually fill up the file system.
Operations may be affected because:
< Outbound R/ 3 System files may not be able to be created.
< Transport export may fail.
< Inbound files may not be createable.
In an extreme situation, if you run out of tablespace R/ 3 may stop, or you may have other
failures because R/ 3 or another application cannot write to the necessary files.
When
The transport directory check is important after a major implementation in which many
transports have been created and take up large amounts of space. Immediately before or
after performing a database copy, most (if not all) files dated prior to the copy will become
irrelevant to the system.
How
To complete a transport directory check:
1. Check the following directories under /usr/sap/trans:
Data
Cofiles
Log
2. Sort the directory by date to determine the age of files.
3. Archive obsolete files.
These are files created before a database refresh or those that have been applied
successfully to all target systems.
4. As an option, archive old transports to a backup media such as tape, optical, or CD.
Chapter 7: Scheduled Quarterly Tasks
Other Tasks
Release4.0B
710
Check both of the following:
< Hot package directory /usr/sap/trans/EPS/in
< Transport data directory /usr/sap/trans/data
Hot package files can be reloaded if needed and can be very large. For example, hot
package 10 for Release 4.0B is over 200MB.
Other Tasks
Checking Maintenance Contracts
What
Many of the servers and related equipment are under maintenance or service contracts with
the manufacturer or distributor.
< The production system and critical equipment should be under a premium
24 hour x 7 day (x 2 hour response) support agreement.
< Less critical equipment can be under a next business day support agreement.
Why
If you need support or service on a piece of equipment and the service contract has expired,
the confusion and time to reestablish the service contract could be critical.
What
Depending on the use of the equipment, the support level should be selected accordingly. If
a piece of equipment becomes critical to the companys operation, its support level should
be upgraded to reflect the critical nature of that equipment.
Conversely, equipment could become noncritical or be replaced. In this situation, the
service contracts should be downgraded or dropped as appropriate.
How
< Keep a list of service contracts.
Include what they are for and the expiration date in the list.
< Review equipment usage to determine if the support level for equipment should be
upgraded, downgraded, or dropped.
< Review the list for expiration dates within a quarter.
This time period depends on the time it takes to go through the purchase requisition and
approval process in your company.
< Renew service contracts.
Chapter 7: Scheduled Quarterly Tasks
Other Tasks
R/3 System Administration Made Easy
711
Check your UP8 8hutdown Process
What
Verify that your uninterruptible power supply (UPS) shutdown process works. A shutdown
process is an automated script for the UPS to shut down R/ 3, the database, other
applications, the operating system, and then the UPS itself.
Why
The purpose is to verify that the entire shutdown process works as planned and
documented.
When there is a power failure, the R/ 3 environment should be shut down in an orderly
manner. There should be sufficient reserve in the UPS to reach the end of the shutdown
process.
Something might have changed since your last test to cause the shutdown process to fail.
If it fails, you need to find out why and fix the problem.
The stopsap command does not work within all UPS control programs.
You need to verify that your UPS control program will properly stop R/ 3 and the database
before shutting down the server.
Like a car battery, UPS batteries wear out over time and must be replaced. If the battery
is worn out, the UPS will not have sufficient power to complete the shutdown process.
Chapter 7: Scheduled Quarterly Tasks
Other Tasks
Release4.0B
712
R/3 System Administration Made Easy
81
Chapter 8: 8cheduled Annual Tasks
Contents
Checklists ................................................................................................................82
R/3 Tasks .................................................................................................................84
Backups ....................................................................................................................84
Security & Profile Audit .............................................................................................84
Checking that the Production System Is Not Modifiable...........................................88
Verifying that Dangerous Transactions Are Locked .................................................89
Database Tasks.....................................................................................................815
Backups ..................................................................................................................815
Operating System Tasks......................................................................................815
Backups ..................................................................................................................815
Other Tasks ...........................................................................................................815
Disaster Recovery Test...........................................................................................815
Chapter 8: Scheduled Annual Tasks
Checklists
Release 4.0B
82
Checklists
System: __________
Date: ____/ ____/ ____
Admin: _____________________
The R/3 8ystem
Task Transaction Procedure Check
off/initial
Archive year-end backup Send year-end backup tapes to long-
term offsite storage.
Audit user security Review users security authorization
forms against assigned profiles.
Can also be done with report
RSUSR100
SU02 Security
Profile Maintenance
Spot check profiles for recent changes.
Can also be done with report
RSUSR101
Audit profiles and
authorizations
SU03 Security
Authorization
Maintenance
Spot check authorizations for recent
changes.
Can also be done with report
RSUSR102
Review segregation of
duties
Audit user IDs SAP* and
DDIC
Run SAP user audit
reports
SA38 (or SE38)
Execute ABAP
Program
Run user audit reports:
< RSUSR003
< RSUSR005
< RSUSR006
< RSUSR007
< RSUSR008
< RSUSR009
< RSUSR100
< RSUSR101
< RSUSR102
Chapter 8: Scheduled Annual Tasks
Checklists
R/3 System Administration Made Easy
83
Task Transaction Procedure Check
off/initial
Check that the system is
set to Not modifiable.
SE03 Workbench
Organizer Tools
Verify that system is set to Not
modifiable.
SCC4 Clients:
Overview
Check changeable status for applicable
client
Check locked transactions SM01 Transaction
codes: Lock/ Unlock
Check against your list of locked
transactions.
Database
Task Where Procedure Check
off/initial
Archive year-end backup Send year-end backup tapes to long-
term offsite storage
Operating 8ystem
Task Where Procedure Check
off/initial
Archive year-end backup Send year-end backup tapes to long-
term offsite storage
Other
Task Where Procedure Check
off/initial
Restore entire system to disaster
recovery test system
Perform disaster recovery
test
Test business resumption
Notes
Problem Action Resolution
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
Release 4.0B
84
R/3 Tasks
Backups
For a year-end backup:
< Make certain to get a usable backup at year-end.
< Send the backup tapes offsite for an extended period.
The length of the extended period should be determined by your legal and finance
departments, external auditors, and others as appropriate in the company.
Be aware that you may have two different year-end backup dates:
< End of the calendar or fiscal year
< After the financial books are closed for the year
8ecurity & Profile Audit
Reviewing Profiles for Accuracy and Permission Creep
What
A permission creep is an incremental increase in permission given to a user over time. If
left unchecked, increased permissions may grant a user more authority in the system than
required or intended.
Why
Users may have undesirable authorization(s) or combinations.
Your external auditors may have an audit step to check for permission creepage.
How
You can conduct a spot audit of:
< Individuals
Review the security forms for a user, and compare these forms to the profiles
assigned to that user, and investigate inconsistencies.
Review the profiles assigned to the individual for reasonableness.
Reasonableness is: Does it make sense?
Review the individual profiles assigned for content and check to see if the profile has
been recently changed.
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
R/3 System Administration Made Easy
85
< Profiles (transaction SU02) and authorizations (transaction SU03)
Check to see if the change date is recent.
You can also execute the following audit reports:
< RSUSR100 (user changes)
< RSUSR101 (profile changes)
< RSUSR102 (authorization changes)
For additional information on these reports, see the User Security Audit section on page 87.
Accurate 8egregation of Duties
What
There are standard audit guidelines which cover job/ task combinations that are considered
risky or reduce internal controls. Some of these are:
< Accounts Payable and Check Generation
< Accounts Receivable and Cash Receipts
< ABAP development and transport control
Your external auditors should be able to help you define these risky combinations.
For your external auditors, testing for segregation of duties is a standard audit procedure.
How
The review of segregation of duties should be completed with the various user owners (key
users of each functional area).
Out of necessity, smaller companies must assign multiple functions to a single person. Be
aware of the potential security risks in this situation. If you must combine functions,
combine them in a way that you minimize risks.
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
Release 4.0B
86
Restricting Access to 8AP* or DDC
What
These are system user IDs that have restricted uses for specific purposes.
Why
There are certain functions that can only be performed by SAP* or DDIC.
If an R/ 3 user requires similar functionality, they should have a copy of the SAP* profile.
These users should be grouped as super users, with the appropriate security approvals.
The security profile for SAP* is SAP_ALL. This profile is extremely because it grants the user
complete access to the system. See further explanation in chapter 9, the section Recommended
Polices and Procedures: System Administration.
A user with user administration rights cannot change the password to gain access to a user
ID and then change the password back to the original password. Passwords are not visible
to the administrators, thus they cannot restore the original password if they do not know it.
At a subsequent logon, the owner of the user ID will know that the password has been
altered because they cannot log in with their old password.
How
1. Log on using SAP* and DDIC to determine if someone has changed the password.
2. Periodically change the password for these users:
In all systems
In all clients in those systems.
This step prevents a person who knew the password from gaining access.
3. Update the secured password list.
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
R/3 System Administration Made Easy
87
User 8ecurity Audit
There are several predefined SAP security reports, including:
< RSUSR003 Check for default password on user IDs SAP* and DDIC
< RSUSR005 Lists users with critical authorizations
< RSUSR006 Lists users who are locked due to incorrect logon
This report should be scheduled to run daily, just before midnight.
< RSUSR007 Lists users with incomplete address data
< RSUSR008 Lists users with critical combinations of authorizations or transactions
< RSUSR009 Lists users with critical authorizations
< RSUSR100 Lists change documents for users and shows changes made to a users
security
< RSUSR101 Lists change documents for profiles and shows changes made to security
profiles
< RSUSR102 Lists change documents for authorizations and shows changes made to
security authorizations
Some of these reports have parameter tables that need to be properly maintained to make
best use of them. Review and analyze these reports based on your knowledge of the
company. However, be aware that security issues may exist. If you have a small company,
these issues cannot be avoided because one person often must wear many different hats.
Your external auditors may require some of these reports to be executed as part of the
annual financial audit.
How
1. Enter transaction SA38 or SE38.
2. Enter the report name in Program.
3. Choose Execute.
4. Choose OK.
Notes for 8pecific Reports
< RSUSR008 (lists critical combinations of authorizations or transactions)
These combinations are maintained on table SUKRI.
Dangerous combinations include the following transactions:
- RZ02 (with anything)
- RZ03 (with anything)
- SE14 (with anything)
- SU01 (with security, users, and profiles)
- SU02 (with security, users, and profiles)
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
Release 4.0B
88
Checking that the Production 8ystem s Not Modifiable
What
Check that the production system is set to Not modifiable. The locks on the system should
be set so that configuration changes (client-independent and client-dependent) cannot be
made directly into the production system.
Why
Configuration changes should not be made directly into the production system.
The goal is to protect the production system from changes, without the changes being
properly tested and to preserve the integrity of the pipeline. A pipeline is defined as the
environment where development is moved from the development system to the quality
assurance system, and finally to the production system.
If changes are made into the production system, the development and testing pipeline
could become out of sync with the production system. When this happens, it becomes
difficult to develop and test with any certainty that things will not be different in the
production system.
All changes should be made in the development system then transported through the
pipeline into production. In this way, all systems get the same changes.
A common excuse to make changes directly into the production system is, it takes too
long to transport the fix.
1. The risk is creating an out of sync landscape, where the change made to the
production system, is not the same as made to the development and/ or test systems.
2. Emergency transports can occur at any time, with coordination.
How
See procedure in chapter 11, the section Setting the Production System to Not Modifiable
Exceptions
There are infrequent exceptions to the rule. These occur when:
< There is no mechanism to transport the changes.
< An Online Service System note requires the direct change.
Only in these (and similar) cases, the changes must be made directly into the target systems.
Manual entry always increases the chance that an error will be made.
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
R/3 System Administration Made Easy
89
Verifying that Dangerous Transactions Are Locked
What
Dangerous transactions are transactions that could do the following:
< Damage or corrupt the system
< Present a security risk
< Adversely impact performance
Why
If a user accesses these transactions by accident, they could corrupt or destroy the R/ 3
System.
Access to dangerous transactions is more critical in the production system than the
development or test systems. This is because of live data and the fact that the companys
operations are dependent on the R/ 3 System.
Certain transactions should be locked in the production system, but not in the development,
test, or training systems.
Standard security normally prevents access to these transactions, but some administrators,
programmers, consultants, and functional key users could have access to them depending
on which system they are on. In these cases, the transaction lock provides a second line of
defense.
There are over 16,000 English transaction codes in the R/ 3 System. Thus, to make it
manageable, it is only the critical ones that you need to lock. Your functional consultants
should supply you with any additional critical transactions in their modules.
The following table, contributed to by various Basis consultants and users, lists transactions
that we recommend you lock. The transactions are categorized by the risk categories:
dangerous, security-related, and performance impact.
Transaction Description Dangerous Security Performance
FO40 Document Archiving X
FO41 Bank Master Data Archiving X
FO42 G/ L Accounts Archiving X
FO43 Customer Archiving X
FO44 Vendor Archiving X
FO45 Document Archiving X
FO46 Transaction Figures Archiving X
GCE2 Profiles: Initial screen X
GCE3 Maintain Authorizations: Object Classes X
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
Release 4.0B
810
Transaction Description Dangerous Security Performance
KA10 Archive Cost Centers (all) X
KA11 Archive admin: cost centers (all) X
KA12 Archive cost centers (plan) X
KA13 Archive admin: cost centers (plan) X
KA14 Archive cost centers (actual) X
KA15 Archive admin: cost centers (actual) X
KA16 Archive cost centers (line items) X
KA17 Archive admin: cost centers (line items) X
O001 Maintain Users: Initial Screen X
O002 Profiles: Initial Screen X
O016 Maintain Authorizations: Object Classes X
OBR1 Reset Transaction Data
(delete transaction data)
X
OBZ7 Maintain Users: Initial Screen X
OBZ8 Profiles: Initial screen X
OBZ9 Maintain Authorizations: Object Classes X
OD02 Maintain Authorizations: Object Classes X
OD03 Profiles: Initial screen X
OD04 Maintain Users: Initial Screen X
OIBA Maintain Authorizations: Object Classes X
OIBB Maintain Users: Initial Screen X
OIBP Profiles: Initial Screen X
OMDL Maintain Users: Initial Screen X
OMDM Profiles: Initial Screen X
OMEH Maintain Users: Initial Screen X
OMEI Profiles: Initial Screen X
OMG7 Maintain Authorizations: Object Classes X
OMI6 Maintain Authorizations: Object Classes X
OML0 Maintain Users: Initial Screen X
OMM0 Profiles: Initial Screen X
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
R/3 System Administration Made Easy
811
Transaction Description Dangerous Security Performance
OMNP Maintain Authorizations: Object Classes X
OMSN Maintain Users: Initial Screen X
OMSO Profiles: Initial Screen X
OMSZ Maintain Authorizations: Object Classes X
OMWF Maintain Users: Initial Screen X
OMWG Profiles: Initial Screen X
OMWK Maintain Authorizations: Object Classes X
OOAU Maintain Authorizations: Object Classes X
OOPR Profiles: Initial Screen X
OOSB Change View "User Authorizations":
Overview
X
OOSP Change View "Authorization Profiles":
Overview
X
OOUS Maintain Users: Initial Screen X
OP15 Profiles: Initial Screen X
OP29 Maintain Users: Initial Screen X
OPCA Maintain Users: Initial Screen X
OPCB Profiles: Initial Screen X
OPCC Maintain Authorizations: Object Classes X
OPE9 Profiles: Initial Screen X
OPF0 Maintain Users: Initial Screen X
OPF1 Maintain Authorizations: Object Classes X
OPJ0 Maintain Users: Initial Screen X
OPJ1 Profiles: Initial Screen X
OPJ3 Maintain Authorizations: Object Classes X
OSSZ Maintain Authorizations: Object Classes X
OTZ1 Maintain Users: Initial Screen X
OTZ2 Profiles: Initial Screen X
OTZ3 Maintain Authorizations: Object Classes X
OVZ5 Maintain Users: Initial Screen X
OVZ6 Profiles: Initial Screen X
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
Release 4.0B
812
Transaction Description Dangerous Security Performance
OY20 Maintain Authorizations: Object Classes X
OY21 Profiles: Initial Screen X
OY22 Maintain Users: Initial Screen X
OY27 Maintain Users: Initial Screen X
OY28 Maintain Users: Initial Screen X
OY29 Maintain Users: Initial Screen X
OY30 Maintain Users: Initial Screen X
SCC5 Client delete X
SE01 Transport Organizer
SE06 System Table maintenance X X
SE09 Workbench Organizer
SE10 Customizing Organizer
SE11 Data Dictionary maintenance X
SE13 Maintain Storage parameters for table X
SE14 Utilities for dictionary tables X
SE15 Data Dictionary Information System
SE16 Data Browser X
SE17 General Table display X
SE38 ABAP workbench X
SM49 External OS commands X
SM69 External OS commands X
ST05 SQL trace X
SU12 Delete All Users X X
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
R/3 System Administration Made Easy
813
The following table shows dangerous transactions that probably cannot be locked because they are (or
could be) used regularlyor have other valid reasons for use in a production systembut because of the
potential danger, need to have restricted access.
Transaction Description Dangerous Security Performance
RZ10 Edit System Profiles X
SA38 ABAP Workbench X
SM04 User Overview X
SM12 System Locks X
SM13 Update Terminates X
SM30 Table Maintenance X
SM31 Table Maintenance X
STMS Transport Management System X
SU01 User Maintenance X
SU02 Profiles: Initial Screen X
SU03 Maintain Authorizations: Object Classes X
Table TSTCT contains the transaction codes and the name of the transaction. The current
content is over 30,000 entries in the table, with over 16,000 in English.
How
Document and keep a list of the following information:
< Which transactions were locked?
< Why are they locked?
< Who locked them?
< When were they locked?
Chapter 8: Scheduled Annual Tasks
R/3 Tasks
Release 4.0B
814
Guided Tour
1. In the Command field, enter transaction SM01 and choose Enter
(or choose Tools Administration, then Administration Tcode administration).
2. Enter the transaction code you
want to lock (for example, SE14)
in the search field at the bottom of
the TCode column.
3. Choose Enter.
4. Use the Locked checkbox:
< To lock a transaction, select the
checkbox next to the
transaction.
< To unlock a transaction,
deselect the checkbox.
5. Choose Enter.
Carefully check which transactions you lock. You could accidentally lock yourself out of a
transaction, which would prevent you from unlocking this or other transactions.
4
2
5
3
Chapter 8: Scheduled Annual Tasks
Database Tasks
R/3 System Administration Made Easy
815
Access to transactions can also be controlled by building security authorizations on the
security object S_TCODE under Cross application authorization objects.
Database Tasks
Backups
< Make certain you get a usable backup at year-end.
< Send backup tapes offsite for an extended period.
Operating 8ystem Tasks
Backups
< Make certain you get a usable backup at year-end.
< Send backup tapes offsite for an extended period.
Other Tasks
Disaster Recovery Test
Perform a full system recovery test.
See chapter 2, Disaster Recovery.
Chapter 8: Scheduled Annual Tasks
Other Tasks
Release 4.0B
816
You might also like
- Sap Solution Manager - Implemetation ToolsDocument20 pagesSap Solution Manager - Implemetation Toolshttp://wlacaze.googlepages.com/home100% (7)
- Microsoft Azure For Sap Workloads Specialty Skills MeasuredDocument5 pagesMicrosoft Azure For Sap Workloads Specialty Skills MeasuredDenazareth JesusNo ratings yet
- Technical Monitoring SOLMANDocument29 pagesTechnical Monitoring SOLMANrathoremssssssNo ratings yet
- Managing PSE Files at The Web Dispatcher - Application Server InfrastructureDocument5 pagesManaging PSE Files at The Web Dispatcher - Application Server InfrastructureivanNo ratings yet
- SAP 4.7 Installation TutorialDocument54 pagesSAP 4.7 Installation Tutorialrajeev.ashokan8023100% (34)
- SAP Solution Manager Service Desk Support Team E-Mail NotificationDocument19 pagesSAP Solution Manager Service Desk Support Team E-Mail NotificationadhaferaNo ratings yet
- A Step by Step Manual Guide With Screen Shots - Sap Basis - Daily Check ListDocument7 pagesA Step by Step Manual Guide With Screen Shots - Sap Basis - Daily Check ListAnimesh Sinha100% (1)
- SAP Solution ManagerDocument4 pagesSAP Solution ManagerPrasanta Kumar NandaNo ratings yet
- HANA Technical Landscape Preparation v4Document58 pagesHANA Technical Landscape Preparation v4phong_ho_10No ratings yet
- BW Strategies, Techniques, and Best Practices To Upgrade, Copy, and Migrate SAP BW Systems PDFDocument86 pagesBW Strategies, Techniques, and Best Practices To Upgrade, Copy, and Migrate SAP BW Systems PDFAlexis Antonio Ramirez LaraNo ratings yet
- SAP Basis - Daily Check List: SAP Logon Connection TestDocument6 pagesSAP Basis - Daily Check List: SAP Logon Connection Testkhaled_dudeNo ratings yet
- SAP Consultant CertificationDocument32 pagesSAP Consultant Certificationnev2nevNo ratings yet
- Installation of SAP Content Server DMS On WindowsDocument40 pagesInstallation of SAP Content Server DMS On WindowsAndres OrtizNo ratings yet
- Implementation Guide For Data Volume Management Workcenter - V3 PDFDocument23 pagesImplementation Guide For Data Volume Management Workcenter - V3 PDFanurag100% (1)
- How To Check SAP Performance - Quick ChecksDocument4 pagesHow To Check SAP Performance - Quick ChecksDevender5194No ratings yet
- Thrinath Soma – SAP Basis Consultant ProceduresDocument179 pagesThrinath Soma – SAP Basis Consultant Proceduressoma3nathNo ratings yet
- Sap Solution Manager - CHARM - Issue ManagementDocument13 pagesSap Solution Manager - CHARM - Issue Managementhttp://wlacaze.googlepages.com/home100% (5)
- Questions On SAP BASISDocument16 pagesQuestions On SAP BASISsai ramNo ratings yet
- SAP Basis - Daily Check List SAP How To Step by Step Guide With Screen ShotDocument6 pagesSAP Basis - Daily Check List SAP How To Step by Step Guide With Screen ShotRafael Andrade FagundesNo ratings yet
- Step by Step Guide of Modeling HANA Views Into BW in SAP BW 7 4 On HANADocument44 pagesStep by Step Guide of Modeling HANA Views Into BW in SAP BW 7 4 On HANAJaya SankarNo ratings yet
- SAP System Health Check DocumentDocument6 pagesSAP System Health Check DocumentSandy SoupyNo ratings yet
- Security Weaver - Transaction Archive GuideDocument27 pagesSecurity Weaver - Transaction Archive GuideFabian HernandezNo ratings yet
- The Ultimate C - P - TSEC10 - 75 - SAP Certified Technology Professional - System Security ArchitectDocument3 pagesThe Ultimate C - P - TSEC10 - 75 - SAP Certified Technology Professional - System Security ArchitectKirstingNo ratings yet
- BW Source System: Troubleshooting Guide: P. Mani Vannan SAP Labs IndiaDocument14 pagesBW Source System: Troubleshooting Guide: P. Mani Vannan SAP Labs Indiarao_okcNo ratings yet
- Quick Guide To Checks Any SAP Performance Issue in SAP ABAP System BuddySAPDocument2 pagesQuick Guide To Checks Any SAP Performance Issue in SAP ABAP System BuddySAPksreddy58No ratings yet
- Configuration GuideDocument99 pagesConfiguration Guideandrealeger755774No ratings yet
- SAP SolMan BO IntegrationDocument29 pagesSAP SolMan BO IntegrationAshish VermaNo ratings yet
- Monitor SAP Systems with 15 ActivitiesDocument16 pagesMonitor SAP Systems with 15 ActivitiesBharath Teja UyyalaNo ratings yet
- Fine Tuning Performance SAP Enterprise PortalDocument50 pagesFine Tuning Performance SAP Enterprise PortalJ Agostinho O JuniorNo ratings yet
- Hana PDFDocument7 pagesHana PDFDevender5194No ratings yet
- Sap MonitoringDocument13 pagesSap MonitoringmoorthykemNo ratings yet
- Technical Details - Software Provisioning Manager 1.0 SP22Document20 pagesTechnical Details - Software Provisioning Manager 1.0 SP22talankirkNo ratings yet
- Install Guide Erp 6.0 Ehp7 Abap JavaDocument32 pagesInstall Guide Erp 6.0 Ehp7 Abap JavamigofcisNo ratings yet
- SAP ECC Systems SP Upgrade and Impact On SAP BIDocument10 pagesSAP ECC Systems SP Upgrade and Impact On SAP BIVasu SreeNo ratings yet
- Upgrade Sap Ehp7 JavaDocument38 pagesUpgrade Sap Ehp7 JavaRohit KanthNo ratings yet
- Cts FinalDocument55 pagesCts FinalSanket KohliNo ratings yet
- Sap Basis IntroductoryDocument53 pagesSap Basis IntroductoryJatin KashyapNo ratings yet
- Troubleshooting TipsDocument75 pagesTroubleshooting TipsSurendra KumarNo ratings yet
- SAP Java Troubleshooting MonitoringDocument24 pagesSAP Java Troubleshooting MonitoringTeegala BalreddyNo ratings yet
- How Do I Use The Cron To Schedule A BackupDocument44 pagesHow Do I Use The Cron To Schedule A BackupCesar Ubilla50% (2)
- Backup&Restore of SAP LandscapesDocument64 pagesBackup&Restore of SAP LandscapesRavindra Chowdary GokinaNo ratings yet
- Programming (PDF Library)Document18 pagesProgramming (PDF Library)Karthik KumarNo ratings yet
- SAP R3 SysadminstartorDocument56 pagesSAP R3 SysadminstartorvsivaramakrishnaNo ratings yet
- SAP Web Dispatcher InstallationDocument1 pageSAP Web Dispatcher InstallationAbdul27No ratings yet
- SAP Identity Management APIsDocument57 pagesSAP Identity Management APIsDwi Pamudji SoetedjoNo ratings yet
- SAP User License TypesDocument1 pageSAP User License Typesb_desarkarNo ratings yet
- How To Configure SAP Web Dispatcher For SSL20Document15 pagesHow To Configure SAP Web Dispatcher For SSL20Tam CaptainNo ratings yet
- Sap Support PortalDocument17 pagesSap Support PortalRobert van MeijerenNo ratings yet
- SAP NetWeaver Business Warehouse A Complete Guide - 2021 EditionFrom EverandSAP NetWeaver Business Warehouse A Complete Guide - 2021 EditionNo ratings yet
- RAC System Test Plan Outline 11gr2 v2 0Document39 pagesRAC System Test Plan Outline 11gr2 v2 0Dinesh KumarNo ratings yet
- ABAP SQL Trace PDFDocument35 pagesABAP SQL Trace PDFVenkateshNo ratings yet
- Landscape Is Like A Server System or Like A Layout of The Servers or Some May Even Call It The Architecture of The Servers VizDocument5 pagesLandscape Is Like A Server System or Like A Layout of The Servers or Some May Even Call It The Architecture of The Servers VizasdlhaskdgjasNo ratings yet
- RAC System Test Plan Outline 11gr2 v2 4Document39 pagesRAC System Test Plan Outline 11gr2 v2 4xwNo ratings yet
- DB Replay White Paper Ow07 1-2-133325Document19 pagesDB Replay White Paper Ow07 1-2-133325IgorNo ratings yet
- Computing Center Management SystemDocument3 pagesComputing Center Management Systemganesanmani1985No ratings yet
- Silk PerformerDocument33 pagesSilk PerformerGeetha Sravanthi100% (1)
- Software Performance Testing: - Sathireddy MandadiDocument35 pagesSoftware Performance Testing: - Sathireddy MandadiIchaituNo ratings yet
- SW Engineering NotesDocument4 pagesSW Engineering NotesRamu EppalaNo ratings yet
- Development & Application of V&V Model To Tyre Industry Process For Production & Quality ImprovementDocument5 pagesDevelopment & Application of V&V Model To Tyre Industry Process For Production & Quality ImprovementijaertNo ratings yet
- SDLC Testing and Deployment StrategiesDocument25 pagesSDLC Testing and Deployment StrategiesJesseSpero75% (4)
- March 2015 Accounts Assistant 0Document2 pagesMarch 2015 Accounts Assistant 0Mariana Claudia PanaitNo ratings yet
- Kubernetes As A Service at VCCloudDocument27 pagesKubernetes As A Service at VCCloudKiên Trần TrungNo ratings yet
- Lenovo S650: Quick Start Guide v1.0Document6 pagesLenovo S650: Quick Start Guide v1.0dedi iskandarNo ratings yet
- Information Systems Management Dissertation TopicsDocument7 pagesInformation Systems Management Dissertation TopicsPaperWritersForCollegeWashingtonNo ratings yet
- Modbus Devices - User Manual - EN - 1.4Document54 pagesModbus Devices - User Manual - EN - 1.4huskeeNo ratings yet
- Tweak Network Configurations of OpenGeo Suite ServerDocument3 pagesTweak Network Configurations of OpenGeo Suite ServerSiAgam DevinfoNo ratings yet
- Master Test PlanDocument15 pagesMaster Test PlanALVARO NICOLAS ZEVALLOS RIOSNo ratings yet
- Quickbooks Update Error 15227Document4 pagesQuickbooks Update Error 15227andrewmoore01No ratings yet
- 6-1 JMS Adapter Install GuideDocument10 pages6-1 JMS Adapter Install GuidesatenawNo ratings yet
- Sap BW On Hana (Lesson1-3)Document18 pagesSap BW On Hana (Lesson1-3)Azfar RazaNo ratings yet
- WEATHERFORD - Rig-IntegrationDocument8 pagesWEATHERFORD - Rig-IntegrationWolfensteinNo ratings yet
- Generating PDF With Animations Using LaTeXDocument6 pagesGenerating PDF With Animations Using LaTeXchristos032No ratings yet
- HP LJ m14 m17 and m28mfp m31mfp Troubleshooting ManualDocument156 pagesHP LJ m14 m17 and m28mfp m31mfp Troubleshooting ManualVladimirNo ratings yet
- BNG CiscoDocument10 pagesBNG CiscoangelpyNo ratings yet
- Hawassa University IOT RUP Software ProcessDocument17 pagesHawassa University IOT RUP Software ProcessZobahaa HorunkuNo ratings yet
- Focus ERP & Implementation Methodology DocuementDocument42 pagesFocus ERP & Implementation Methodology DocuementRuban ThomasNo ratings yet
- Introduction to Java AppletsDocument22 pagesIntroduction to Java AppletsParthibanNo ratings yet
- Cambridge International AS & A Level: Computer Science 9608/11Document16 pagesCambridge International AS & A Level: Computer Science 9608/11Zaki JrNo ratings yet
- iCog-Labs Internship ReportDocument34 pagesiCog-Labs Internship Reportmanu100% (2)
- RNC Software ARCH-Ver0.01Document23 pagesRNC Software ARCH-Ver0.01Rishi SinghNo ratings yet
- Free PMI-SP QuestionsDocument7 pagesFree PMI-SP QuestionsAbhishekKumarNo ratings yet
- Oracle Business AcceleratorsDocument24 pagesOracle Business AcceleratorsSuman BeemisettyNo ratings yet
- Syllabus Info CSE240Document7 pagesSyllabus Info CSE240Seungbin HwangNo ratings yet
- Design an App or Website Using Figma for UI/UXDocument68 pagesDesign an App or Website Using Figma for UI/UXAldrin VillanuevaNo ratings yet
- Online Safety, Security, Ethics, andDocument23 pagesOnline Safety, Security, Ethics, andGil Victor MerzaNo ratings yet
- Oracle® Transportation Management: Data Management Guide Release 6.3 Part No. E38426-04Document128 pagesOracle® Transportation Management: Data Management Guide Release 6.3 Part No. E38426-04Nirav PanchalNo ratings yet
- ACAD LineType PDFDocument3 pagesACAD LineType PDFManjunath HrmNo ratings yet
- ATILA Finite Element Software Package For The Analysis of 2D and 3D Structures Based On Smart MaterialsDocument2 pagesATILA Finite Element Software Package For The Analysis of 2D and 3D Structures Based On Smart MaterialsTariq MahmoodNo ratings yet
- 10 Top Advantages and Disadvantages of Technology in Education - Green Garage PDFDocument5 pages10 Top Advantages and Disadvantages of Technology in Education - Green Garage PDFnadheer bashirNo ratings yet
- Logicore Ip Reed-Solomon Encoder v8.0: Product GuideDocument30 pagesLogicore Ip Reed-Solomon Encoder v8.0: Product GuideamanNo ratings yet