Professional Documents
Culture Documents
ISO27001 Server Security Best Practices Checklist
Uploaded by
fnky_byOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
ISO27001 Server Security Best Practices Checklist
Uploaded by
fnky_byCopyright:
Available Formats
Server Security Best Practices Checklist
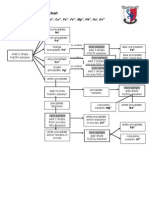
No Area 1 Organizational Information System Security Policy Control Status A security policy should specify the basic information system security tenets and rules, and their intended internal purpose. The policy should also outline who in the organization is responsible for particular areas of information security (e.g., implementation, enforcement, audit, review). The policy must be enforced consistently throughout the organization to be effective. Generally, the CIO is responsible for drafting the organizations security policy. The process of controlling modification to a systems design, hardware, firmware, and software provides sufficient assurance that the system is protected against the introduction of an improper modification before, during, and after system implementation. Configuration control leads to consistency with the organizations information system security policy. Configuration control is traditionally overseen by a configuration control board that is the final authority on all proposed changes to an information system. If resources allow, consider the use of development, quality assurance, and/or test environments so that changes can be vetted and tested before deployment in production. Risk assessment is the process of analyzing and interpreting risk. It involves determining an assessments scope and methodology, collecting and analyzing riskrelated data, and interpreting the risk analysis results. Collecting and analyzing risk data requires identifying assets, threats, vulnerabilities, safeguards, consequences, and the probability of a successful attack. Risk management is the process of selecting and implementing controls to reduce risk to a level acceptable to the organization.
2 Configuration/Change Control and Management
3 Risk Assessment and Management
4 Standardized Configurations Standardized Configurations Organizations should develop standardized secure configurations for widely used OSs and server software. This will provide recommendations to server and network administrators on how to configure their systems securely and ensure consistency and compliance with the organizational security policy. Because it only takes one insecurely configured host to compromise a network, organizations with a significant number of hosts are especially encouraged to apply this recommendation.
5 Secure Programming Practices
Secure Programming Practices Organizations should adopt secure application development guidelines to ensure that they develop their applications for servers in a sufficiently secure manner. Security Awareness and Training A security training program is critical to the overall security posture of an organization. Making users and administrators aware of their security responsibilities and teaching the correct practices helps them change their behavior to conform to security best practices. Training also supports individual accountability, which is an important method for improving information system security. If the user community includes members of the general public, providing security awareness specifically targeting them might also be appropriate. Contingency, Continuity of Operations, and Disaster Recovery Planning Contingency plans, continuity of operations plans, and disaster recovery plans are established in advance to allow an organization or facility to maintain operations in the event of a disruption.8 Certification and Accreditation Certification in the context of information system security means that a system has been analyzed to determine how well it meets all of the security requirements of the organization. Accreditation occurs when the organizations management accepts that the system meets the organizations security requirements Prepared By
6 Security Awareness and Training
7 Contingency, Continuity of Operations, and Disaster Recovery Planning
8 Certification and Accreditation
Acknowledged By
Date
Date
Notes
Prepared By
You might also like
- Qualified Security Assessor Complete Self-Assessment GuideFrom EverandQualified Security Assessor Complete Self-Assessment GuideNo ratings yet
- Security Awareness Programs A Complete Guide - 2019 EditionFrom EverandSecurity Awareness Programs A Complete Guide - 2019 EditionNo ratings yet
- ISO IEC 27001 Lead Implementer A Complete Guide - 2020 EditionFrom EverandISO IEC 27001 Lead Implementer A Complete Guide - 2020 EditionNo ratings yet
- Asset Attack Vectors: Building Effective Vulnerability Management Strategies to Protect OrganizationsFrom EverandAsset Attack Vectors: Building Effective Vulnerability Management Strategies to Protect OrganizationsNo ratings yet
- Security And Risk Management Tools A Complete Guide - 2020 EditionFrom EverandSecurity And Risk Management Tools A Complete Guide - 2020 EditionNo ratings yet
- Security TestingDocument70 pagesSecurity Testingneovik82No ratings yet
- Information technology audit The Ultimate Step-By-Step GuideFrom EverandInformation technology audit The Ultimate Step-By-Step GuideNo ratings yet
- Information Technology Security Audit A Complete Guide - 2021 EditionFrom EverandInformation Technology Security Audit A Complete Guide - 2021 EditionNo ratings yet
- Certified Information Security Manager (CISM) Domain 1 - Information Security GovernanceDocument136 pagesCertified Information Security Manager (CISM) Domain 1 - Information Security GovernancenawabkabirNo ratings yet
- A548361697 23636 4 2019 Standards1Document53 pagesA548361697 23636 4 2019 Standards1angel tenshiNo ratings yet
- Navigating the Dark Waters of Cybersecurity Incident ResponseFrom EverandNavigating the Dark Waters of Cybersecurity Incident ResponseNo ratings yet
- Business Continuity Management And IT Disaster Recovery Management A Complete Guide - 2021 EditionFrom EverandBusiness Continuity Management And IT Disaster Recovery Management A Complete Guide - 2021 EditionNo ratings yet
- 1 180 Server Hardening PolicyDocument1 page1 180 Server Hardening PolicylogicRNo ratings yet
- IT Risk Management Process A Complete Guide - 2020 EditionFrom EverandIT Risk Management Process A Complete Guide - 2020 EditionNo ratings yet
- Dynamic Application Security Testing A Complete Guide - 2019 EditionFrom EverandDynamic Application Security Testing A Complete Guide - 2019 EditionNo ratings yet
- A Practitioner's Guide to Adapting the NIST Cybersecurity FrameworkFrom EverandA Practitioner's Guide to Adapting the NIST Cybersecurity FrameworkNo ratings yet
- Threat and Vulnerability Management Complete Self-Assessment GuideFrom EverandThreat and Vulnerability Management Complete Self-Assessment GuideNo ratings yet
- Aquisition Assessment PolicyDocument2 pagesAquisition Assessment PolicyConstantin TomaNo ratings yet
- Cism WB04Document86 pagesCism WB04kingshukdutta100% (1)
- Iso 27001 SampleDocument54 pagesIso 27001 SampleergNo ratings yet
- Information Security Made SimpleDocument15 pagesInformation Security Made SimpleSeenivasagam Seenu50% (2)
- Information Security Incident Management PolicyDocument14 pagesInformation Security Incident Management PolicyLy ĐỗNo ratings yet
- Cloud Security Best PracticesDocument55 pagesCloud Security Best PracticesSidNo ratings yet
- It PolicyDocument4 pagesIt PolicyRoen AbeNo ratings yet
- Ism Presentation SlidesDocument13 pagesIsm Presentation Slidesnithi_123No ratings yet
- Information Security Risk Management Policy: General DescriptionDocument8 pagesInformation Security Risk Management Policy: General DescriptionAmr M. AminNo ratings yet
- CISA Item Development Guide Bro Eng 0117Document20 pagesCISA Item Development Guide Bro Eng 0117Fahim YusufNo ratings yet
- Active Directory Services Audit - Document ReferencesDocument7 pagesActive Directory Services Audit - Document ReferencesJinish KG100% (1)
- ITA IT Risk Assessment MatrixDocument36 pagesITA IT Risk Assessment MatrixssglcnNo ratings yet
- Anti Virus Protection PolicyDocument3 pagesAnti Virus Protection PolicyOmar AyoubNo ratings yet
- Invincea Spear Phishing Watering Hole Drive by Whitepaper 5.17.131 PDFDocument16 pagesInvincea Spear Phishing Watering Hole Drive by Whitepaper 5.17.131 PDFfnky_byNo ratings yet
- Information Systems For Business and BeyondDocument167 pagesInformation Systems For Business and Beyondfnky_byNo ratings yet
- HackingDocument50 pagesHackingtallyx67% (3)
- TcodeDocument6 pagesTcodejaganegellagaNo ratings yet
- 20 Security ControlsDocument63 pages20 Security ControlsbcotterNo ratings yet
- Data Leakage: Pete Readings CISSPDocument8 pagesData Leakage: Pete Readings CISSPfnky_byNo ratings yet
- Sap r3 BasisDocument4 pagesSap r3 Basisfnky_byNo ratings yet
- Cisco Physical and Logical SecurityDocument15 pagesCisco Physical and Logical Securityfnky_byNo ratings yet
- Cocktail Making Techniques 13.3.11Document3 pagesCocktail Making Techniques 13.3.11Ryan MenezesNo ratings yet
- Adobeconstruct 19 NeubDocument34 pagesAdobeconstruct 19 NeublailanuitNo ratings yet
- LPG PropertiesDocument2 pagesLPG Propertiesvvk557No ratings yet
- Nutrition Label ResponseDocument1 pageNutrition Label ResponseZoe JonesNo ratings yet
- Book Summary - I Hear You Summary Michael Sorensen - Read in 7 MinutesDocument10 pagesBook Summary - I Hear You Summary Michael Sorensen - Read in 7 MinutesNogüey JoseNo ratings yet
- INTERWELL Anchored Production Straddle Product SheetDocument2 pagesINTERWELL Anchored Production Straddle Product SheetDavid Pit FermiereNo ratings yet
- AT-502 - AT-504 - OM-0-Introduction-1 - 10-12-2019Document6 pagesAT-502 - AT-504 - OM-0-Introduction-1 - 10-12-2019Vinicius RodriguesNo ratings yet
- CV Mary Mugo 2017Document4 pagesCV Mary Mugo 2017Mary Wanja MugoNo ratings yet
- Alix Pelletier Luginbühl - Works / PRINT VERSIONDocument44 pagesAlix Pelletier Luginbühl - Works / PRINT VERSIONJonathan Philippe LEVYNo ratings yet
- PNOZ E1vp EN-23-27Document5 pagesPNOZ E1vp EN-23-27Rachid MoussaouiNo ratings yet
- Sensus 143-80 Service Regulator R-1301 R5Document11 pagesSensus 143-80 Service Regulator R-1301 R5Paolita Auza BalderramaNo ratings yet
- Magicad Heating&Piping and Ventilation Version 2011.11: User'S GuideDocument285 pagesMagicad Heating&Piping and Ventilation Version 2011.11: User'S GuideCalin CalinNo ratings yet
- Testing For Cations Flow ChartDocument2 pagesTesting For Cations Flow Chartapi-252561013No ratings yet
- Stern TubesDocument8 pagesStern Tubesweesweekwee8652No ratings yet
- Expository Cause and Effect OUTLINEDocument2 pagesExpository Cause and Effect OUTLINEAutoDefenceNo ratings yet
- All Electricity Worksheets For Midterm 22Document22 pagesAll Electricity Worksheets For Midterm 22Maryam AlkaabiNo ratings yet
- Fosroc Conplast SP335: Multi-Range Water Reducing AdmixtureDocument2 pagesFosroc Conplast SP335: Multi-Range Water Reducing AdmixtureVincent JavateNo ratings yet
- Pay Slip SampleDocument3 pagesPay Slip SampleJoseph ClaveriaNo ratings yet
- SurveyDocument1 pageSurveyJainne Ann BetchaidaNo ratings yet
- Conference Proceedings: Inhaled Nitric Oxide: Delivery Systems and MonitoringDocument27 pagesConference Proceedings: Inhaled Nitric Oxide: Delivery Systems and MonitoringPhanNo ratings yet
- 9 SolutionsDocument31 pages9 SolutionsLaurertan TavaresNo ratings yet
- Tibia Bone Segmentation in X-Ray Images - A Comparative AnalysisDocument8 pagesTibia Bone Segmentation in X-Ray Images - A Comparative AnalysisSuzanaPetrovicNo ratings yet
- Presented By: Agamjeet Singh Batra, VI - NDocument27 pagesPresented By: Agamjeet Singh Batra, VI - NlovleshrubyNo ratings yet
- Ferrography/oil Analysis: An Excellent Condition Monitoring TechniqueDocument5 pagesFerrography/oil Analysis: An Excellent Condition Monitoring Techniquedaniel zorroNo ratings yet
- Health Insurance BookDocument3 pagesHealth Insurance BookHarish SihareNo ratings yet
- Should Beauty Pageants Be BannedDocument2 pagesShould Beauty Pageants Be BannedHastin Dilipbhai BagthariyaNo ratings yet
- Stanford - Trauma - Guidelines June 2016 Draft Adult and Peds FINALDocument166 pagesStanford - Trauma - Guidelines June 2016 Draft Adult and Peds FINALHaidir Muhammad100% (1)
- PQPDocument60 pagesPQPlee100% (4)
- The Room - SartreDocument14 pagesThe Room - SartreYue Biohazard100% (1)
- Dingenen 2017Document14 pagesDingenen 2017pedro.coleffNo ratings yet