Professional Documents
Culture Documents
BOBJ
Uploaded by
madhu.gCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
BOBJ
Uploaded by
madhu.gCopyright:
Available Formats
Greg Wcislo
September, 2013
EA209
Understanding Security and Rights in
SAP BusinessObjects Business Intelligence 4.1
2013 SAP AG or an SAP affiliate company. All rights reserved. 2
Disclaimer
This presentation outlines our general product direction and should not be relied on in making a
purchase decision. This presentation is not subject to your license agreement or any other agreement
with SAP. SAP has no obligation to pursue any course of business outlined in this presentation or to
develop or release any functionality mentioned in this presentation. This presentation and SAP's
strategy and possible future developments are subject to change and may be changed by SAP at any
time for any reason without notice. This document is provided without a warranty of any kind, either
express or implied, including but not limited to, the implied warranties of merchantability, fitness for a
particular purpose, or non-infringement. SAP assumes no responsibility for errors or omissions in this
document, except if such damages were caused by SAP intentionally or grossly negligent.
2013 SAP AG or an SAP affiliate company. All rights reserved. 3
Agenda
What security is available in BI4
Authentication, Report, Application, Data
Inheritance
Securing at the right layer
BI Object security (report level)
Universe security
Data source security
Best practices for a low headache security model
Security changes between 3.1 and 4.x
Different levels of security
2013 SAP AG or an SAP affiliate company. All rights reserved. 5
Data Security
Data can be secured at:
Folder/report level
Universe level
Database source level
2013 SAP AG or an SAP affiliate company. All rights reserved. 6
Considerations when creating Connections to data (shared)
Shared Connection
All users logon to database with same shared
user ID.
Often referred to as Technical User or
System User.
Secure in BI system at report or universe level
Pros:
No need to replicate users & manage
security at database level
Cons:
No differentiation of what users can see
in the database*.
2013 SAP AG or an SAP affiliate company. All rights reserved. 7
Considerations when creating Connections to data (SSO)
Use Single Sign On
Kerberos available for
MS SQL Server & Analsysis Services
Oracle
Teradata (as of 4.1 via ODBC)
HANA
Trust Certificates*
HANA (internally SAML)
SAP
Pros:
Users account & security applied at data source level
(most secure)
Cons:
No Kerberos SSO for scheduling
User acounts must exist on both systems
Refer to http://scn.sap.com/docs/DOC-
33875 for full list of SSO options
2013 SAP AG or an SAP affiliate company. All rights reserved. 8
Considerations when creating Connections to data (save password)
Credential Mapping
Users database credentials hardcoded and saved
in BI4 system
Password capture/replication required
A user can only have one of these in the system.
Capture during logon if no SSO or set via SDK
2013 SAP AG or an SAP affiliate company. All rights reserved. 9
Some help deciding where to secure
Report objects are still going to be listed if only database is secured
Consider where your main user management is, take user federation into consideration
Consider your overall landscape (not just BI). Do you have other applications accessing your DB?
2013 SAP AG or an SAP affiliate company. All rights reserved. 10
Application rights
Set what user can do in system
Example Webi report edit panel, logon to CMC
2013 SAP AG or an SAP affiliate company. All rights reserved. 11
Access Control List
Access Control List (ACL) is the list of principals who have access to an object .
Principals are the users and groups.
2013 SAP AG or an SAP affiliate company. All rights reserved. 12
Access Levels
Many rights in the system
Do not assign individual rights
Not reproducible, high maintenance
Use Access levels which are collections
of rights
Assign to groups, not individual users
Build up from minimum rights and increment
Minimize explicit denies
Grant + Deny = Deny
2013 SAP AG or an SAP affiliate company. All rights reserved. 13
Rights
General rights can be
overridden by content specific
rights.
Example: Right to Add object
granted, right to add Webi
object denied.
Application rights example:
right to use the webi application
2013 SAP AG or an SAP affiliate company. All rights reserved. 14
Example of Application rights
Dictates what you can do with the
application
You must have rights to the actual
object (webi document in this case)
to perform actions
2013 SAP AG or an SAP affiliate company. All rights reserved. 15
Granted, Denied, Not Specified, not sure?
Granted & Denied should be clear, what is not specified?
Denied > Granted > Not Specified
If a right setting is Not Specified, it is denied.
Not permitted unless I say otherwise
Apply to current level or all sublevels
Trumping rights
Ex 1: Set grant rights on folder, but explicitly deny right on a single report or subfolder
Ex 2: Deny rights on folder, but explicitly grant right on single report or subfolder
= granted
= denied
= not specified
2013 SAP AG or an SAP affiliate company. All rights reserved. 16
Multiple folders for departments, basic permissions
Root public folder is denied by default (secure by default).
I have 20 department folders. For each department group, I have to deny permission on 19
folders and grant permission on the single folder. Times 20
Example, how do we actually set this up:
Grant view object but not subjobjects
Seen By Administrator
Seen By HRUser
2013 SAP AG or an SAP affiliate company. All rights reserved. 17
Create access levels from minimal rights to full control
Multiple departments? Consider multi-tenancy tool
Common roles:
Viewers/Consumers
Report creators/Editors
Sometimes split into Analyst user who create or edit reports an Report Editor who can publicly edit &
modify all reports
Report Publisher scheduling & publishing
2013 SAP AG or an SAP affiliate company. All rights reserved. 18
2 Level of inheritance
Groups & Folders
What happens if user is member of 2 groups, one explicitly permits, one explicitly denies?
DENY >GRANT >NOT SPECIFIED
Users & groups also have inheritance
Cheat Sheet:
G + NS = Grant
G + D = Deny
G + D + NS = Deny
D + NS = Deny
2013 SAP AG or an SAP affiliate company. All rights reserved. 19
What has changed between 3.x and 4.x
New Owner Right
Webi Rights changes/renames
http://wiki.scn.sap.com/wiki/display/BOBJ/WEB
I+security+rights+changes+between+XI3.1+and
+BI4.x
Connection Download right
2013 SAP AG or an SAP affiliate company. All rights reserved. 20
CMC tab access
Useful for delegated administration.
http://scn.sap.com/docs/DOC-41311
- Important to note, this is not actual security.
The UI is hidden, but if you do not actually configure rights, a skilled user could still use the
SDK to manage & access settings if they have the rights to do so.
2013 SAP AG or an SAP affiliate company. All rights reserved. 21
More on universe rights, User attribute mapping 1/2
Custom user attributes can be used to further secure universe
2013 SAP AG or an SAP affiliate company. All rights reserved. 22
More on universe rights, User attribute mapping 2/2
See SCN article on complete how to. http://scn.sap.com/community/bi-platform/blog/2012/07/05/user-
attribute-mapping-in-bi4
2013 SAP AG or an SAP affiliate company. All rights reserved. 23
More on universe rights, User attribute mapping 2/3
Full how to at:
http://scn.sap.com/community/bi-
platform/blog/2012/07/05/user-attribute-mapping-in-bi4
2013 SAP AG or an SAP affiliate company. All rights reserved. 24
Security Query Tool
You can see a full listing of rights for a principal
(single user or group)
Useful for debugging
Export to CSV for compliance
Can be scripted for more users, there are
partners who expose more
2013 SAP AG or an SAP affiliate company. All rights reserved. 25
Security Query Tool Results
Output lets you drill down (select HR
folder, select right, see where the source
of the right setting is.
2013 SAP AG or an SAP affiliate company. All rights reserved. 26
Further Information
SAP Education and Certification Opportunities
www.sap.com/education
Watch SAP TechEd Online
www.sapteched.com/online
SAP Public Web
scn.sap.com
http://scn.sap.com/community/bi-platform/blog/2012/07/05/user-attribute-mapping-in-bi4
http://scn.sap.com/docs/DOC-33875
http://scn.sap.com/docs/DOC-41311
http://wiki.scn.sap.com/wiki/display/BOBJ/WEBI+security+rights+changes+between+XI3.1+and+BI4.x
2013 SAP AG or an SAP affiliate company. All rights reserved. 27
SAP TechEd Virtual Hands-on Workshops and SAP TechEd Online
Continue your SAP TechEd education after the event!
SAP TechEd Virtual Hands-on Workshops
Access hands-on workshops post-event
Available January March 2014
Complementary with your SAP TechEd registration
SAP TechEd Online
Access replays of keynotes, Demo Jam, SAP TechEd
LIVE interviews, select lecture sessions, and more!
View content only available online
http://saptechedhandson.sap.com/
http://sapteched.com/online
Feedback
Please complete your session evaluation for EA209.
Thanks for attending this SAP TechEd session.
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (121)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
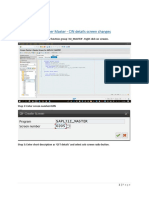
- Customer Master - CIN Details Screen ChangesDocument4 pagesCustomer Master - CIN Details Screen Changespranav kumarNo ratings yet
- 2.7 Industrial and Employee RelationDocument65 pages2.7 Industrial and Employee RelationadhityakinnoNo ratings yet
- Home Energy Loan Program (HELP) Guide and FAQ, City of Penticton, XXXXDocument4 pagesHome Energy Loan Program (HELP) Guide and FAQ, City of Penticton, XXXXIvanJNo ratings yet
- Platform1 Server and HIO Configuration Guide V1.01Document40 pagesPlatform1 Server and HIO Configuration Guide V1.01sirengeniusNo ratings yet
- A 2009Document88 pagesA 2009heroic_aliNo ratings yet
- Punjab National BankDocument28 pagesPunjab National Bankgauravdhawan1991No ratings yet
- Fitzgerald TransformationOpenSource 2006Document13 pagesFitzgerald TransformationOpenSource 2006muthu.manikandan.mNo ratings yet
- Special Topics in Income TaxationDocument78 pagesSpecial Topics in Income TaxationPantas DiwaNo ratings yet
- Table 1: Alagh Committee RecommendationsDocument4 pagesTable 1: Alagh Committee RecommendationsNaveen Kumar Singh100% (1)
- Right To Social JusticeDocument13 pagesRight To Social Justicejooner45No ratings yet
- Read The Five Text Items 1 - 5. Then Read The Headlines A - J. Decide Which Headline A - J Goes Best With Which TextDocument9 pagesRead The Five Text Items 1 - 5. Then Read The Headlines A - J. Decide Which Headline A - J Goes Best With Which TextVeronika HuszárNo ratings yet
- Exchange Content UpdatesDocument2,163 pagesExchange Content UpdatesAlejandro Cortes GarciaNo ratings yet
- Bill Ackman Questions For HerbalifeDocument40 pagesBill Ackman Questions For HerbalifedestmarsNo ratings yet
- United States v. Salvatore Salamone, 902 F.2d 237, 3rd Cir. (1990)Document6 pagesUnited States v. Salvatore Salamone, 902 F.2d 237, 3rd Cir. (1990)Scribd Government DocsNo ratings yet
- CHAPTER 7:, 8, & 9 Group 3Document25 pagesCHAPTER 7:, 8, & 9 Group 3MaffyFelicianoNo ratings yet
- Exercise 2B: 1 A 700 G, As This Is The Most Often Occurring. B 500 + 700 + 400 + 300 + 900 + 700 + 700 4200Document15 pagesExercise 2B: 1 A 700 G, As This Is The Most Often Occurring. B 500 + 700 + 400 + 300 + 900 + 700 + 700 4200drsus78No ratings yet
- Notes On Qawaid FiqhiyaDocument2 pagesNotes On Qawaid FiqhiyatariqsoasNo ratings yet
- Davao October 2014 Criminologist Board Exam Room AssignmentsDocument113 pagesDavao October 2014 Criminologist Board Exam Room AssignmentsPRC Board0% (1)
- ARLANXEO EPDM at A GlanceDocument6 pagesARLANXEO EPDM at A GlanceErwin ErwinNo ratings yet
- Group 4 Written ReportDocument21 pagesGroup 4 Written ReportEm Bel100% (1)
- Fundamentals of Criminal Investigation and IntelligenceDocument189 pagesFundamentals of Criminal Investigation and IntelligenceGABRIEL SOLISNo ratings yet
- COM670 Chapter 5Document19 pagesCOM670 Chapter 5aakapsNo ratings yet
- 2023 Peruvian Citrus Operations ManualDocument30 pages2023 Peruvian Citrus Operations ManualDamarys Leyva SalinasNo ratings yet
- El Presidente - Film AnalysisDocument4 pagesEl Presidente - Film AnalysisMary AshleyNo ratings yet
- Dyson Cylinder DC22 Vacuum User GuideDocument16 pagesDyson Cylinder DC22 Vacuum User Guidejames ryerNo ratings yet
- Business Ethics Session 5Document9 pagesBusiness Ethics Session 5EliaQazilbashNo ratings yet
- InstitutionalismDocument15 pagesInstitutionalismLowel DalisayNo ratings yet
- An Expert Guide To SQL Server Performance Tuning PDFDocument10 pagesAn Expert Guide To SQL Server Performance Tuning PDFMarioNo ratings yet
- Government of IndiaDocument13 pagesGovernment of Indiavikash_kumar_thakurNo ratings yet
- BI - Oleum 65 and 25 PDFDocument2 pagesBI - Oleum 65 and 25 PDFSANDEEP KUMARNo ratings yet